Author: Zhao LimingImproving database performance is crucial for efficient data management. It involves optimizing queries, indexing strategies, and hardware utilization to ensure faster data retrieval and processing times. Maintaining good database performance can significantly enhance the overall functionality of applications
Member of the Aikesen MySQL DBA team, familiar with databases like Oracle, MySQL, specializing in diagnosing database performance issues, analyzing transaction and lock issues, responsible for handling daily maintenance problems in customer MySQL and our self-developed DMP platform, and very interested in open-source database technologies.
Source of this article: Original contribution
* Produced by the Aikesen Open Source Community, original content must not be used without permission, please contact the editor for republishing and cite the source.
Tshark, tcpdump, and Wireshark are all network packet capture tools that can capture and analyze packets on the network.
An open-source, command-line-based network packet capture tool. It can capture and analyze network packets, running on nearly all Unix and Linux systems. It can capture packets in real-time network communication, then parse and process packets through filters and other parameters.
The command-line version of Wireshark, also an open-source network analysis tool. It can capture and analyze network traffic data in the command line and use Wireshark filters to extract needed data, also supporting automation of the analysis process by integrating with various scripting languages (e.g., Python and Perl).
It is a popular network protocol analyzer that supports capturing packets from online networks or local files, providing a graphical user interface to display packet contents. It can parse and display various network protocols, offering powerful analysis tools and filters; compared to tshark and tcpdump, Wireshark’s advantage is its user-friendly GUI interface, facilitating easier analysis and debugging of network protocols for users.
These tools can all capture and analyze network packets directly, but they differ slightly in usage and functionality. Typically, we first capture packets on the target server with tcpdump or tshark to generate a pcap file, then analyze it on a host with Wireshark. This article will share some usage tips of tshark and Wireshark.
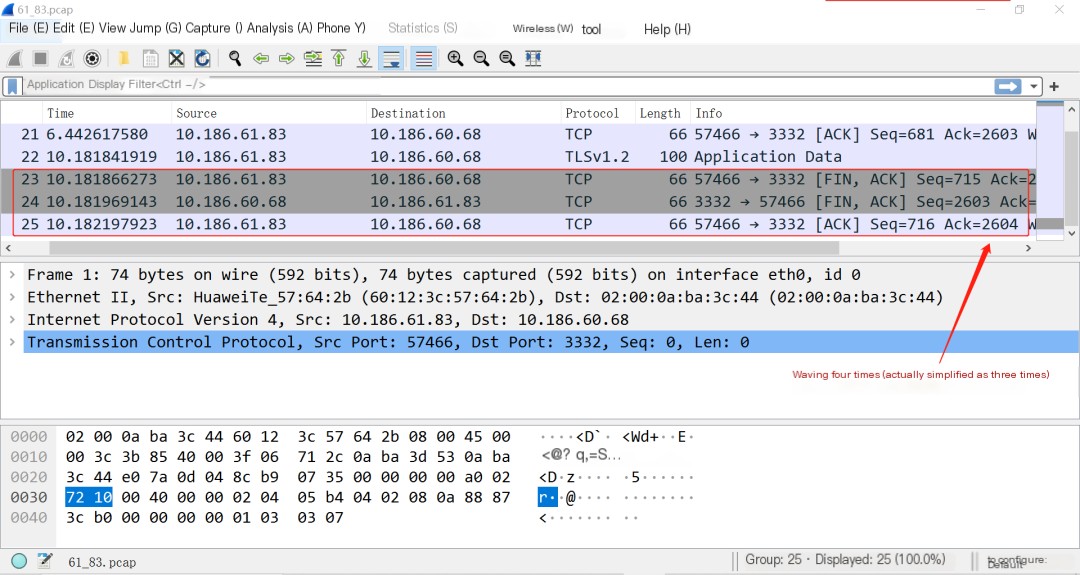
The three-way handshake and four-way wave in the TCP protocol are the processes for establishing and closing a TCP connection.
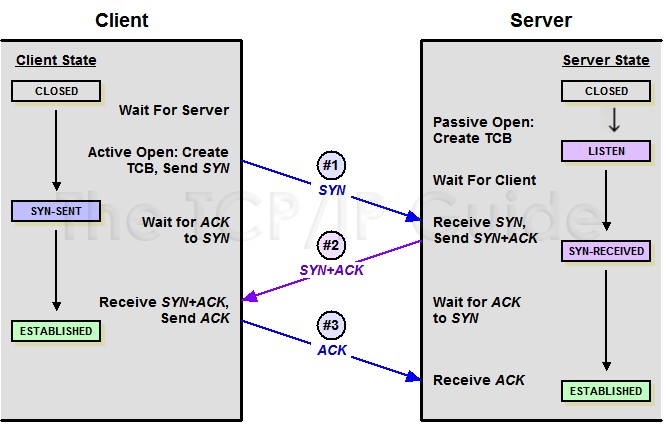
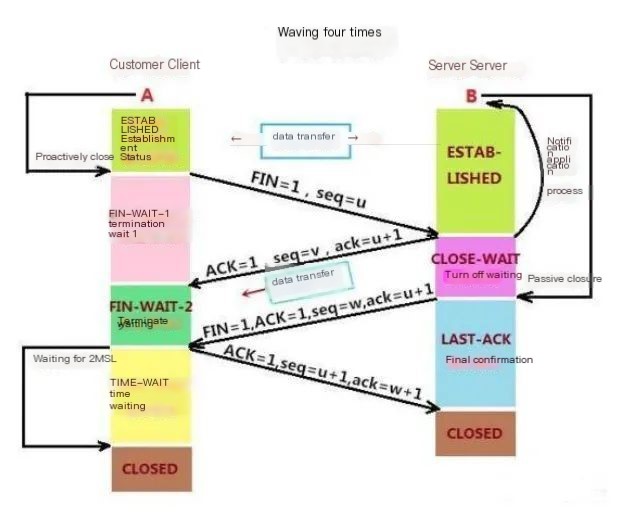
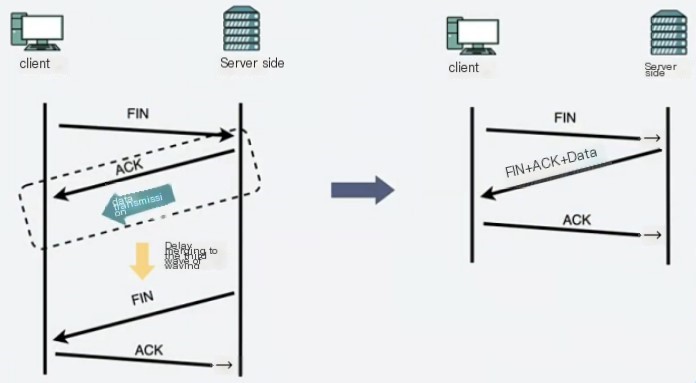
The three-way handshake is used to establish a connection, it’s the process of both parties negotiating to establish a TCP connection. The four-way wave is used to disconnect, it’s the process of both parties ending the TCP connection. Sometimes the four-way wave can turn into three waves (if no data is being sent, 2 packets will be combined for transmission).
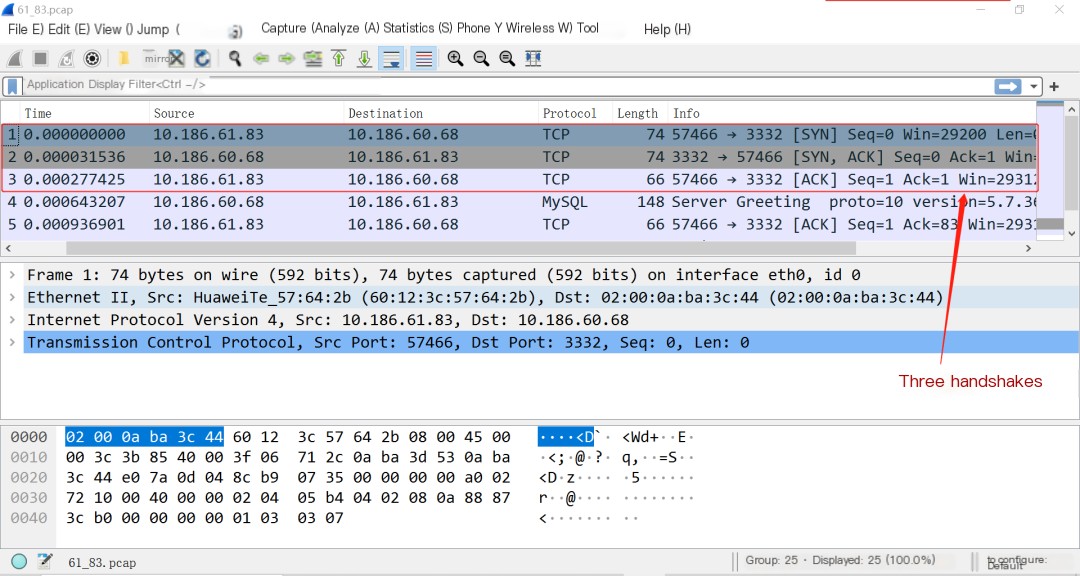
We can observe the specific process of TCP connection establishment and disconnection through packet capture with tshark.
TCP (Transmission Control Protocol) headers have 6 flags, which are URG, ACK, PSH, RST, SYN, FIN, with hexadecimal values of: 0x20, 0x10, 0x08, 0x04, 0x02, 0x01, where each flag’s meaning is as follows:
Similar to previous methods, just adjust the IP address and port number as needed.
Tshark can also capture packets on the server first, then use Wireshark’s graphical window for further analysis.
The following screenshot shows the process of the three-way handshake and four-way wave.
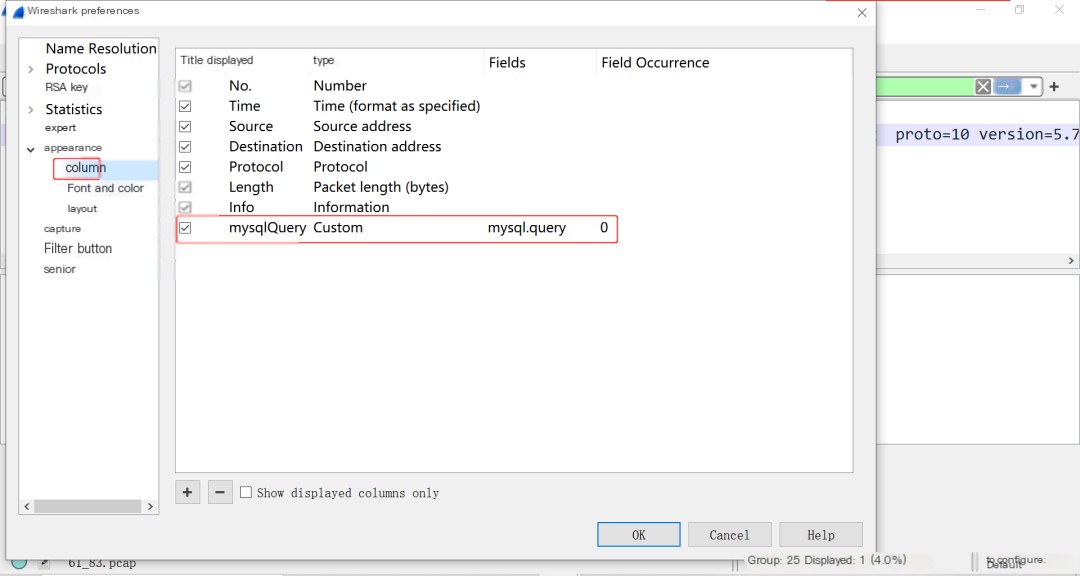
Similarly, fields can also be displayed in Wireshark:
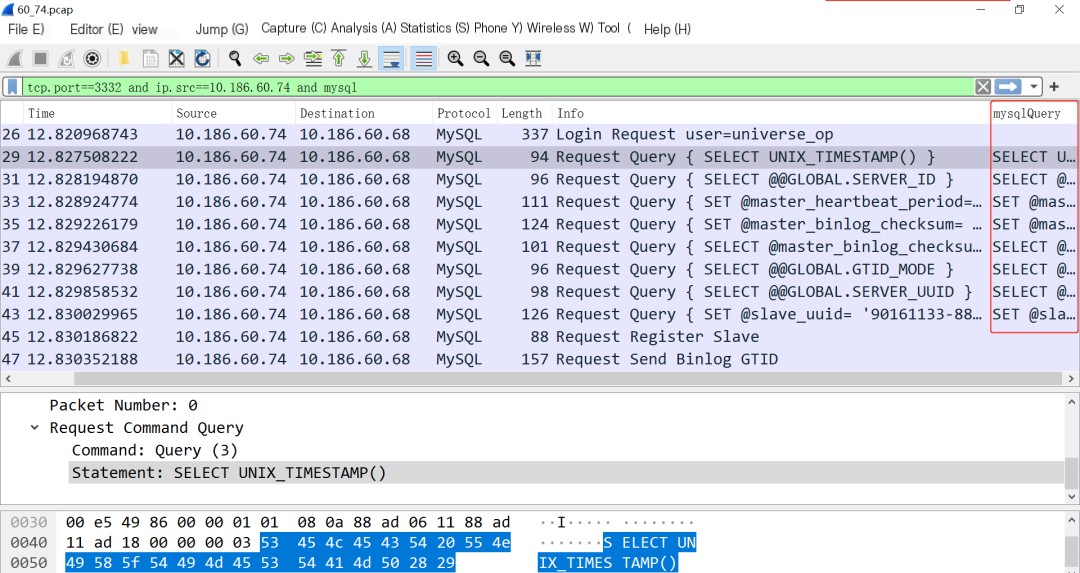
The content in the filter expression below indicates: filter and display packets with TCP port 3332, source IP address 10.186.60.74, and protocol type MySQL, as shown in the effect:
Tshark, as Wireshark’s command-line tool, compared to tcpdump, has many advantages:
It has more filtering conditions than tcpdump, enabling more precise filtering of desired packets. Tshark supports all the features of Wireshark filter syntax and provides more advanced functions.
Can output captured data in various file formats and standard output, while tcpdump’s output format is very limited.
The output is more readable, as it parses packets and displays various included data, such as protocols, parameters, and error information, which is very helpful for packet analysis.
Consumes fewer system resources compared to tcpdump, and doesn’t need to store all data in memory, thus able to handle larger data streams.
Supports more network protocols, including IPv6, IS-IS, IPX, etc., whereas tcpdump supports a relatively smaller number of protocols.
In conclusion, in some more complex packet analysis and network diagnosis scenarios, tshark and Wireshark are more suitable, while for simple applications only needing to quickly capture network traffic, tcpdump might be more appropriate.



