Environment: CentOS 7.6_x64
FreeSWITCH Version: 1.10.9
Python Version: 3.9.12
1. Background Description of CentOS 7.6_x64
PCM (Pulse Code Modulation) audio data is uncompressed audio sampling data, which is standard digital audio data converted from analog signals through sampling, quantization, and encoding.
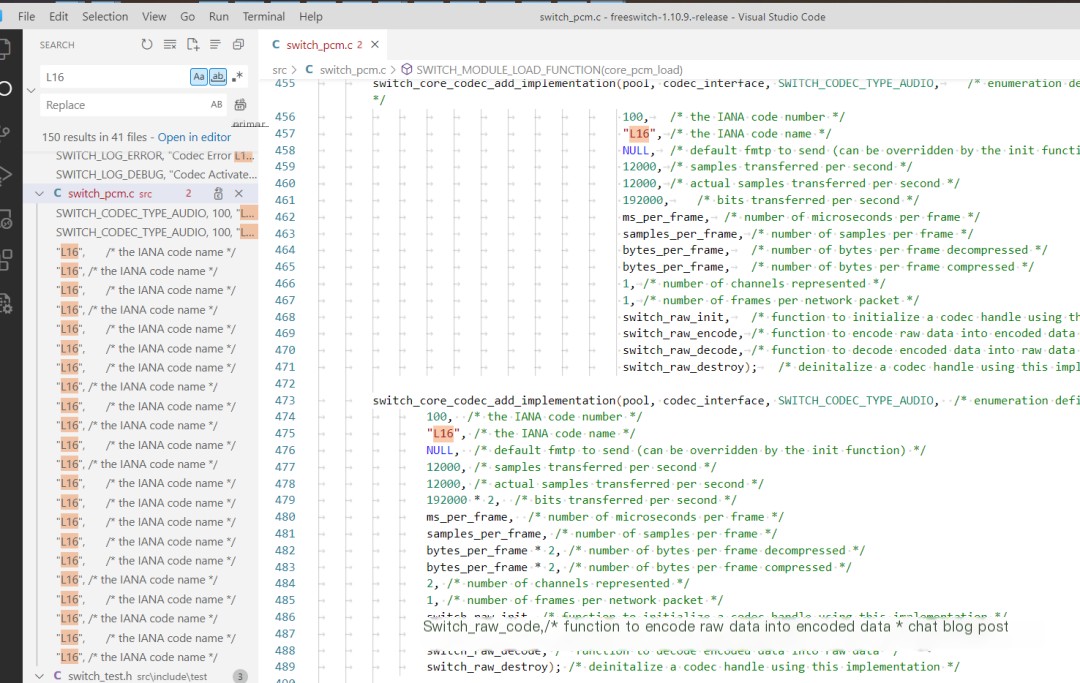
In FreeSWITCH, it is reflected as L16 encoding (in the switch_pcm.c file), and this encoding is used when interfacing audio with network platforms. Here we will document how to use FreeSWITCH for L16 encoded communication and how to retrieve raw data from pcap files.
 />
/>
The FreeSWITCH version used here is 1.10.9, and the operating system is CentOS 7.6_x64. For compiling and installing FreeSWITCH, you can refer to my previous article:
Install FreeSWITCH 1.10 from Source on CentOS7
2. Detailed Implementation on CentOS 7.6_x64
1. Configure FS and Softphone for L16 Encoding on CentOS 7.6_x64
1) Configure FS to support L16 encoding
File: freeswitch/conf/vars.xml
Add L16 encoding:
Language: javascriptCopy
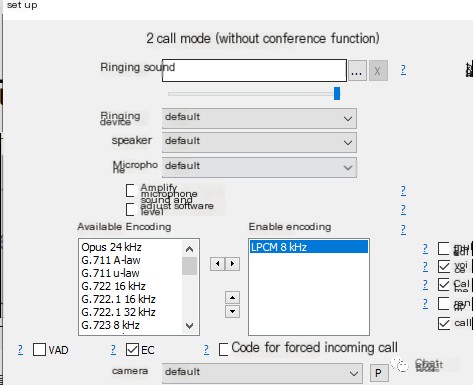
2) Configure the softphone to support L16 encoding
Using MicroSIP softphone, enable the codec: LPCM 8kHz
Detailed configuration is as follows:
 />
/>
2. L16 Codec Communication and Packet Capture on CentOS 7.6_x64
1) Configure Test Dialing Scheme
Call 6001 to play moh audio, details are as follows:
Language: javascriptCopy
2) Make calls using L16 encoding
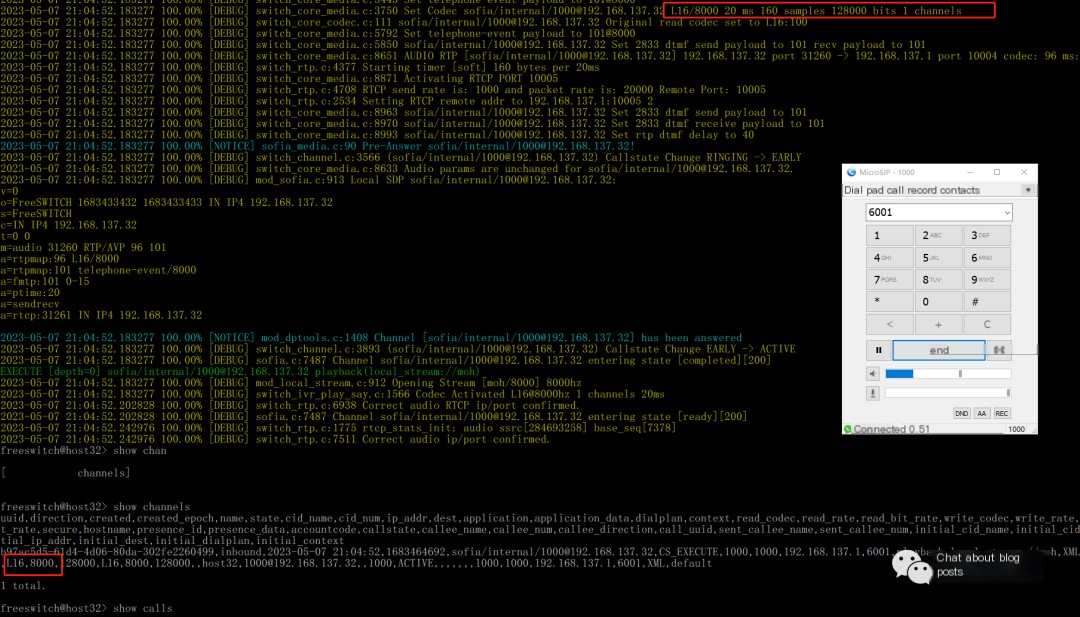
Register an extension, dial 6001 to make a call, and you can see in the console that L16 encoding is being used:
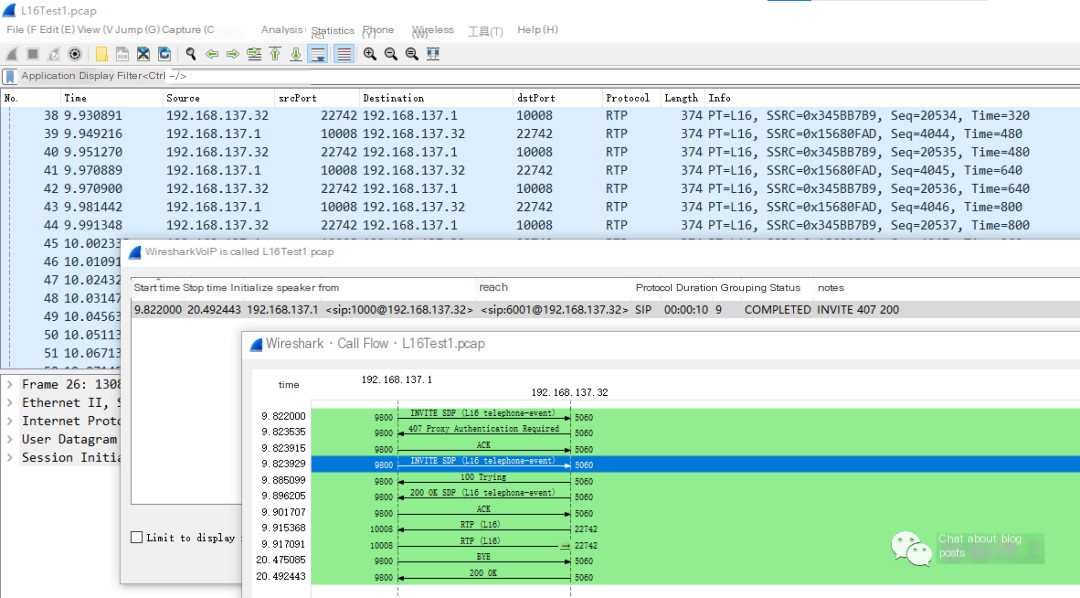
3) Data Capture and Encoding Examination
Use Wireshark to analyze the captured packets on the server:
3. Raw Data Extraction and Playback
Wireshark cannot play L16 format audio data:
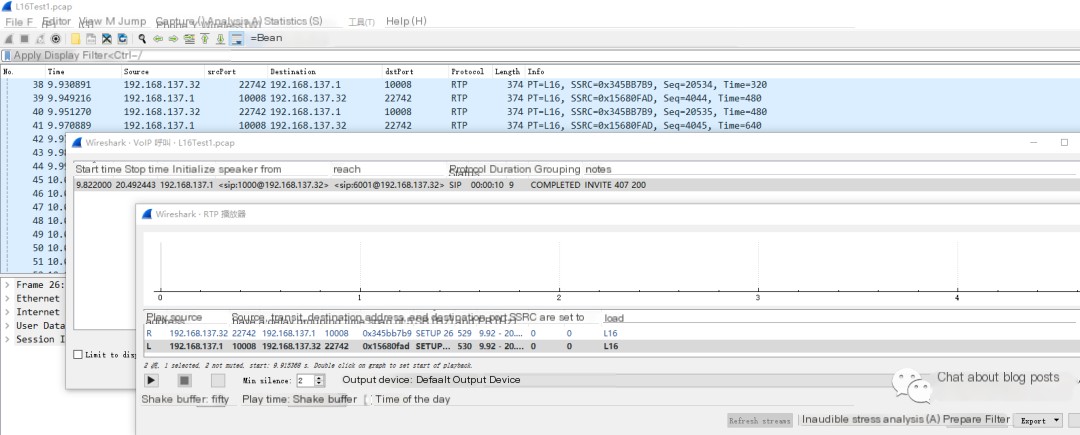
Data needs to be extracted from RTP payload, then played using other tools.
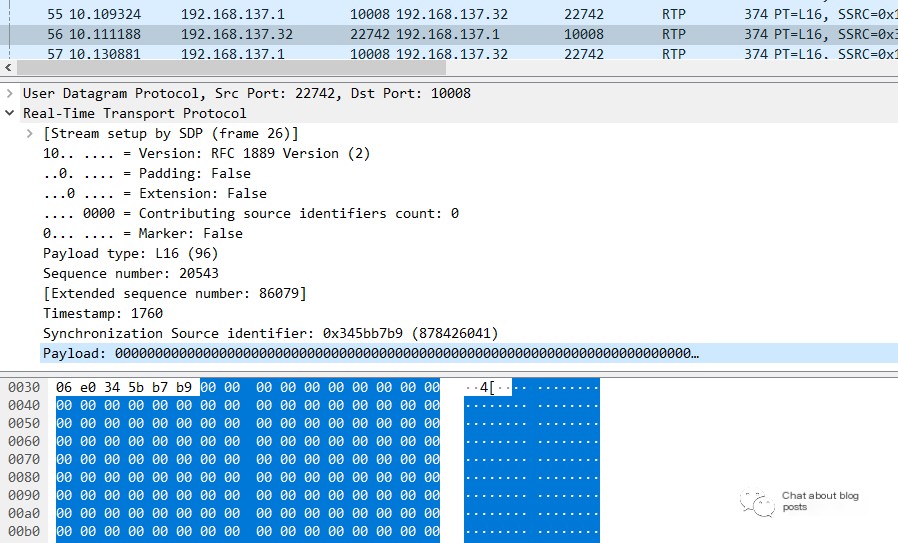
Here are two methods using Python to extract raw data, as described below.
1. Extract PCM Data Using libpcap from pcap Files
libpcap Version: 1.11.0b7
To learn how Python3 uses libpcap to parse pcap files, refer to this article:
Using libpcap Library in Python3 for Packet Capture and Data Processing
Here is an example of the PCM data extraction process.
File: export_raw_libpcap.py
Content is as follows:
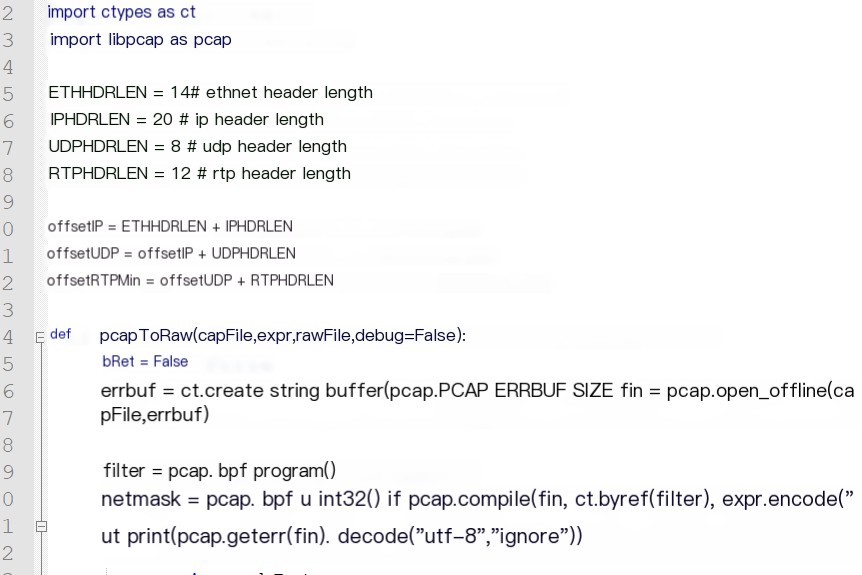
2. Extract PCM Data Using Scapy from pcap Files
Scapy Version: 2.5.0
Scapy Website: https://scapy.net/
Scapy Documentation: https://scapy.readthedocs.io/
Here is an example of the PCM data extraction process.
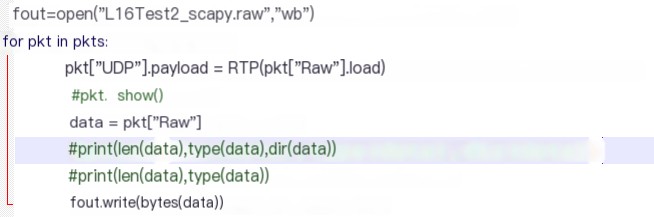
File: export_raw_scapy.py
Content is as follows:
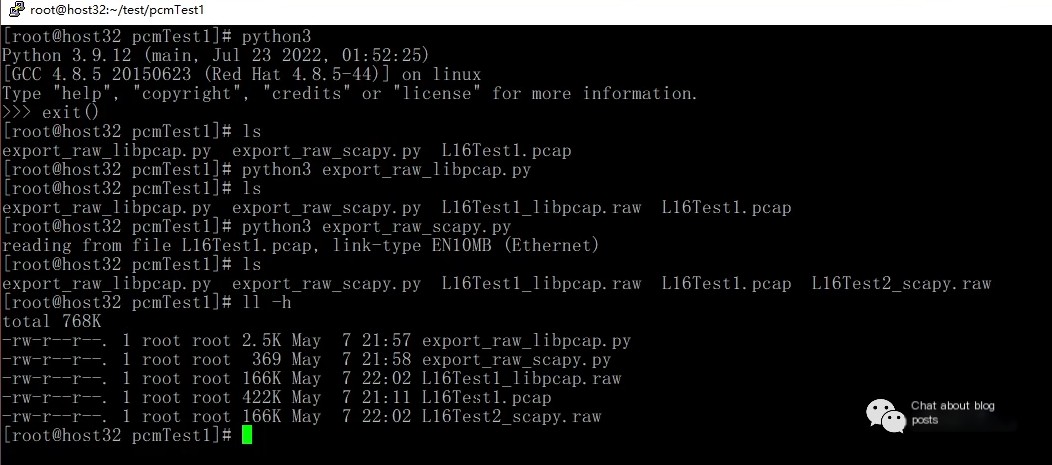
3. Execution Effects
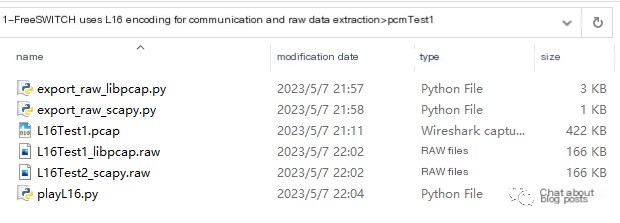
By running the Python script, you can extract L16 format PCM data from a pcap file, as shown below:
4. Playback of L16 Format Audio
Audacity, ffmpeg can be used for playback, detailed in my previous article:
Recording, Playing, and Converting PCM Audio
Note that the data captured by Wireshark is in big-endian byte order, and the exported PCM file is in s16be format.
Here is a method using pyaudio for playback on Windows 10.
pyaudio Version: 0.2.13
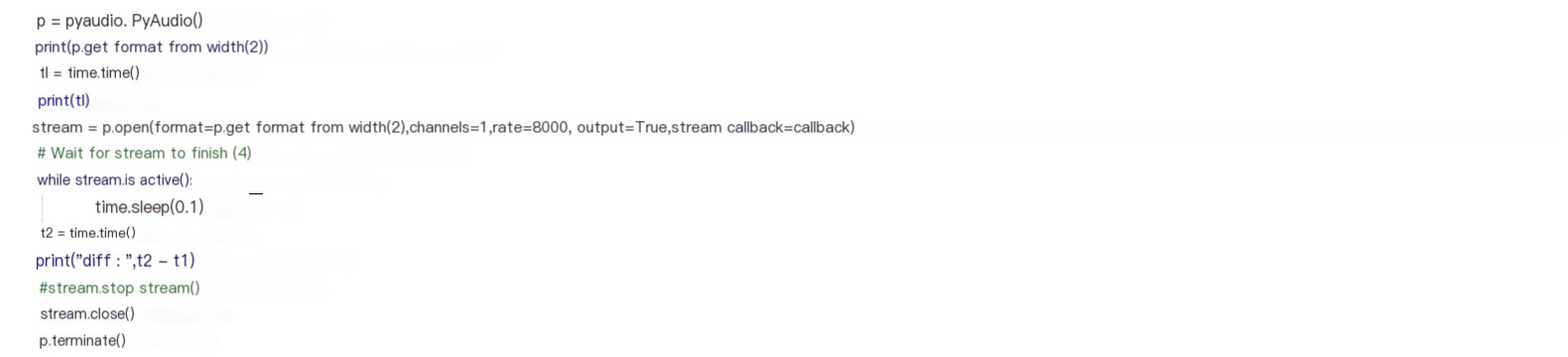
File: playL16.py
Content is as follows:
L16 encoded raw data extraction and playback effect video:
Follow the WeChat official account (chat blog) and reply 2023050701 to obtain.
4. Resource Downloads
The source code and binary files involved in this article can be obtained through the following channels:
Follow the WeChat official account (chat blog) and reply 20230507 to obtain.