Common Tools
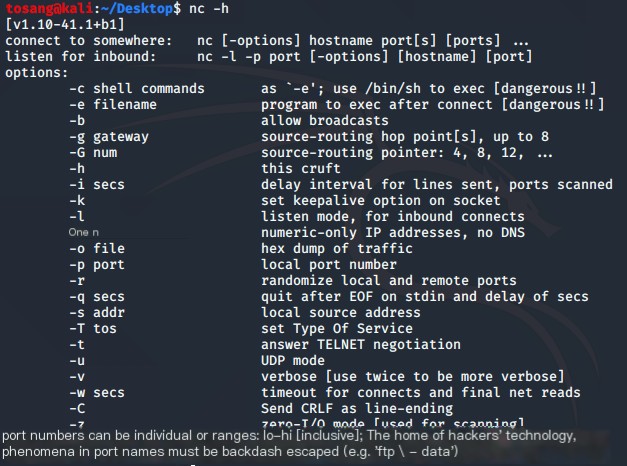
nc is a remote transfer control tool. Use the `nc -h` command to view parameter descriptions.
NC—Fetching Banner Information
Test
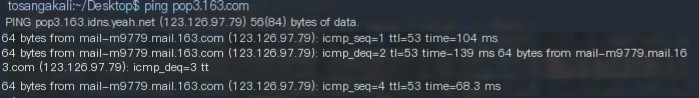
First, use ping + domain name to get the IP address.
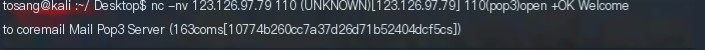
As the port for pop3 is; use the nc -nv command to connect directly.
NC—Telnet Text Transfer&
NC—File/Directory Transfer
NC—Port Scanning (Not Very Accurate, Not Commonly Used)
NC—Remote Control
Summary
NC lacks encryption and authentication capabilities, making it insecure. You can use NCAT to make up for NC’s shortcomings, as it supports SSL encryption. NCAT is included in nmap.
Wireshark is a packet sniffing and protocol analysis tool.
Using Wireshark to Capture Packets
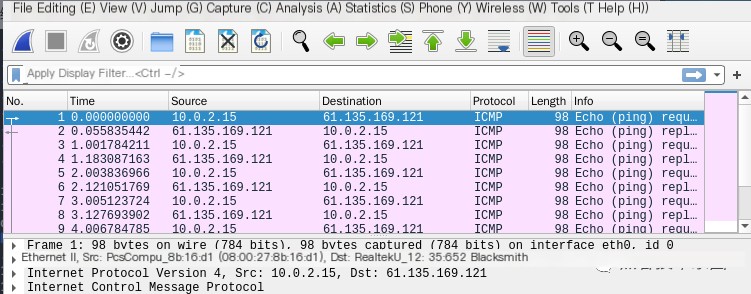
You can save captured packet data files here. It is recommended to save them in pcap format for better compatibility.
Filters
Wireshark can filter by IP, domain name, and protocol and supports combined expressions called filters. As shown in the figure below, the current protocol line can be selected and applied as a filter.
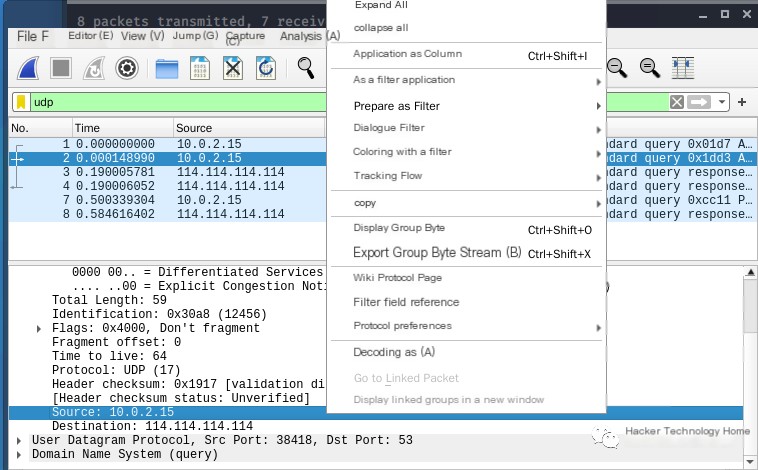
Common Protocol Packets
Statistical Analysis
Summary
Wireshark is not suitable for capturing a large number of packets. Thus, enterprises typically use tools like Sniffer, Cace, Cascad point, etc.
Information Gathering
DNS Information Gathering—NSLOOKUP
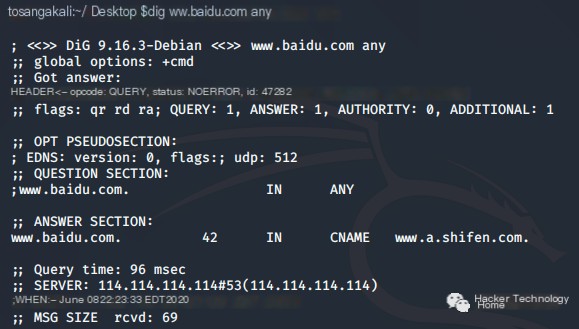
DNS Information Gathering—DIG & More Powerful
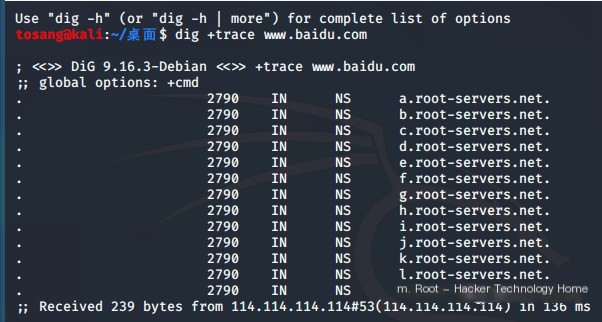
The DNS tracking example diagram shows 13 root domain servers in the root domain.
Then query the .com domain server address in the com domain.
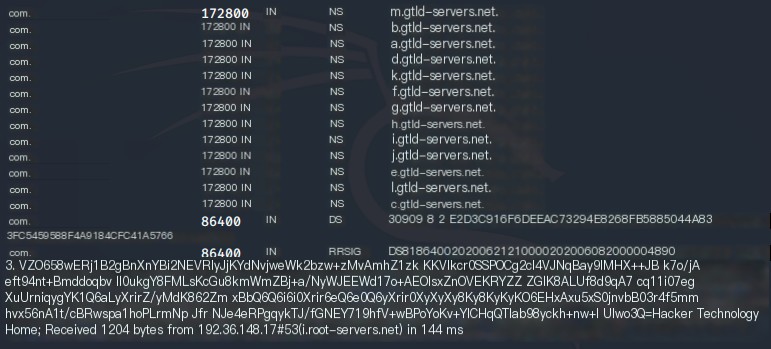
Next, randomly select an IP from these .com domains to query the ns record of the baidu.com domain.
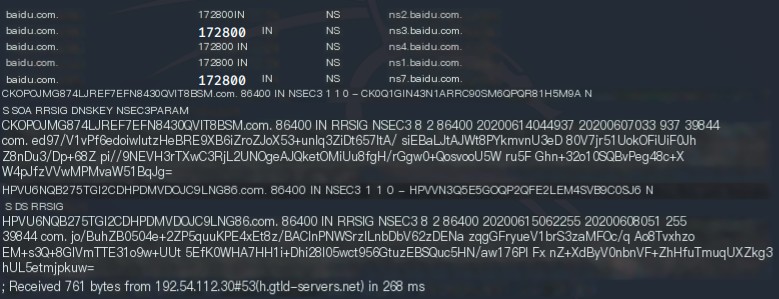
Finally, randomly select one from the ns records to query for the www.baidu.com record and get the cname result. Decoding the cname can get the final IP address from Baidu’s domain server ns.
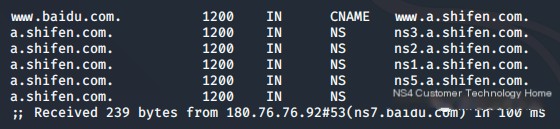
DNS Zone Transfer
Zone transfer refers to the process of synchronizing data between domain name servers; through zone transfer, you can obtain all host records within a domain.
DNS Brute Force
DNS Registration Information
Search Engines
Usage example: first obtain the IP of a certain domain through nc, taking gscaep.ac.cn as an example here.

Use Shodan to search all information about this IP.
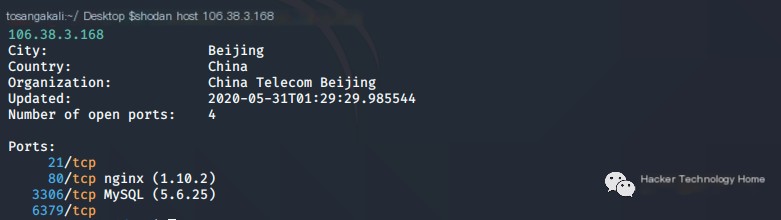
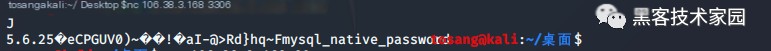
This penetration reveals the database version in use and its port information, which you can attempt to connect to using nc.
Google Search Methods
Search Tools
File Information—METADATA
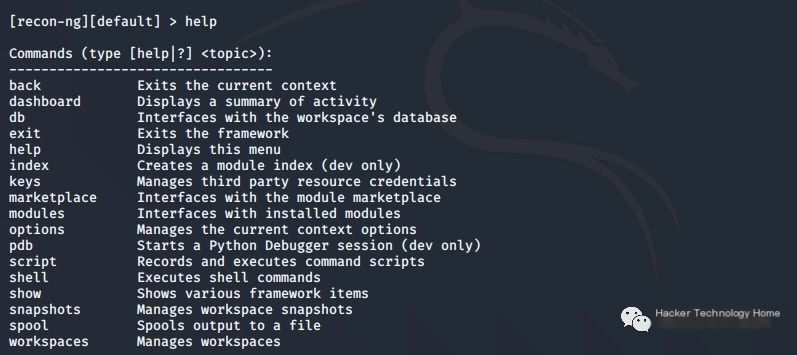
RECON-NG
RECON-NG is a full-featured web reconnaissance framework based on Python. Enter help to view the meanings of all commands.
Active Information Gathering
“Layer 2 Discovery — nc remote transfer using arping”
Layer 2 discovery uses the ARP protocol and is carried out under a local area network.
Layer 2 Discovery—nmap (Commonly Used)
Layer 2 Discovery—Netdiscover (nc remote transfer)
Layer 2 Discovery—Scapy
Layer 3 Discovery
Advantages: Routable, relatively fast Disadvantages: Slower than Layer 2, often filtered by border firewalls Protocols: IP, ICMP protocol. Conducted over a wide area network
Layer 4 Discovery
Advantages: Routable and results are reliable, not likely to be filtered by firewalls, can even find hosts where all ports are filtered. Disadvantages: Firewall with state-based filtering may filter scans, slow for full port scans TCP: Unsolicited ACK-RST, SYN-SYN/ACK, RST UDP: ICMP port unreachable, no response
All TCP scans are based on variations of the three-way handshake to determine the state of the target port.
Service Scanning
SNMP: Simple Network Management Protocol Community strings Information queries or reconfiguration Identify and bypass firewall filtering
SNMP Scanning
Not very useful; current servers restrict SNMP access to specific IPs.
SMB Scanning
The protocol has historically presented the most security issues in Microsoft, is complex to implement, and by default is open with file sharing.
WAF Identification
Vulnerability Scanning
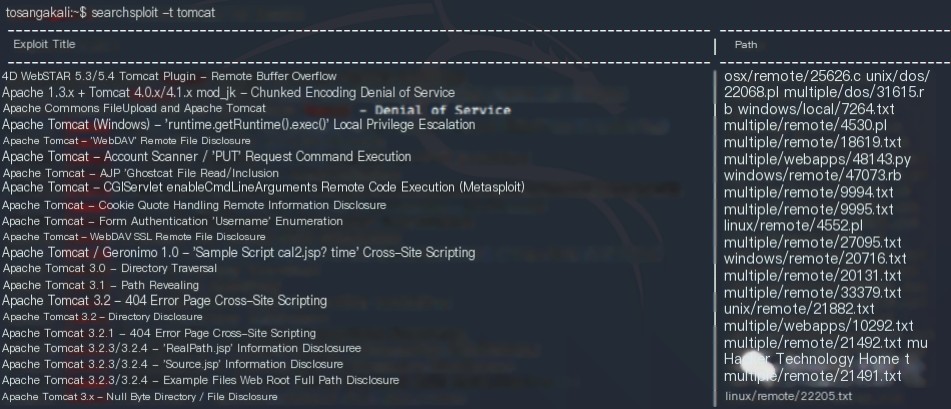
Kali integrates exploitation tools. Using searchsploit, we can search for existing software vulnerabilities and exploitation codes.
Additionally, NEXPOSE is a powerful vulnerability scanning tool for enterprises that can perform login or black-box scans on web pages and operating systems. NEXPOSE scores the identified vulnerabilities based on CVSS ratings and can generate reports.
Privilege Escalation
Admin escalates to System
Packet Sniffing
Basic Information Gathering
When we acquire root privileges on a host, we should gather as much information as possible.
cmd with m privileges Can only be used on XP systems Via service method SC Create syscmd binPath= “cmd /K start” type= own type= interact SC start syscmd
Covert Injection The above methods create a separate process, which might be detected. You can use pinjector for covert injection, injecting into a process with system privileges. Then, you can use nc for a remote shell.
Windows Systems Wireshark Omnipeek commview Sniffpass Linux Systems Tcpdump Wireshark Dsniff
— Feel free to reach out if there are any more sections you need help with!



