What is Sasser worm?
Appearing in May 2004, the Sasser virus (also known as the W32/Sasser.worm, W32.Sasser.Worm, Worm.Win32.Sasser.a, Worm.Win32.Sasser.b or Win32.Sasser) is a virus which exploits a security hole in the LSASS (Local Security Authority Subsystem Service, which corresponds to the executable file lsass.exe) in Windows. The appearance of the first virus to exploit the security hole in Windows’ LSASS service occurred barely two weeks after the hole was publicised and the first patches for it were released. Windows NT 4.0, 2000, XP and (to a lesser degree) Windows Server 2003 are all affected.
What the virus does
The Sasser virus is programmed to launch 128 processes (1024 for the SasserC variant) which scan a range of random IP addresses looking for systems vulnerable to the LSASS hole on port 445/TCP.
The virus installs an FTP server on port 5554 so that it can be downloaded by other infected computers.
Then, when a vulnerable machine is found, the worm opens a remote shell on the machine (on TCP port 9996), and makes the remote machine download a copy of the worm (named avserve.exe or avserve2.exe for the Sasser.B variant) in the Windows directory.
Once the file has been downloaded, it creates a file named win.log (or win2.log for the Sasser.B variant) in the c:\ directory in order to record how many machines it was able to infect. Then it creates entries in the registry so that it will restart every time the computer is rebooted:
HKLM\Software\Microsoft\Windows\CurrentVersion\Run\avserve = avserve.exe
or
HKLM\Software\Microsoft\Windows\CurrentVersion\Run\
avserve.exe -> C:\%WINDIR%\avserve.exe
The virus runs “AbortSystemShutdown” to prevent the user or other viruses from rebooting (and from deactivating it).
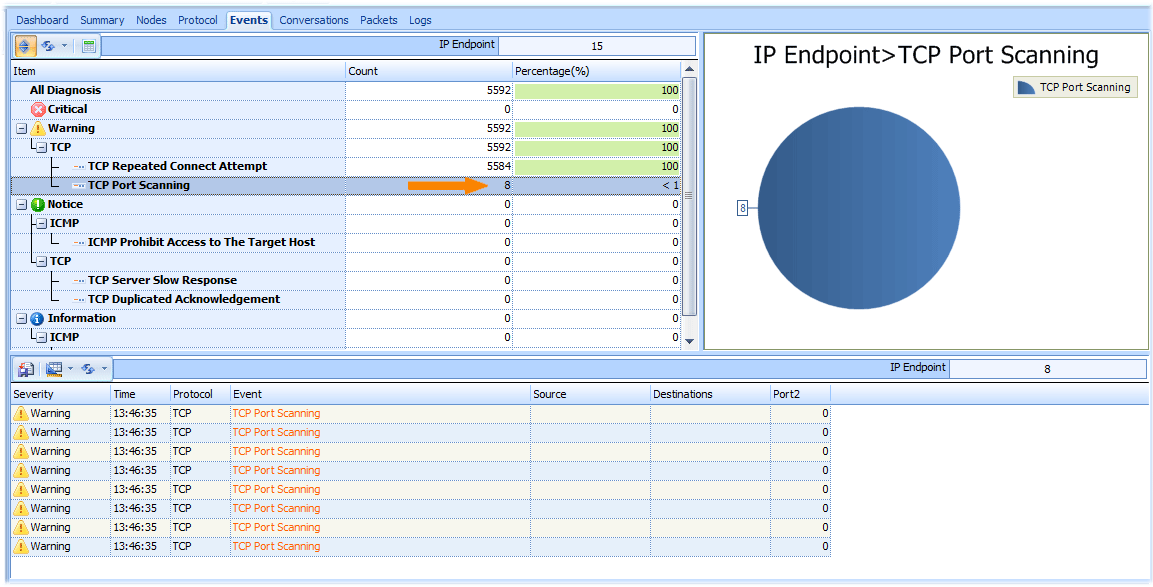
Detect Sasser Worm in Event Tab
Ok, let’s launch the Unicorn and start a new project. We have found that the Sasser will scan a range of random IP addresses looking for systems vulnerable to the LSASS hole on port 445/TCP by analyzing the behavior of the virus. That will lead to Unicorn generate many TCP Scan events. To view events, switch to Events tab.
Figure 1: Detect Sasser Worm in Event Tab
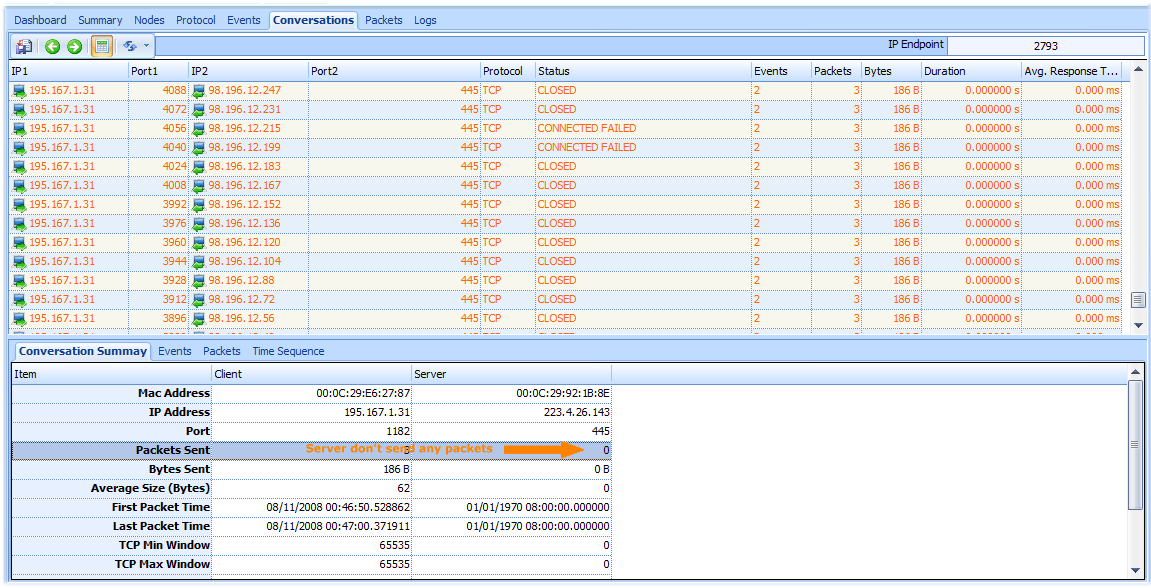
Detect Sasser Worm in Conversation Tab
Let’s switch to conversation tab, we will see that a lots of TCP connections are established via port 445 and many TCP connections are failed, to did not receive any packets from server.