Malware (sometimes referred to as malicious software) is examined and understood through the process of malware analysis. This technique is crucial for identifying and mitigating cyber risks when hackers use malware to gain unauthorized access to computers, steal valuable information, or damage computer systems.
Examine malware that has not yet been triggered. This method allows us to identify libraries and hardcoded strings. A certain malicious file is being used.
Investigate malware through execution. This technique enables us to determine which processes, threads, and HTTP requests are generated by the infection.
The execution of processes and any accompanying activities (such as file and network traffic) can be visually mapped by analysts using ProcDOT. This application uses visualization methods to display this data, making it easier for analysts to spot suspicious activities and understand the functionality of the malware.
Always use a virtual machine to test malware
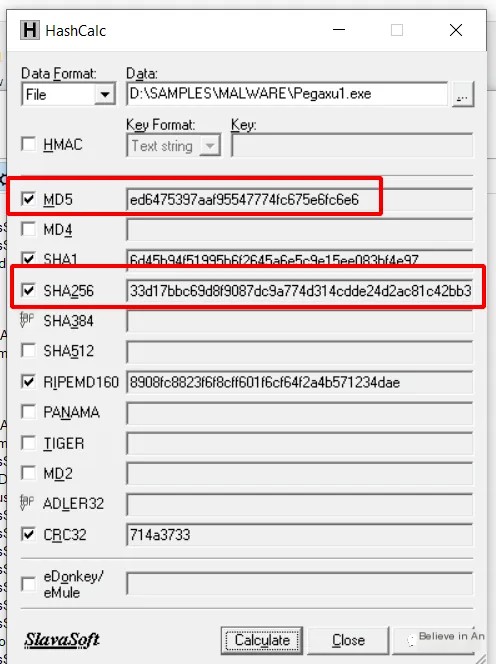
Malware sample download:
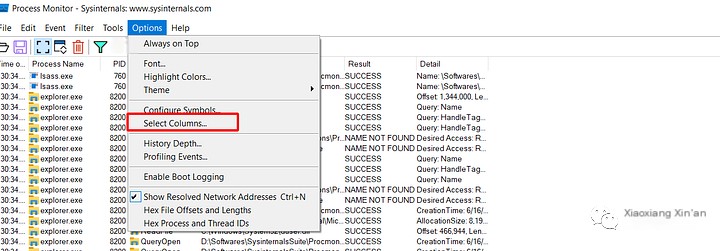
Select the thread ID and deselect the sequence number (if selected)
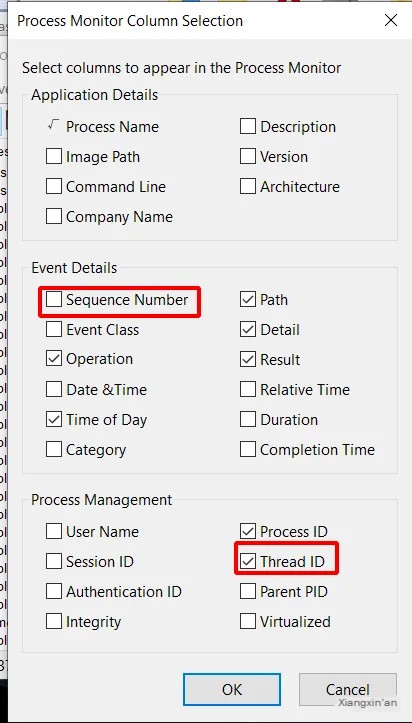
Select the resolved network address
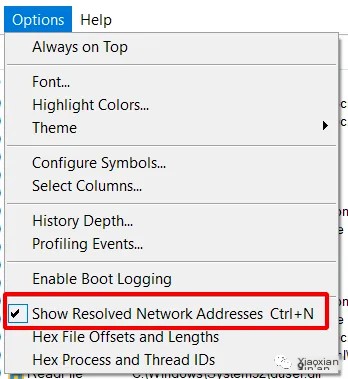
Now run any packet capture software, I used Wireshark to do it.
Launch the malware while closely monitoring the background programs procmon and wireshark.
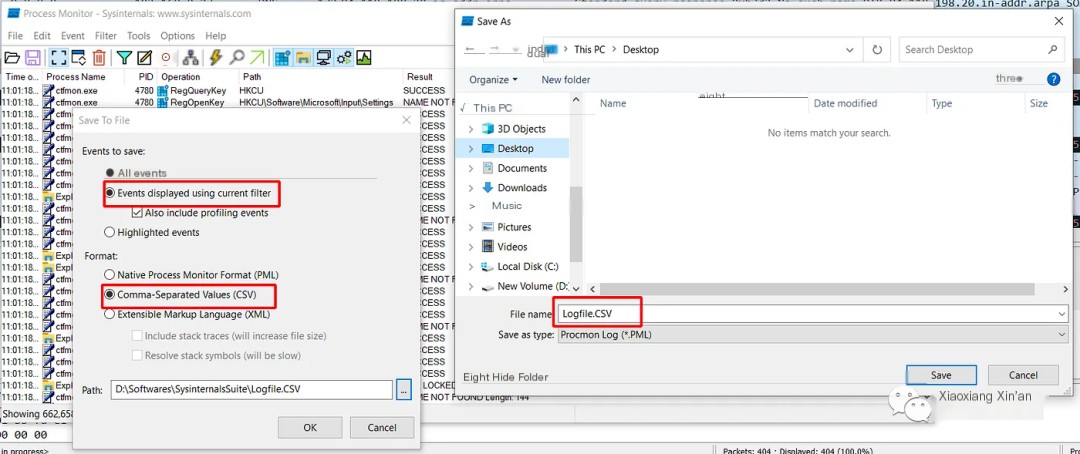
Save the procmon log file in CSV format.
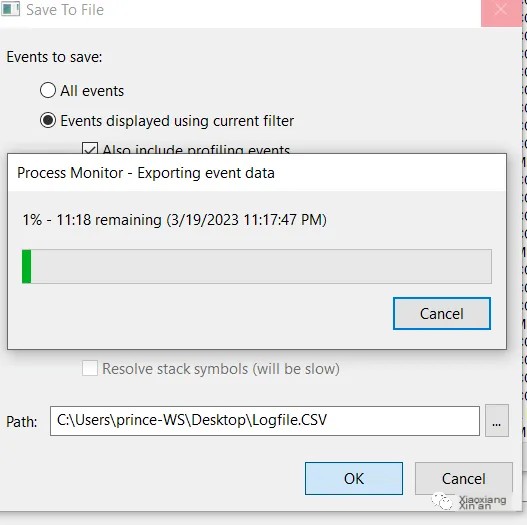
After a while, save the packets captured by Wireshark now in the .txt format allowed by ProcDot.
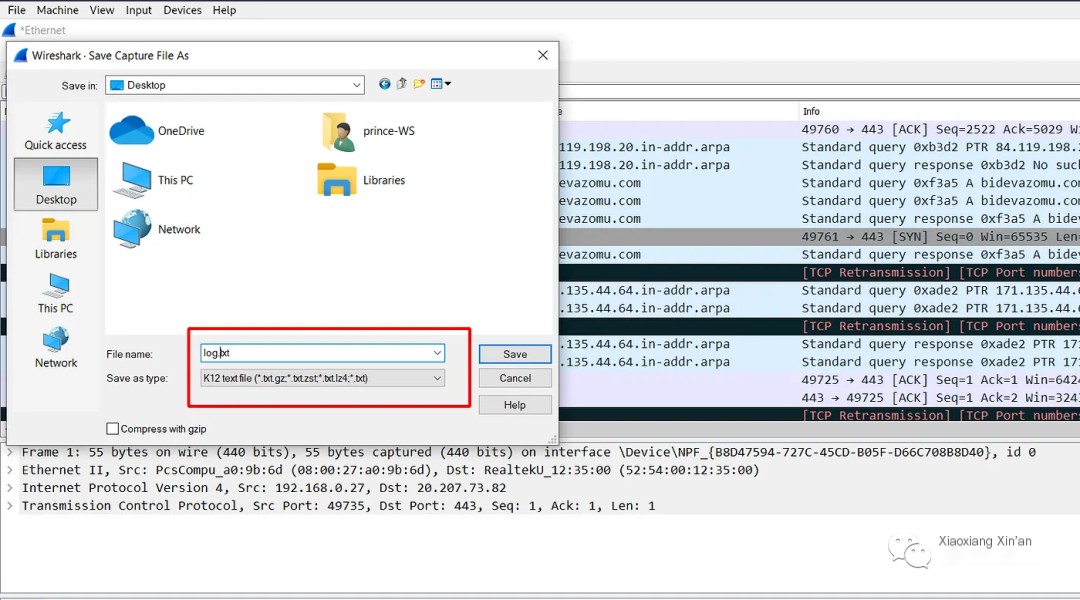
Select the procmon log file in ProcDot, then choose the malicious process you want to view. After selecting the infected process, select the TXT pcap file previously saved in Wireshark.
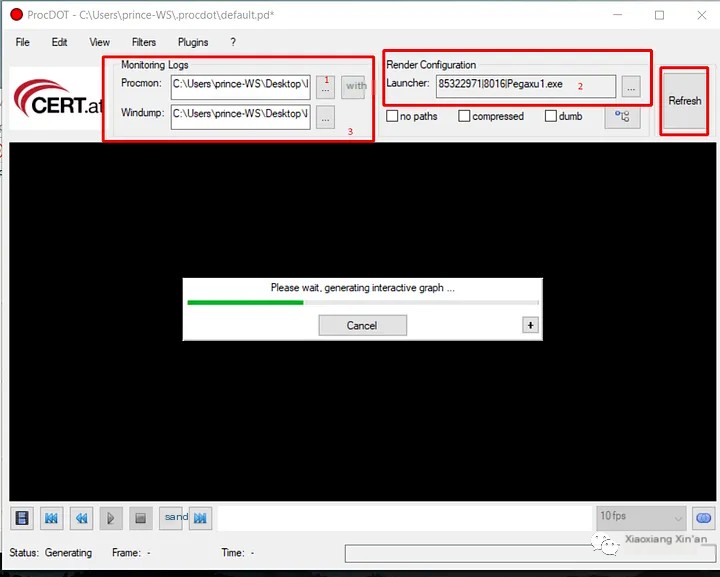
The diagram will provide a comprehensive view of all processes, subprocesses, registry edits, and other changes executed by the malicious process.
By analyzing this detailed report, you can better understand how the malicious process operates and the extent of the damage it causes.
Additionally, this information can be used to develop and implement more effective security measures to prevent similar attacks in the future.
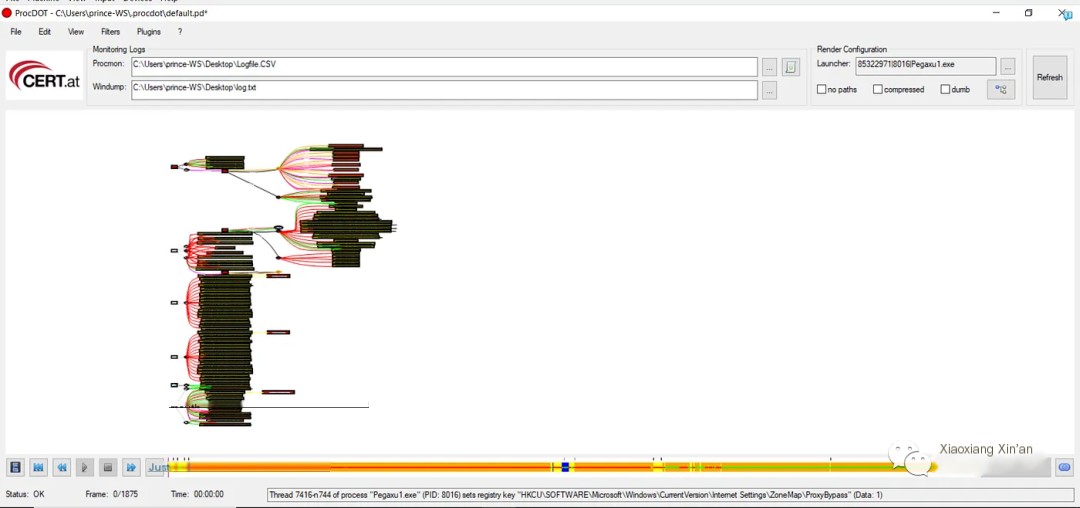
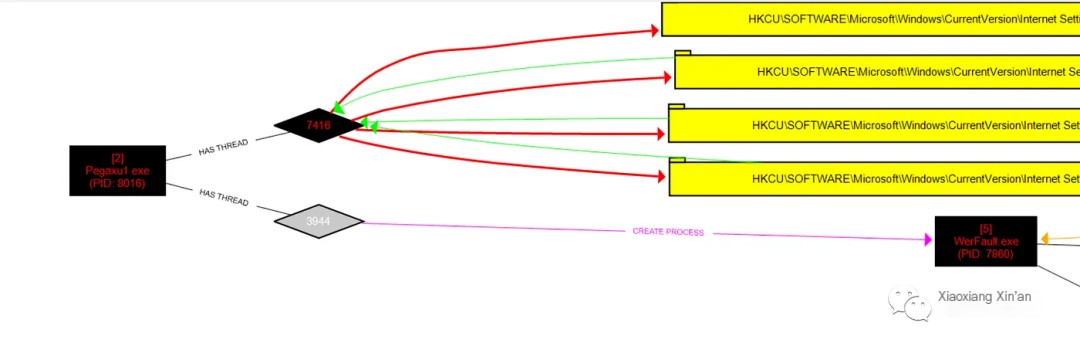
In the above image, we can see that the malicious process created new subprocesses and then connected to a random IP address
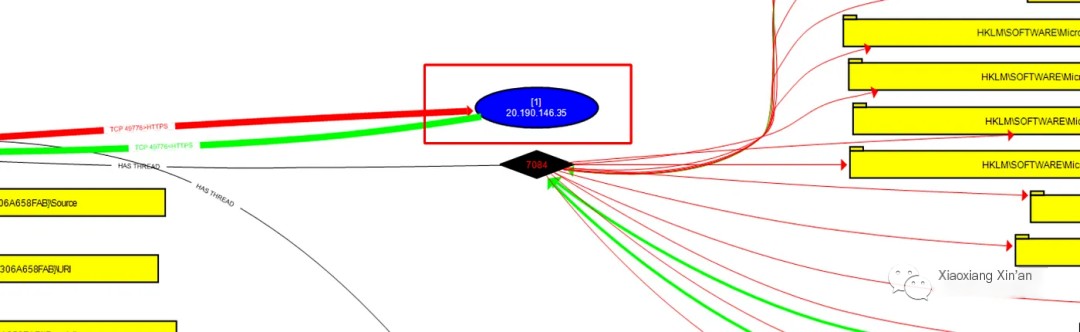
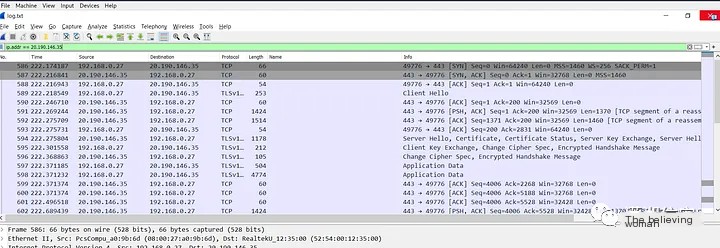
After collecting detailed information, we can view the pcap to see the details shared in the packets
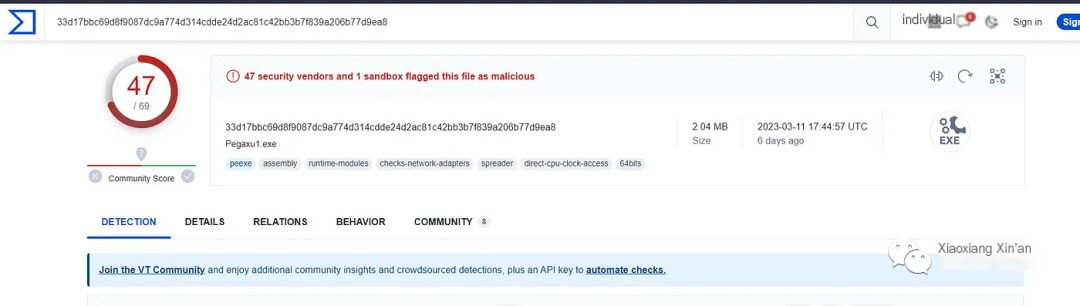
Let’s check the IP details on Virustotal to understand the reputation
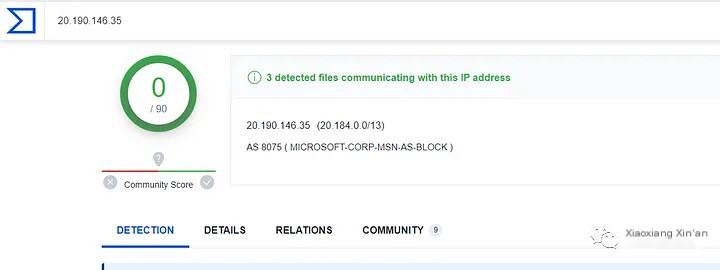
The IP is clean, let’s see what the community says about this IP:
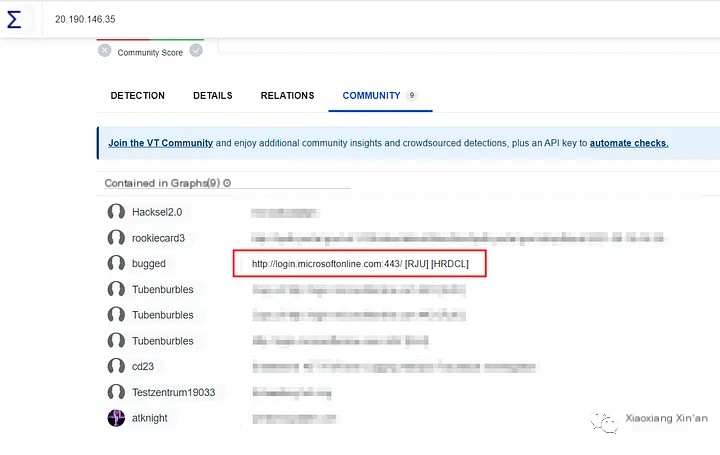
Therefore, a Microsoft IP means it is safe, but we can see all the IP addresses found in the chart or pcap file.
Let’s see all the files created or deleted by this malware
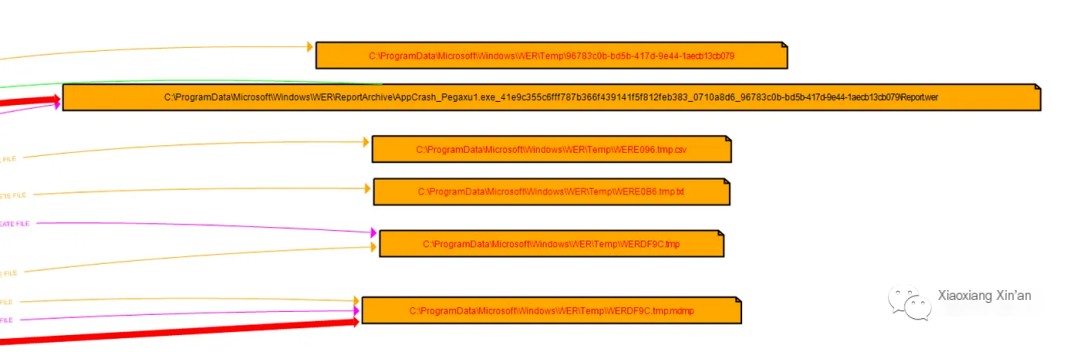
With this technology, we are able to dynamically examine the behavior of malware in a system or network architecture in real-time. By doing so, we can more effectively detect and respond to threats, ultimately enhancing the security of the organization.
Furthermore, insights gained from analyzing malware behavior can be used to strengthen our overall security posture, identifying potential vulnerabilities and areas for improvement.
This technology provides us with a powerful tool to combat cyber threats, enabling us to stay one step ahead of attackers and protect our critical assets.


