What is Sniffer in Networking?
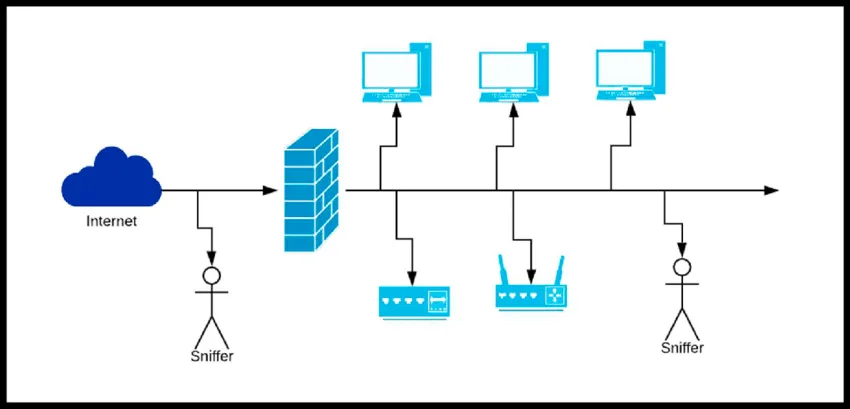
In the realm of computer networks, a network sniffer is a powerful tool used by administrators and hackers alike to intercept and analyze data packets transmitted over a network. Also known as packet sniffers or protocol analyzers, these tools play a crucial role in network management, troubleshooting, and security.
How Network Sniffers Work
At their core, network sniffers function by capturing data packets as they traverse a network. These packets contain valuable information such as source and destination addresses, protocol headers, and payload data. By intercepting these packets, sniffers provide insights into network traffic, allowing users to diagnose issues, monitor performance, and identify potential security threats.
Sniffers operate by placing a network interface into promiscuous mode, enabling it to capture all packets passing through the network segment to which it is connected. This mode allows the sniffer to intercept traffic not intended for the device, providing a comprehensive view of network activity.
Types of Network Sniffing Attacks
Network sniffing can be categorized into two main types: passive and active sniffing. Passive sniffing involves monitoring network traffic without altering it, while active sniffing involves injecting packets into the network to elicit responses from other devices.
Additionally, sniffers can operate in either promiscuous or non-promiscuous modes. Promiscuous sniffing captures all packets on a network segment, regardless of their intended destination, while non-promiscuous sniffing only captures packets intended for the device itself.
What are Network Sniffer Tools?
Network sniffers find application in various areas of network management and security. They are commonly used for:
- Troubleshooting network issues by analyzing packet traffic.
- Monitoring network performance to identify bottlenecks or anomalies.
- Conducting security audits and detecting potential security breaches or unauthorized access.
If you want to find a reliable tool for network sniffing, you can try Unicorn. Unicorn is crafted as a network analyzer, aids users in pinpointing and resolving network failures while also safeguarding against network threats. It offers support in overseeing network performance and security, furnishing real-time fault diagnosis along with detection and response to threats.
Commonly Used Network Sniffing Tools
Several tools are available for capturing and analyzing network traffic, with Wireshark, Tcpdump, and Snort being among the most popular. These tools offer robust features for packet capture, filtering, and analysis, making them indispensable for network administrators and security professionals.
Risks and Concerns of Network Sniffers
While network sniffers offer valuable insights into network activity, they also pose significant risks to privacy and security. Unauthorized use of sniffers can result in the interception of sensitive information, such as passwords, financial data, or personal communications.
To mitigate these risks, it is essential to implement security measures such as encryption, network segmentation, and intrusion detection systems.
Best Practices for Mitigating Sniffing Risks
- Encrypt sensitive data to prevent interception by sniffers.
- Segment networks to limit the scope of sniffing attacks.
- Deploy intrusion detection systems to identify and respond to suspicious network activity.
Real-world Examples of Sniffing Attacks
Numerous incidents have demonstrated the potential impact of sniffing attacks on organizations and individuals. From large-scale data breaches to targeted espionage operations, sniffing attacks continue to pose a significant threat to network security.
Future Trends in Network Sniffing Technology
As technology evolves, so too do the capabilities of network sniffers. Advancements in encryption standards, detection algorithms, and network infrastructure will shape the future of sniffing technology, influencing how organizations defend against and mitigate the risks associated with network sniffing.
Conclusion
In conclusion, network sniffers are powerful tools with diverse applications in network management, troubleshooting, and security. Understanding how sniffers work, their potential risks, and best practices for mitigating those risks is essential for safeguarding sensitive information and maintaining the integrity of network infrastructure.
FAQs about Network Sniffer
- What are the main risks associated with network sniffing?
- Network sniffing poses risks to privacy and security by intercepting sensitive information transmitted over a network.
- Can network sniffers be used for ethical purposes?
- Yes, network sniffers can be used for legitimate purposes such as network troubleshooting and security auditing when used responsibly and with proper authorization.
- How can I tell if someone is sniffing my network?
- Unusual network activity, unexpected data traffic, and suspicious behavior on network devices can indicate the presence of a network sniffer.
- Are there any laws against using network sniffers?
- The legality of using network sniffers varies depending on jurisdiction and intent. Unauthorized use of sniffers to intercept private communications may violate privacy laws.
- Is it possible to completely prevent network sniffing?
- While it is challenging to completely prevent network sniffing, implementing security measures such as encryption and intrusion detection can help mitigate the risks associated with sniffing attacks.



