1. Packet capture filter
BPF Syntax:
- type: host, net, port
- dir (direction): src, dst
- proto(protocol): ether, ip, tcp, udp, http, ftp
- Logical operators: &&, ||, !
example:
1) src host 192.168.1.1 && dst port 80 captures traffic with source address 192.168.1.1 and destination port 80
2) host 192.168.1.1 || host 192.168.1.2 captures the traffic of 192.168.1.1 and 192.168.1.2
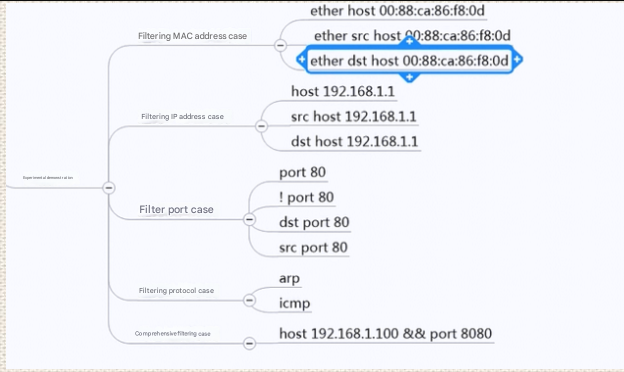
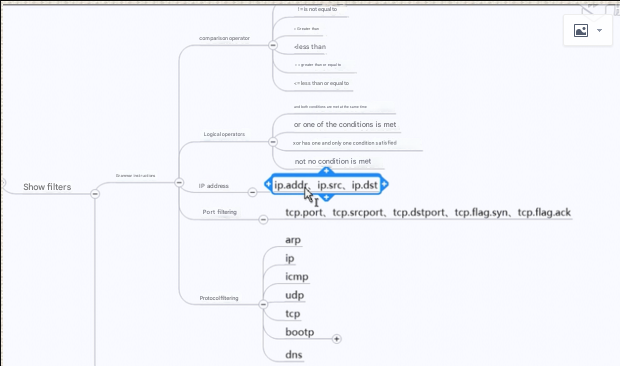
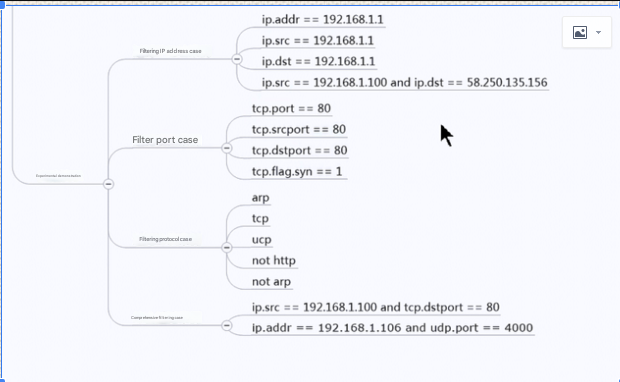
2. Display Filters
3. How to capture local localhost packets with WireShark
WireShark can only capture packets that pass through the computer’s network card. Since I used localhost or 127.0.0.1 for testing, the traffic does not pass through the computer’s network card, so WireShark cannot capture packets. The solution is as follows: 1. Open the command prompt as an administrator 2. Enter route add local ip mask 255.255.255.255 gateway ip (can be viewed through ipconfig) 3. Replace localhost or 127.0.0.1 in our program with the local ip 4. Use WireShark to capture local packets Note: After the test, use route delete local ip mask 255.255.255.255 gateway ip to delete our above changes, otherwise all the packets from our local machine will pass through the network card first and then return to the local machine, which will consume performance.



