1. Host Discovery
1.1. Host Discovery
The target machine GAARA[1] specifies the attack IP, so the Host Discovery process is not involved.
1.2. Host Discovery Service
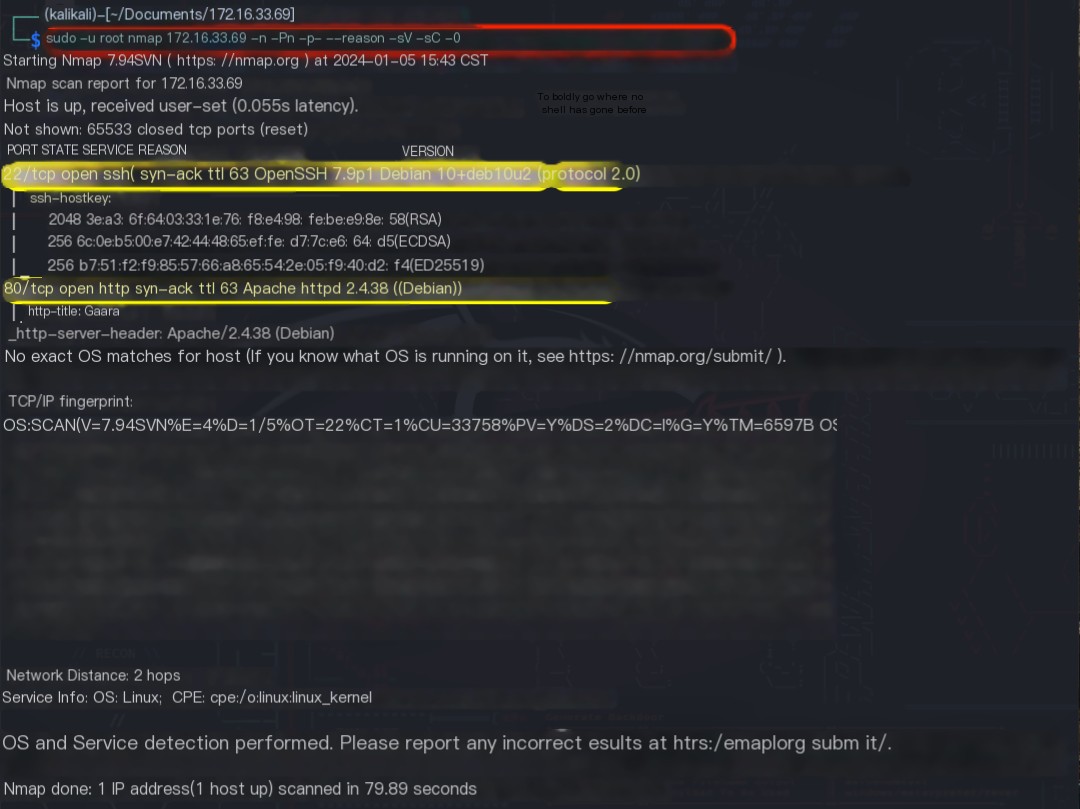
Using the command sudo -u root 172.16.33.69 -n -Pn -p- --reason -sV -sC -O, obtain the open ports of the host, the services provided, the components used, and the versions of the components.
Please provide the original heading you would like me to rewrite, including the keyword “Host Discovery.”
 />
/>
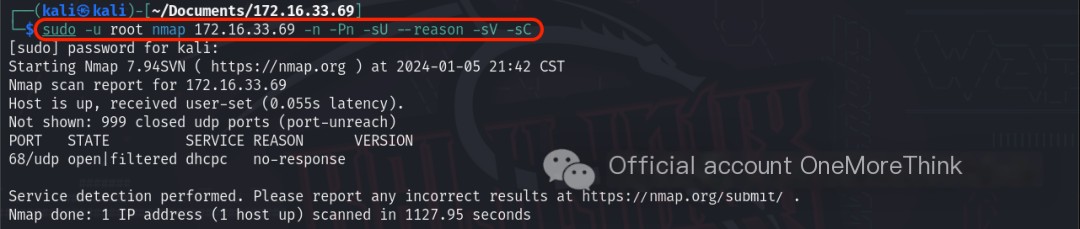
Using the command sudo -u root nmap 172.16.33.69 -n -Pn -sU --reason -sV -sC, no results were obtained.
 />
/>
The final summary is as follows:
|
Open Ports |
Services Provided |
Components Used |
Component Versions |
|---|---|---|---|
|
22/tcp |
ssh |
OpenSSH |
7.9p1 |
|
80/tcp |
http |
Apache httpd |
2.4.38 |
|
– |
os |
Debian Linux |
? |
Please provide the original heading you would like me to rewrite, including the keyword “Host Discovery.”
2. Vulnerability Discovery (Gaining Permissions)
2.1. Host Discovery: Port 80/HTTP Service
2.1.1. Component Vulnerabilities in Host Discovery
0x01. Web Middleware
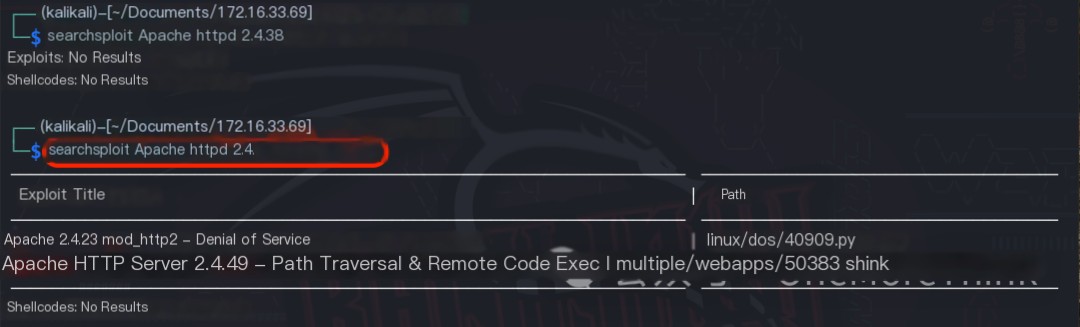
Using the command searchsploit Apache httpd 2.4., no 0-day vulnerabilities were found for Apache httpd 2.4.38 web middleware.
Please provide the original heading you would like me to rewrite, including the keyword “Host Discovery.”
0x02. Web Framework
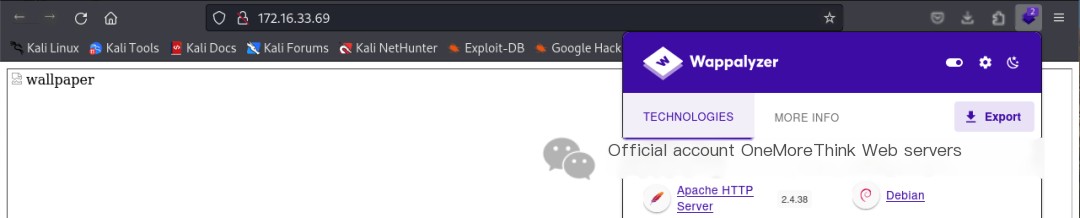
Using the browser plugin Wappalyzer, no web frameworks with 0-day vulnerabilities were found.
Please provide the original heading you would like me to rewrite, including the keyword “Host Discovery.”
2.1.2. URL Vulnerabilities
0x01. Direct Access
Directly accessing http://172.16.33.69/ with a browser only showed a single image that failed to load.
Please provide the original heading you would like me to rewrite, including the keyword “Host Discovery.”
0x02. Directory Scanning
Using the command dirsearch -u http://172.16.33.69/ to scan the website’s directories and files yielded no results.
Using the command dirb http://172.16.33.69/ to scan the website’s directories and files yielded no results.
Using the command gobuster dir -u http://172.16.33.69/ -w dictionary, using dictionaries /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-small.txt and /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt to scan the website’s directories and files yielded no results.
0x03. Fuzzing
Based on the currently known information, there is no need to fuzz the website’s directories and files.
2.2. Port 22/SSH Service
2.2.1. Component Vulnerabilities
Using the command searchsploit OpenSSH 7., no 0-day vulnerabilities were found for OpenSSH 7.9p1.
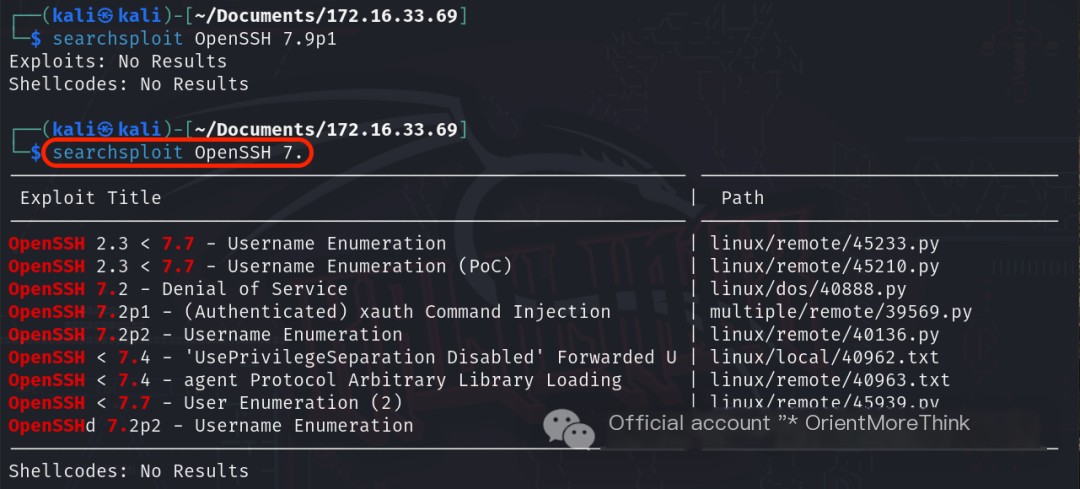
Please provide the original heading you would like me to rewrite, including the keyword “Host Discovery.”
2.2.2. Password Vulnerabilities
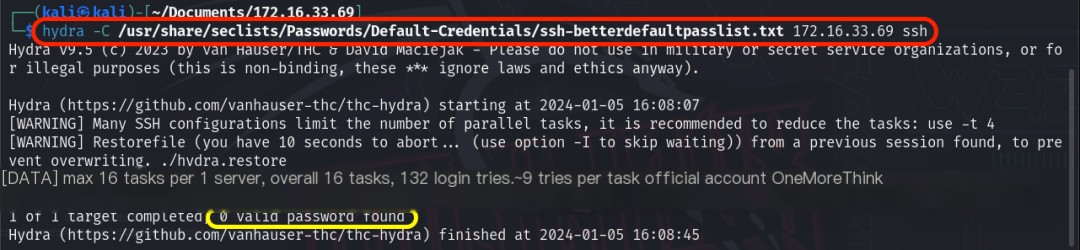
Using the command hydra -C /usr/share/seclists/Passwords/Default-Credentials/ssh-betterdefaultpasslist.txt 172.16.33.69 ssh, no weak passwords were found.
Please provide the original heading you would like me to rewrite, including the keyword “Host Discovery.”
Using the command cewl http://172.16.33.69/ obtained the keyword “gaara,” which was used as both the username and password for the SSH service for weak password brute-forcing, yielding no results.

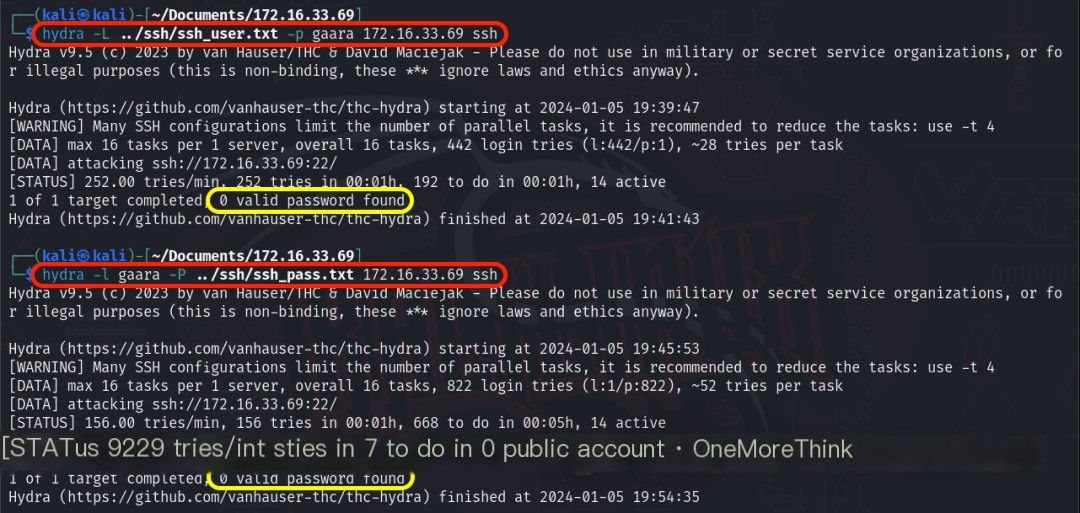
At this point, there were no more options. In the 1.2 Service Discovery phase, 65,535 TCP ports and 1,000 UDP ports were scanned, essentially covering everything; in the 2.1 Port 80/HTTP Service phase, 3 tools scanned 4 dictionaries, essentially covering everything; in the 2.2 Port 22/SSH Service phase, in addition to general dictionary scans, the website keyword “gaara” was also collected and scanned, essentially covering everything.
To break through, it would only be possible to repeat these 3 aspects and use larger and better dictionaries for brute-forcing. Consulting the WriteUp, this was indeed the case. Using the dictionary /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt for the HTTP service or the dictionary /usr/share/wordlists/rockyou.txt for the SSH service could achieve a breakthrough.
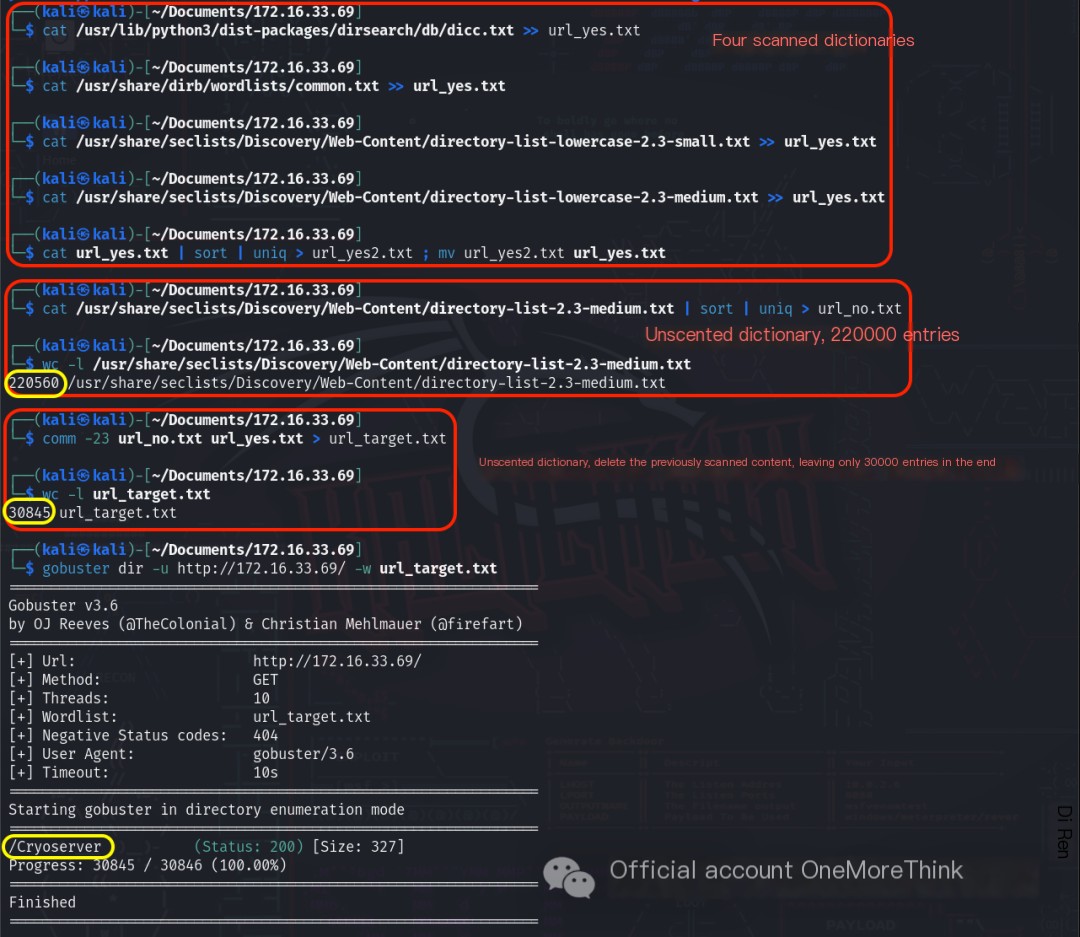
2.3. Port 80/HTTP Service
The dictionary /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt contains 220,000 entries, many of which were already scanned in the previous 4 dictionaries. Rescanning is redundant. Therefore, after removing previously scanned entries, 30,000 entries remained. Using the command gobuster dir -u http://172.16.33.69/ -w dictionary, the /Cryoserver file was discovered.
Accessing http://172.16.33.69/Cryoserver with a browser and scrolling to the bottom revealed 3 URL links. Opening them revealed almost identical content.
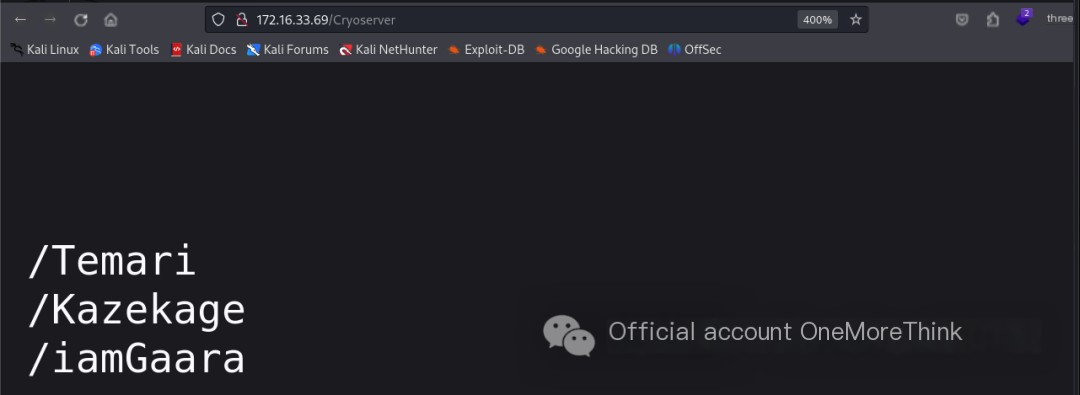
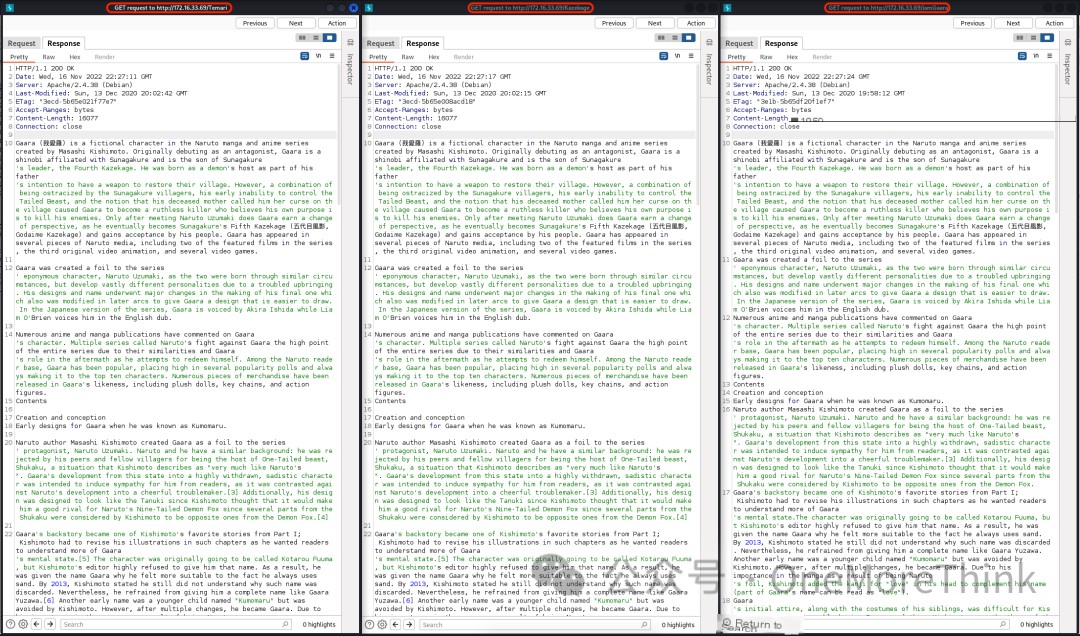
Using BurpSuite’s Comparer function, it was found that Temari and Kazekage had the same content, but iamGaara contained an additional mysterious string f1MgN9mTf9SNbzRygcU.


