Instructions
iptables source: “Linux Network Technology” by Wang Bo (First Edition). Command introduction about iptables. See supplementary information.
During use, it’s not necessary to strictly follow the code specified in the book to meet the requirements. Instead, you should use tools like Wireshark that can capture packets, then debug and observe with iptables to achieve successful communication.
rinetd Port Forwarding
For port forwarding, a much more efficient tool than iptables is rinetd. However, the source code wasn’t found, making recompilation and embedded porting impossible.
Rinetd usage instructions can be found in detail at https://www.cnblogs.com/llhl/p/9648614.html. This software can automatically handle some cross-network segment issues.
Assume the user network segment is 10.8.0.0/24, and this user needs to access the device 192.168.1.111 in the 192.168.1.0/24 segment.
A command can be directly written into the gateway device between the two segments, allowing gateway 1 (e.g., 10.8.0.2) to direct to 192.168.1.111 (no need to write into 192.168.1.105, gateway 2).
The software automatically handles access from 192.168.1.105 to 192.168.1.111. It doesn’t matter if you don’t understand it, as long as the software is convenient. Use it with Wireshark: capture, observe, troubleshoot, and debug.
Enable IP Forwarding in iptables
First, try if sysctl -p can be used.
Then modify (or create a file) /etc/sysctl.conf by removing or writing net.ipv4.ip_forward=1. Re-execute sysctl -p.
It stands to reason that if the value in /proc/sys/net/ipv4/ip_forward is 1, the IP forwarding function is enabled.
iptables Table Chains
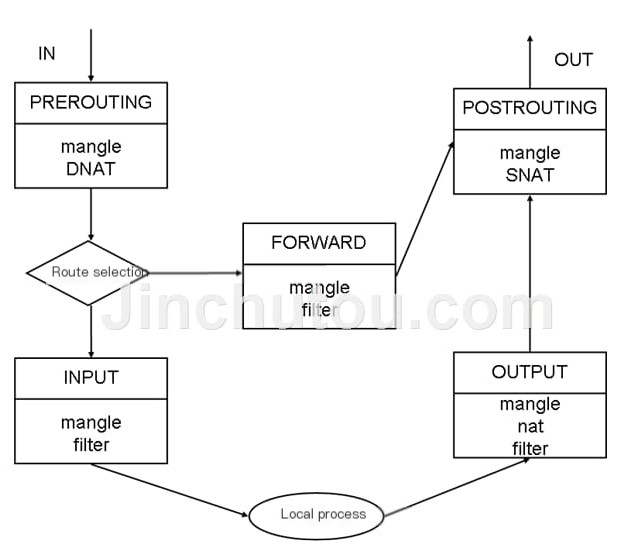
Three tables, each corresponds to several chains, and you can create chains yourself. It is important to understand which chain data enters the gateway, whether it enters the internal network of the gateway or not.
Understanding requires a lot of practical coding operation, no further explanation here. The book contains very detailed cases.
Common iptables Operations
-A to add, -I to insert, -j for action, -F to flush, -t for table selection, -p for policy, etc. See supplementary information for details.
Forwarding with iptables
When external network segment users need to access data from a specific machine within an internal network segment, it’s important to know that different network segments cannot access the data.
Code 1:
Code language: javascriptCopy
iptables -t nat -A PREROUTING -p tcp -d 10.8.0.88 --dport 1020 -j DNAT --to 192.168.15.103:1020This code is on the gateway machine, which has dual network cards. Its NIC 1 is 10.8.0.88, and NIC 2 is 192.168.15.11.
When an external machine 10.8.0.22 accesses the corresponding port 1020 of the internal network machine 192.168.15.103, the source address of the packet sent to the network interface machine is 10.8.0.22 and the destination address is 10.8.0.88.
On the network interface machine, this code translates the destination address of the packets from external machines accessing the gateway from 10.8.0.88 to 192.168.15.103 with the port (at this time, the source address of the packet is 10.8.0.22).
The different network segments cannot access each other, so even though the destination address has changed, the source address is not valid. 10.8.0.22–>192.168.15.103
Code 2:
Code language: javascriptCopy
iptables -t nat -A POSTROUTING -p tcp -s 10.8.0.0/24 -o eth1 -j SNAT --to-source 192.168.15.11This code is in POSTROUTING, and it transforms the source address of packets from the 10.8.0.0/24 network segment into 192.168.15.11. At this time, the packet is:
192.168.15.11–>192.168.15.103, which allows forward transmission. Data can now be accessed.
During the forwarding process, pay attention to capture issues, note the direction of packets in iptables’s table chains, and determine the iptables code writing.
Additional Explanation on Ping Issues
For example, if a can ping b, but b cannot ping a, it might be a firewall issue with a. (This refers to the redirect host issue)
Note it is the firewall on a. Try disabling the firewall. Additionally, check a’s firewall settings for inbound/outbound rules, and in all disabled or non-enabled items under Generic, check if icmp-related settings like printers are in the non-enabled list,
set them to allow through.



