2. Attacks Behavioral Analysis
2.1. Beast Mail Server
A zombie machine, often referred to as a puppet machine, is a device that hackers can control remotely. When transformed into a zombie machine, it becomes a tool for attackers, participating in activities such as data theft, launching additional attacks, like Brute Force Attack Prevention circumvention, or causing sabotage. In the following, we will use WireShark to explore how a zombie machine can be utilized as an advertising spam distribution station.
2.1.1 Problems
When conducting security testing on a certain enterprise server group, we found that one of the customer’s servers (10.190.214.130) was abnormal. Judging from its communication behavior, it should be an idle server. After a period of packet capture and data statistics, we found that most of them were SMTP protocols.
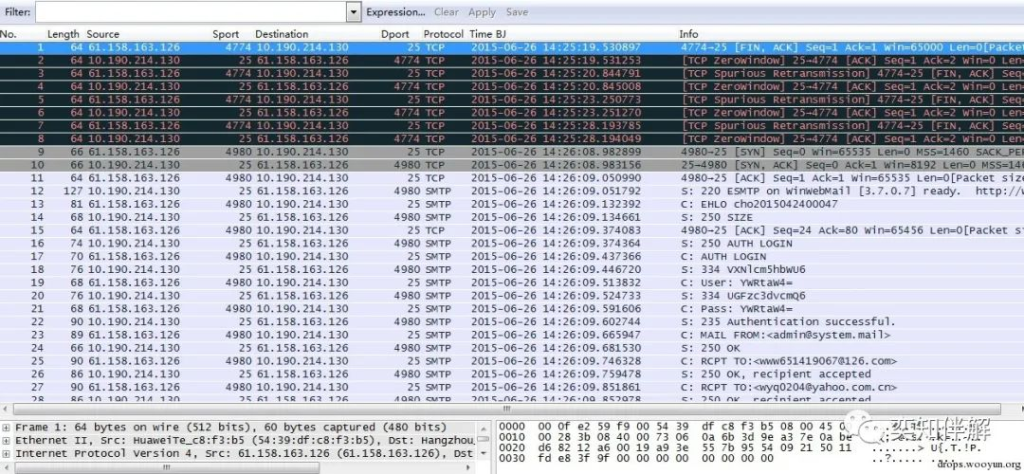
SMTP is an email transmission protocol. Normally, there are two situations in which this protocol appears:
“`
1. Generated when a user sends an email.
2. Normal communication with the mail server occurs.
“`
This IP address belongs to the server, so it is definitely not an individual user using a PC to send emails.
So is this a mail server? If so, why only SMTP protocol, POP3, HTTP, IMAP, etc?
With doubts, we counted the IP, port and other information of the data:

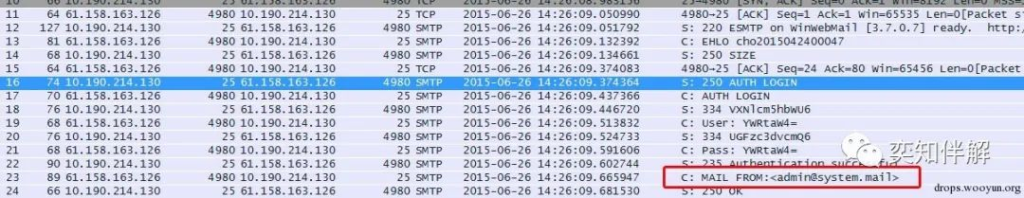
From the data, we can see that the email login is successful. Right-click Follow TCPStream to see the complete login information.

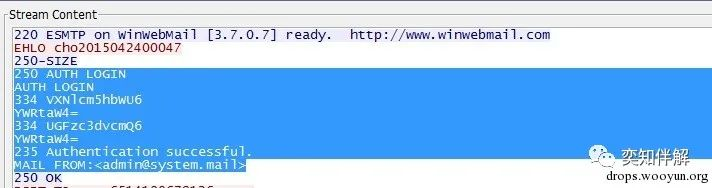
“`
334 VXNlcm5hbWU6 // Base64 decoded to: “Username:”
YWRtaW4= //Username entered by the user, Base64 decoded to: “admin”
334 UGFzc3dvcmQ6 //Base64 decoded to: “Password:”
YWRtaW4= //The password entered by the user, Base64 decoded to: “admin”
235 Authentication successful. //Authentication successful
MAIL FROM:<[email protected]> //Mail sent from…
“`
This data shows that 61.158.163.126 successfully logged into the mail server 10.190.214.30 through the SMTP protocol using the username admin and password admin. The domain name of the mail server is @system.mail, and [email protected] is used to send mails.
As soon as I looked at the username, password, and email address, I found the problem:
> 1. The admin account is generally not managed through Internet login.
>
> 2. Only stupid administrators will set the admin account as a password.
>
> 3. The domain name @system.mail has nothing to do with the customer.
Obviously, this is a controlled mail server – a “zombie mail server”.
2.1.2 Behavior Tracking
The problem has been discovered. The next step is to track its behavior and find out what this zombie server is doing. Checking the complete information of Follow TCPStream, we can find that this is a mass email sent by [email protected]. The recipients include: [email protected], [email protected], [email protected] and other 10 people (the mailbox with QQ is temporarily deleted, the reason is shown at the end), and the email content is not much.
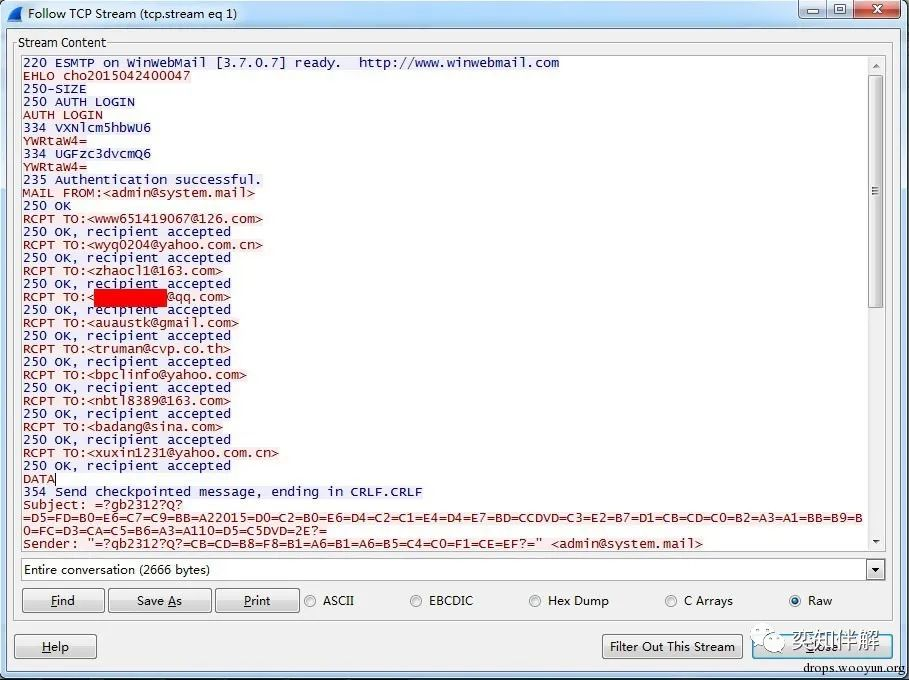
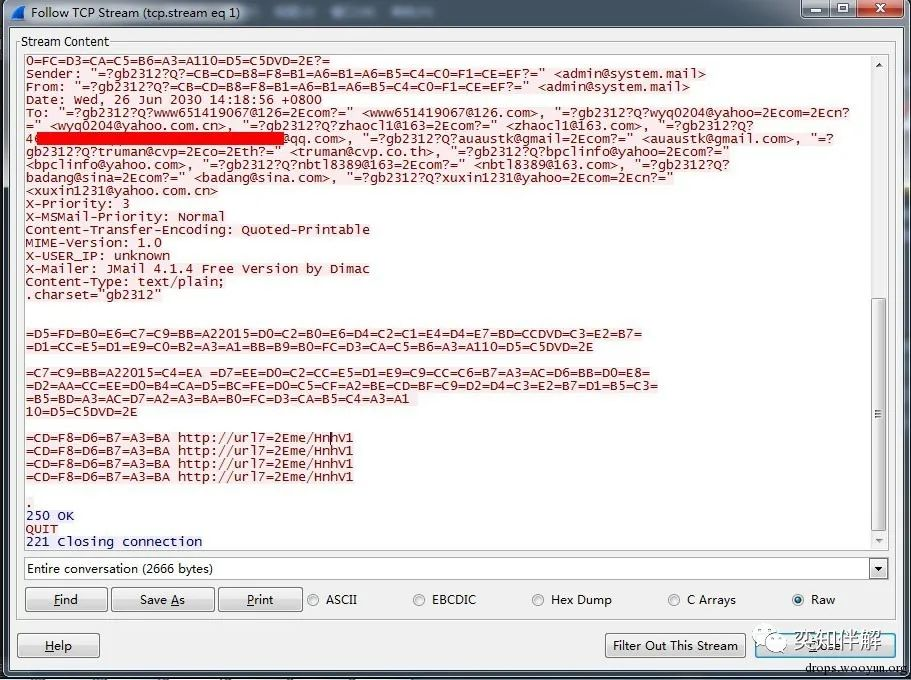
To see the complete email content, we can click Save As to save it as X.eml and open it with an email client such as Outlook.
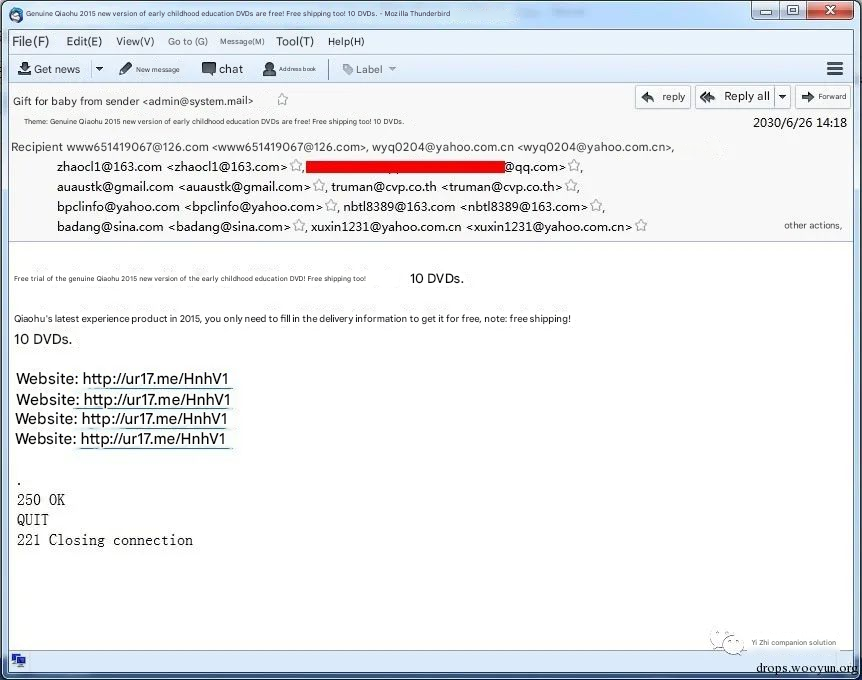
2.1.3 Analysis Conclusion
1. After a simple detection, the server opened a large number of high-risk ports such as TCP25/110/445/135/3389/139, so it was inevitable that it would be attacked and controlled.
2. The server has been controlled to create a zombie mail server (WinWebMail), the mail server domain name is @system.mail, and it is logged in by 61.158.163.126 (Sanmenxia City, Henan Province) using the [email protected] user to send spam through mail clients or special software.
3. A simple search on Baidu shows that many people often receive spam from [email protected]. Today I finally figured out the whole story.
4. Spam emails are not sent randomly, but are very targeted.
2.2. Bodisparking malicious code
2.2.1 Problems
We received a security request and conducted a security analysis on the hosts in the Internet office area. When analyzing the communication data of a certain host, we filtered the HTTP protocol.
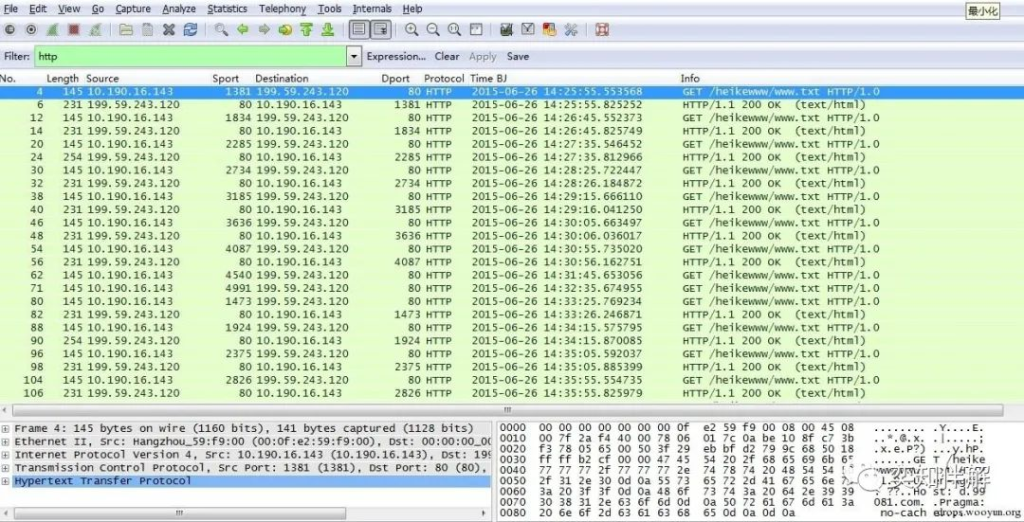
When I looked at the data, I found something unusual. There was not much HTTP data on this host, but a large number of HTTP requests were “Get heikewww/www.txt”. The problem was certainly not caused by the pinyin “heike”. Click “Info” to arrange it, and you can see it more clearly. You can also see that the request interval is about 50 seconds.
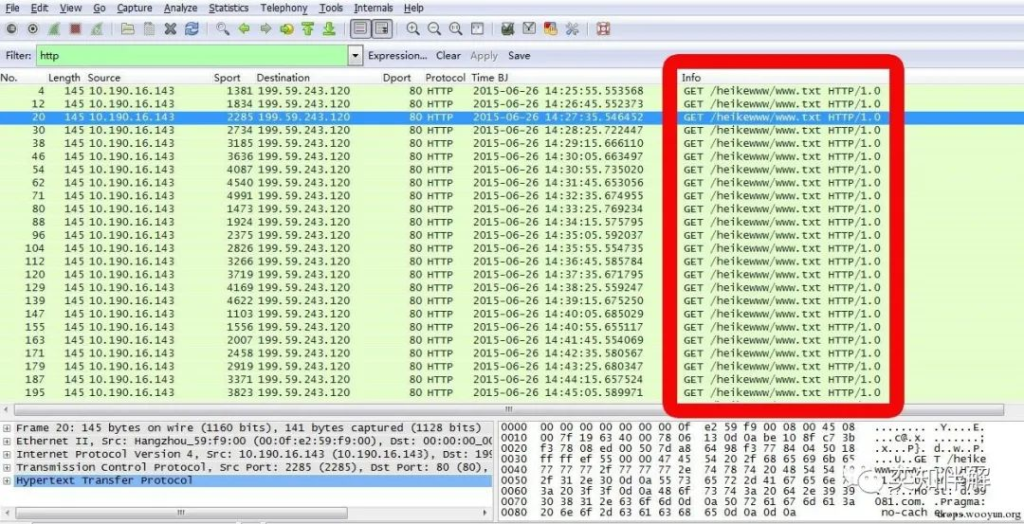
To analyze the requested URLs more accurately, select Statistics, HTTP, and Requests in the menu. You can see that there is only one URL requested: “d.99081.com/heikewww/www.txt”, which was requested 82 times in a short period of time.

This kind of regular and long-term HTTP communication behavior of requesting the same domain name is generally either fraud or theft.
1. Treachery: Many antivirus software, apps, and commercial software will periodically connect to their servers via HTTP or other protocols to maintain a long connection. This is done to provide online services, monitor upgrades, etc., but it can also monitor your computer and mobile phone and steal your information.
2. Theft: In order to monitor whether the puppet host is online, malware such as Trojans and viruses will have a heartbeat mechanism, which is to connect to its zombie server through HTTP or other protocols. Once you are online, they can control you at any time.
Let’s filter the DNS protocol and see.
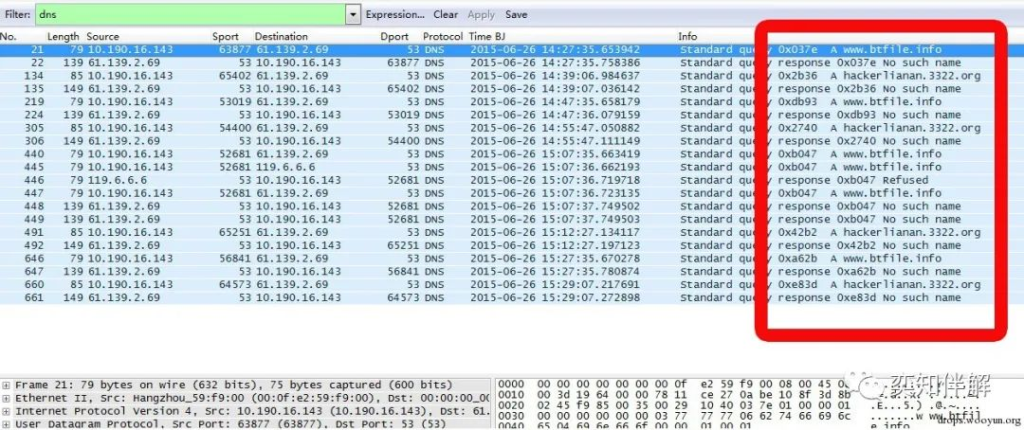
It can be seen that there is no related request for the domain name “d.99081.com” in the DNS request. There are many methods and techniques for Trojan virus communication without DNS resolution. Readers who are interested can search and learn by themselves. Therefore, as a security monitoring device, monitoring based only on DNS is completely insufficient.
Next, let’s look at the specific content of the HTTP request. Click on a packet of HTTP GET data and you can see that the full domain name of the request is “d.99081.com/heikewww/www.txt”, and it keeps getting the www.txt file.
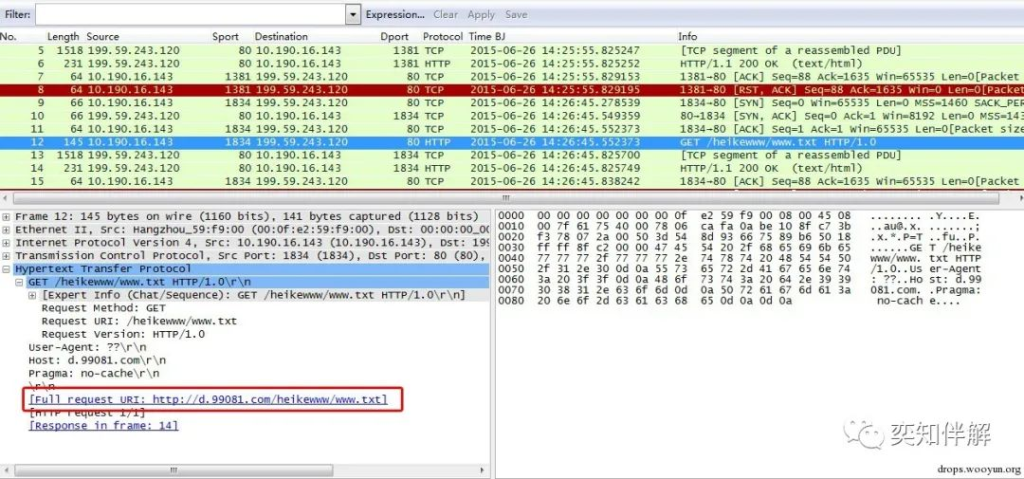
Follow TCPStream and you can see all the malicious codes in www.txt.

2.2.2 Associated Behavior
At this point, it is basically confirmed that the malicious code is running on the host 10.190.16.143. It will communicate with the IP address 199.59.243.120 (domain name d.99081.com) through the HTTP protocol at a fixed time, and download and run the above /heikewww/www.txt.
So, are there other hosts that have been affected?
This problem is easy to solve. The prerequisite is to monitor the traffic of the entire network for a period of time, and then see which other hosts are communicating with the IP (199.59.243.120). If the domain name is a dynamic IP, it needs to be resolved again.
- If the packet capture file is only a PCAP file, just filter “ip.addr==199.59.243.120”.
- The overall network traffic rate is generally high, so it is unlikely to be saved as a single packet. If there are a large number of PCAP files, batch filtering can also be achieved through WireShark.
Based on this case, let’s take a look at the usage of “tshark.exe” in WireShark and use it to implement batch filtering.
Tshark needs to be used in a command line environment. A single filtering command is as follows:
Code language: javascript
copy
cd C:\Program Files\Wireshark
tshark -r D:\DATA\1.cap -Y "ip.addr==199.59.243.120" -w E:\DATA\out\1.capExplanation: Go to the WireShark directory first, call the tshark program, -r followed by the source directory address, -Y followed by the filter command (consistent with the Filter rules in Wireshrk), -w followed by the destination address.
With this command, you can write batch processing to filter a large number of PCAP packages in a folder.
In this way, all communication data of IP address 199.59.243.120 is filtered.
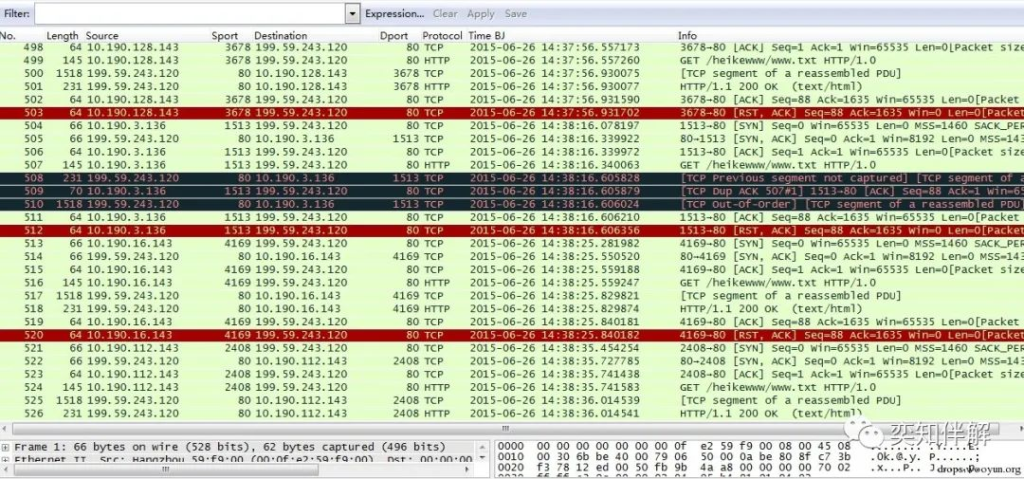
Statistics of communication IP.
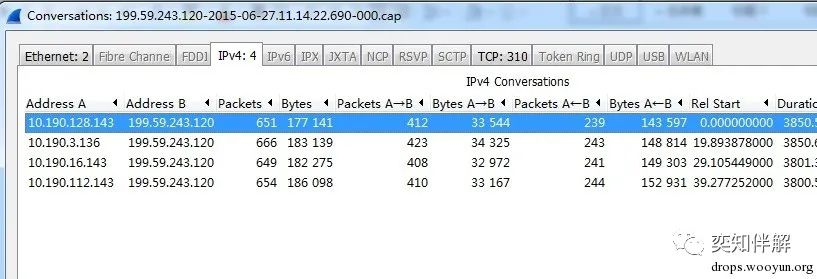
According to the statistical results, it can be found that 4 hosts in the entire network have been infected by the same malicious code. All communication contents are the same, but the request time intervals are slightly different, some are 50 seconds, and some are 4 minutes.
2.2.3 In-depth analysis
**1 Source of malicious code**
We found the URL “/Zm9yY2VTUg” in www.txt, and after opening it, we found that it was full of sponsored ads and other spam information. As shown below:
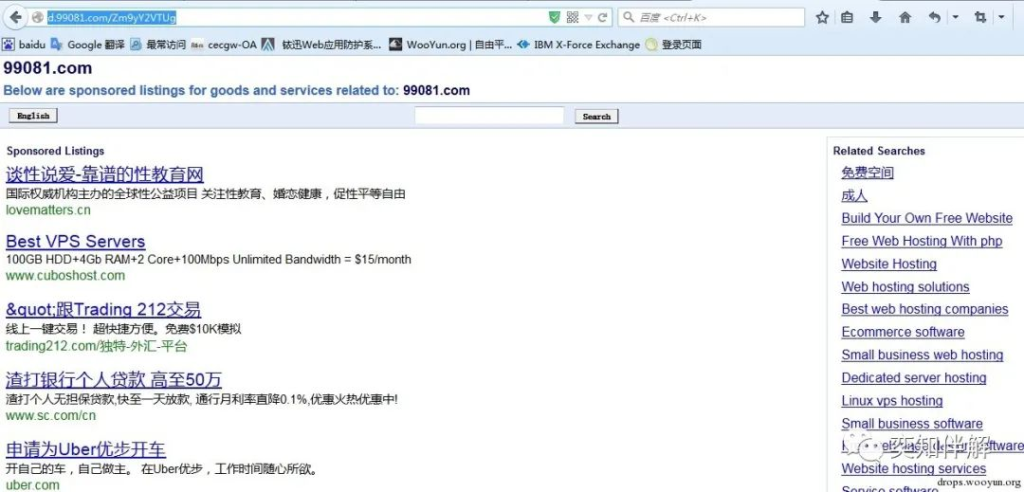
**2 Malicious code behavior**
Through information from public channels, we learned that Bodis.com is a domain name parking service provider that has been operating for many years. It mainly relies on Internet advertising to obtain income. Whether it has engaged in illegal online activities remains to be analyzed.
99081.com is a registered user of Bodis.com, i.e. a domain parking user. It gets its share of profits by displaying Bodis.com ads and attracting users to click on them. Our preliminary analysis shows that 99081.com uses system vulnerabilities or software bundling to install and run malicious code on a large number of victims’ computers to access its domain parking website, and gets a share of Bodis.com’s profits by generating a large amount of traffic to 99081.com. Usually, this behavior will be considered cheating by domain parking service providers, and once discovered, there will be a heavier penalty.
2.2.4 Analysis Conclusion
1. Attackers use domain names to park website ads through illegal means to make money, but their methods are not professional enough;
2. The attack method should be through website Trojans or software bundling, etc. People who visit the Trojan-infected website and download and execute the bundled software can easily become victims;
3. The malicious code continuously accesses the domain parking website through the HTTP protocol, and the attacker makes money through the traffic generated by the malicious code.
2.3. Brute force attack
Brute force cracking is to use brute force to try to guess the password in large quantities. There are generally three ways to guess the password:
**1. Permutation and combination**: First list the possible password combinations, such as numbers, uppercase letters, lowercase letters, special characters, etc.; gradually guess the password length from 1 digit, 2 digits, etc. Of course, this method requires high-performance cracking algorithms and CPU/GPU support.
**2. Dictionary cracking**: Most attackers do not have high-performance cracking algorithms and CPU/GPU. To save time and improve efficiency, they use social engineering or other methods to build a decryption dictionary and use the usernames and passwords in the dictionary to guess the passwords.
**3. Combination of permutations and combinations + dictionary cracking** In theory, most passwords can be cracked as long as you have a powerful enough computer and enough time.
Brute force cracking generally has two application scenarios:
1. Before the attack, try to crack whether the user has a weak password or a regular password; if so, the entire attack will be more effective.
2. After a large number of attacks, if there are no loopholes or weak links in the user’s network system, then the only option is to use brute force to crack the system in the hope of obtaining weak or regular passwords. Therefore, it is very dangerous for users, especially administrators, to set weak or regular passwords, which may become the “stepping stone” or “last straw” for hacker attacks.
Brute force cracking has a wide range of applications. It can be said that any entry that requires login can be attacked using brute force cracking. Application level includes: web pages, emails, FTP services, Telnet services, etc., and protocol level includes: HTTP, HTTPS, POP3, POP3S, IMAP, IMAPS, SMTP, SMTPS, FTP, TELNET, RDP, QQ, MSN, etc. This article only lists some common protocols, and other protocols are similar.
2.3.1 Normal login status
To identify brute force attacks from the communication data level, we must first understand the data formats of normal logins of various protocols. Let’s take a look at the common data formats of the POP3/SMTP/IMAP/HTTP/HTTPS/RDP protocol authentication process. The formats are slightly different depending on the server type. (Note: The server environment used in this chapter is Exchange2003 and WampServer)
1. POP3 protocol
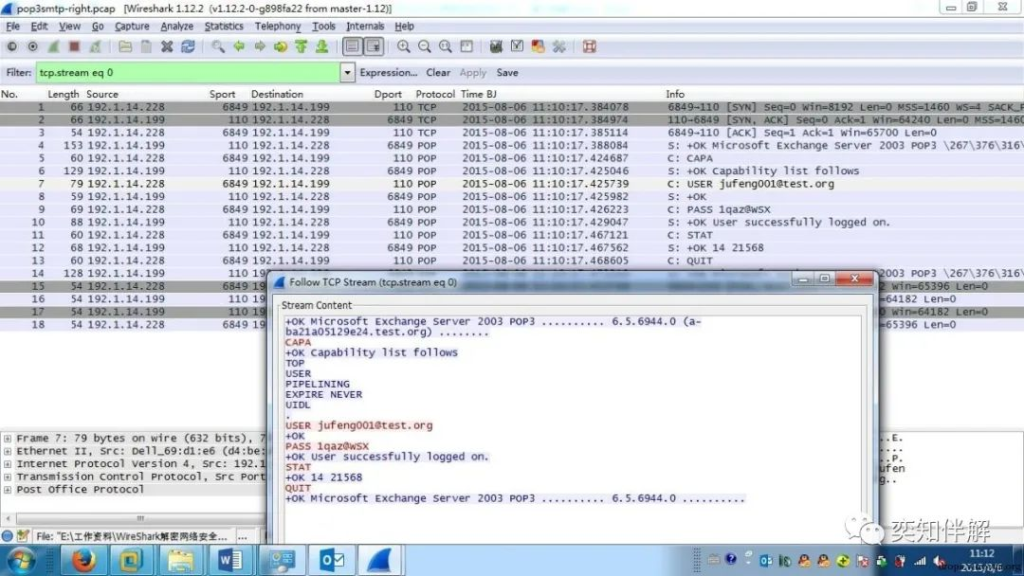
“`
+OK Microsoft Exchange Server 2003 POP3 ………. 6.5.6944.0 (a-ba21a05129e24.test.org) …….. //Server is ready
CAPA //Used to obtain the function option list of this server
+OK Capability list follows
TOP
USER
PIPELINING
EXPIRE NEVER
UIDL
.
USER [email protected] //Send account name to POP3 Server
+OK
PASS 1qaz@WSX //Send password to POP3 Server
+OK User successfully logged on. //Authentication successful
STAT
+OK 14 21568
QUIT
+OK Microsoft Exchange Server 2003 POP3 ……. 6.5.6944.0 …….
“`
2. SMTP protocol
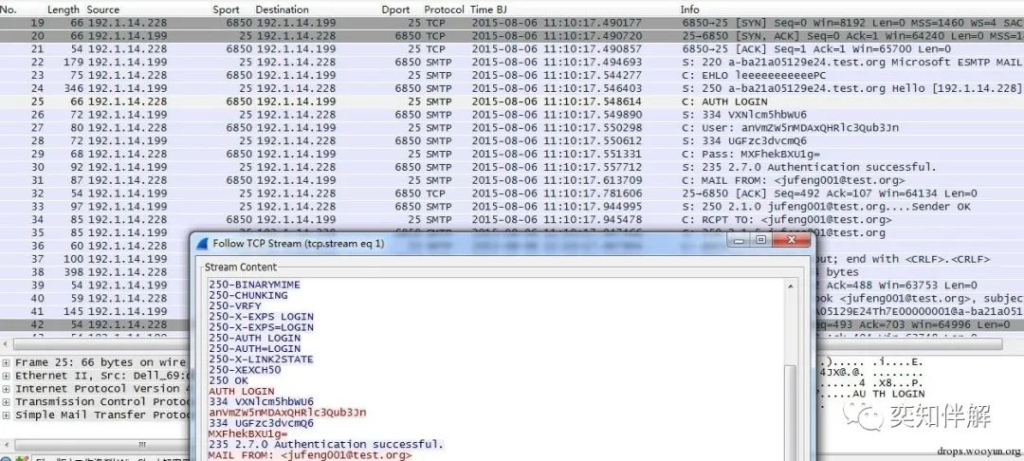
“`
220 a-ba21a05129e24.test.org Microsoft ESMTP MAIL Service, Version: 6.0.3790.3959 ready at Thu, 6 Aug 2015 11:10:17 +0800 //Service ready
EHLO Mr.RightPC //Host name
250-a-ba21a05129e24.test.org Hello [192.1.14.228]
…
250 OK
AUTH LOGIN //Authentication starts
334 VXNlcm5hbWU6 // Username:
anVmZW5nMDAxQHRlc3Qub3Jn // Input the base64 encoding of the user name
334 UGFzc3dvcmQ6 // Password:
MXFhekBXU1g= //Enter the base64 encoding of the password
235 2.7.0 Authentication successful. //Authentication successful
“`
3. HTTP protocol
There are many HTTP protocol authentication formats, only one is listed here for reference.
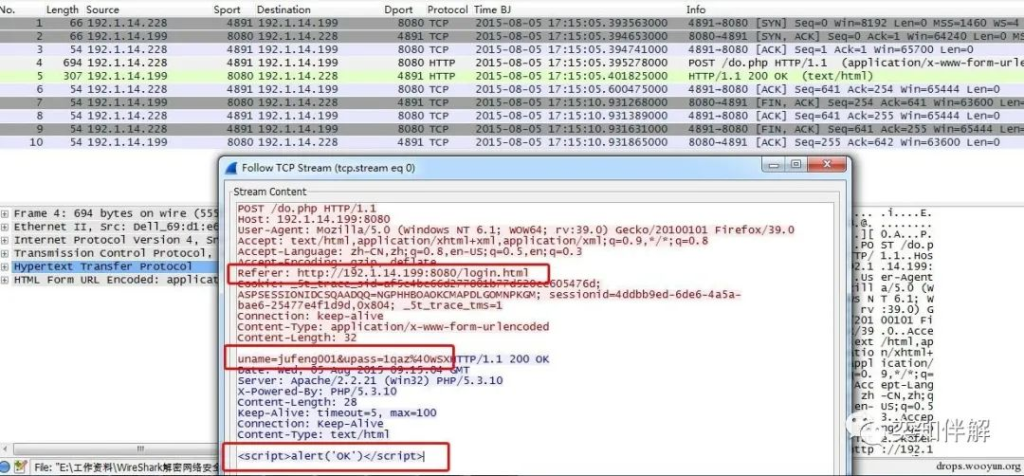
“`
Referer: http://192.1.14.199:8080/login.html //Login address
uname=jufeng001&upass=1qaz%40WSXHTTP/1.1 200 OK
…
<script>alert(‘OK’)</script>
//Enter the user name jufeng001 and the password 1qaz%40WSX. The Web server returns HTTP/1.1 200 and a dialog box “OK” pops up, indicating that the authentication is successful.
“`
4. HTTPS protocol
HTTPS is an encryption protocol. It is difficult to determine whether the authentication is successful from the data. It can only be determined based on the data header combined with social engineering. For example, if there are steps to view web pages or emails after authentication, encrypted data will be generated.
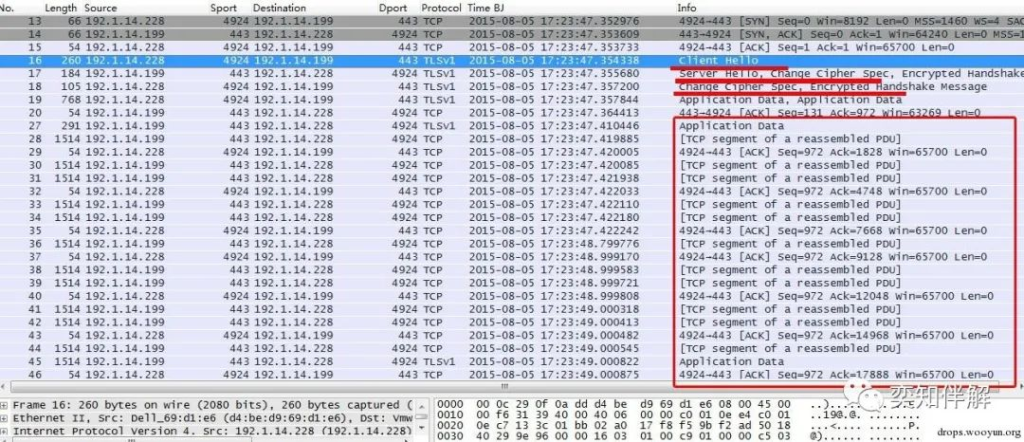
From the data, we can see that there is an authentication negotiation process in the HTTPS header. After authentication, there is a large amount of encrypted data, which basically indicates that the authentication is successful. The SSL authentication process is shown in the figure below:
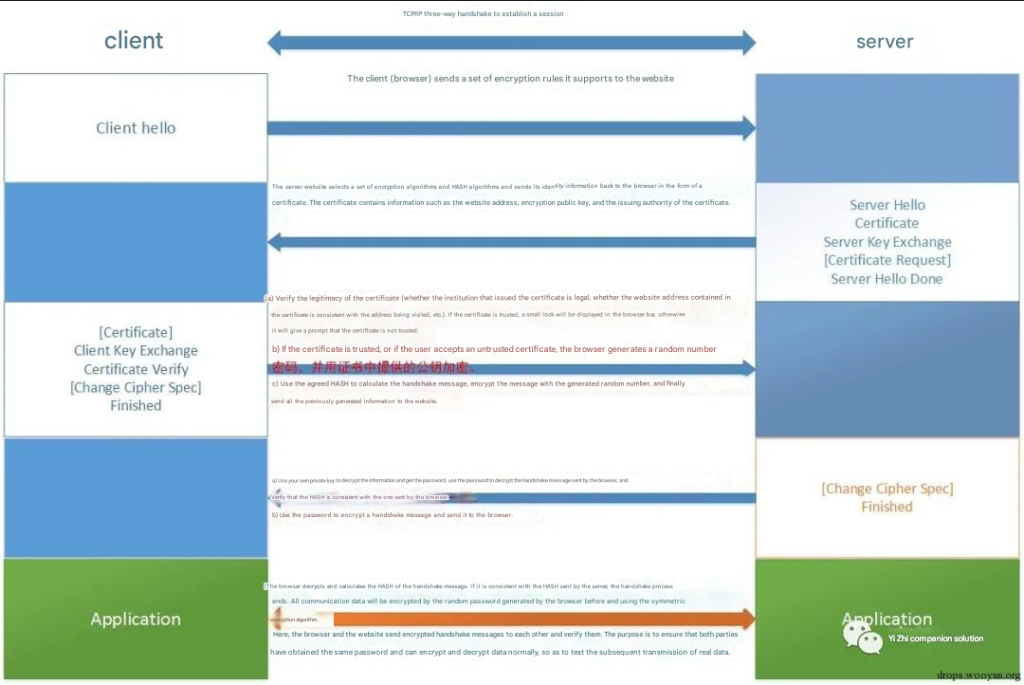
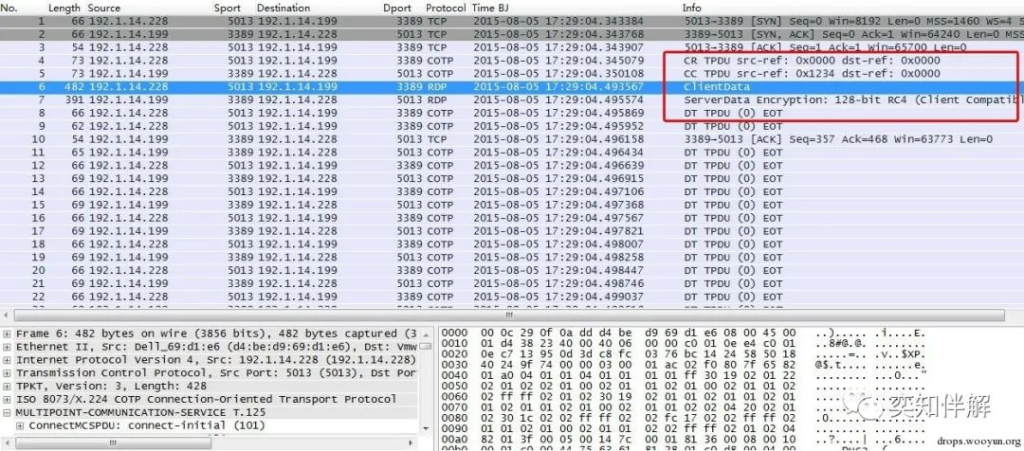
5. RDP protocol
RDP is a Windows remote control protocol that uses TCP port 3389. The encryption algorithm used in this version is 128-bit RC4; the red line is the login authentication process, followed by the successful login operation data.
2.3.2 Identify brute force attacks
From the principle of brute force cracking, we know that a large number of wrong passwords will be guessed during the attack. Generally, attackers will collect or guess some user names, related dictionaries and brute force algorithms through other means before brute force cracking to improve efficiency.
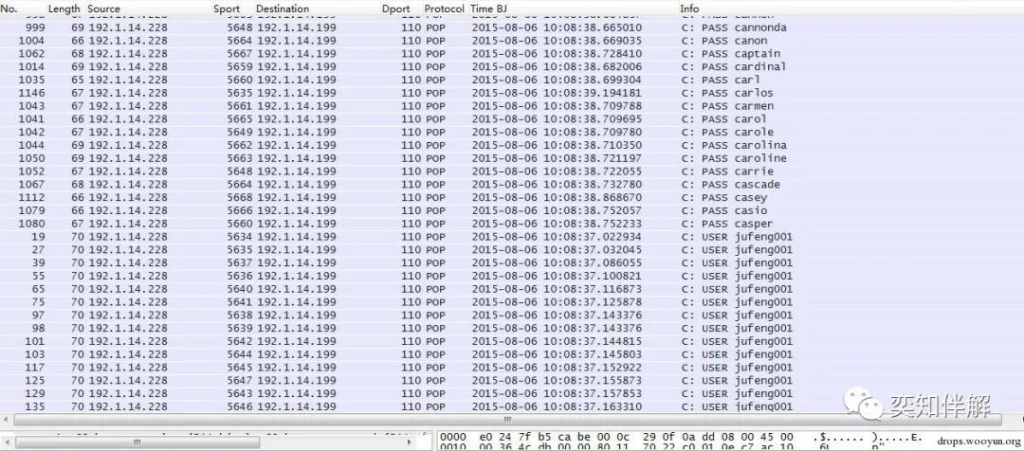
1. POP3 blasting
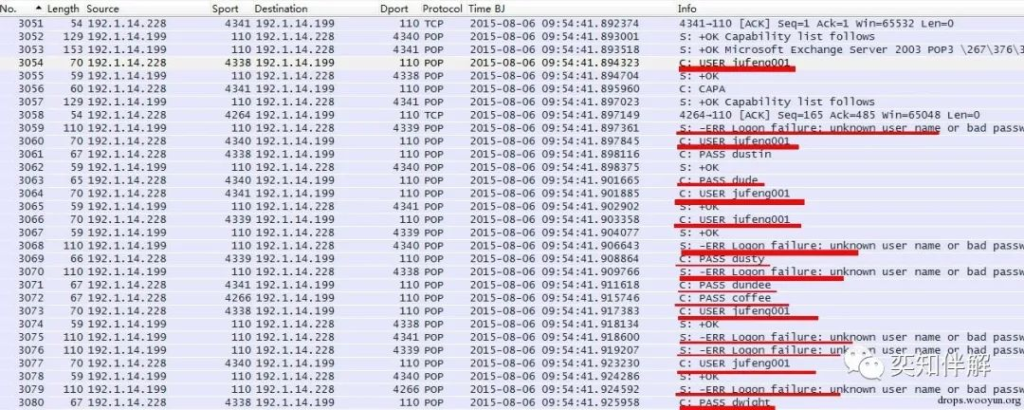
As can be seen from the figure, the attacker repeatedly enters the username jufeng001 and tries different passwords, and the server also reports a large number of errors: `-ERR Logon failure: unknown user name or bad password`. Follow TCPStream to see more clearly.
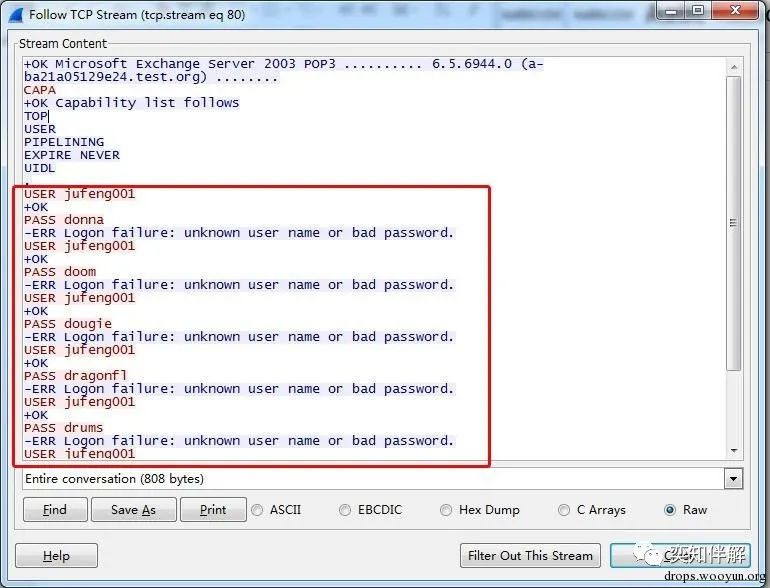
By extracting all the information, we can know which usernames and passwords the attacker guessed.
2. SMTP blasting
The SMTP protocol is often a loophole in users’ email security management, so it is often exploited by hackers.
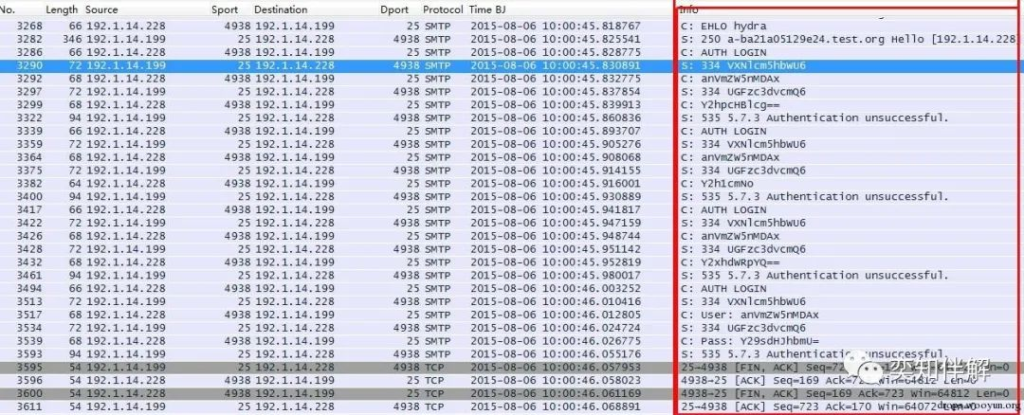
As can be seen from the figure, the attacker continuously enters the username jufeng001 and tries different passwords, and the server also reports a large number of errors: `535 5.7.3 Authentication unsuccessful`. Follow TCPStream:
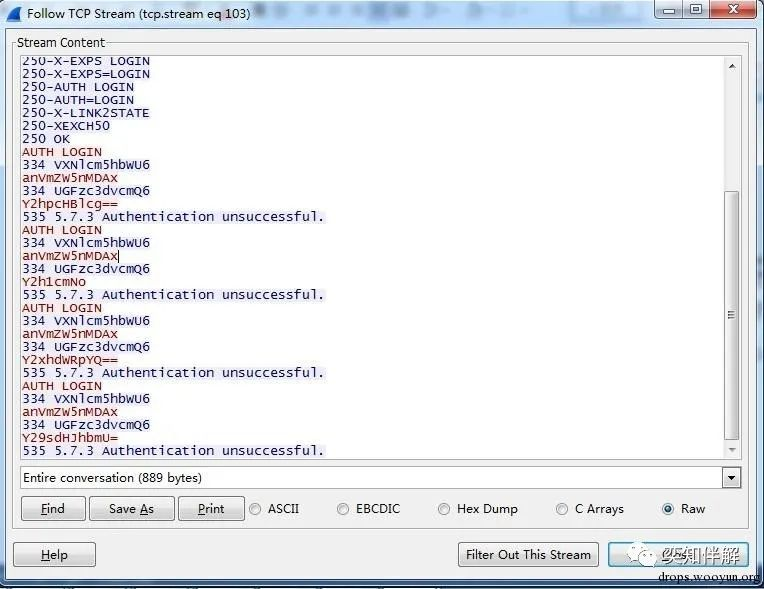
3. HTTP blasting
Due to the existence of a large number of Web servers, HTTP blasting is the most common, and many people are researching blasting methods and bypass mechanisms. Here we only use the simplest Web experiment environment for introduction.
First, when you open the data, you can see that a large number of login page request packets appear in a short period of time.
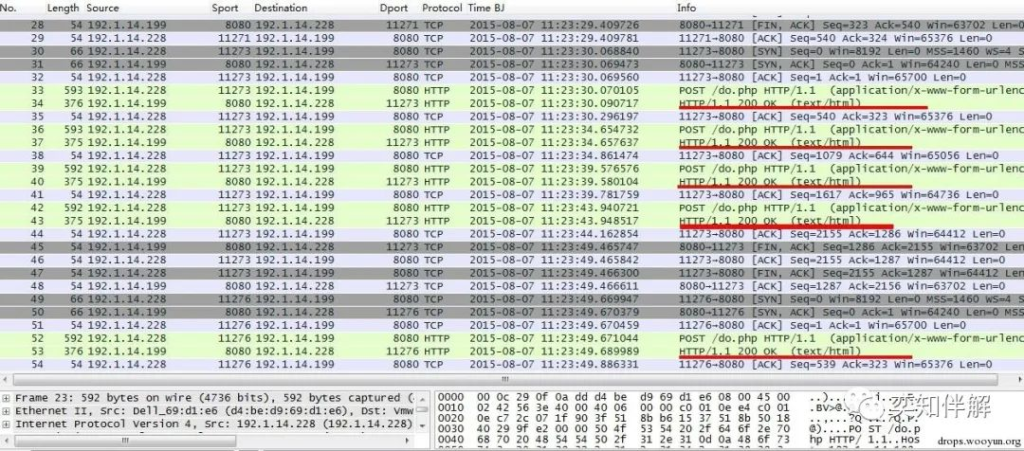
By extracting Follow TCPStream, you can see the user name and password input. The server return value is no longer “OK” for a successful login, but “…………” for a login error.
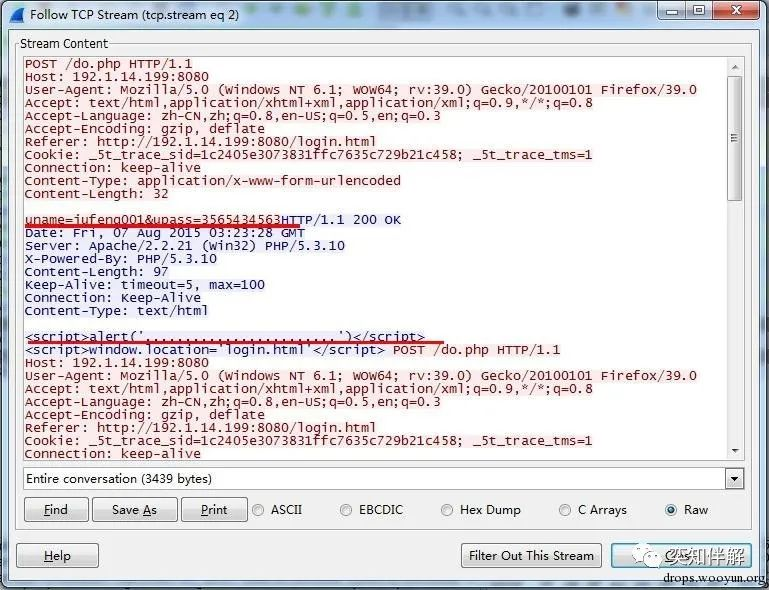
The above “…………” does not mean that no content is returned. This is because Wireshark cannot recognize the Chinese encoding. We can click Hex Dump to see the hexadecimal encoded content.
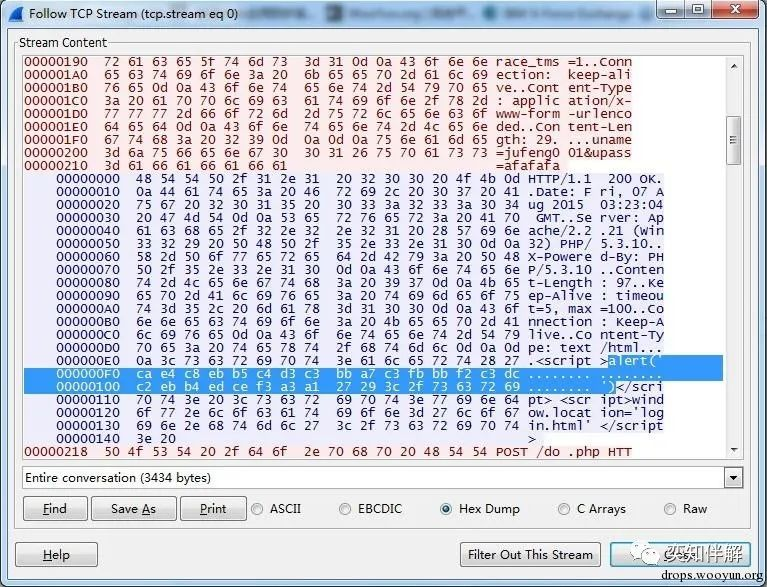
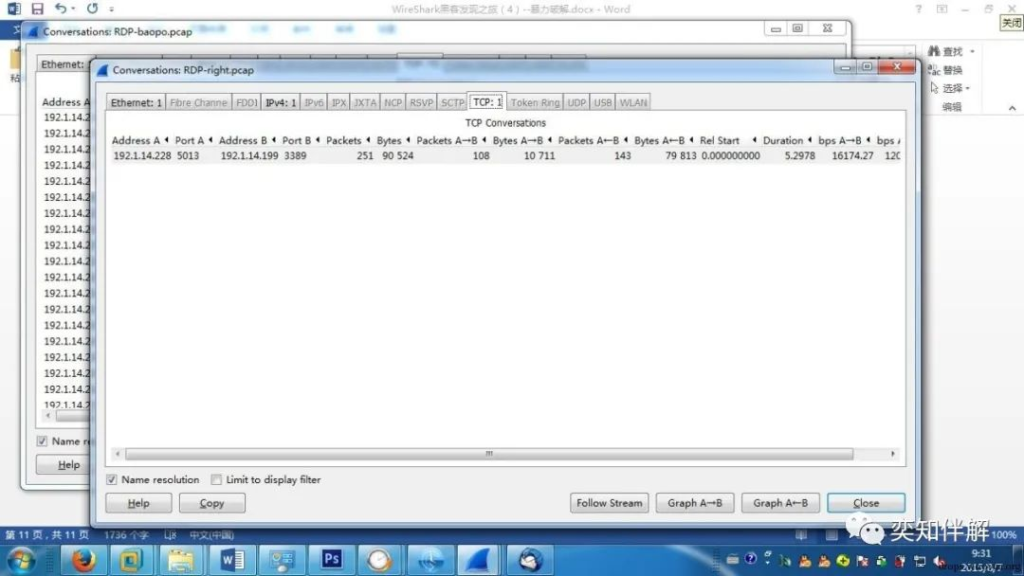
4. RDP blasting RDP blasting is widely used in hacker attacks. Once the login password is cracked, the machine can be basically controlled. Since the RDP protocol data is also encrypted, it is also difficult to identify the blasting. The following introduces another method for quick identification, which is also applicable to the blasting of other protocols.
First, we count the TCP port and other information of the normal login RDP protocol. It can be seen that if the login is normal, it is a set of “source port and destination port” within a certain period of time.
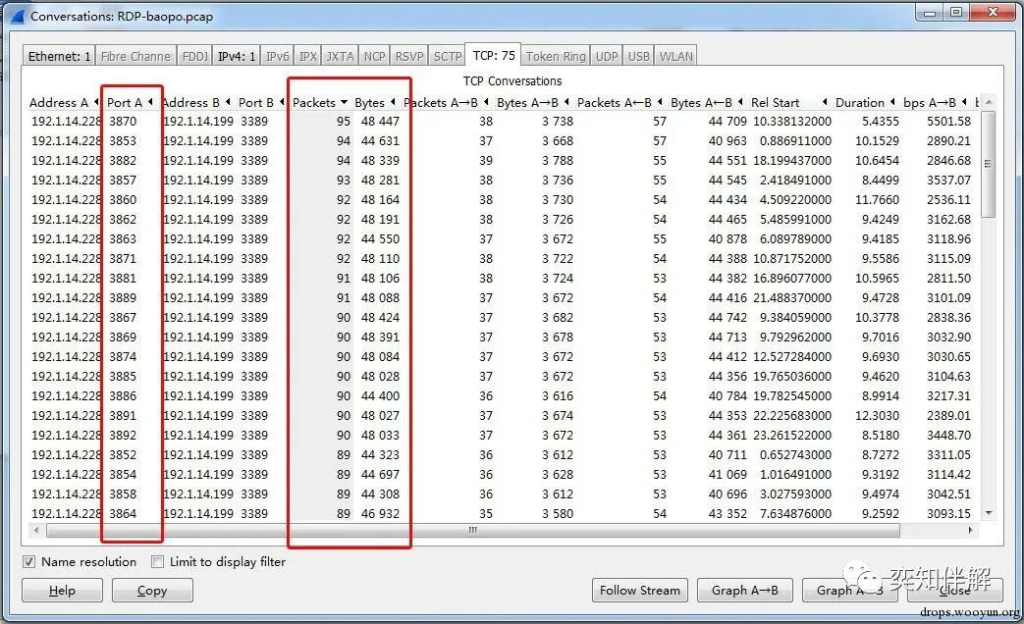
Looking at the TCP port and other information of the brute-force RDP protocol, we can see that a large number of different “source ports and destination ports” appear in a short period of time, and the number of packets and byte lengths are basically the same. This indicates that a large number of “short communications” with basically the same actions appear, and combined with the data format, it can be determined as brute force cracking behavior.
2.3.3 How to identify a successful blast
Of course, discovering brute force attacks is only part of the job. What is more important is to know whether the attacker succeeded in the brute force attack and what impact it would have on us if successful. The following is an introduction based on Wireshark to how to detect a successful brute force attack.
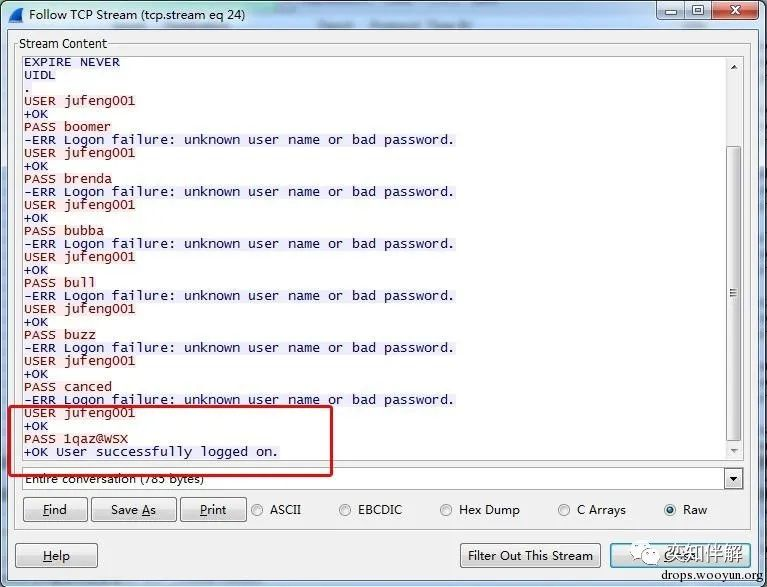
(1) First, we need to understand the protocol that the attacker is blasting, as well as the server return value when the protocol successfully logs in. The following figure shows the blasting of POP3. From the previous introduction, we know that if the login is successful, the server returns: “+OK User successfully logged on”.
2) Search for ” ” in the data +OK User successfully logged on.
(3) Through searching, it is found that there is indeed successful login information returned by the server.

(4) Following TCPStream, we found that after trying a large number of incorrect passwords, the attacker finally succeeded in cracking the password: username jufeng001, password 1qaz@WSX.
2.3.4 Analysis Conclusion
1. Whether you are a user or an administrator, we must pay attention to the security issue of weak passwords or regular passwords, and don’t let security precautions be lost in the details.
2. The verification code mechanism to prevent brute force cracking is only applicable to HTTP/HTTPS protocols and cannot prevent other protocols.
3. Once you understand the communication principle of brute force cracking, you can monitor and block it from the communication level.
4. The login permissions of important management systems are subject to many brute force attacks. It is best to bind the login permissions to the IP addresses commonly used by administrators or add an authentication mechanism to prevent hackers from having a chance to brute force attacks.
3. Summary
The document offers an in-depth analysis of various attack scenarios, focusing on the behavioral analysis of cyber threats. It begins with the examination of a compromised mail server, known as a “zombie machine,” detailing its misuse for spamming, pointing out vulnerabilities like high-risk open ports (e.g., TCP25/110) which allowed such control. Tools like WireShark are highlighted for data capture and protocol analysis. The document then explores a specific malicious code from Bodisparking, highlighting its persistence through scheduled HTTP requests, and noting the infection spread across multiple network hosts using indicators like repeated domain requests. It concludes with a comprehensive look at brute force attacks, outlining methods such as permutation and dictionary-based attacks that exploit weak passwords across multiple protocols including POP3 and HTTP. Emphasis is given to recognizing brute force attack patterns in communication data and implementing prevention measures, including binding login permissions with specific IPs and utilizing verification codes for HTTP/HTTPS, underlining the necessity of robust password policies to mitigate these threats. Keywords such as Brute Force Attack Prevention are central to the discussion, advocating for enhanced security practices in network management.



