1. VMware Virtual Machine Installation Just install it directly Baidu Cloud Disk: https://pan.baidu.com/s/1Jw3ypreqmOqF4vgsXAEz2Q 2. Mininet Installation sudo apt install mininet
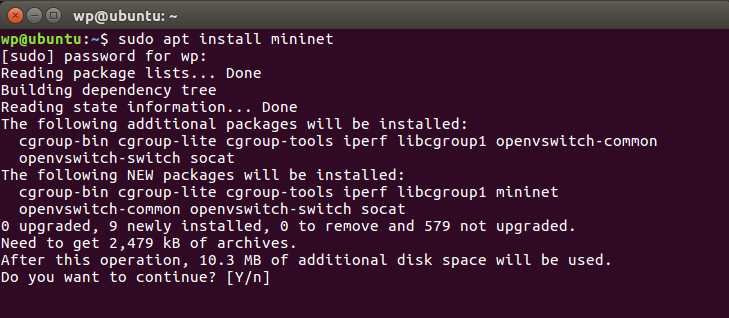
Choose Y Then it starts downloading and installing, let it run for a while

After it finishes running, here it is
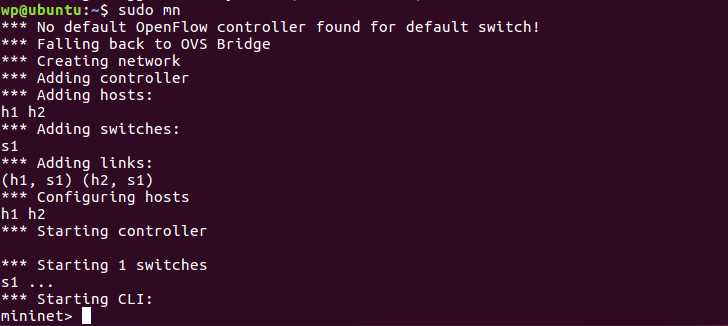
Let’s take a look at the effects sudo mn
Mininet is installed. If you only need Mininet, you are done. However, most friends use Mininet for learning and testing You will find a situation like the image below, indicating that OpenFlow and Open vSwitch are not installed
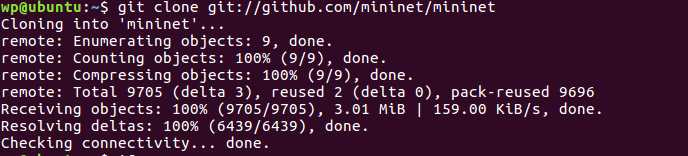
Let’s continue with the installation Git installation sudo apt install git Obtain the source code git clone git://github.com/mininet/mininet
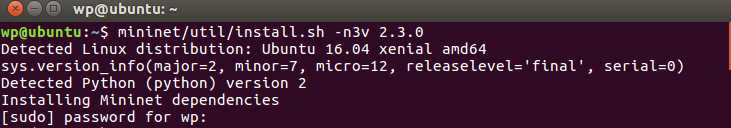
Install only OpenFlow 1.3 and Open vSwitch 2.3.0 mininet/util/install.sh -n3v 2.3.0
Then it starts
This time let’s test to see the result, you’ll find those two lines are gone sudo mn

2. Visual Mininet Editor There is a visual tool in Mininet called Miniedit which can quickly create topologies, let’s take a look sudo mininet/examples/miniedit.py
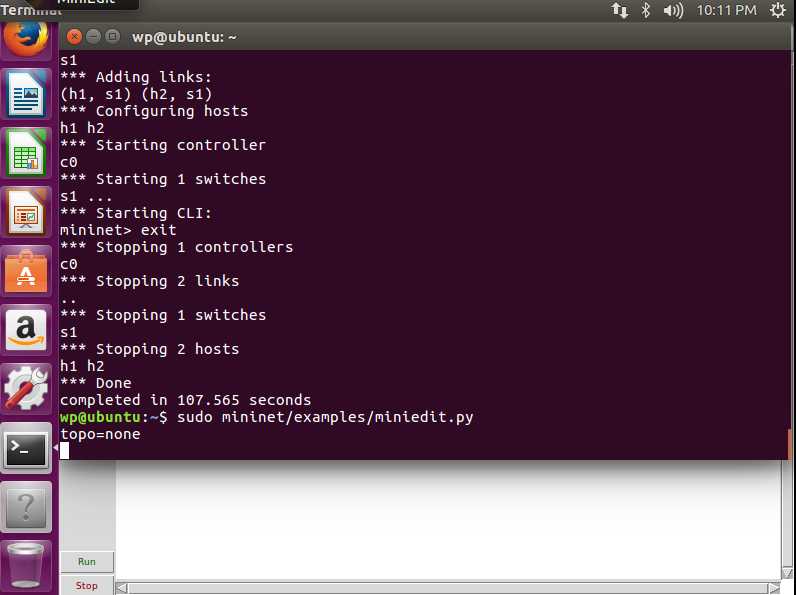
This kind of interface will pop up, and you can create your topology within it
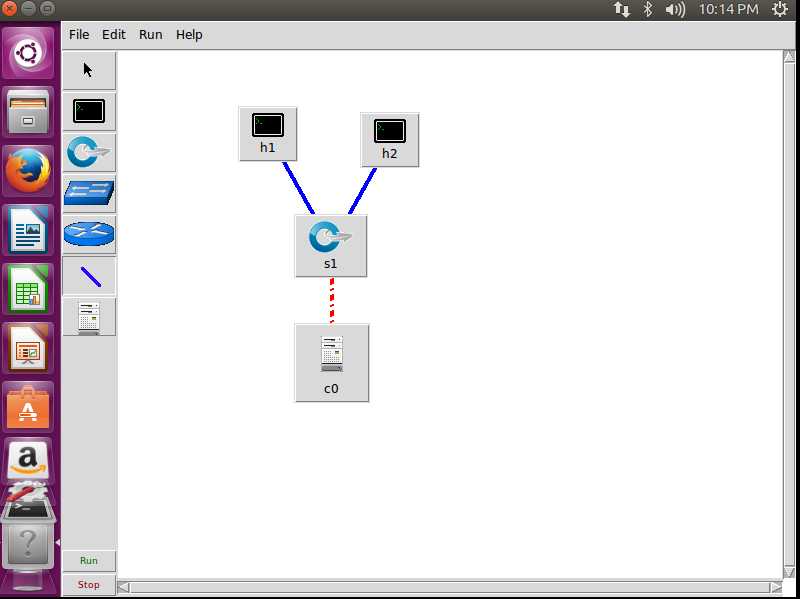
Create a topology randomly here
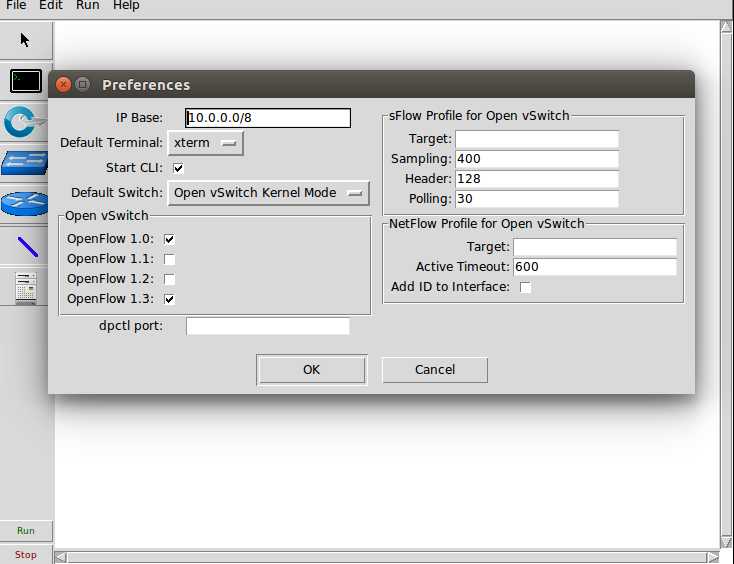
In state, set edit-preferences, mark start CLI and OpenFlow 1.3, OK
Run it, and clicking run, you will find an error, the path is wrong
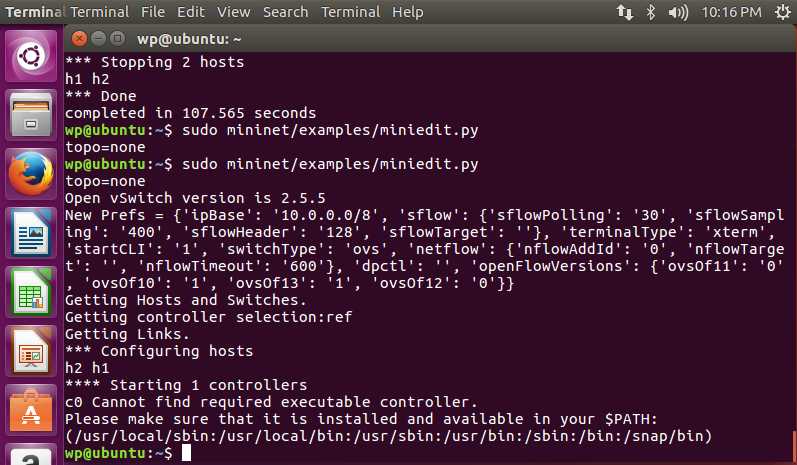
Run: sudo ln /usr/bin/ovs-testcontroller /usr/bin/controller
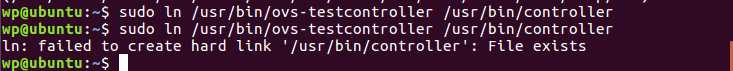
Then let’s try again, sudo mininet/examples/miniedit.py, create the topology, set according to the steps above, and run You will find the left side becomes all gray
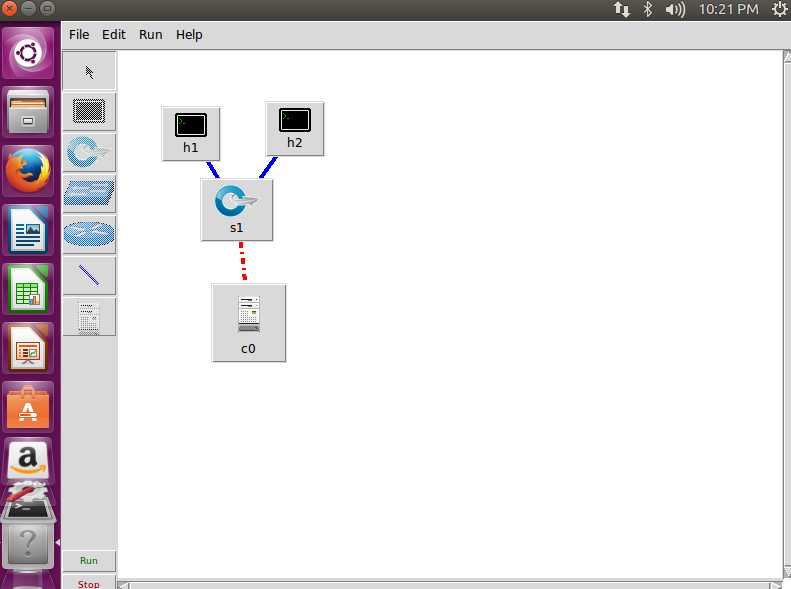
Let’s switch back to the control interface, everything is OK
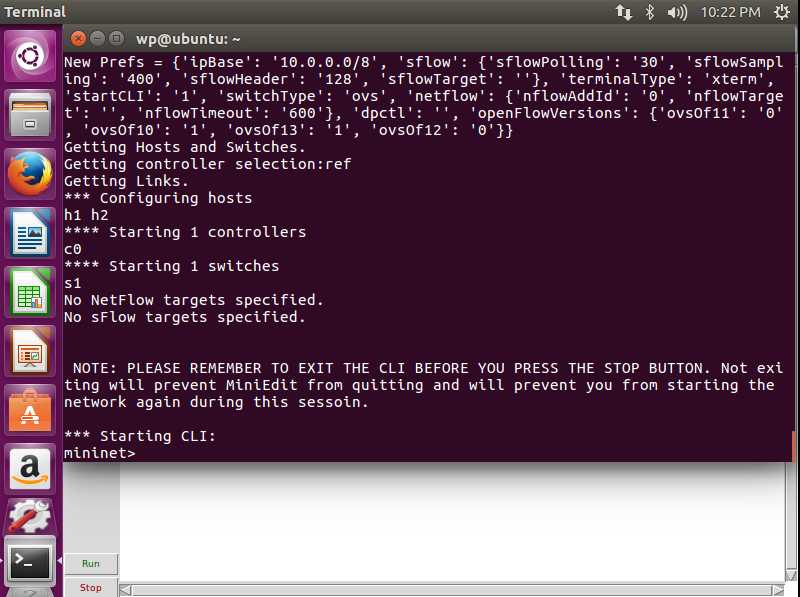
3. Packet Capture Tool Wireshark Installation and Testing sudo apt install wireshark
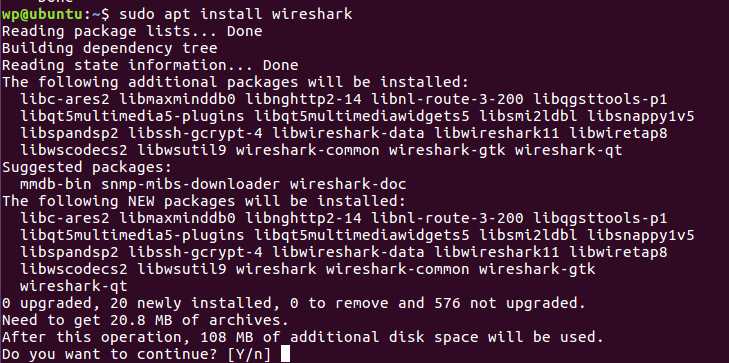
Choose Y, and it starts installing
Select yes
Done
Let’s test this packet capture tool, first establish a topology, using the default one or drawing one with the visual tool is also fine Here, use the default sudo mn In another terminal window, enter sudo wireshark

At this moment, a new window will pop up, indicating Wireshark is running, let’s go in and take a look
Select any in the middle
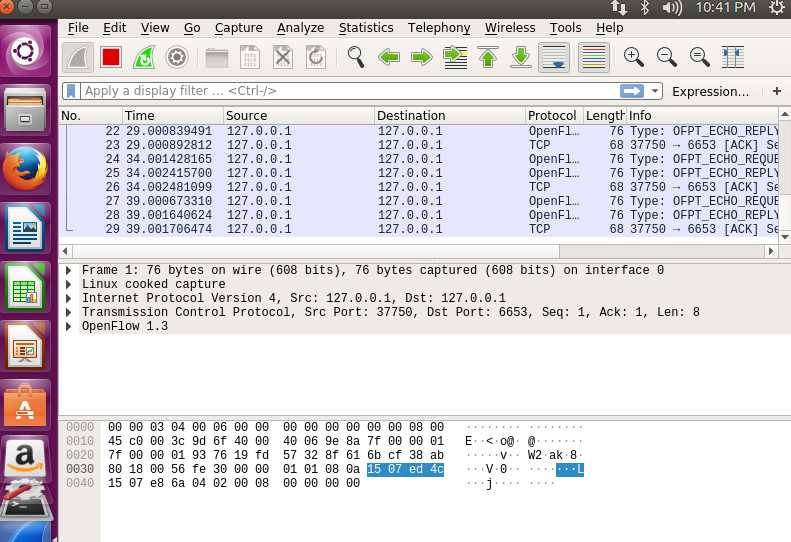
Here you can see the captured packets



