1. Introduction
Wireshark acts like a microscope in the network world, providing us with the ability to understand everything occurring within a network. Previously, I demonstrated how to use Wireshark for TLS Protocol Analysis to capture HTTPS packets from QQ Music, discussing ways to remove the encrypted shell of HTTPS. This time, we will delve into the Wireshark-analyzed handshake process of the HTTPS protocol, with the hope that everyone can gain an understanding in case of an emergency.
2. HTTPS protocol handshake overview
This time, we will still use Wireshark to capture HTTPS packets of QQ Music as an example.
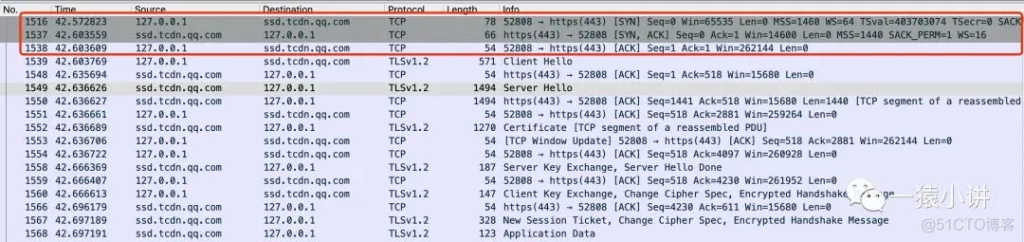
From the above picture, we can see that the HTTPS handshake is based on TCP. First, the TCP three-way handshake is performed (I have shared it before, if you are interested, you can check the historical tweets to reminisce), and then the TLS connection is established. The following will focus on the TLS handshake process (HTTPS = HTTP + TLS/SSL).
We can use the “Statistics|Flow Graph” function provided by Wireshark to display the flow chart of the HTTPS protocol handshake, as shown in the figure below.
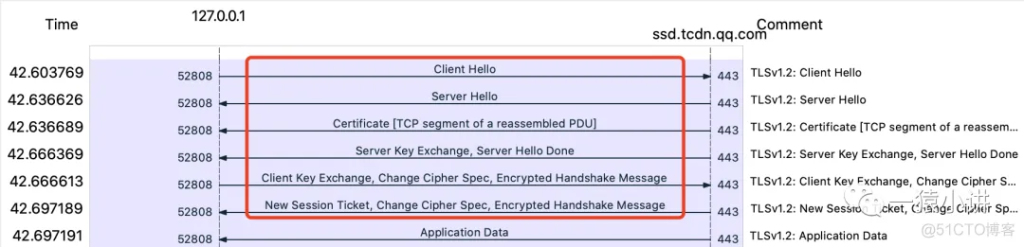
We can also use the “display filter” function provided by Wireshark to filter out the TLS handshake packets of interest, as shown in the figure below.
Through the two screenshots above, we can sort out several important steps of the HTTPS protocol handshake.
Step 1: The client sends a Client Hello to the server
Step 2: The server returns a Server Hello to the client
Step 3: The server returns a Certificate to the client
Step 4: The server returns Server Key Exchange, Server Hello Done to the client
Step 5: The client sends Client Key Exchange, Change Cipher Spec, Encrypted Handshake Message to the server
Step 6: The server returns New Session Ticket, Change Cipher Spec, Encrypted Handshake Message to the client
3. HTTPS protocol handshake analysis
The HTTPS handshake process can be seen very clearly with the help of Wireshark. Next, we will analyze it layer by layer in an onion-peeling manner.
Step 1: Client Hello
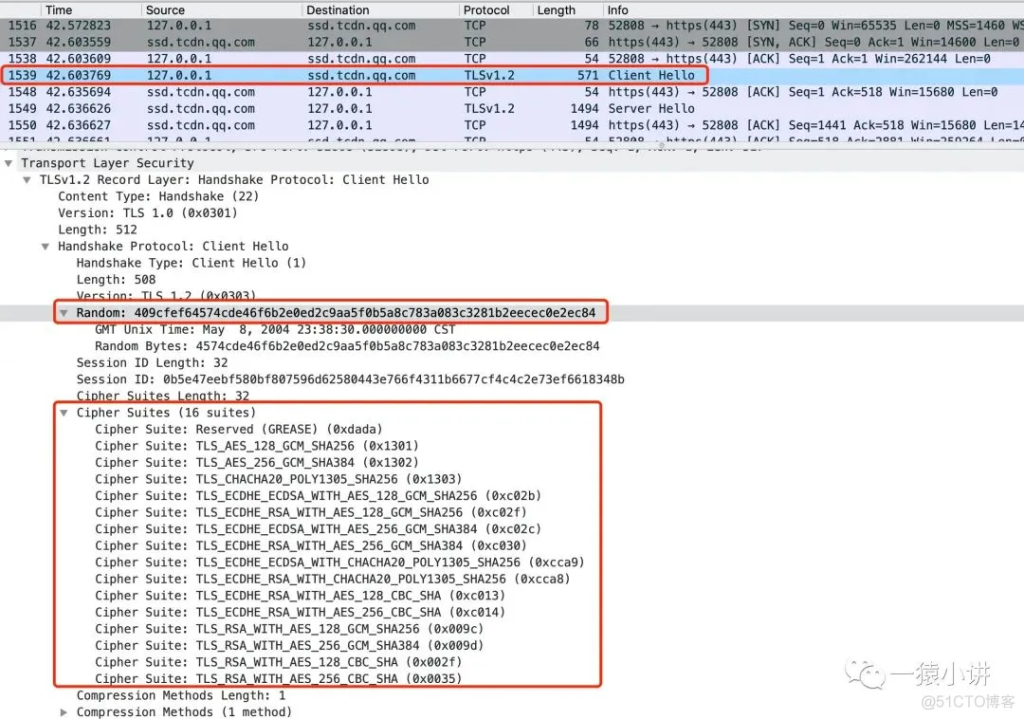
Through Wireshark packet capture analysis, as shown in the figure above, the Client Hello stage is mainly for the client to tell the server the version number of the TLS protocol supported by the client, the encryption suite supported by the client, the compression method supported by the client, and a random number generated by the client.
Step 2: Server Hello
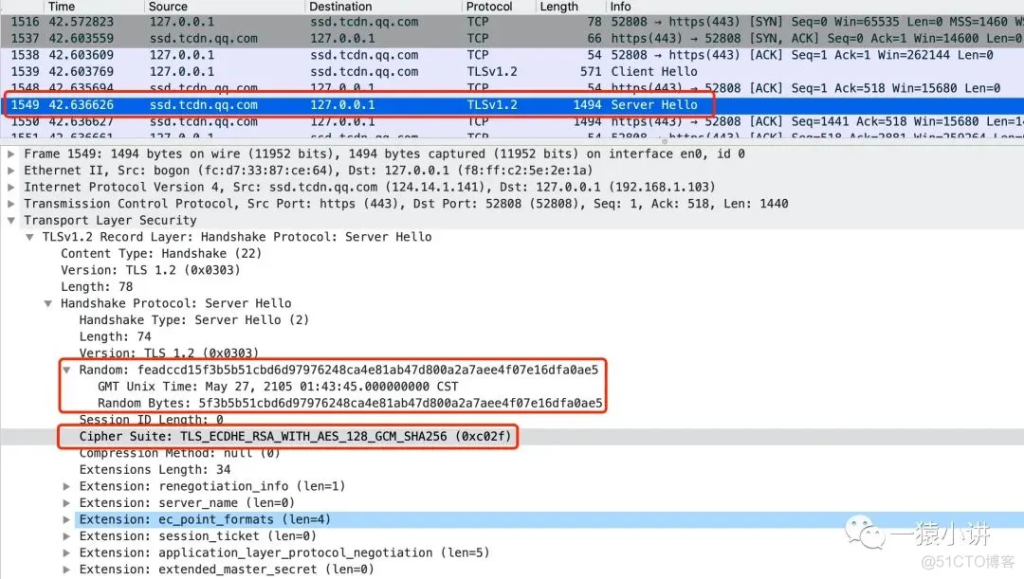
Through packet capture analysis, as shown in the figure above, the server mainly determines the SSL/TLS protocol version to be used based on the relevant information supported by the client; determines which encryption suite and compression method to use; and generates a random number Random.
Step 3: Certificate
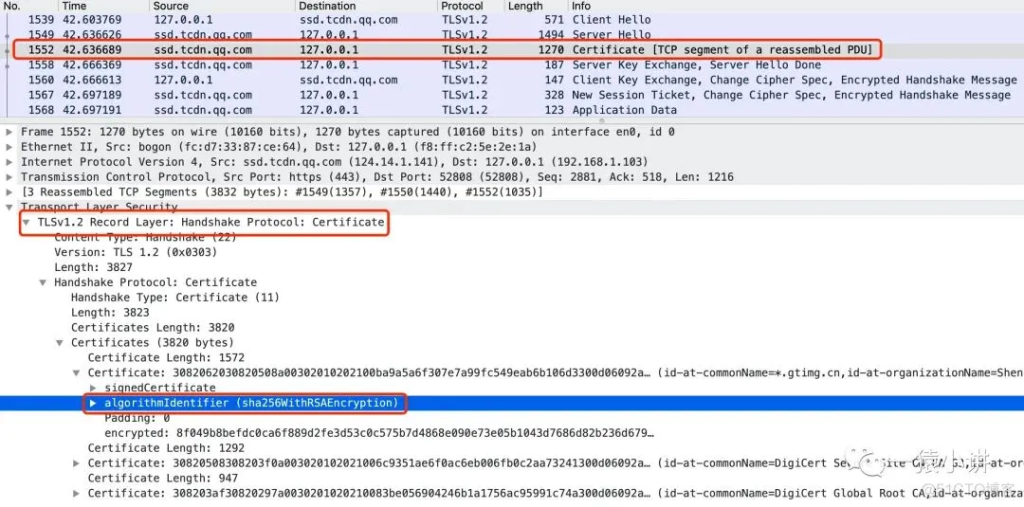
This step mainly involves the server sending the certificate to the client.
Step 4: Server Key Exchange, Server Hello Done
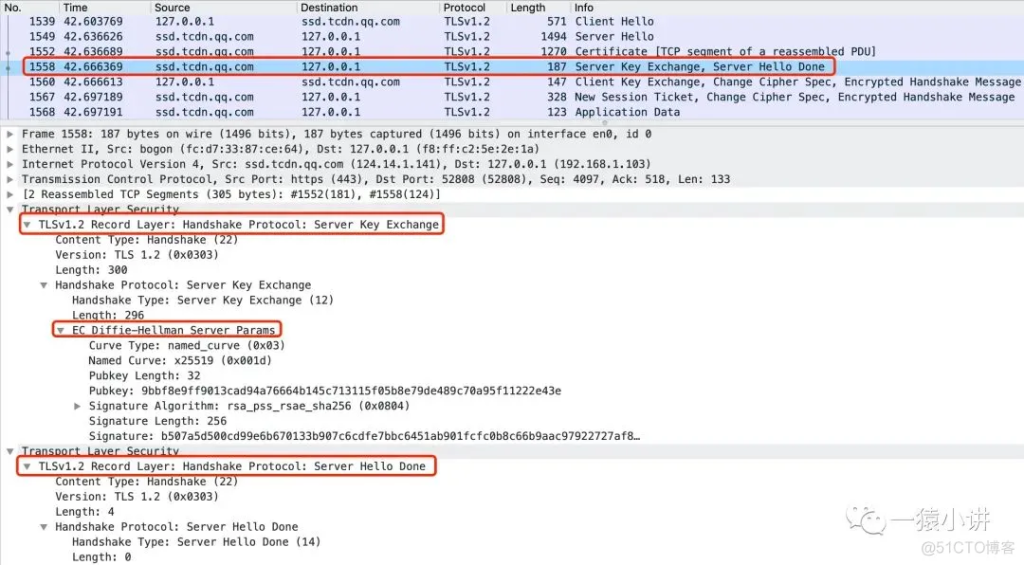
Server Key Exchange: This message is sent by the server to the client to send key exchange algorithm related parameters and data. Commonly used key exchange algorithms include RSA, DH, ECDH, etc.
Server Hello Done: The server tells the client that the message has been sent.
Step 5:
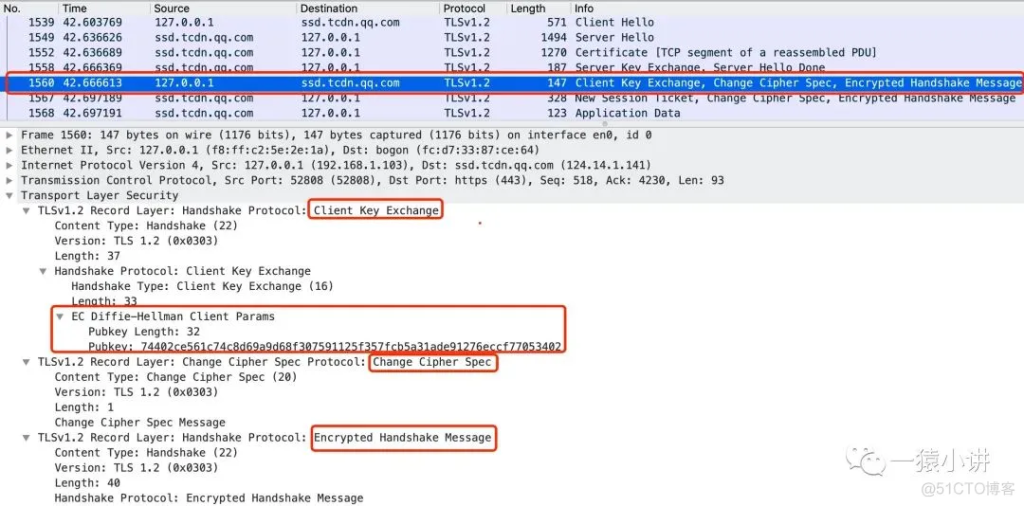
Client Key Exchange: This message is used to exchange secret key parameters, generate a pre-master key, and then pass this key to the server. The server will decrypt the key with its own private key to obtain the third random number, and then generate a communication key.
Change Cipher Spec: This message tells the server that all subsequent communications will be encrypted using the negotiated key.
Encrypted Handshake Message : The client generates a summary of the previous handshake message and then encrypts it with the negotiated key. If the server can decrypt it after receiving it, it means that the previously negotiated key is consistent.
Step 6:
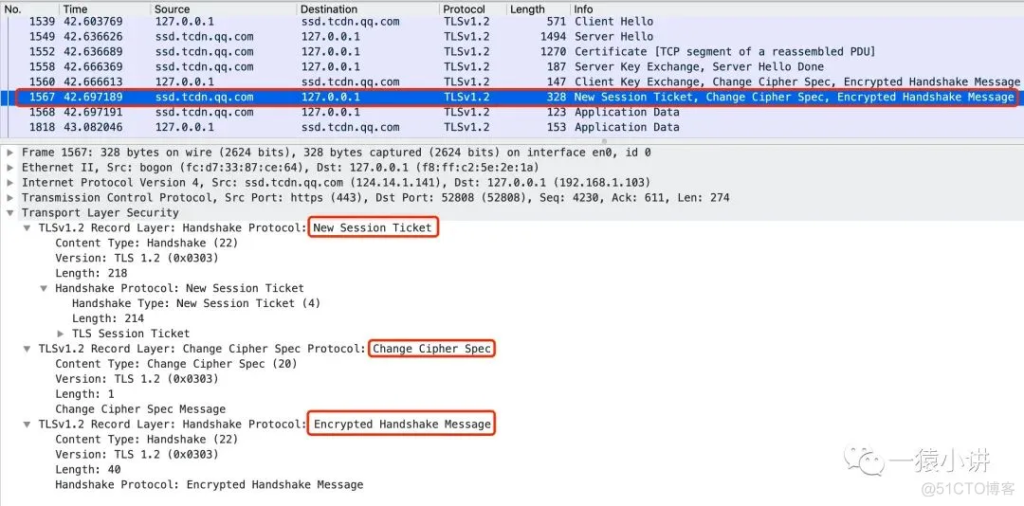
New Session Ticket: Contains the information needed for encrypted communication, which is encrypted with a key known only to the server. The goal is to eliminate the need for the server to maintain a session state cache for each client.
Change Cipher Spec: This message tells the client that all subsequent communications will be encrypted using the negotiated key.
Encrypted Handshake Message: The server generates a summary of the handshake message and then encrypts it with the secret key. This is the first encrypted message sent by the server. After receiving it, the client will decrypt it with the secret key. If it can be decrypted, it means that the negotiated secret key is consistent.
At this point, the TLS handshake is complete, and the next step is data transmission. HTTPS data transmission is shown in the figure below.
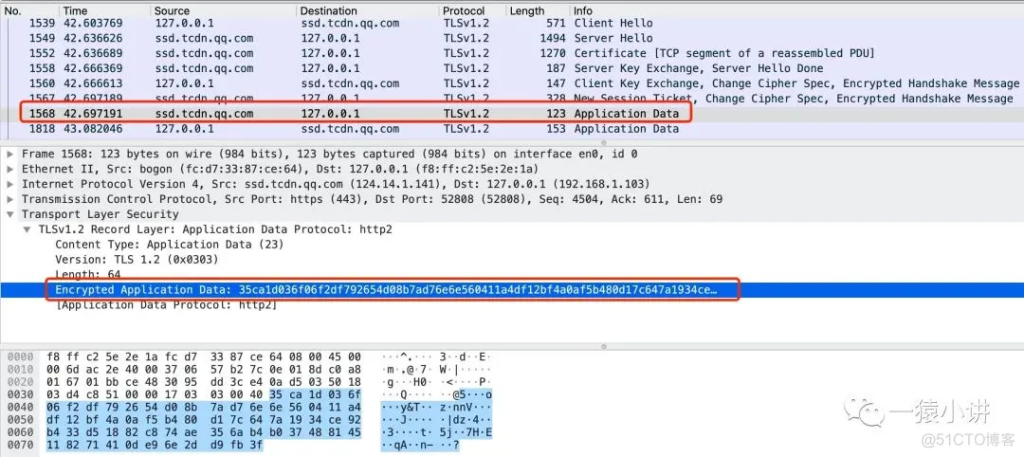
4. Summary
This content offers a comprehensive guide to understanding the HTTPS protocol handshake process through the lens of TLS Protocol Analysis using Wireshark, comparing Wireshark to a microscope for network analysis. Initially, the document revisits earlier work on decrypting HTTPS traffic from QQ Music before shifting focus to examining the HTTPS handshake process in detail. The overview begins by explaining that the HTTPS handshake is built on the TCP three-way handshake and continues with the intricate details of the TLS handshake. Key steps include the Client Hello, Server Hello, Certificate exchange, Server Key Exchange, and subsequent confirmation steps utilizing Change Cipher Spec and Encrypted Handshake Messages. Clear graphics and Wireshark screenshots support this analysis, facilitating an easier understanding of these steps. In summary, the guide aims to help readers thoroughly grasp the TLS handshake through detailed packet capture and analysis, leveraging Wireshark’s tools like “Statistics|Flow Graph” and display filters to effectively sort and scrutinize network packets. The process concludes with the initiation of encrypted data transmission, indicating the successful establishment of a secure connection. This systematic breakdown serves as a practical resource for users to efficiently troubleshoot or analyze network communications through TLS Protocol Analysis.



