Why Need Trojan Detection and Prevention
Network security is critical in protecting systems from threats like Trojans. Effective Trojan detection and prevention using packet analysis and firewall configurations can help mitigate attacks and reduce network congestion. This case study highlights how these strategies identified and resolved Trojan-related issues, safeguarding the network from further damage.
Trojan Detection and Prevention in Network Security
Customers reported that the entire company’s network performance was sometimes good and sometimes bad, demonstrating no regular pattern in its fluctuations. When the network stability was good, accessing the website could be either fast or slow.
Topology Analysis
Since we cannot go to the user site, according to the user’s description, they are a small LAN with a single exit, which eliminates Layer 2 loops and Layer 3 routing oscillations; excludes enterprise infrastructure failures (DHCP DNS), and assumes that all devices are working normally.
Since the problem phenomenon is not obvious, we can only capture the packet to analyze the phenomenon and ask the customer network manager to capture the packet on the firewall port on the core switch.
Using Wireshark to analyze, we found that there were as many as 56,109 retransmitted packets, and there were as many as 143,823 packets from server port 445. It was initially determined that the network was stuck due to the retransmission caused by too many packets of this type. (As shown below)
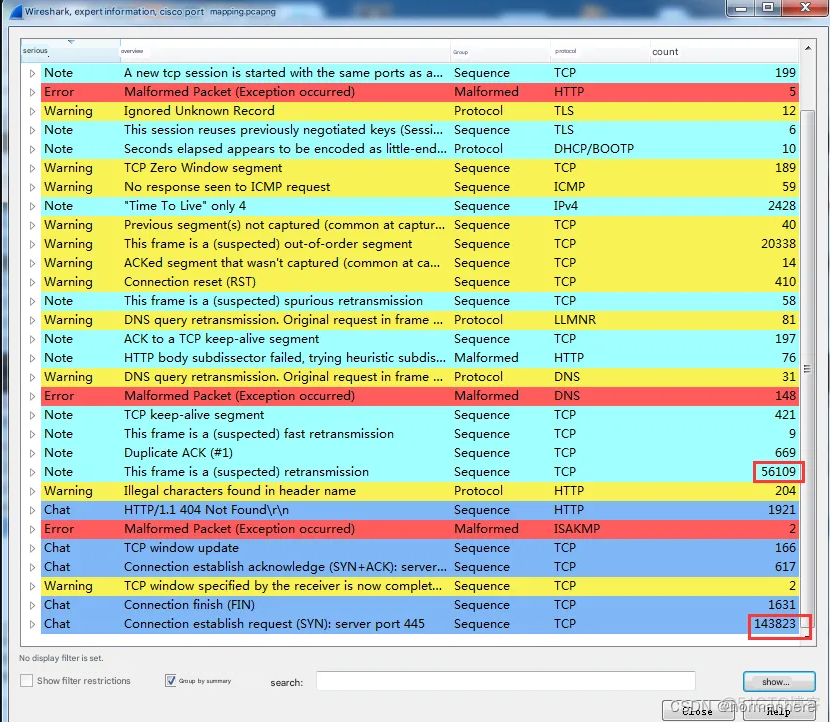
Trojan Detection and Prevention
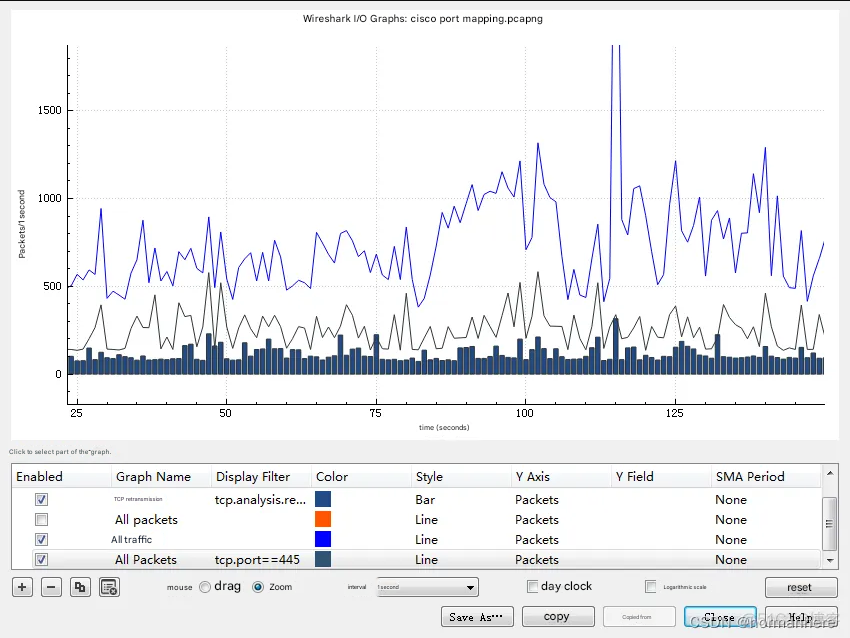
Using I/O chart analysis, TCP.PORT==445 and TCP.ANALISIS.RETRASMISSION is positively correlated. It is the retransmission caused by this type of data packet that causes network congestion.
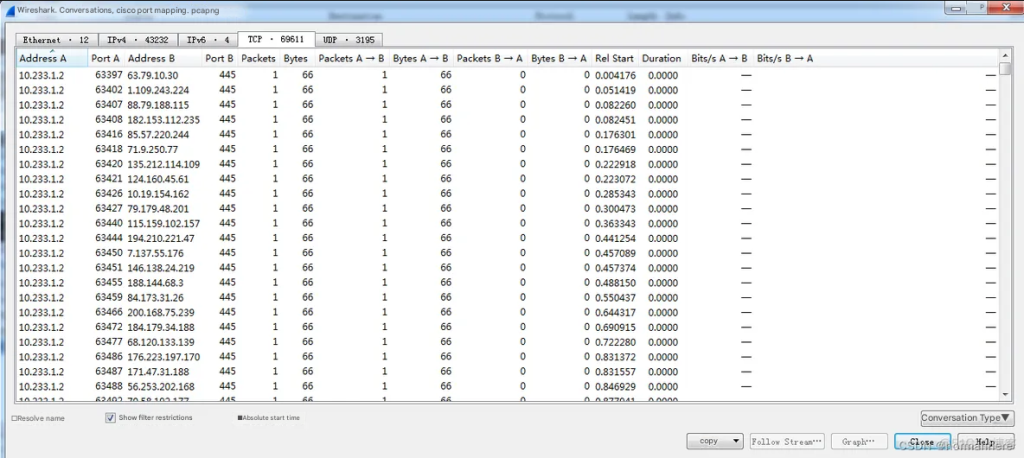
Using conversation statistics, we can see obvious characteristics of Trojans in the intranet host: source ports generated sequentially, the destination IP of the Trojan client scanned according to the list, the destination port is 445, the byte size is a fixed 66 bytes, a large number of concurrent connections in a short period of time, but most of the Trojan clients are offline.
Preliminary judgment shows that many hosts in the intranet have been infected by Trojans such as Super Rabbit.
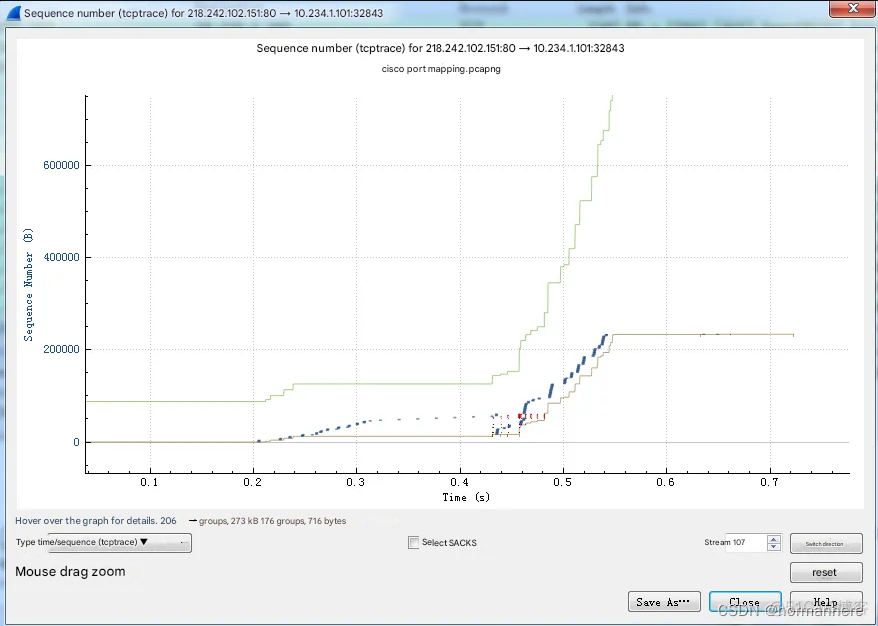
This is a normal TCP sequence of a client requesting to download a picture. As you can see, many retransmissions occurred, resulting in an extremely slow speed.
The Trojan client at 139.199.19.197 has connected to a zombie on the intranet and started trying to connect anonymously.
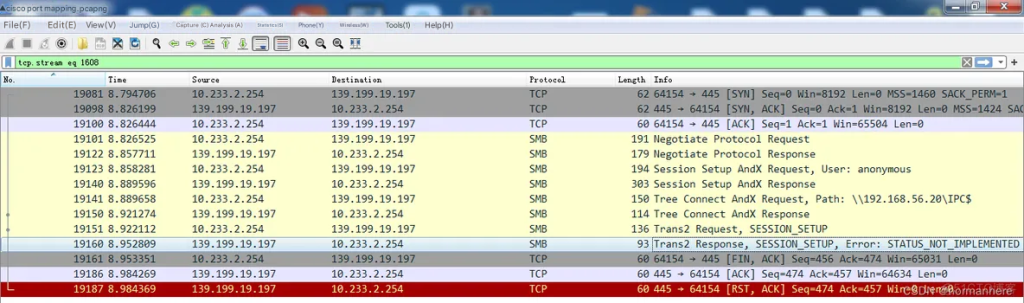
The Trojan client begins to guess the username and password. It is initially determined that the Trojan client is currently invading the intranet shared folders on a large scale (especially the shared folders shared to anyone and the default shared folders of the default system).
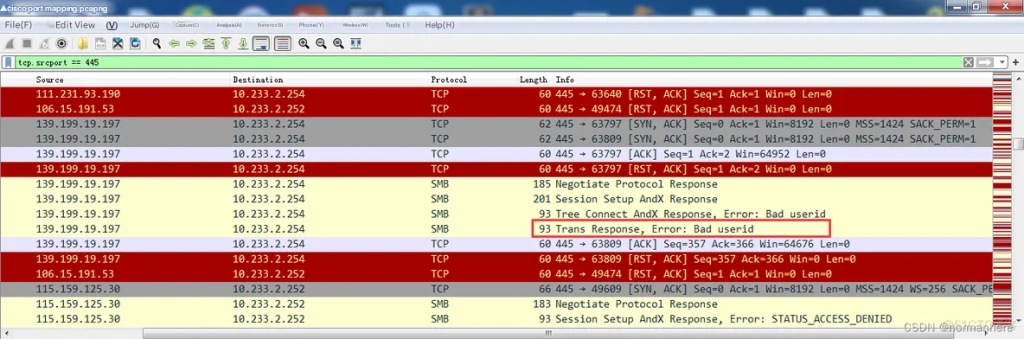
Conclusion
The suggestion given is
- Create an ACL on the Layer 3 switch to block all packets with a destination port of 445 and apply it to all access layer ports, or create a VACL call on the VLAN gateway to alleviate the congestion caused by too many packets of this type entering the network.
- Then make a policy on the firewall to prohibit traffic from port 445 from entering the intranet, blocking the Trojan client from manipulating the zombies.
- Then disinfect all suspicious hosts listed in the conversation.
The crisis is resolved
This case illustrates:
- If the security device is not configured properly, it will not be able to play a security role and will be useless. By default, all external network access ports to the internal network must be closed, and only necessary ports are allowed to be opened. In addition, a 7-layer or 3-layer ACL is required to restrict the login of external IP addresses, and AAA deployment is required.
- Improve the security of the intranet, implement AD domain control, assign permissions to shared folders, and use domain control firewall policies to close non-essential ports.
- Most of the time, network administrators only call for help after an accident occurs, which is too late. It is necessary to deploy IPS and related alarm equipment to remind administrators when suspected attacks occur on the intranet to avoid the expansion of harm.
- Preserve evidence. If damage has already occurred, it is necessary to collect host logs and data packet evidence as legal evidence.


