1 Introduction to OpenWrt
Here’s the rewritten content:Note: In a previous article I wrote, I realized that the structure and content layout were not optimal, leading to a poor reading experience, which affected both distribution and SEO. Therefore, I am reorganizing and splitting it for better readability, with a focus on OpenWrt.
This series introduces two hack techniques for smart routers for your enjoyment.
This article mainly discusses the data monitoring capabilities of openwrt-smart routers. (To maintain the independence of this article, there will be some repetition in the content.)
Previous article:
OpenWrt: Overview and Preparation
According to Baidu Encyclopedia, OpenWrt can be described as an embedded Linux distribution (mainstream router firmwares include dd-wrt, tomato, openwrt) rather than trying to establish a single, static system. OpenWrt’s package management provides a fully writable filesystem, offering choices and configurations from application vendors, and allows you to customize the device to suit any application.
Before officially starting the experiment, some preparatory work is required:
Note
This article was based on purchases from Xiaomi’s official website, then followed tutorials to flash it into a customized
After a successful flash, you can remotely route via PC just like remotely logging into an ordinary Linux server. After login, the router terminal interface prompts:
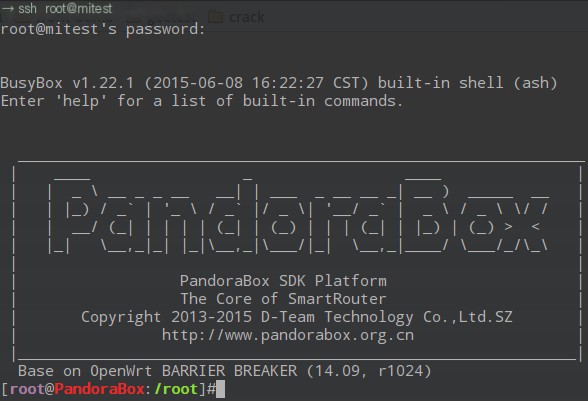
Basic file operations, network operations, etc., are similar to regular Linux. Meanwhile, openwrt can also install application software through a software repository. For specifics, see openwrt software package management.
For example, installing an application:
The basic knowledge of openwrt has been briefly introduced above, and now we start some comprehensive applications.
| [1] | openwrt software package management <http://wiki.openwrt.org/doc/packages> |
|---|
OpenWrt: 3 Information Monitoring Tools
As a gateway, in addition to network configuration functions, a smart router also has network data forwarding functions. Since openwrt is based on Linux, it has excellent packet capture applications, combined with visualization tools, can achieve the ability to monitor all data passing through this route.
The usage methods of these tools are not the focus of this article, so it will not be elaborated, it is assumed the reader has a certain level of foundational knowledge in this area.
The following example is an experiment to monitor all the data passing through the router using a remote machine through visualization tools.
3.1 Principles and Methods
The basic network structure diagram is as follows:
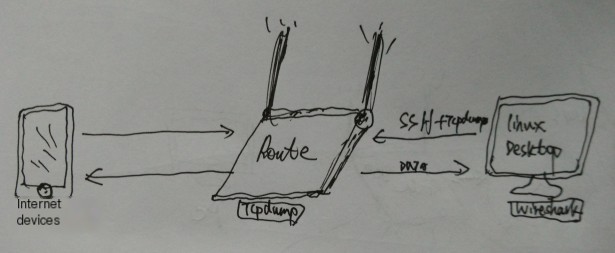
The main operation principle is:
Execute the following command in the desktop system terminal:
Then enter the corresponding account password to monitor.
Explanations for the above command line are as follows:
3.2 Tool Tips and Tricks
The basic principles and operational methods were described earlier, but the downside is that long command lines and passwords must be input each time. Using some small Linux operating tricks can simplify this process; creating a command tool for easy invocation.
Basic principle:
Auto-login script implementation:
Edit the ~/.bash_alias file to define command line aliases:
After this, just input zshark in the shell to complete the command initiation.
3.3 Demonstrating and Applying Results
Then start the packet capture tool, connect the Xiaomi 4 phone to the router, open the UC Browser, and visit:
Click to enter and access the webpage:
The packet capture effect diagram is as follows:
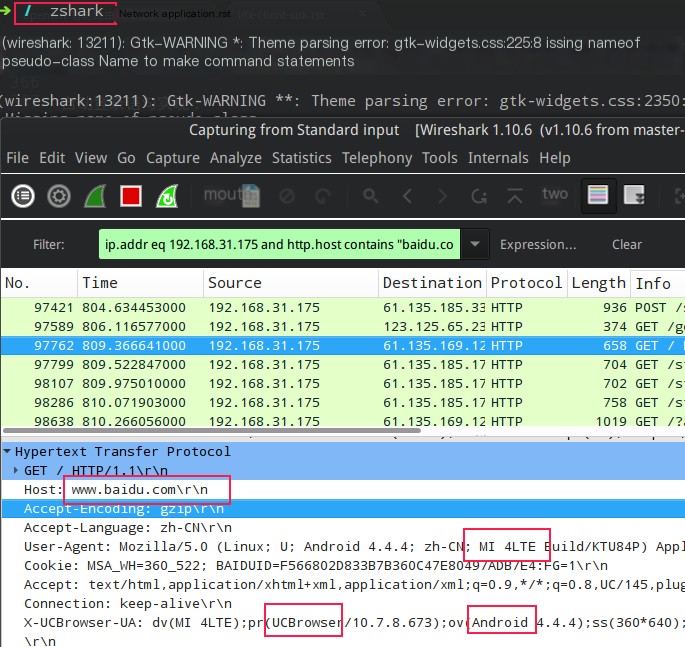
You can already see the corresponding network IO access content of the device.
This functionality can be used to monitor and analyze network data on platforms without packet capture applications. For example: analyzing network communication situations on mobile phones.
During software development, caching often easily creates some incorrect illusions, which can significantly affect analysis and judgment during software debugging. For instance, during network environment migrations, different devices have varied DNS or static file caching mechanisms, especially mobile browsers that have certain features. These features have altered the previously understood network request process. If unaware of this impact, applications often display perplexing or misleading phenomena. Therefore, network monitoring tools must confirm that the network environment has been correctly migrated to ensure developers observe credible phenomena.
For example: UC and QQ mobile browsers have features, but at least they can be turned off in the settings, but the WeChat embedded browser also has this feature, and there’s no place to turn it off, making it easy to cause confusion or misunderstanding during web development debugging.
3.4 Reflections on Network Security
The preceding content has already described how to capture packets, and one can clearly see the related access information on a mobile phone connected to the PC:
For non-sensitive information, it can still be relatively sensitive sometimes, an invasion of privacy, after all, nobody wants all their network behavior habits to be totally exposed.
For example, wireshark can count access records of a specific device:
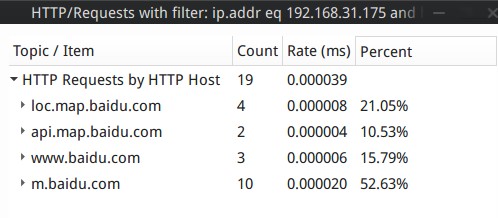
This was just a brief visit to baidu.com during the experiment. If long-term network exit monitoring is conducted, it would be easy to analyze preferences and characteristics of the device holder based on the content categories of the browser’s websites. For example, a discovery of numerous shopping links for women’s clothing could identify the individual as a young woman; if many pages searching for technological papers are found, it could indicate a researcher.
Having more data allows for the analysis of even more content. For instance, if you’re secretly searching on your mobile phone browser, carefully thinking that no one knows, in fact, others know everything. You think you’re learning more through search engines, which leads to more network activities, letting others know even more.
Fortunately, the largest domestic search engine switched to using secure service protocols by 2015. Before that, the protocol was unencrypted. Other search engines, as of now, still use unencrypted protocols.
For sensitive information, such as usernames and passwords, if transmitted under the HTTP protocol, they can be directly captured and viewed on the router. The impact of this information can be quite significant.
Therefore, the security summary is as follows:
Note
Content transmitted under encrypted protocols is not visible in plain text, even if packets are captured by a router. Currently, large internet companies’ sensitive data transmissions are mostly based on encrypted protocols. However, many small and medium-sized internet companies have not yet paid attention to this, still using unencrypted protocols. Things like usernames and passwords can be seen in plain text when transmitted through routers.
4 Public WIFI Security Warning
Through the following methods explanation, it should raise some users’ awareness of public WIFI security. If the opponent is the router administrator and the terminal user connects their device to the router (being phished), then:
Generally, WIFI with clear origins can still be trusted (since major merchants now offer free WIFI, there is no need to reject the benefits), but it is best not to easily connect to unknown WIFI to avoid unpredictable risks.
5 Final Summary
The two smart router plays introduced above are meant to encourage everyone to use them positively in production to improve software productivity. Please use responsibly.
| Author: | Harmo哈莫 |
|---|---|
| Author Introduction: | https://zhengwh.github.io |
| Email: | [email protected] |
| QQ: | 1295351490 |
| Time: | 2015-10 |
| Copyright Statement: | Readers are welcome to freely reprint for learning and communication purposes, but please 【indicate the source】 |
| Support this article: | If the article inspired you, you can click the button at the bottom right corner of the blog to 【recommend】 |



