【Introduction】 Previous methods relied on built-in Windows functions or other tools that called system functions for privilege escalation. However, as Windows versions are continuously upgraded, their security improves, making privilege escalation through the system itself much less feasible. With the failure of these previous methods, it is important to consider other approaches, such as Keystroke Logging.
Password Sniffing
Sniffing is a relatively stealthy method, but its success depends on luck as well.
There are many sniffing tools available. Most people are familiar with Wireshark; however, installing Wireshark on the target system is excessive, and it is challenging to filter out what we need from a massive amount of data packets.
Here, I introduce two tools:
Windows: Sniffpass
http://www.nirsoft.net/utils/password_sniffer.html
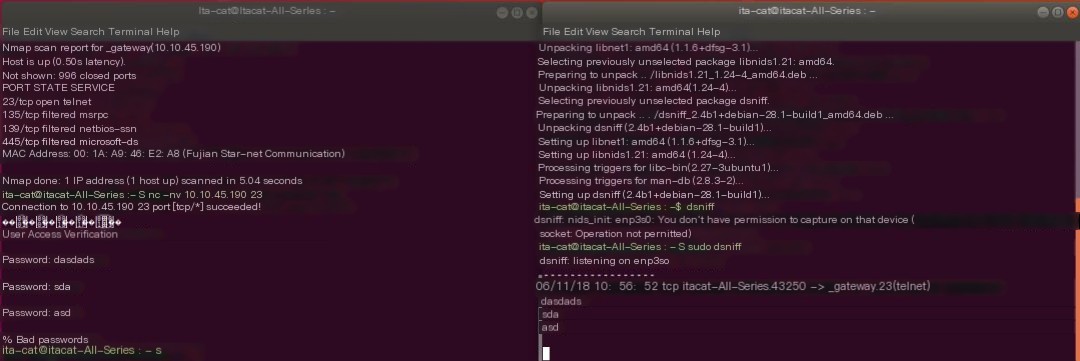
Linux: Dsniff
https://www.monkey.org/~dugsong/dsniff
Both of these tools sniff only the passwords of various protocols, such as FTP, etc.
They are exceptionally simple to use.
The Windows version is a graphical tool, not much to elaborate on.
For Linux, simply use Dsniff -i eth0 to start.
 />
/>
You can see the Telnet account and password were successfully sniffed.
Keystroke Logging
Keystroke logging is a common feature of many Trojan programs. By using hooks, one can capture all the keystrokes of a system administrator, potentially obtaining the password we need.
I won’t introduce Trojans here, but I’ll mention Klogger.exe that comes with Kali.
Located in /usr/share/windows-binaries/
Copy this program to Windows and execute it directly; it will generate a klogger.txt document in the current directory, recording our keystrokes.
Cached Passwords
Many people cache their account passwords in their browsers, so next time they visit a website, they don’t have to enter the password. While convenient, this poses significant security risks.
Of course, this also applies to Wi-Fi passwords.
Since we need passwords for so many things in real life, many people use common passwords or have some relation between them, so we might be able to obtain high-privilege credentials.
Browser Cached Passwords
Different browsers vary; here we only take the widely used IE as an example.
IE browser (Tools– Internet Options– Content– Settings)
Network Passwords
In Windows, go to Control Panel– User Accounts and Family Safety– Credential Manager.
Wireless Passwords
Windows GUI: Right-click– View connection properties–
The above methods are feasible when we have low privilege access.
There are also some readily available tools that we can use.
http://www.nirsoft.net/password_recovery_tools.html
You can download from the page above.


