Introduction to the Article on TCP Stream
In today’s internet era, network security is an issue that cannot be ignored. As network technology evolves, network attack methods are becoming increasingly complex and covert. Therefore, network security professionals need to have certain technical skills and the ability to use tools. Among these tools is WireShark, a widely used network protocol analysis tool that helps users gain an in-depth understanding of the TCP Stream and the transmission process of network data packets, enhancing network security defense capabilities. This article will introduce WireShark’s object export functionality to help readers better utilize this feature for network packet analysis and security protection tasks.
File Transfer with TCP Stream
When users use various applications to transfer files, the protocol used at the transport layer is mostly TCP. Sometimes a file may be transmitted with a single data packet; other times, due to the large size of the data, it may need to be split into multiple packets for transmission, yet these packets maintain a certain sequence in transmission. We refer to these orderly data packets as a stream. Wireshark’s “Stream Tracking (TCP Stream)” function can reassemble all captured communication packets into a complete session or file and restore them.
Object Export
Object Definition: If two devices are transferring files over a network, then the transferred file is considered an object.
Packet Example: https://wiki.wireshark.org/SampleCaptures
 />
/>
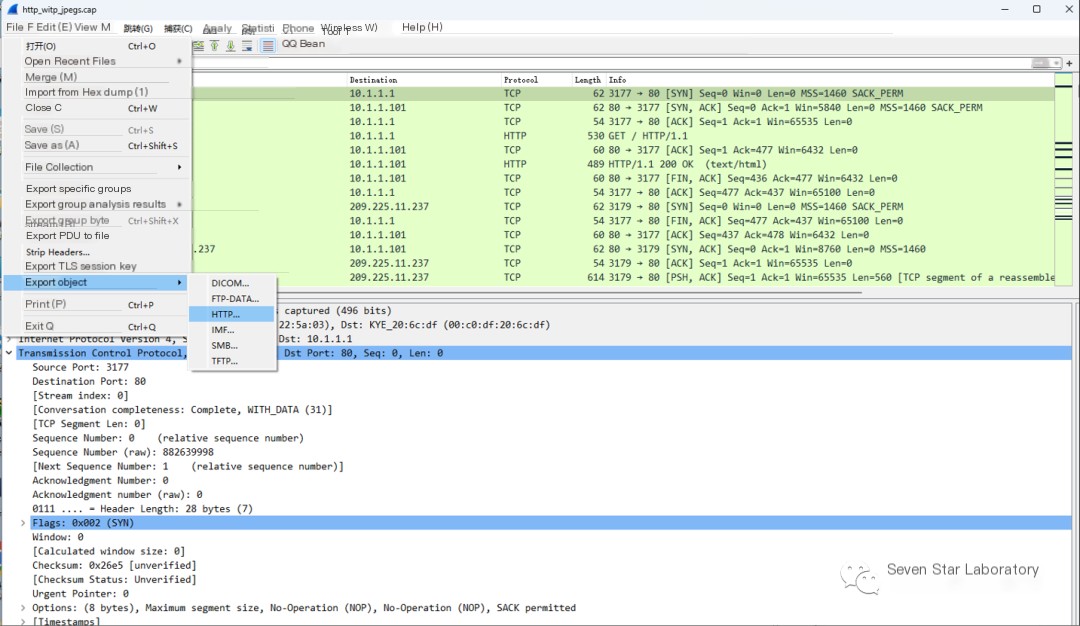
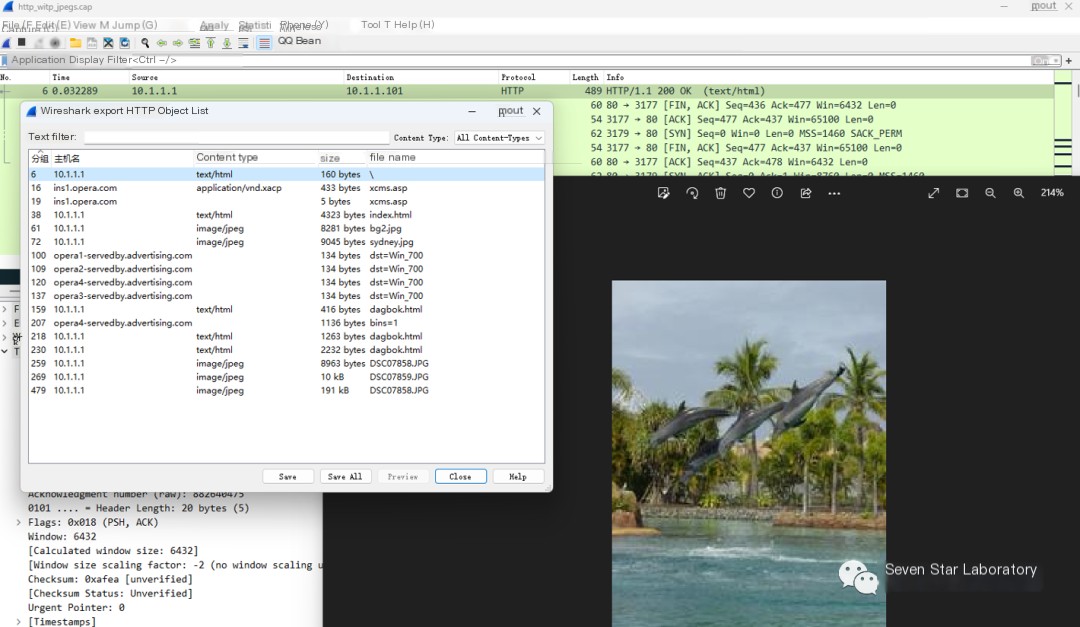
Open the packet using WireShark and then use Wireshark’s export object feature, File—Export Objects
 />
/>
Afterward, the files transferred using the HTTP protocol can be seen as follows:
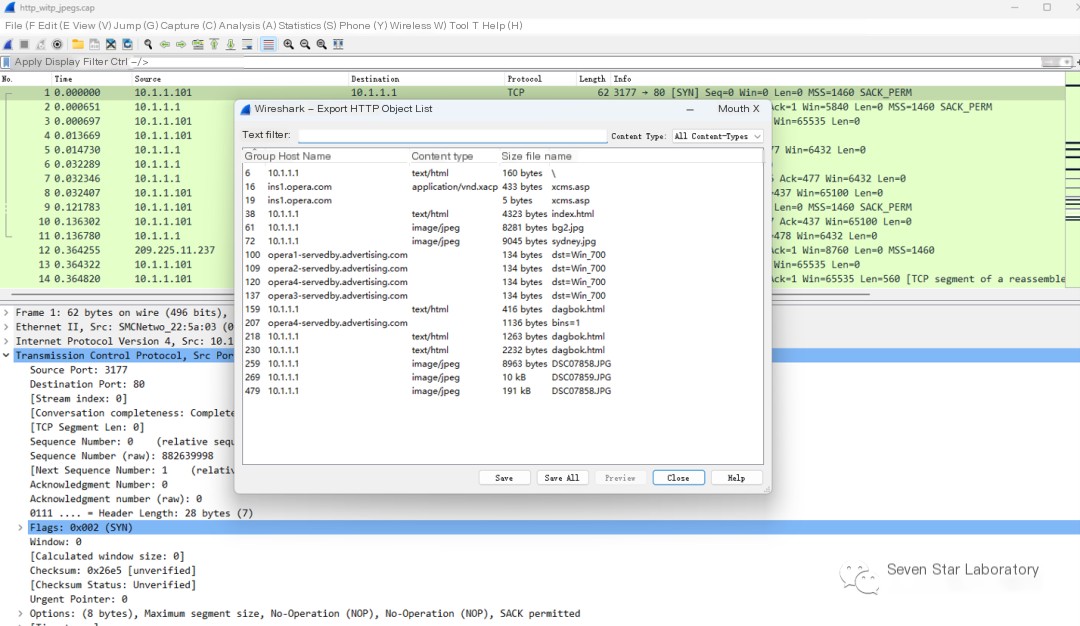
Then save the object locally using “Save”
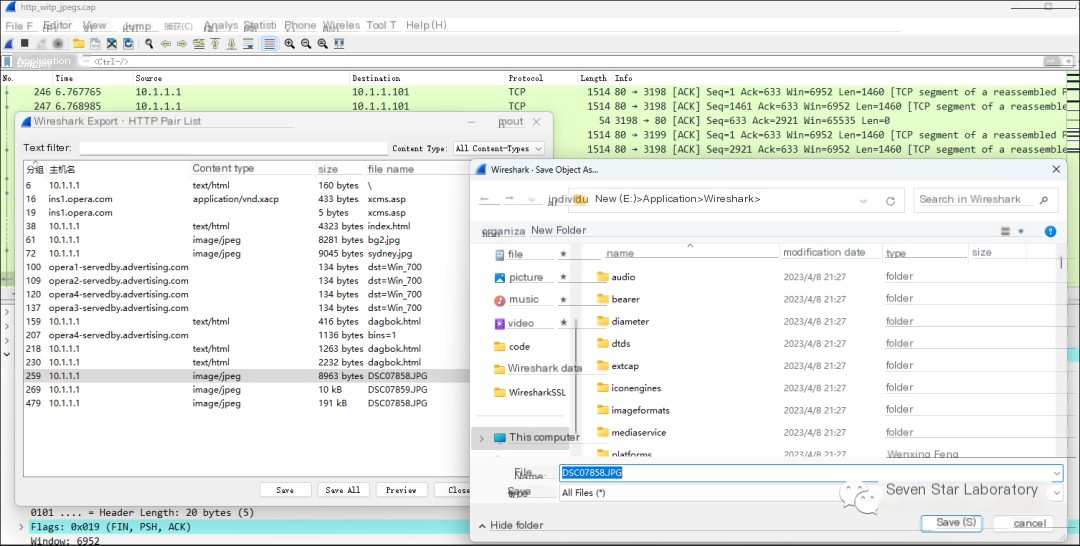
The image file is shown as follows:
Data Stream Class
First, use a display filter to filter packets
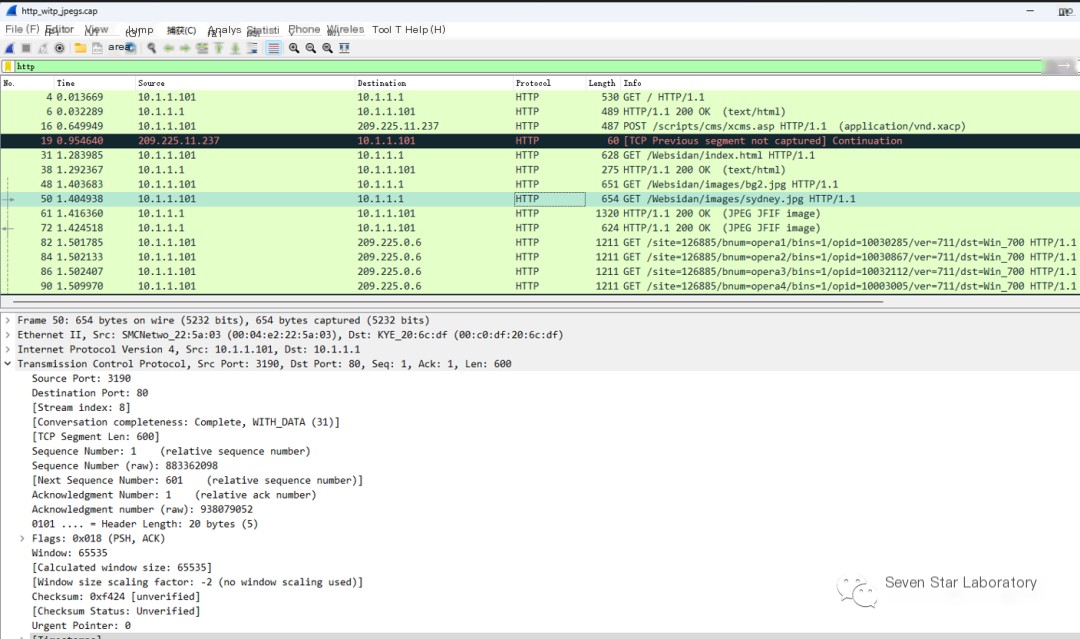
Then select a file packet to trace its data stream
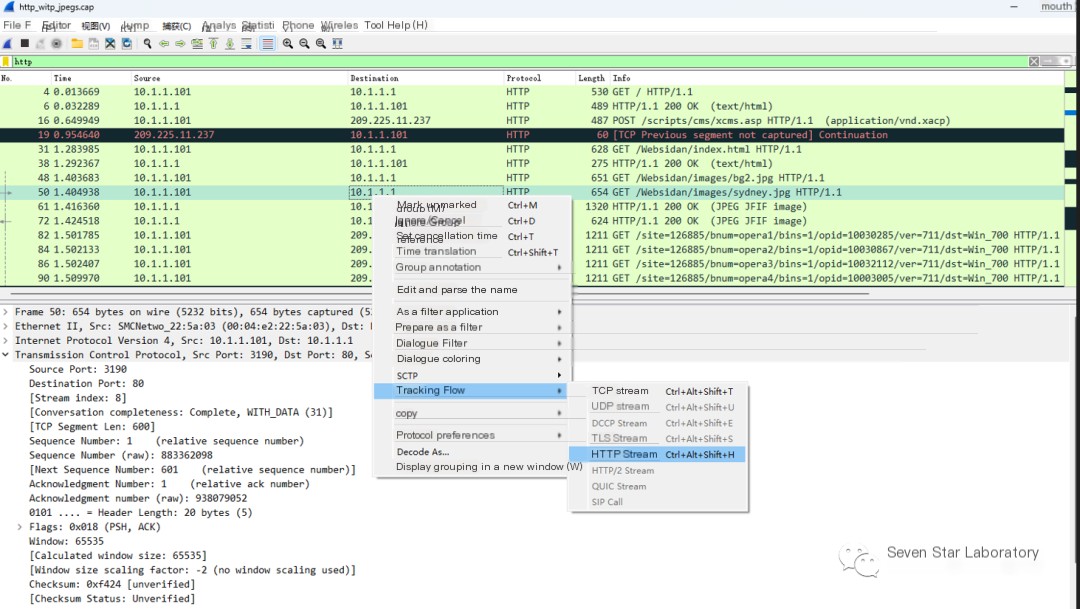
Select a direction of the data stream in the lower-left corner of the following diagram
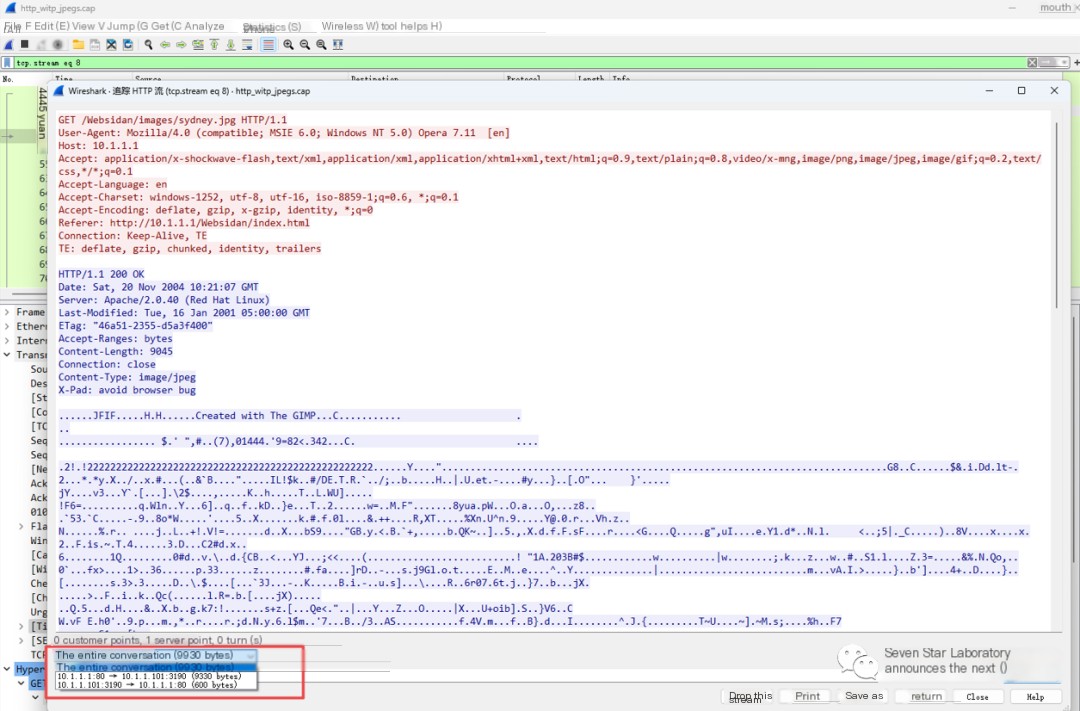
Here, we select the data stream of the echo packet and choose “Raw Data” for display or saving data in the lower right corner
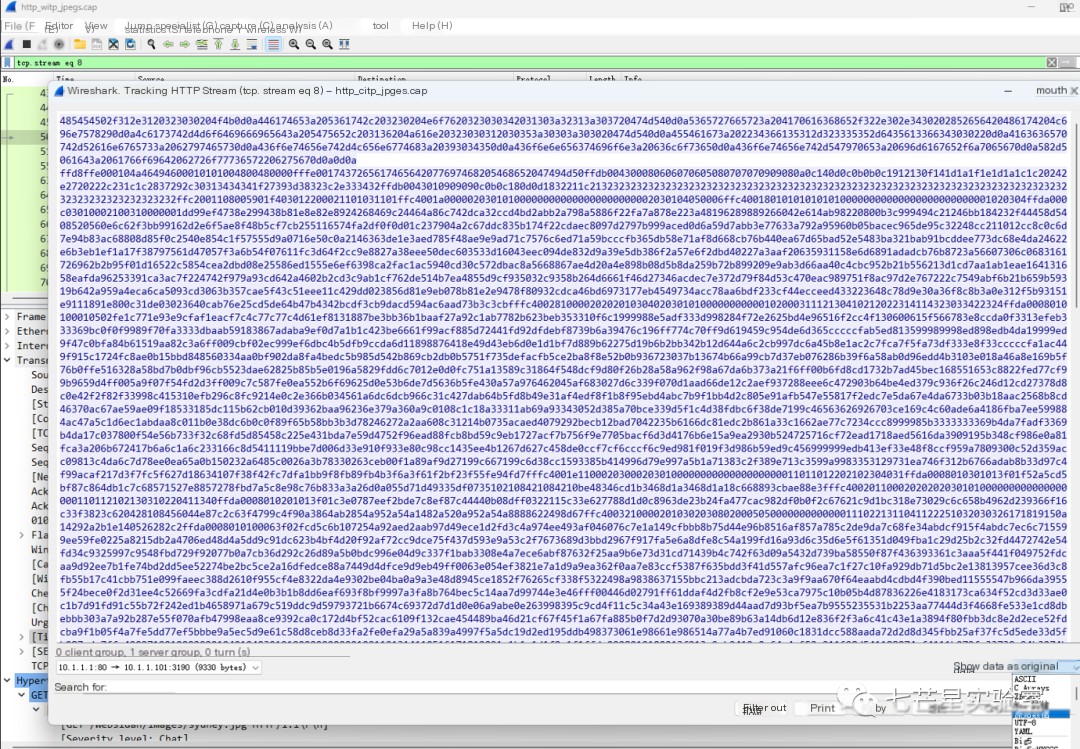
Save the file as a bin file, open it using Notepad++, and see the following content:
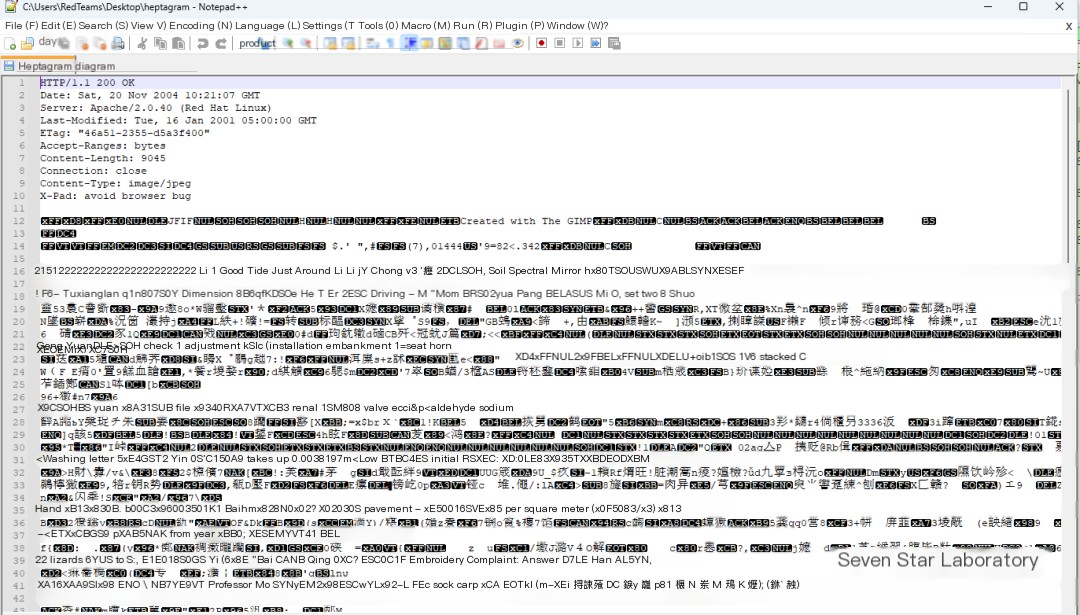
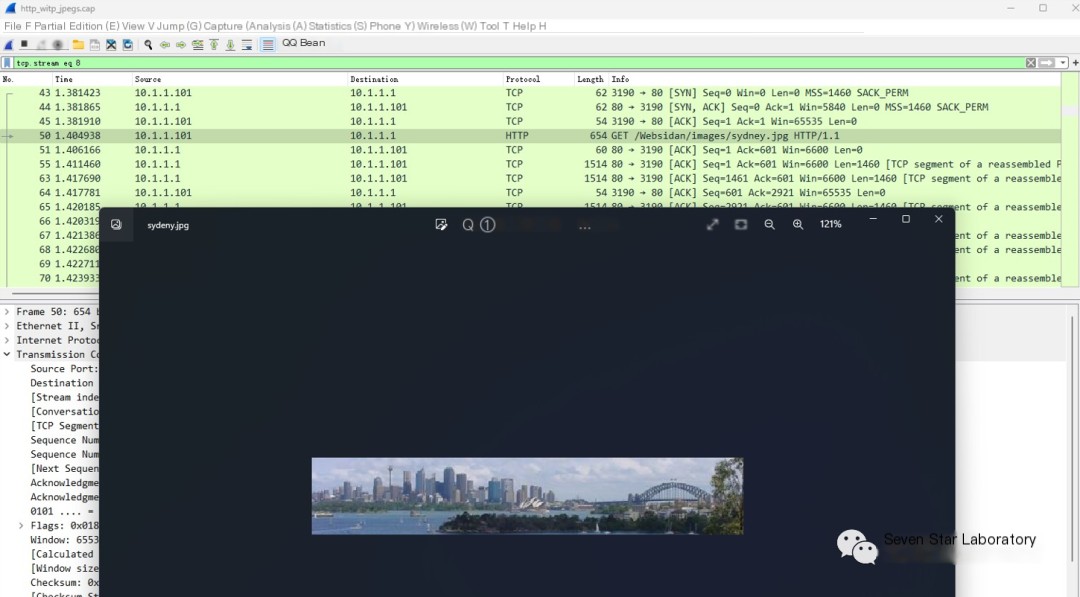
Remove the response header above, then save the file as xxx.jpg, and after checking the original image, you can get the following result:
Multi-File Class
Here, we use a CTF challenge as an example to introduce how to restore the original file from data packets split during transmission due to large data size:
Challenge Description: Caught a fly!
Challenge File: misc_fly.p.capng—https://pan.baidu.com/s/1kVyyCbt
Solution Steps: First, use Wireshark to open the corresponding traffic data packet misc_fly.pcapng
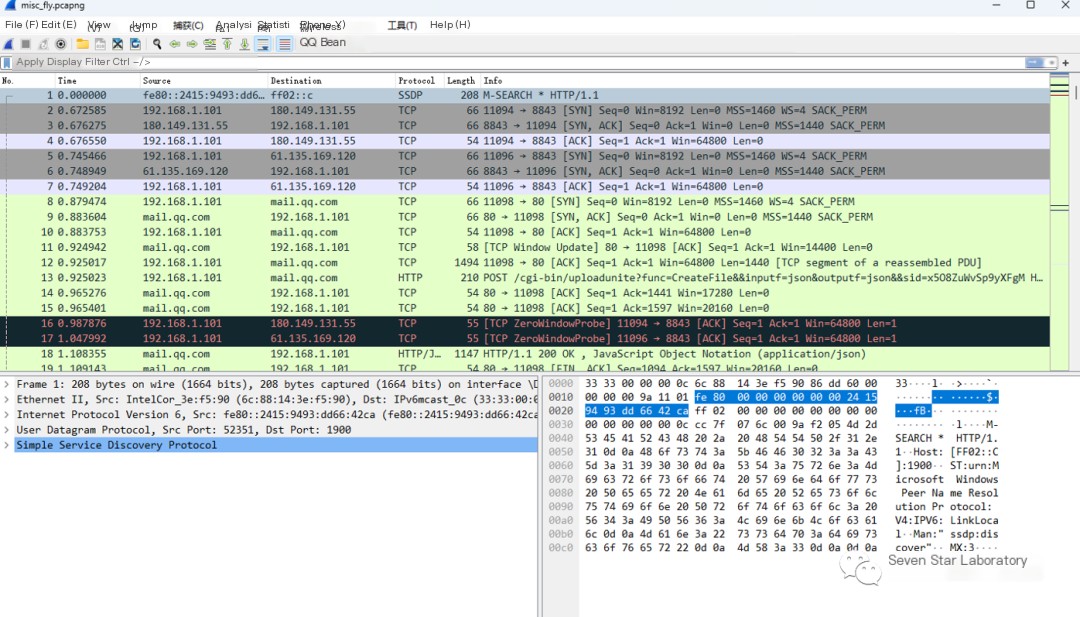
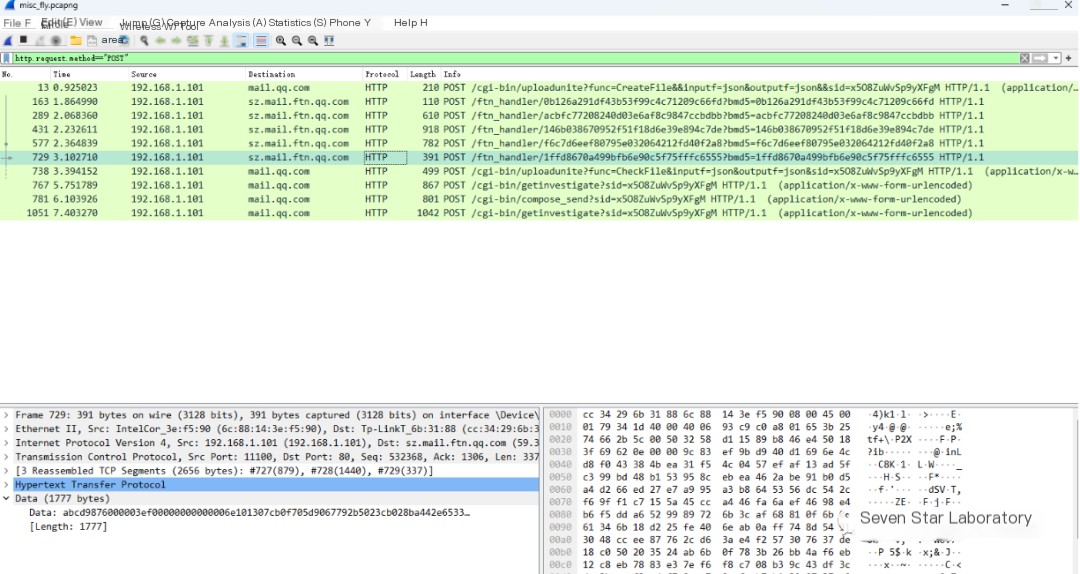
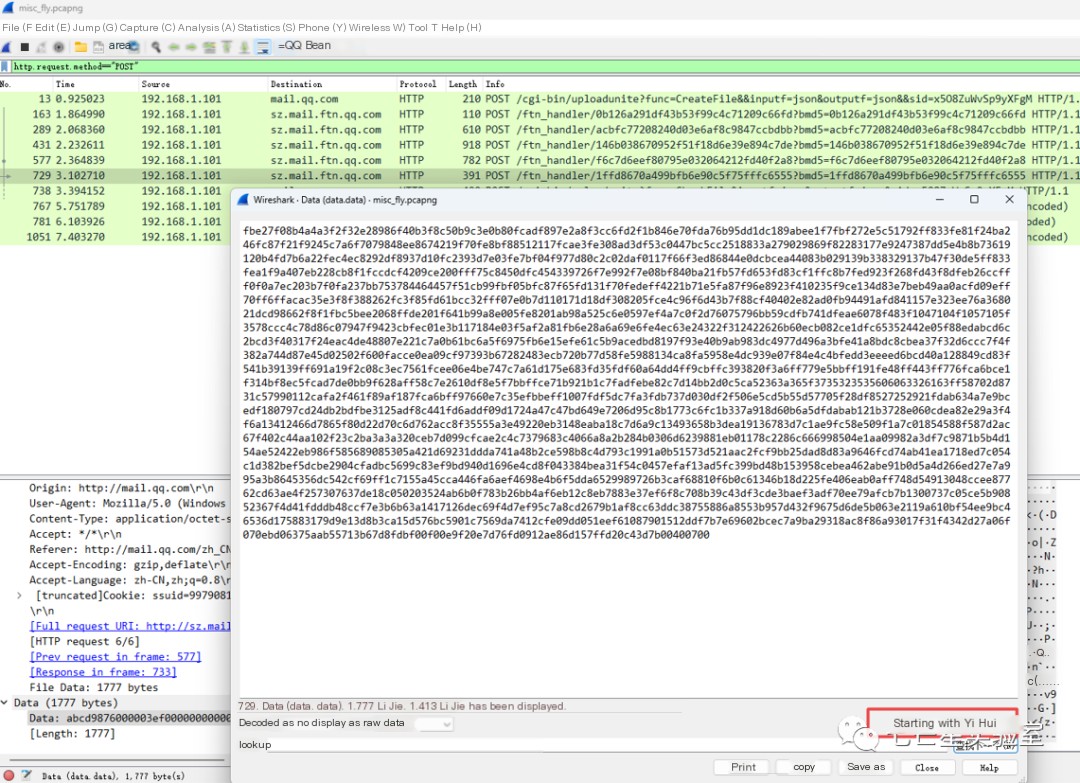
Use HTTP to filter the protocol
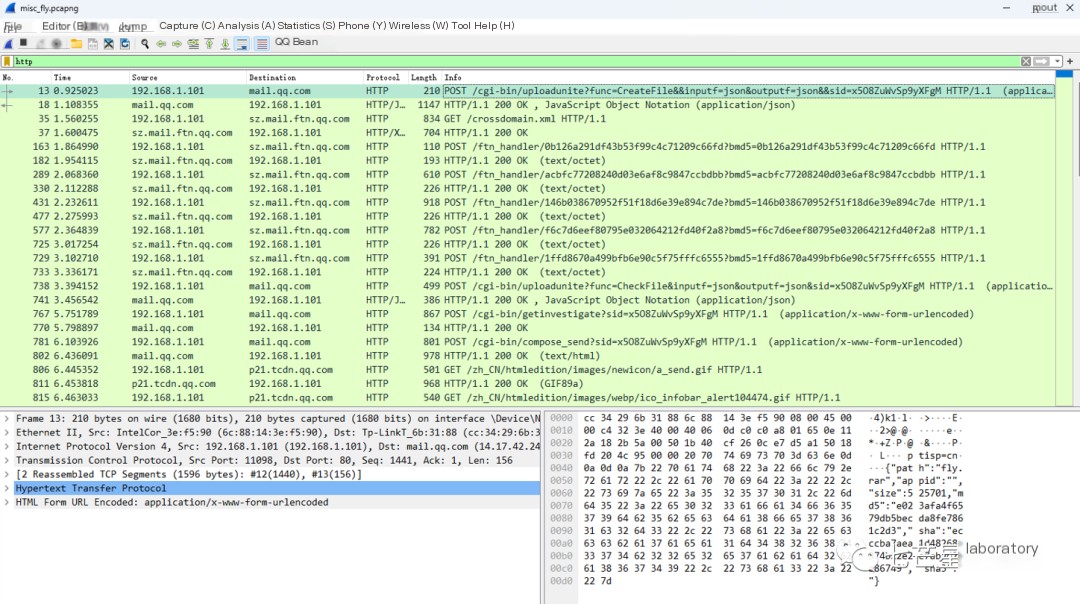
From the data stream, discover the keyword “fly.rar” in the request parameters, size 525701, with an md5 value of “e023afa4f6579db5becda8fe7861c2d3.” Considering our challenge “Caught a fly!” is likely related to this uploaded compressed package
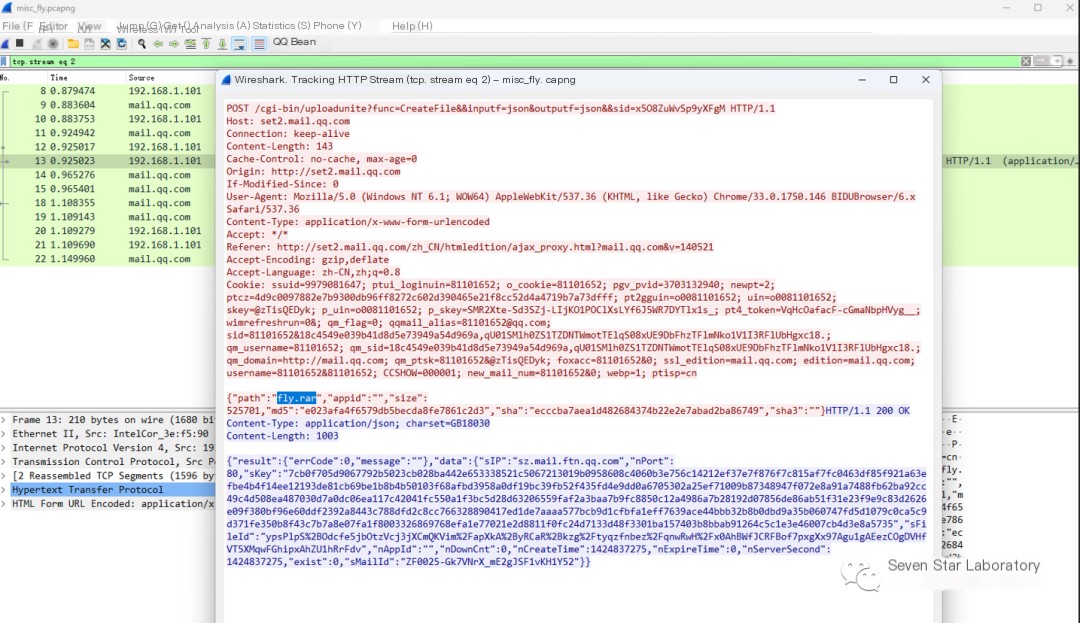
The next step is to restore this compressed package by first filtering the request type:
Language Type: JavaScriptCopy
http.request.method=="POST"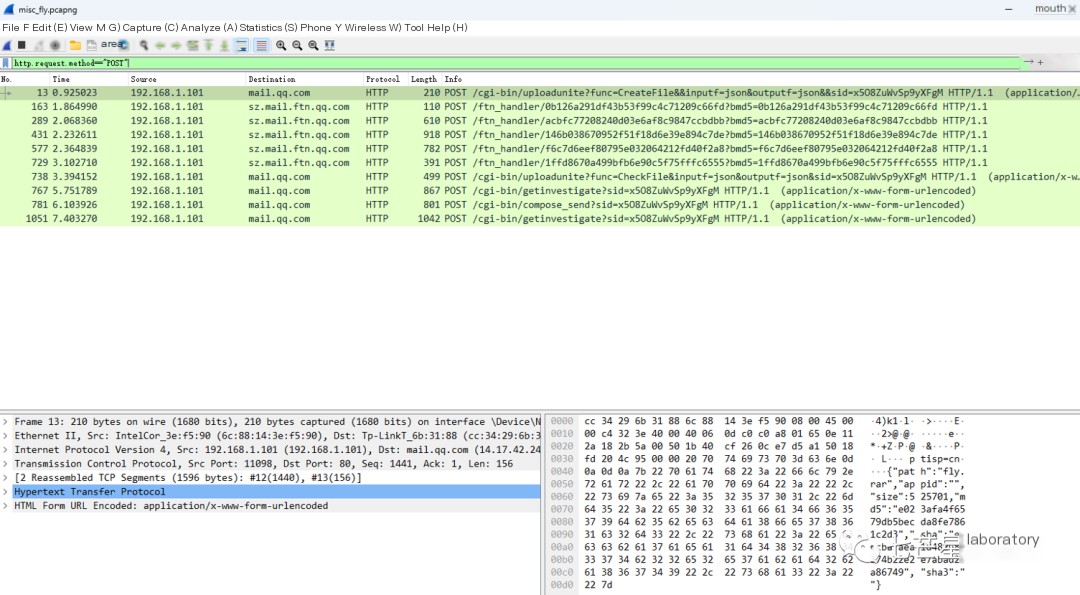
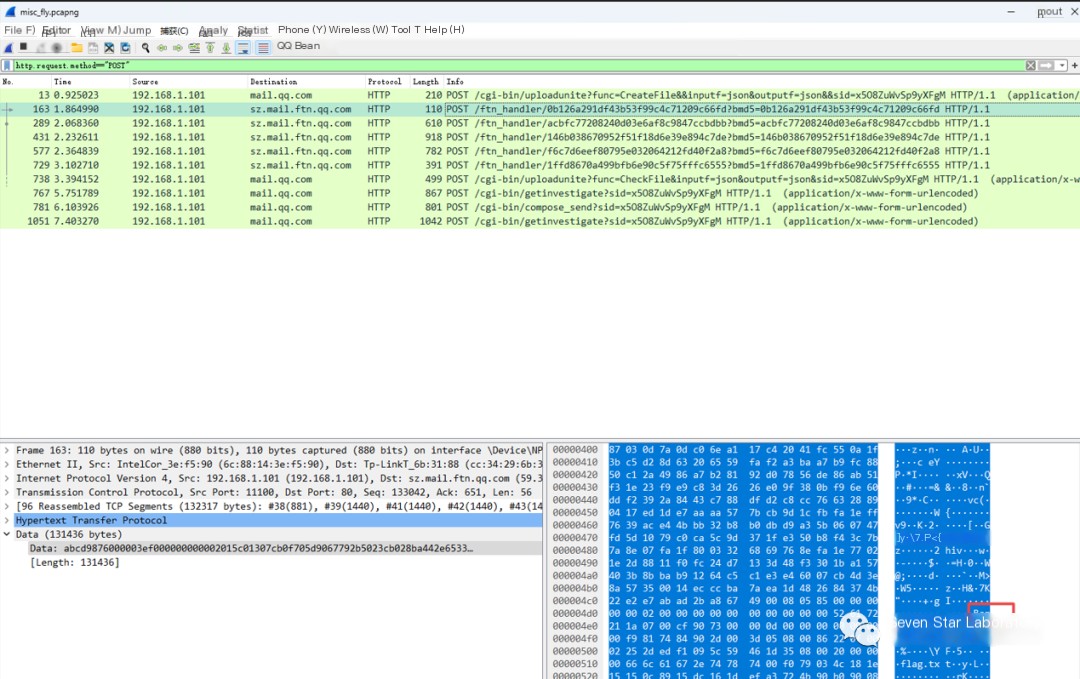
From the packet structure, it should be the second to sixth packets responsible for data transmission. Opening the second packet shows the MediaType length of 131436
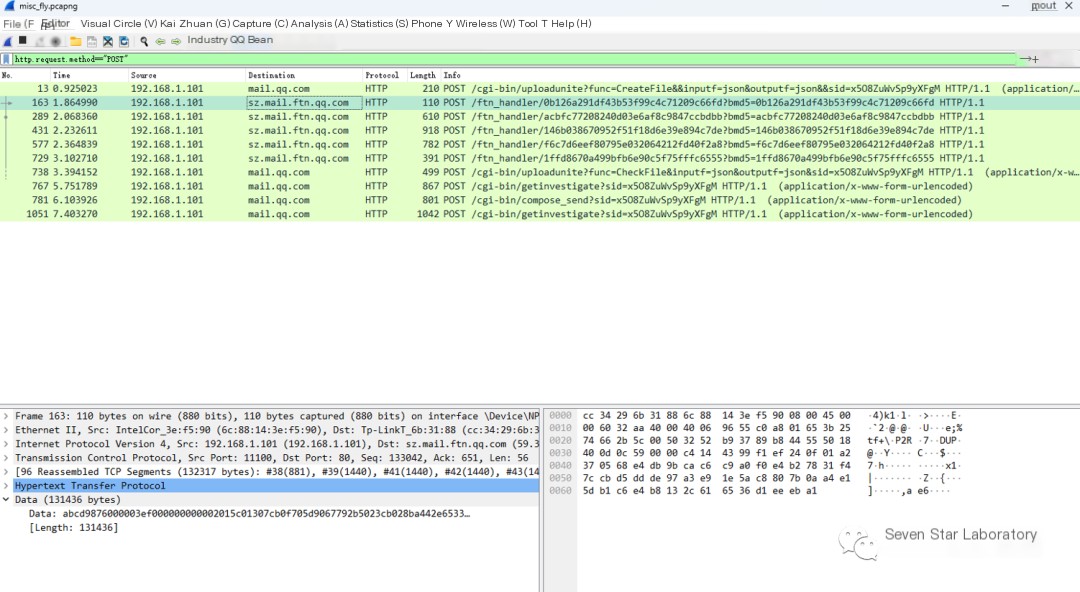
The second to fifth ones have the same length, and the sixth is 1777, which should be the last remaining piece of data
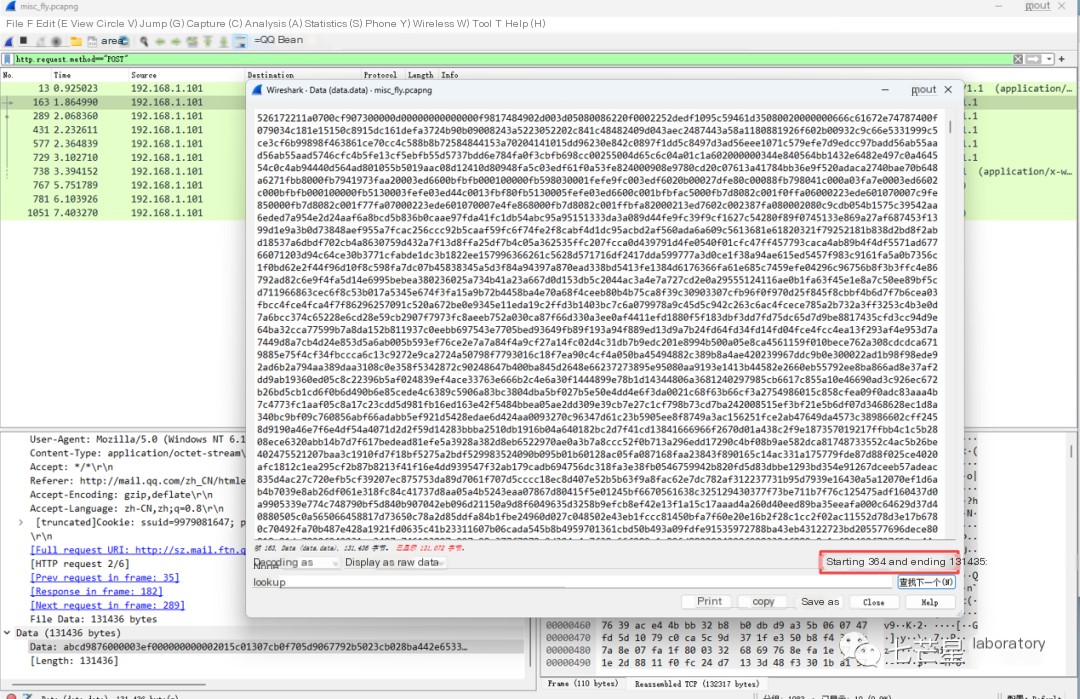
But 131436*4+1777=527521, which is 1820 more than the previously given length of 525701 for fly.rar. Since each packet contains header information, 1820/5 = 364, indicating that each packet’s header information is 364
Perform the same operation on each packet to get five files, then splice these files in order
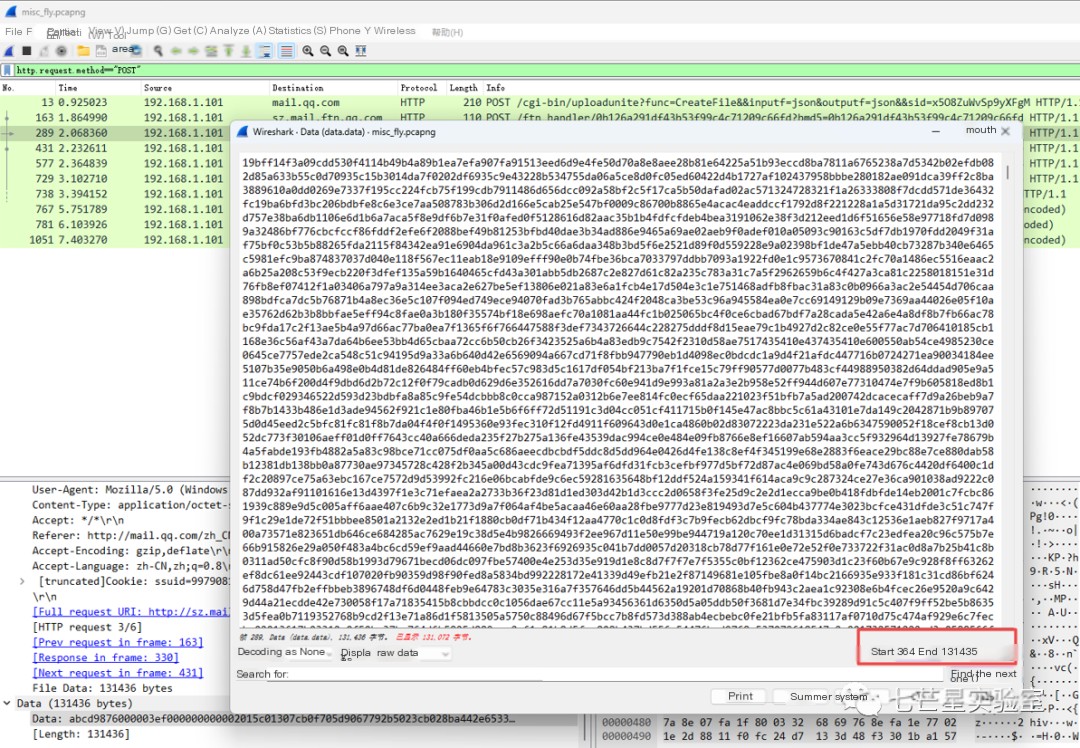
Merge the five files into one fly.rar file. Here, we use the Linux cat command directly to complete the task
Language Type: JavaScriptCopy
cat 1 2 3 4 5 > fly.rar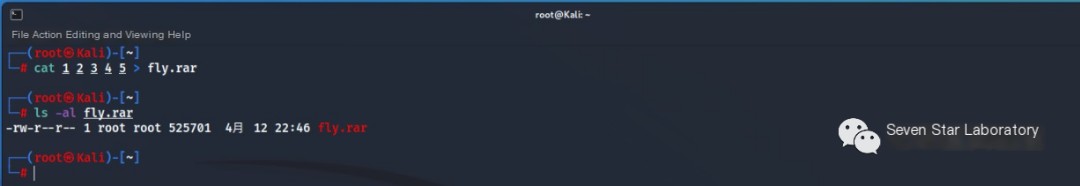
Recalculate the md5, and you can see the md5 value is correct
Language Type: JavaScriptCopy
md5sum fly.rar
However, upon opening the archive, you will find an issue:
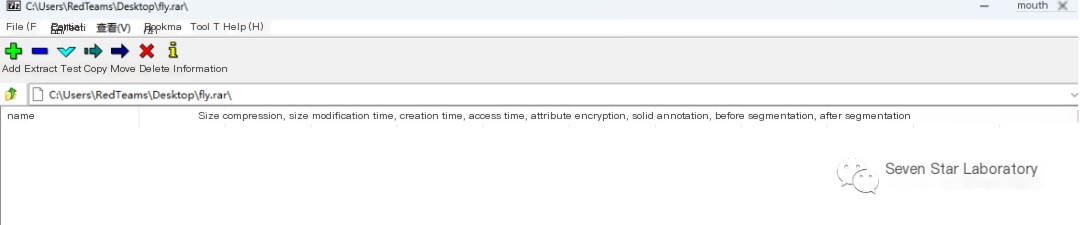
This is due to a pseudo-encryption setting; modify the encryption bit by changing 0x84 to 0x80
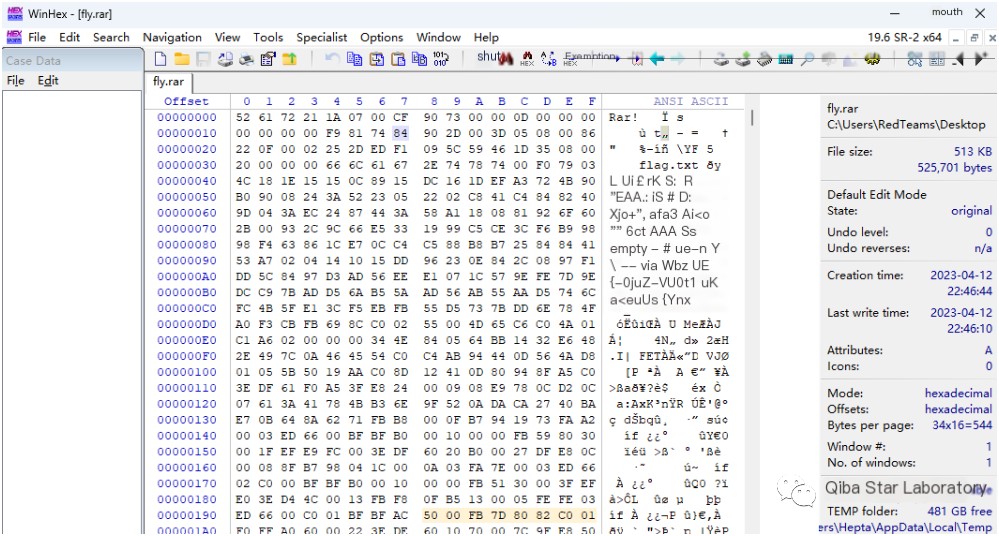
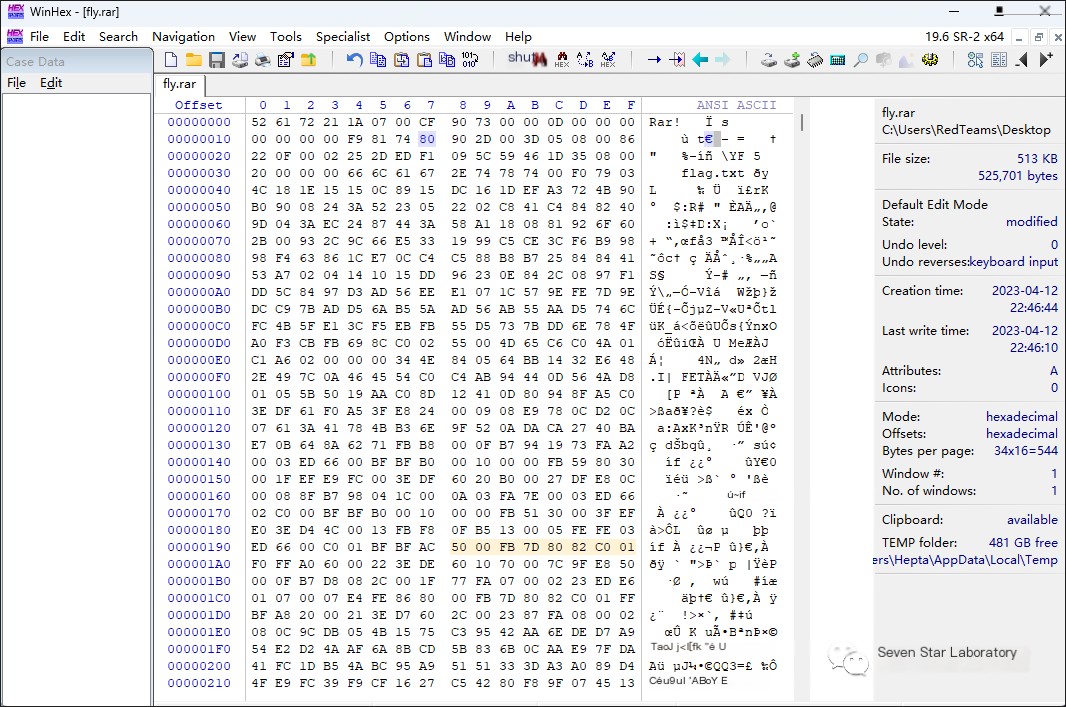
Then reopen the archive
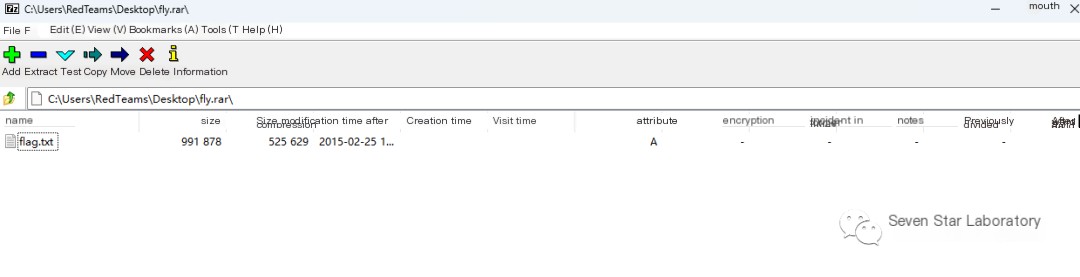
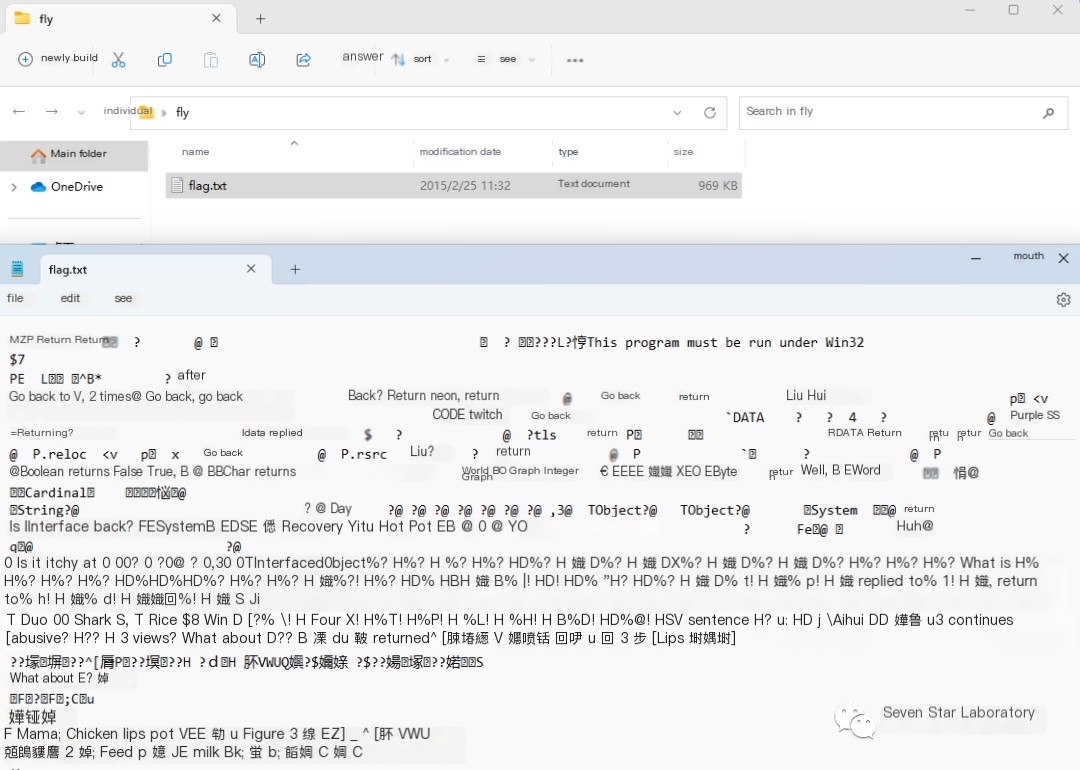
Inspect the file and discover it is a binary file:
Use binwalk to examine the file information and find that it contains multiple png files
Language Type: JavaScriptCopy
binwalk flag.txt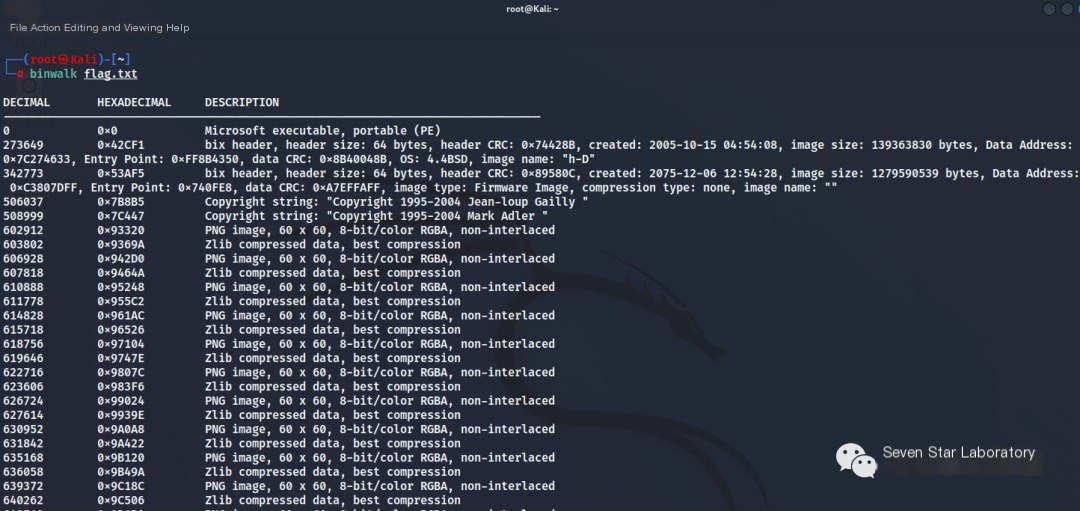
Then use foremost to separate files
Language Type: JavaScriptCopy
formost flag.txt
Among the many png files, a QR code is found
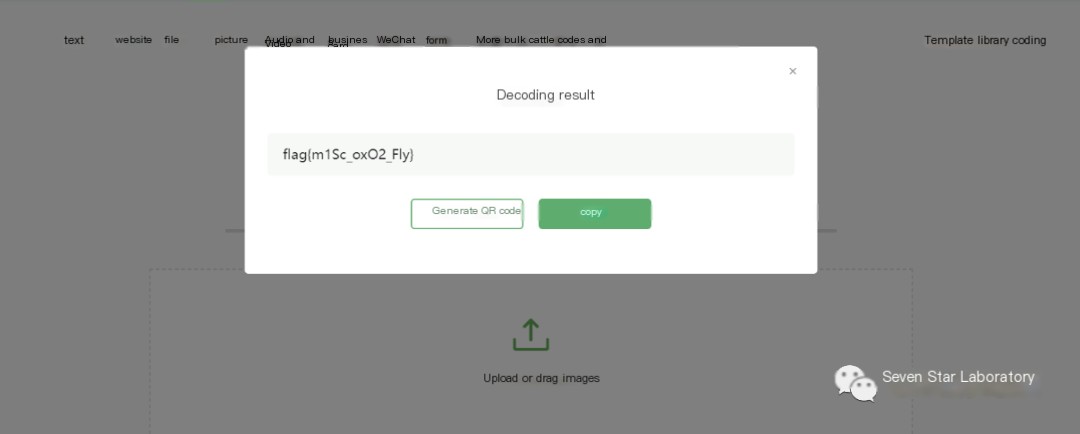
Then scan the QR code to obtain the flag
Conclusion
In this article, we introduced two methods for restoring transferred files when data packets are found during packet analysis using WireShark. For single large file segment transmissions, some complex operational steps and calculations may be needed, so special attention should be paid during handling.



