Most computer vulnerabilities can be exploited in a variety of ways. trojan.hacker attacks may use a single specific exploit, several exploits at the same time, a misconfiguration in one of the system components or even a backdoor from an earlier attack.
Due to this, detecting trojan.hacker attacks is not an easy task, especially for an inexperienced user, but Sax2 will let it become very easy, Sax2 is a professional intrusion detection and prevention system (NIDS) and it provides a wealth of security policy. This article gives a few basic solution to help you figure out either if your machine is under attack or if the security of your system has been compromised.
Solution1:
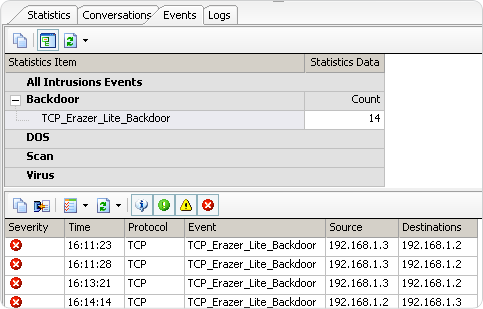
Diagnosis View is the most direct and effective place to detect trojan.hacker attack and should be our first choice. Sax2 can detects most of trojan.hacker attack and generate invasion events, if Sax2 confirm that the current attack are very dangerous, it will automatically block or interfere with the conversation. Picture 1 is an example of detection “Erazer Lite” backdoor.
(picture1)
Solution2:
See E-mail log, Check for suspicious mail, Trojan usually will send a E-mail message in order to steal your important information, such as bank account and password.
Solution3
Suspiciously high outgoing network traffic. If you are on a dial-up account or using ADSL and notice an unusually high volume of outgoing network (traffic especially when you computer is idle or not necessarily uploading data), then it is possible that your computer has been compromised. Your computer may be being used either to send spam or by a network worm which is replicating and sending copies of itself. For cable connections, this is less relevant – it is quite common to have the same amount of outgoing traffic as incoming traffic even if you are doing nothing more than browsing sites or downloading data from the Internet. About how to monitor network traffic (trojan.hacker), please visits https://www.ids-sax2.com/how-to-monitor-network-traffic-with-ax3soft-unicorn/.