0x01 Introduction
Hello everyone, we are the NOP Team. In our previous discussion, we talked about how to detect ICMP/DNS tunnels on Linux. However, there are now tools available for all platforms, and concentrating solely on Linux isn’t enough to help our blue team colleagues fully address the issue. We need to expand our focus to ICMP tunnel detection across all systems.
When studying this part, I found an article titled “How to find the process that sends abnormal ICMP traffic?”
This is an article written by Venustech CERT, published on Security Research, introducing how to find abnormal ICMP packet sending programs on Windows and Linux. It offers a method of monitoring inter-process communication, determining the time, and then using Wireshark packet capture for comparison. There might be some false positives. It is a nifty method—not necessarily brilliant but quite clever.
Today, I bring you a definite method that does not generate false positives.
0x02 Microsoft Message Analyzer
1. Introduction to MMA
Microsoft once released a network protocol analysis tool similar to Wireshark called Microsoft Message Analyzer (MMA). It was designed to help users monitor, capture, and analyze network traffic, as well as conduct in-depth diagnostics of events and messages generated by the system or applications, in the Windows operating system. It is the successor to the network packet capture tool Network Monitor on the Windows platform, with more powerful and comprehensive features. Here are the primary uses of MMA:
- Network Traffic Analysis: MMA can capture network data packets, helping users analyze the details of network communication, including data at different protocol levels, which is crucial for identifying network bottlenecks, troubleshooting, and security auditing.
- Protocol Decoding: Supports a wide range of network protocols, enabling decoding and display of detailed information from various network protocols, facilitating the understanding of the content and structure of data packets.
- Event and Log Analysis: Besides network data packets, MMA can also analyze system and application event logs, correlating network behavior with system events, providing a more comprehensive view for problem diagnosis.
- Flexible Data Views: Offers various ways to view data, including tabular and graphical views, and powerful filtering and search capabilities, helping users quickly locate key information.
- Scripting and Extensibility: Supports the use of scripts and APIs to customize analysis scenarios. Users can create or adjust analysis schemes as needed to improve work efficiency.
- Cross-Platform Support: Although mainly designed for the Windows platform, MMA also supports cross-platform network analysis to some extent, increasing its applicability in multi-environment scenarios.
- Diagnostics and Troubleshooting: In particular, MMA can provide in-depth data analysis capabilities when solving complex network and application interaction issues, helping to identify and resolve problems.
Although Microsoft Message Analyzer is very powerful functionally, it should be noted that Microsoft stopped developing and supporting this tool around 2017/18 and removed the software package from its official website on November 25, 2019.
Download, then install and use.
 />
/> />
/>
2. Simulate ICMP Tunnel
https://github.com/esrrhs/pingtunnel/releases/download/2.8/pingtunnel_windows_amd64.zip
We continue to use pingtunnel to simulate an ICMP tunnel built by an attacker, where the attacker’s controlled server side is 192.168.31.83
The attacker’s server side starts the pingtunnel server
Code Language: javascriptCopy
wget https://github.com/esrrhs/pingtunnel/releases/download/2.8/pingtunnel_linux_amd64.zipunzip pingtunnel_linux_amd64.zip# Start the server, set the key to 1234sudo ./pingtunnel -type server -key 1234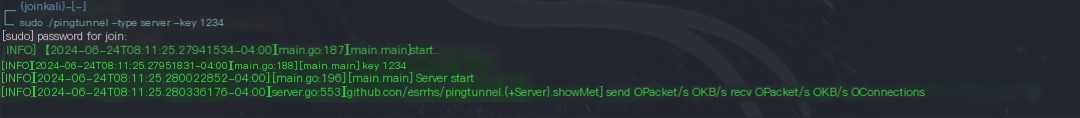
The client on Windows 11 downloads and starts pingtunnel
Code Language: javascriptCopy
# Connect to the serverpingtunnel.exe -type client -l :4445 -s 192.168.31.83 -t 192.168.31.83:4444 -tcp 1 -key 1234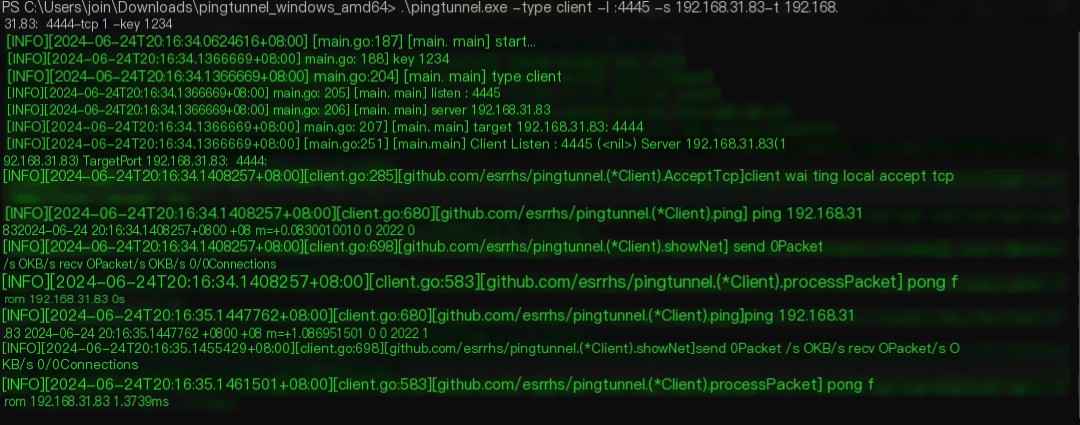
3. Use MMA to Trace ICMP Tunnel
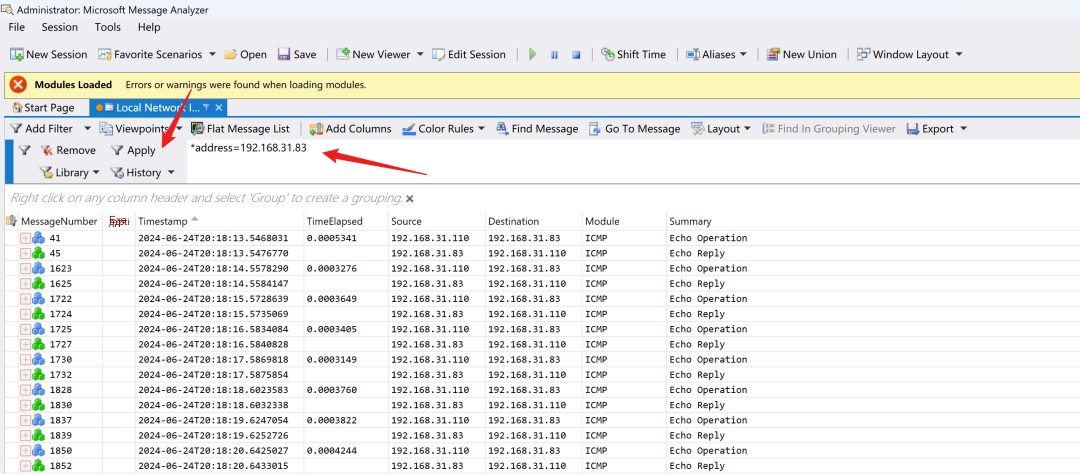
After entering filter conditions, you can directly filter out the relevant traffic, which Wireshark can also do. Now, let’s see if we can find the process ID.
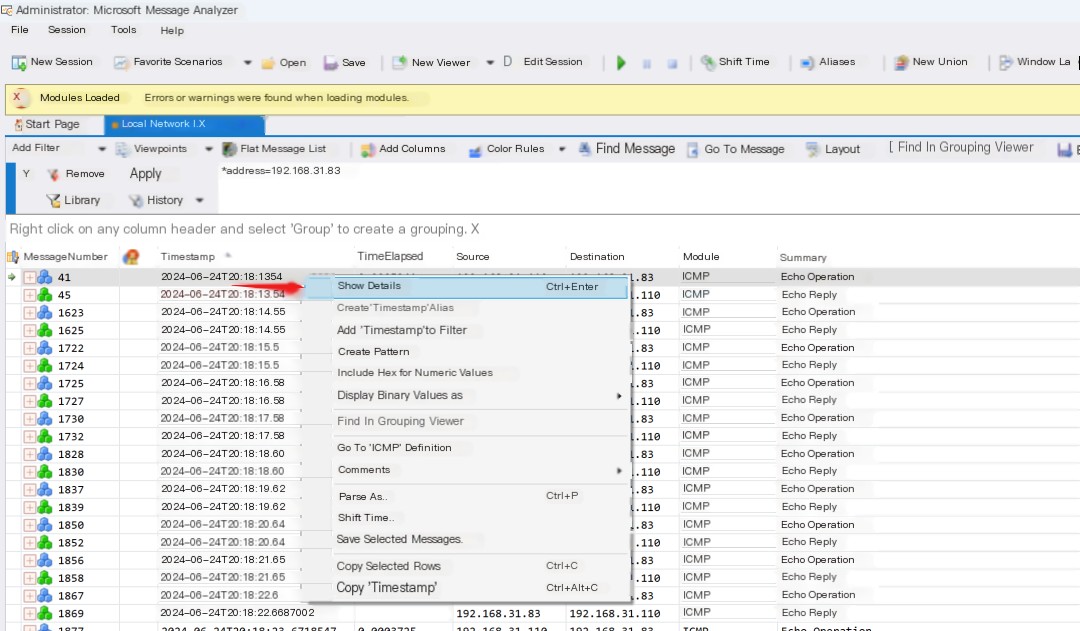
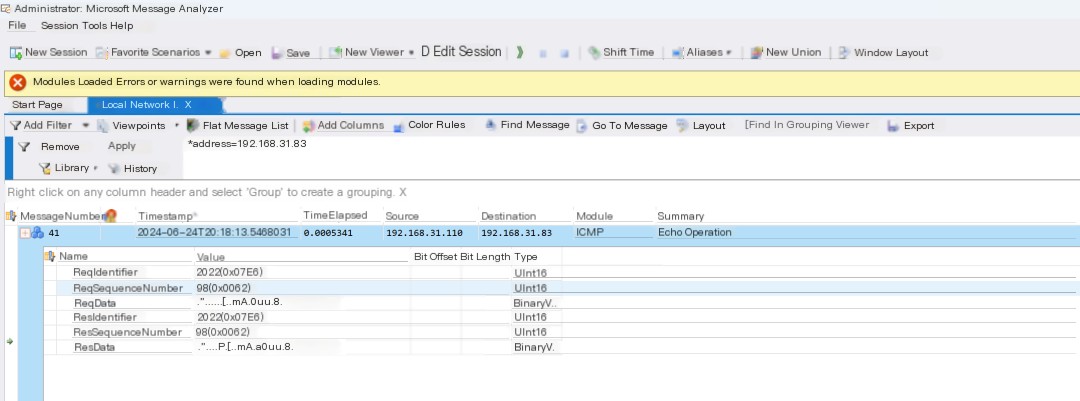
By default, nothing seems to show, just analyzing the ICMP data packets. We click on the Tools at the top to bring up other details interfaces.
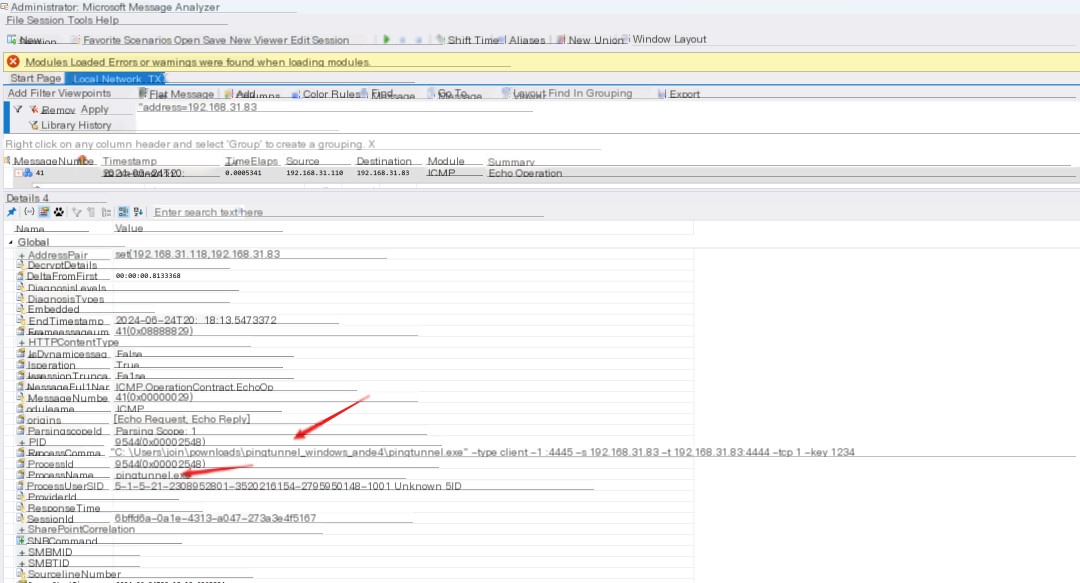
Successfully found the process ID and the corresponding startup command.
4. Successful Location of Malicious Process PID
We use system informer to verify it.
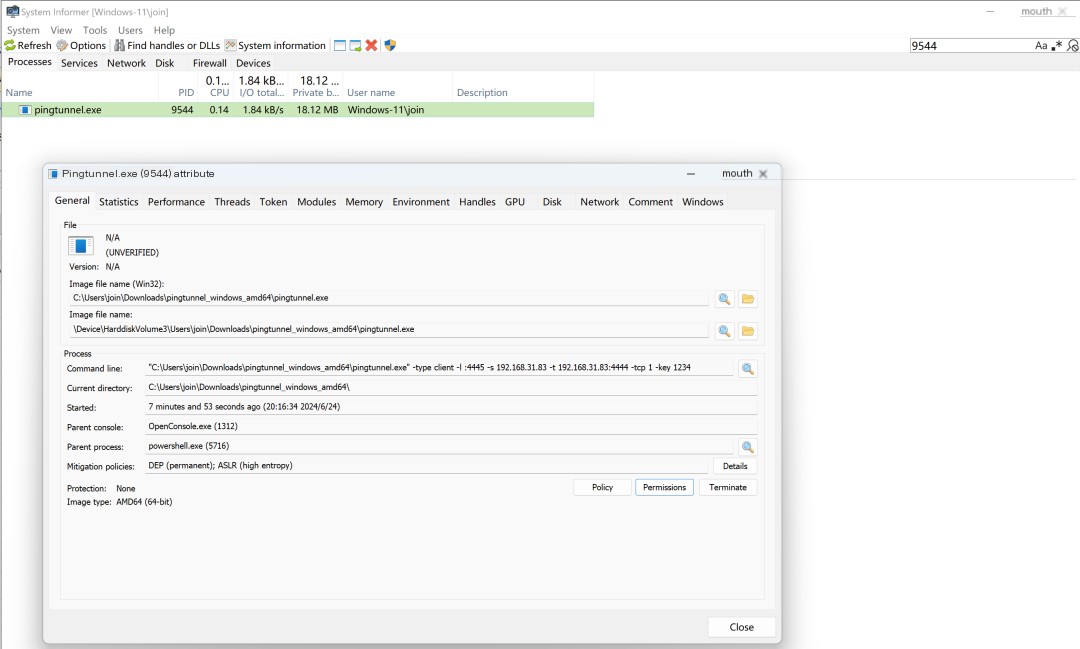
Successfully found the ICMP tunnel process’s PID.
0x03 netsh
1. Introduction to netsh
Netsh (Network Shell) is a powerful command-line tool in the Windows operating system, mainly used to configure and manage network settings. This tool allows users to view, modify, and troubleshoot various network-related configurations through the command-line interface or script files, including but not limited to the following aspects:
- Network Interface Configuration: Can be used to configure the IP address, subnet mask, default gateway, DNS server, etc., of the network interface card (NIC).
- Windows Firewall Management: Allows users to create, modify, or delete firewall rules, and to view the status and configuration of the firewall.
- IPSec Configuration: Supports configuring IPSec policies to secure network communication.
- Wireless Network Management: Can be used to manage wireless network configurations, including connecting to wireless networks and setting the preferred network list.
- Routing and Remote Access Service (RRAS): Configures and monitors routing tables, dial-up connections, VPNs, etc.
- HTTP Proxy and Listener Configuration: In supported versions of Windows, can configure HTTP proxy settings and listeners for handling network requests at the application layer.
- Network Diagnostics and Troubleshooting: Provides commands to help diagnose network connection issues, such as resetting network settings and viewing the network stack status.
Additionally, Netsh supports context switching, meaning users can enter specific network configuration contexts (such as netsh interface, netsh wlan, netsh firewall, etc.) to perform more precise operations on related areas of network configuration. It also provides scripting capabilities, enabling the writing of script files to batch execute a series of network configuration commands, which is very useful for automated network deployment and maintenance.
For more on using netsh, refer to the following official documentation.
https://learn.microsoft.com/zh-cn/windows-server/networking/technologies/netsh/netsh-contexts
Not all scenarios allow us to upload tools, and this is still a tool that has been abandoned, so the likelihood of future incompatibility is high. Therefore, the focus today is on leveraging the built-in Windows tool netsh to help us find ICMP tunnels on Windows.
2. Tunnel Simulation
Simply use the tunnel above, with the attacker’s server side as 192.168.31.83.
3. netsh Track Network Behavior
Start the network tracing function (run as administrator)
Code Language: javascriptCopy
netsh trace start persistent=yes capture=yes tracefile=.\icmp_capture.etl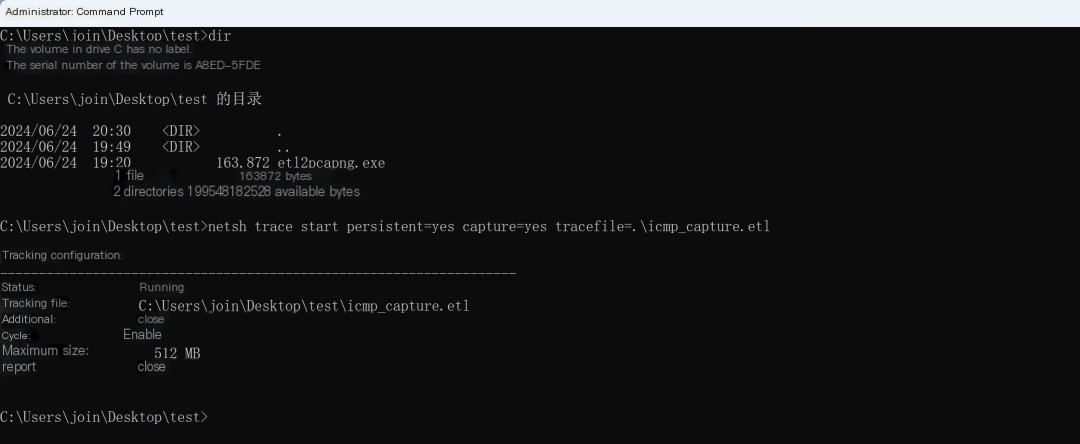
Capture is now enabled, and combined with flow devices, we believe we’ve captured the relevant data packets, we stop the capture.
Code Language: javascriptCopy
netsh trace stop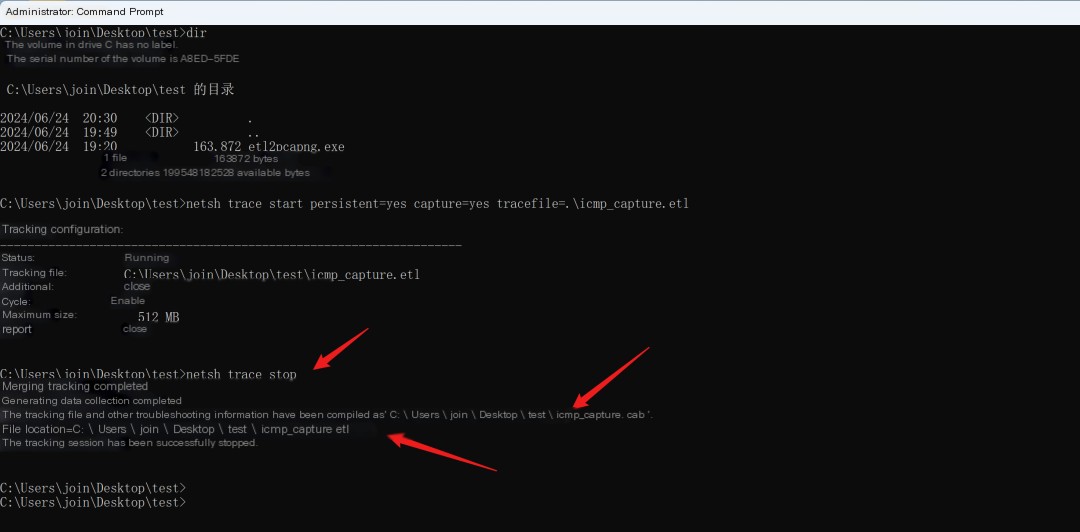
We need to convert the .etl format packet to a packet that Wireshark can parse. This requires etl2pcapng.exe
The command is very simple.
Code Language: javascriptCopy
etl2pcapng.exe in.etl out.pcapng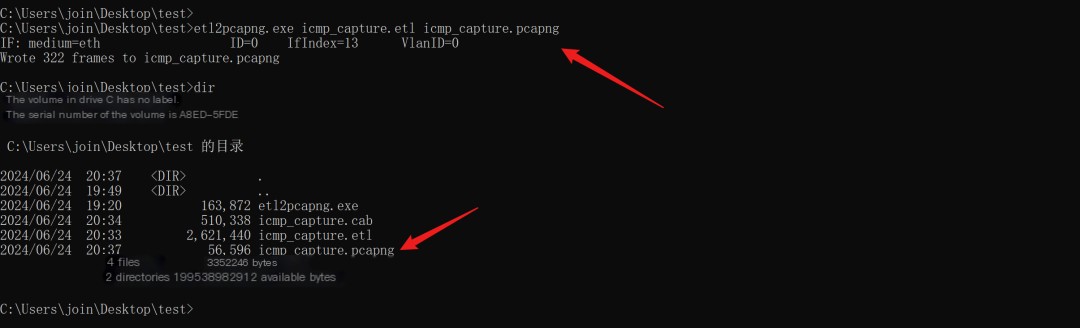
4. Identify the Malicious Process
Take the above file back locally and use Wireshark to open it.
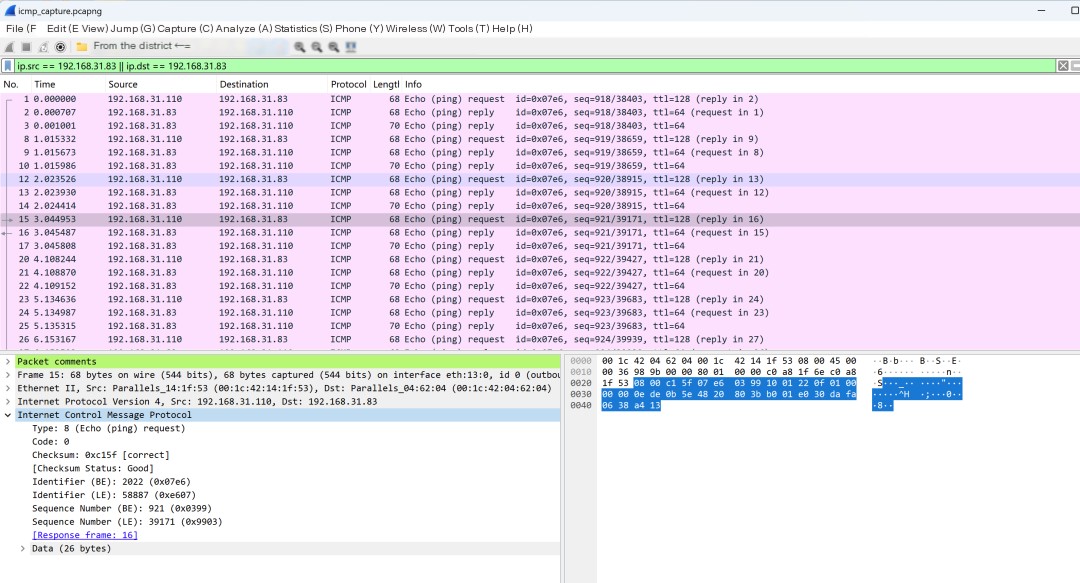
At this point, through filters, you can see these communication flows. You might think, isn’t this just packet capture? It doesn’t seem any different.
Look at the top of this packet where it says Packet comments. Click to see what the content is.
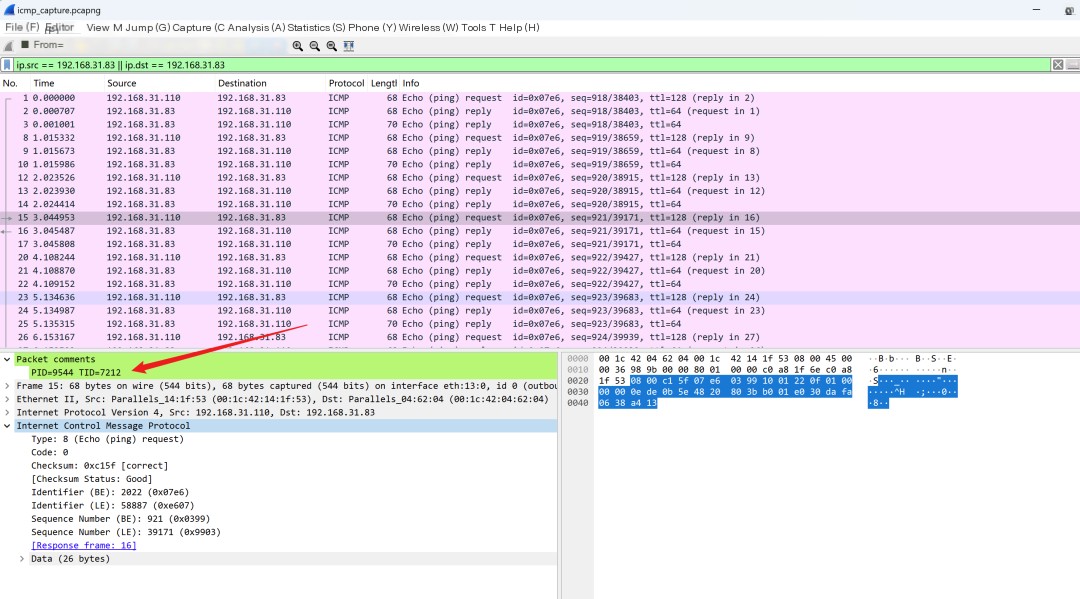
Inside, it notes the PID and TID of the request data packet sender, which helps us find the malicious process. Use system informer to verify it.
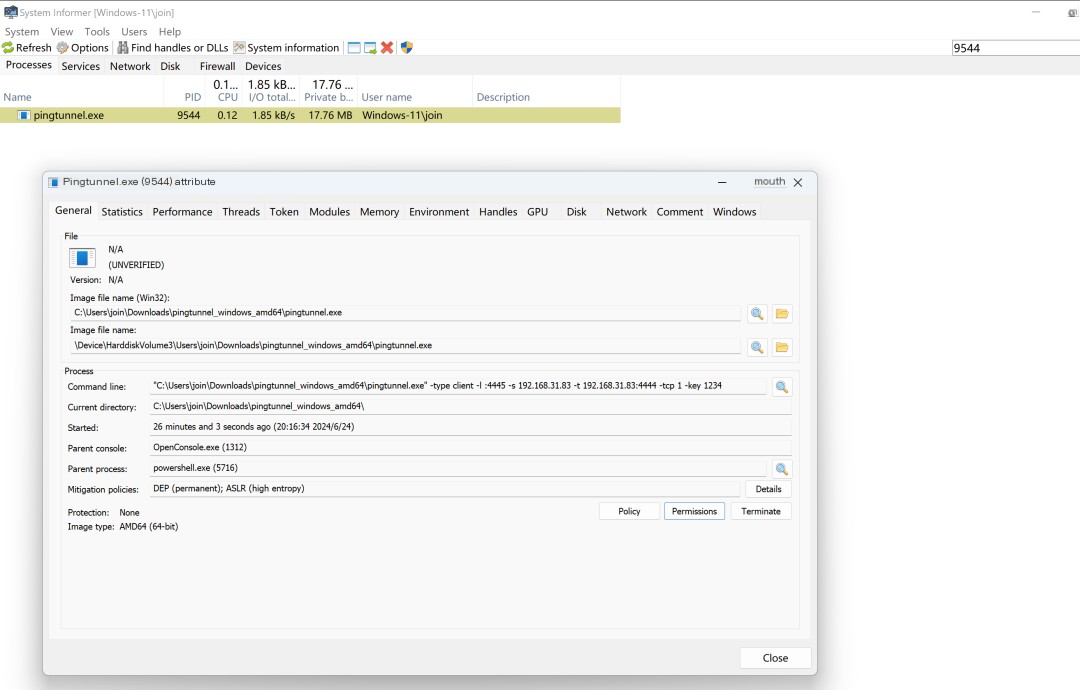
This process set up the tunnel.
As for DNS or other protocol tunnels or malicious programs, the handling method is essentially the same, with ICMP being more challenging and representative.



