What is Snort 3 NIDS?
In this tutorial, you will learn how to install and configure Snort 3 on Ubuntu 21.04. Snort is a lightweight network intrusion detection system (NIDS). It has rule-based logging capabilities that can perform content search/matching in addition to detecting various attacks and scans such as buffer overflows, port scans, CGI attacks, SMB probes, and more. Snort has a real-time alerting feature that can send alerts to syslog or record them as a separate “alert” file, or even to a Windows computer via Samba.
Some of the features of Snort 3:
- Multi-threading is supported
- Share configuration and attribute tables.
- Use simple, scripted configurations.
- Critical components are hot-swappable.
- Auto-detect service without port configuration.
- Support for sticky buffers in rules.
- Automatically generate reference documents.
- Better cross-platform support.
Install and Configure Snort 3 on Ubuntu
The Ubuntu 21.04 repository is currently available as snort 2.9. So we need to compile and install Snort 3 from source.
Step 1. Install Snort 3 from Source
1. Update the System Software Source
osboxes@osboxes:~$ sudo apt update
2. Install Dependent Packages and Some Tools Required for Compilation
sudo apt install build-essential libpcap-dev libpcre3-dev libnet1-dev zlib1g-dev luajit hwloc libdnet-dev libdumbnet-dev bison flex liblzma-dev openssl libssl-dev pkg-config libhwloc-dev cmake cpputest libsqlite3-dev uuid-dev libcmocka-dev libnetfilter-queue-dev libmnl-dev autotools-dev libluajit-5.1-dev libunwind-dev
3. Install Snort DAQ
Download and install the latest version of Snort DAQ (Data Acquisition Library). The default Ubuntu repository is not up to date, so you need to compile and install it from source.
osboxes@osboxes:~$ mkdir snortSourceFiles // Create a directory to store the source code
osboxes@osboxes:~$ cd snortSourceFiles
osboxes@osboxes: ~/snortSourceFiles$ git clone https://github.com/snort3/libdaq.git // Download the daq source code from github
osboxes@osboxes:~/snortSourceFiles$ cd libdaq/
osboxes@osboxes: ~/snortSourceFiles/libdaq$ ./bootstrap // Compile and install
osboxes@osboxes:~/snortSourceFiles/libdaq$ ./configure
osboxes@osboxes:~/snortSourceFiles/libdaq$ sudo make
osboxes@osboxes:~/snortSourceFiles/libdaq$ sudo make install
4. Install Malloc for Google-developed Thread Cache: TCMalloc (Optional)
TCMalloc provides an efficient multi-threaded memory management implementation to replace the memory allocation-related functions of the operating system (malloc, free, new, new[], etc.), with features such as reduced memory fragmentation, multi-core suitability, and better parallelism support.
osboxes@osboxes:~/snortSourceFiles/libdaq$ cd ..
osboxes@osboxes:~/snortSourceFiles$ wget https://github.com/gperftools/gperftools/releases/download/gperftools-2.8/gperftools-2.8.tar.gz
osboxes@osboxes:~/snortSourceFiles$ tar xzf gperftools-2.8.tar.gz
osboxes@osboxes:~/snortSourceFiles$ cd gperftools-2.8/
osboxes@osboxes:~/snortSourceFiles/gperftools-2.8$ ./configure
osboxes@osboxes:~/snortSourceFiles/gperftools-2.8$ sudo make && sudo make install
5. Install Snort 3 NIDS from Source
Get the source code from the Snort 3 GitHub repository
osboxes@osboxes:~/snortSourceFiles/gperftools-2.8$ cd ../
osboxes@osboxes:~/snortSourceFiles$ git clone https://github.com/snort3/snort3.git
Compile and install Snort 3
osboxes@osboxes:~/snortSourceFiles$ cd snort3/
osboxes@osboxes:~/snortSourceFiles/snort3$ sudo ./configure_cmake.sh –prefix=/usr/local –enable-tcmalloc
Build Directory : build
Source Directory: /home/osboxes/snortSourceFiles/snort3
— The CXX compiler identification is GNU 10.3.0
— The C compiler identification is GNU 10.3.0
………..
— Configuring done
— Generating done
— Build files have been written to: /home/osboxes/snortSourceFiles/snort3/build
osboxes@osboxes:~/snortSourceFiles/snort3$ cd build/
osboxes@osboxes:~/snortSourceFiles/snort3/build$ sudo make
osboxes@osboxes:~/snortSourceFiles/snort3/build$ sudo make install
osboxes@osboxes:~/snortSourceFiles/snort3/build$ sudo ldconfig
After the installation is complete, check the snort version information
osboxes@osboxes:~/snortSourceFiles/snort3/build$ snort -V ,,_ –> Snort++ <-o”)~ Version 3.1.16.0 ””By Martin Roesch & The Snort Team http://snort.org/contact#team Copyright (C) 2014-2021 Cisco and/or its affiliates. All rights reserved. Copyright (C) 1998-2013 Sourcefire, Inc., et al. Using DAQ version 3.0.5 Using LuaJIT version 2.1.0-beta3 Using OpenSSL 1.1.1j16 Feb 2021 Using libpcap version 1.10.0 (with TPACKET_V3) Using PCRE version 8.39 2016-06-14 Using ZLIB version 1.2.11 Using LZMA version 5.2.5
The above information shows that Snort3 is installed successfully and works fine.
Step 2. Configure Snort 3 on Ubuntu
1. NIC configuration
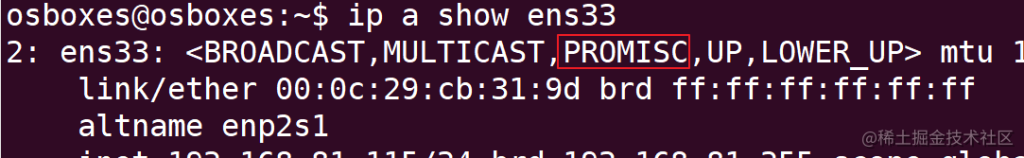
First, you need to set the NIC that Snort is listening on to network traffic to promiscuous mode
osboxes@osboxes:~$ ip a show
1: lo: mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft foreverinet6 ::1/128 scope host valid_lft forever preferred_lft forever
2: ens33: mtu 1500 qdisc fq_codel state UP group default qlen 1000link/ether 00:0c:29:cb:31:9d brd ff:ff:ff:ff:ff:ffaltname enp2s1inet 192.168.81.115/24 brd 192.168.81.255 scope global dynamic ens33 valid_lft 85892sec preferred_lft 85892secinet6 fe80::20c:29ff:fecb:319d/64 scope link valid_lft forever preferred_lft forever
osboxes@osboxes:~$ sudo ip link set dev ens33 promisc on //Set the NIC to promiscuous mode
Disable the NIC Offload feature to prevent Snort from truncating large packets larger than 1518 bytes. You can check if this feature is enabled with the following command:
osboxes@osboxes:~$ ethtool -k ens33 | grep receive-off
generic-receive-offload: on
large-receive-offload: off [fixed]
osboxes@osboxes:~$
You can see that GRO is enabled and disabled with the following command:
osboxes@osboxes:~$ sudo ethtool -K ens33 gro off lro off
However, this disabling and enabling the network card hybrid mode is temporary, and you can write the command to the boot entry so that it will still take effect after restarting.
2. Configure the Snort 3 rule set
Rulesets are a core component of Snort, and there are three main types of rulesets:
Community Rules* Registered Rules* Subscriber Rules* Community Rules: Snort’s free ruleset. * Registration Rules: They are also available for free, but registration is mandatory to get them. * Subscription Rules: Commercial Paid Rule SetsThis tutorial takes configuring a community rule set as an example.
Create a directory where Snort rules are stored. In the /usr/local/etc/snort/snort_defaults.lua configuration file, the default rule set storage path (RULE_PATH) is /usr/local/etc/rules.
osboxes@osboxes:~$ sudo mkdir /usr/local/etc/rules
From the official Snort website www.snort.org/downloads/#… 3′ Community Ruleset
osboxes@osboxes:~$ wget https://www.snort.org/downloads/community/snort3-community-rules.tar.gz
3. Unzip to the rule set directory
osboxes@osboxes:~$ sudo tar xzf snort3-community-rules.tar.gz -C /usr/local/etc/rules/
osboxes@osboxes:~$ ls /usr/local/etc/rules/snort3-community-rules/
AUTHORSLICENSEsid-msg.mapsnort3-community.rulesVRT-License.txt
Next, we need to configure Snort 3, and the main configuration file of Snort is: /usr/local/etc/snort/snort.lua.
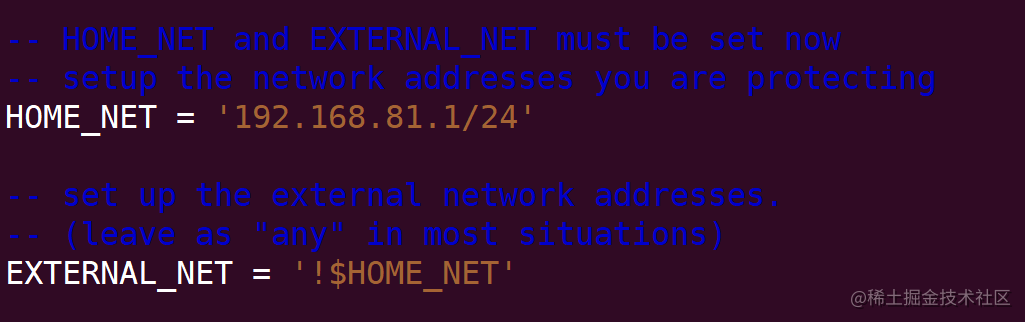
Modify the HOME_NET variables and EXTERNAL_NET variables to change the HOME_NET to the network scope that needs to be detected for network attacks. Set the EXTERNAL_NET to all network ranges except HOME_NET.
osboxes@osboxes:~$ sudo vim /usr/local/etc/snort/snort.lua
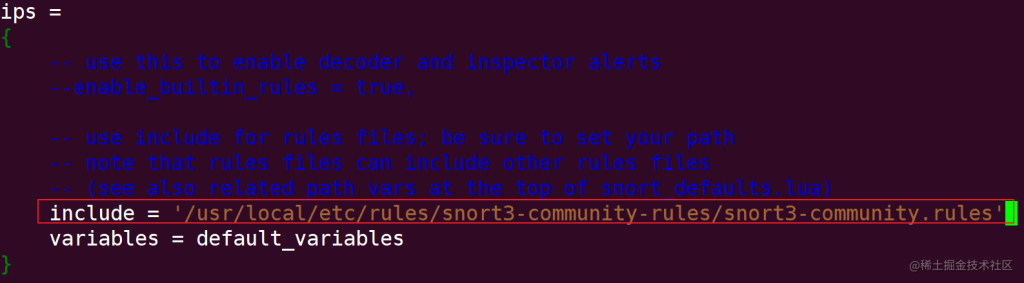
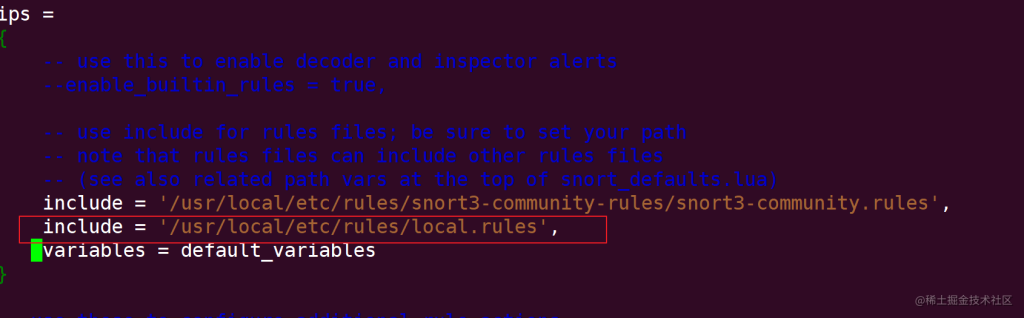
In the IPS section, define the path to the rule set:
You can also modify the /usr/local/etc/snort/snort_defaults.lua configuration file to modify and define some of the default configurations of Snort.
Install Snort OpenAppID
OpenAppID is an application-layer plugin that enables Snort to detect various applications used in the network, such as Facebook, Netflix, Twitter, and more.
From the Snort official website (www.snort.org/downloads/#…%25E4%25B8%258B%25E8%25BD%25BD%25E5%25B9%25B6%25E5%25AE%2589%25E8%25A3%2585 “Snort Rules and IDS Software Download”) Snort OpenAppID
osboxes@osboxes:~$ wget https://www.snort.org/downloads/openappid/19913 -O OpenAppId-19913.tgz
Tips: Please note that the openappid download address here will change due to updates.
Unzip and copy to the appropriate directory:
osboxes@osboxes:~$ tar -xzf OpenAppId-19913.tgz
osboxes@osboxes:~$ sudo cp -R odp /usr/local/lib/
Edit the Snort 3 configuration file and specify the location of the OpenAppID library
osboxes@osboxes:~$ sudo vim /usr/local/etc/snort/snort.lua
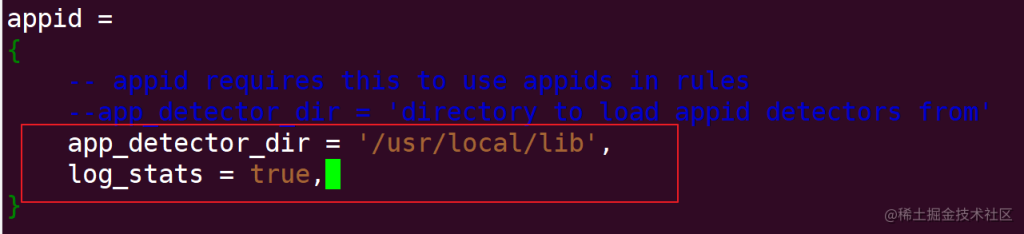
Create a directory where Snort logs are stored
osboxes@osboxes:~$ sudo mkdir /var/log/snort
Check if the snort configuration is correct:
osboxes@osboxes:~$ snort -c /usr/local/etc/snort/snort.lua
o”)~ Snort++ 3.1.16.0
Loading /usr/local/etc/snort/snort.lua:
Loading snort_defaults.lua:
Finished snort_defaults.lua:
……
Finished /usr/local/etc/snort/snort.lua:
pcap DAQ configured to passive.
Snort successfully validated the configuration (with 0 warnings).
o”)~ Snort exiting
The Snort successfully validated configuration (with 0 warnings) message indicates that the configuration file is correct.
Create a custom local ruleset to test Snort.
osboxes@osboxes:~$ sudo vim /usr/local/etc/rules/local.rules
Create a rule for detecting pings with the following:
alert icmp any any -> $HOME_NET any (msg:”ICMP connection test”; sid:1000001; rev:1;)
Test whether the rules are written correctly:
snort -c /usr/local/etc/snort/snort.lua -R /usr/local/etc/rules/local.rules
Then execute the test:
sudo snort -c /usr/local/etc/snort/snort.lua -R /usr/local/etc/rules/local.rules -i ens33 -A alert_fast -s 65535 -k none
Then run the ping command on another machine, ping the snort host, and you can see the output warning message
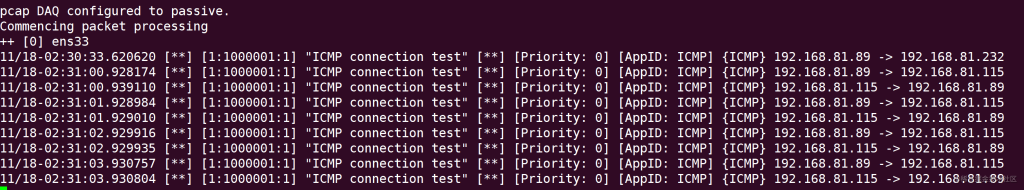
Configure the log output of Snort 3
Modify the snort configuration file and specify whether to output as a file in the Configure outputs section
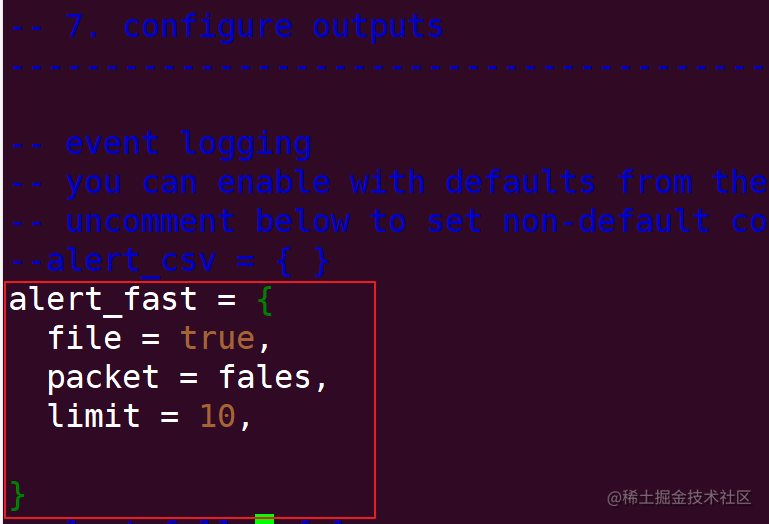
When modified in this way, snort will write to the log to the alert_fast.txt file
Check the configuration:
osboxes@osboxes:~$ snort -c /usr/local/etc/snort/snort.lua
To perform the test, use -l to specify the log directory
sudo snort -c /usr/local/etc/snort/snort.lua -R /usr/local/etc/rules/local.rules -i ens33 -s 65535 -k none -l /var/log/snort/
Warnings are written to the log file:
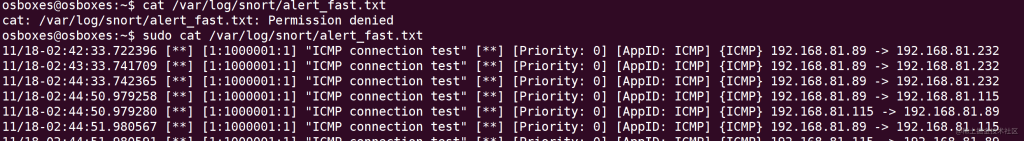
You can write custom rule paths into the snort.lua configuration file
Set Snort to run in service mode
While it is possible to set snort to run in the background using the -D parameter, for more convenience, we can create a systemd service unit for Snort and have Snort run in service mode.
To be on the safe side, create a separate user for snort and set the user shell to nologin
osboxes@osboxes:~$ sudo useradd -r -s /usr/sbin/nologin -M -c SNORT_IDS snort
To create a snort3 service:
osboxes@osboxes:~$ sudo vim /etc/systemd/system/snort3.service
It reads as follows:
[Unit]
Description=Snort 3 NIDS Daemon
After=syslog.target network.target
[Service]
Type=simple
ExecStart=/usr/local/bin/snort -c /usr/local/etc/snort/snort.lua -s 65535 -k none -l /var/log/snort -D -i ens33 -m 0x1b -u snort -g snort
[Install]
WantedBy=multi-user.target
Reload the systemd configuration and modify the /var/log/snort directory permissions.
osboxes@osboxes:~$ sudo systemctl daemon-reload
osboxes@osboxes:~$ sudo chmod -R 5775 /var/log/snort
osboxes@osboxes:~$ sudo chown -R snort:snort /var/log/snort
Start the snort service and configure boot startup
osboxes@osboxes:~$ sudo systemctl enable –now snort3.service
Created symlink /etc/systemd/system/multi-user.target.wants/snort3.service → /etc/systemd/system/snort3.service.
osboxes@osboxes:~$
Check the running status:
If the status is Active: active (running), the service is running normally.
Conclusion on Install and Configure Snort 3 on Ubuntu
At this point, you have finished install and configure Snort 3 on Ubuntu. For more information on how to configure and use the Snort website, please refer to the documentation on the Snort website.



