Nowadays, more and more electronic devices use USB interfaces for communication, and the communication standards are gradually improving. Then, we will be curious about how these devices work? Whether you are a hardware hacker, a hobbyist or just a little interested in it, USB is challenging for us.


In fact, with Wireshark USB capture, we can capture the data sent by USB devices to our host for further research.
In this article, we will introduce how to capture USB data using Wireshark, with the following environment:
l Wireshark 2.0.1 (SVN) l Linux kernel 4.1.6
You can also use other versions of Wireshark, as long as it is above 1.2.0. We have not tested whether it works on Windows.
1. Introduction
Before starting, let’s introduce some basic knowledge of USB. USB has different specifications, and here are three ways to use USB:
- 1. USB UART
- 2.USB HID
- 3. USB Memory
UART or Universal Asynchronous Receiver/Transmitter. Under this mode, the device simply uses USB for receiving and transmitting data, without any other communication functions.
HID is a human interface. This type of communication is applicable to interactive devices, such as keyboards, mice, game controllers, and digital display devices.
The last is USB Memory, or data storage. External HDDs, thumb drives/flash drives, etc., fall into this category.
The most widely used are USB HID and USB Memory.
Every USB device (especially HID or Memory) has a Vendor ID and Product ID. Vendor ID marks which manufacturer produced the USB device. Product ID marks different products, and it’s not a unique number, but it would be best if different. As shown below:
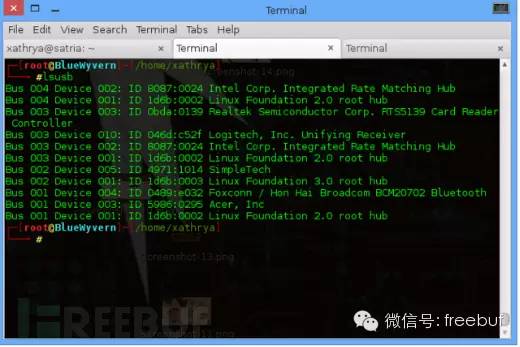
The image above shows the list of USB devices connected to my computer, viewed using the lsusb command.
For example, I have a Logitech wireless mouse. It belongs to the HID device category. This device operates normally, and by using this command, you can view all USB devices. Can you now identify which item is the mouse?? Yes, it’s the fourth one, as shown below:
Bus 003 Device 010: ID 046d:c52f Logitech, Inc. Unifying Receiver
This is the Vendor-Product ID pair, with Vendor ID value 046d and Product ID value c52f. This indicates that the USB device is properly connected, and this needs to be noted.
2. Prepare
We run Wireshark as root to capture USB data streams. However, it’s generally not recommended to do so. We need to give users sufficient permissions to access USB data streams in Linux. We can achieve this using udev. We need to create a usbmon user group and add our account to this group.
addgroup usbmon
gpasswd -a $USER usbmonecho 'SUBSYSTEM=="usbmon", GROUP="usbmon", MODE="640"' >
/etc/udev/rules.d/99-usbmon.rulesNext, we need the usbmon kernel module. If the module is not loaded, we can load it using the following command:
modprobe usbmon
3. Capture
Open Wireshark, and you’ll see usbmonX where X represents a number. The image below shows our result (I used root):
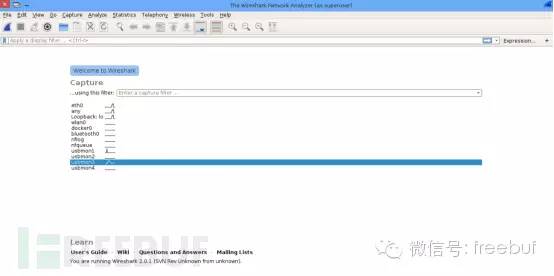
If the interface is active or there is data flow, Wireshark’s interface will display it in a waveform. So, which one should we choose? Yes, it’s the number X I just asked you to note, corresponding to the USB Bus. In this article, it’s usbmon3. Open it to observe the data packets.
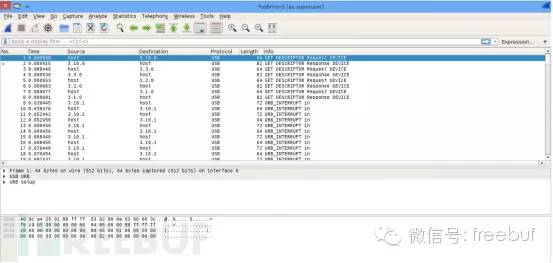
So, what use do we get from this? Through this, we can understand the communication process and working principle between the USB device and the host. Maybe we can apply this knowledge in reverse engineering and gain something. That’s all for now!
Summary
The article provides a guide on how to capture USB data using Wireshark, specifically on a Linux system with Wireshark version 2.0.1 and a kernel of 4.1.6. It begins by explaining the basics of USB protocols, such as USB UART, USB HID, and USB Memory, and emphasizes the importance of Vendor ID and Product ID for USB devices. The guide then describes how to set up the environment, including creating a `usbmon` user group and configuring user permissions with `udev` rules. It also explains loading the `usbmon` kernel module and running Wireshark to capture USB data streams on relevant interfaces. The article serves as a resource for those interested in analyzing USB communications, potentially for reverse engineering purposes. Keywords highlighted include “Wireshark USB capture”.



