Introduction to the SCADA System
SCADA (Supervisory Control And Data Acquisition) refers to a Data Acquisition and Supervisory Control System. A SCADA system is a computer-based DCS and power automation monitoring system; it has a wide range of applications, such as in power, metallurgy, petroleum, chemical, gas, railway industries for data acquisition, monitoring control, and process control.
In recent years, SCADA systems have transitioned from proprietary, closed networks and systems to open systems and TCP/IP networks. This has exposed these networks to the same risks faced by traditional computer networks. However, this does not necessarily mean that the security assessment methods for SCADA evaluations remain the same.
Based on our experience in conducting SCADA assessments, we have noticed that each assessment is different, requiring a unique approach based on system capabilities and industry type. In this blog post, I will share my experience in conducting SCADA assessments and discuss the best practices and tools that are most suitable for evaluating these highly sensitive systems.
“SCADA System from the Protocol Layer”
SCADA systems support various protocols such as DNP3, ModBus, IEC 60870, BACnet, LonWorks, and EPICS. In this blog post, we will continue discussing the ModBus over TCP protocol, as it still has widespread applications in control systems.
ModBus is a serial communication protocol used for communicating with programmable logic controllers (PLCs) and can be used over TCP (port 502). Each device using Modbus for communication has a unique address. Devices communicate using a master-slave model, where only one device (either a master or a slave) can initiate a transaction (called a “query”). Slaves are usually terminal devices (valves, sensors, or gauge readouts) on the SCADA network, process information, and send their output to the master.
A ModBus frame consists of the target device address (or broadcast address), a function code defining the requested action, a data field, and an error-checking field. By default, ModBus lacks authentication and encryption but can be transmitted via SSL/TLS to prevent sniffing, spoofing, and replay attacks.
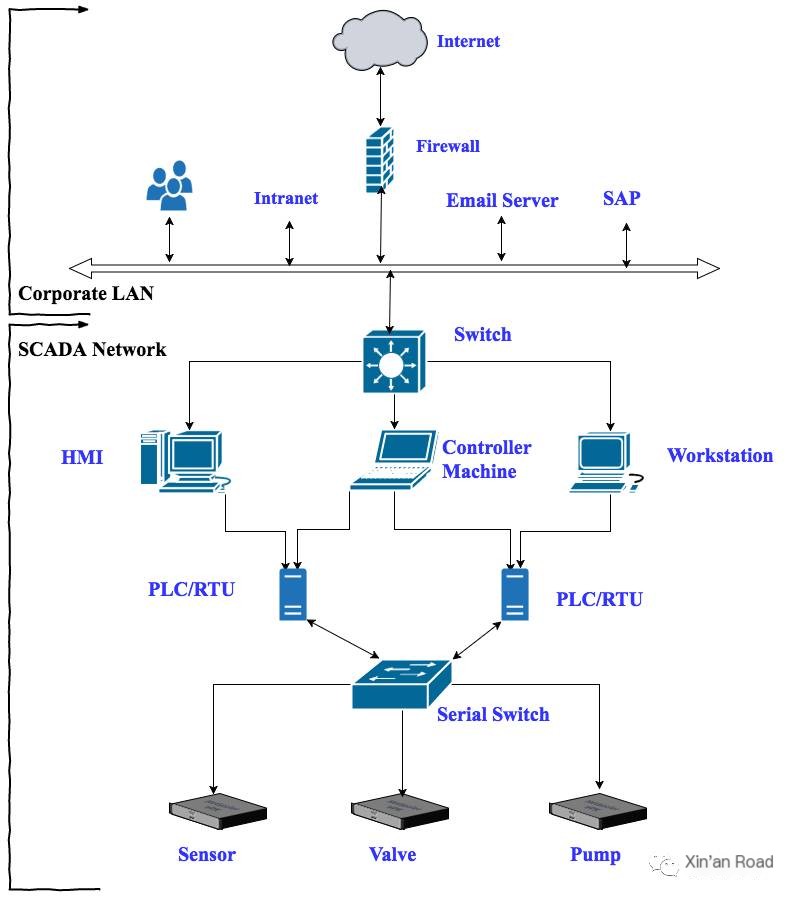
A Typical SCADA System Network
From an attacker’s viewpoint, one can see the attack surface and the degree of isolation from other parts of the network through a network architecture diagram. The next generation of SCADA networks will integrate IoT (Internet of Things) to enhance maintenance and integration convenience to reduce infrastructure costs.
 >
>
From the architecture diagram, it can be seen that the SCADA network is isolated from the enterprise network through firewalls, and correctly configured firewalls do not allow access to the SCADA network.
SCADA involves three primary key components:
1 Human-machine interfaces and control platforms: Usually, Windows workstations are used to manage and control PLCs on the network via software. If the workstation is compromised, everything in the SCADA network can be accessed.
2 PLCs (Programmable Logic Controllers): A PLC is a digital computation electronic system designed for applications in industrial environments. It uses a programmable memory to store instructions for performing logic operations, sequential control, timing, counting, and arithmetic operations to control various types of mechanical devices or production processes through digital or analog inputs and outputs. A PLC can be accessed via a network browser, Telnet, or SSH, making it susceptible to application-level and network-layer attacks. Once compromised, the attacker can manipulate input/output devices and cause damage to the organization.
3 Terminal equipment (sensors, valves, or pumps): Terminal devices are installed at remote sites. They can feedback to the PLC through communication links such as radio, serial interfaces, Ethernet, or modems. If attacked, they may compromise environmental integrity.
Note: The above components are standard configurations for any SCADA network, but you might also find other devices such as database servers, serial device interfaces, etc.
SCADA System Penetration Testing Methods
Preparation
Organizations rarely conduct SCADA testing in QA environments. So, assuming a real-time evaluation of the SCADA network is necessary, all possible scenarios must be considered. It is recommended to prepare beforehand and ensure that every department involved in the testing phases is informed.
Familiarization with the Target
This is the first prerequisite for any assessment. Penetration testers need to understand the role of SCADA: what key tasks it accomplishes, what functionality it provides, who the end-user is, and its role in the organization. Study system documentation, conduct independent research on the implemented products and vendors, uncover known product vulnerabilities, and document default credentials at this stage. Threat modeling can be conducted here.
Network Architecture Study
The main goal of studying network architecture is to logically understand how every component of the SCADA environment relates to each other (this is very complex). It’s also important to understand which components are isolated, how they are connected, or exposed to a broader network. This stage also involves identifying various subnets that exist within the network. Understanding whether the enterprise network is separate from the SCADA network is crucial. This stage helps determine my attack surface.
Network Exploration
With the information from the above stages, the network can be explored, but only with the client’s consent. The preferred method is slow scanning of known ports, listing SCADA-related network protocols and services.
Try to choose different timing options to ensure bandwidth is not consumed or to prevent DOS attacks, as SCADA systems are highly vulnerable and can easily cause DOS scenarios. At this stage, also attempt to use Wireshark to sniff traffic to see if any plaintext transmission issues exist. Communication with stakeholders is crucial at this stage.
Attack Plan
The above stages should have provided sufficient information to understand how to test and which applications to test. Document all testing methods and steps before conducting attacks, so testing sensitive and vulnerable systems is more organized.
Executing the Attack (without brute force)
Testing each vulnerability separately helps us identify the root causes of the vulnerabilities, in case of unexpected device failures. If this happens, communicate promptly with the client. Exploit every component of the SCADA network, including network infrastructure, host operating systems, PLCs, HMIs, workstations, etc.
SCADA Penetration Testing Checklist
- Have factory default settings been changed?
- Is a whitelist set for PLC access?
- Are SCADA networks isolated from other networks?
- Can the SCADA control center be accessed physically?
- Can control machines access the internet?
- Are SCADA network transmissions in plaintext?
- Does the organization adhere to strict password policies?
- Have controllers, workstations, and servers been patched with the latest updates?
- Are antivirus software running and application whitelists configured?
Tool List
- smod (https://github.com/enddo/smod): Modbus penetration testing framework
- plcscan (https://github.com/yanlinlin82/plcscan): A Python script for scanning PLCs
- NMAP Scripts (https://nmap.org/book/man-nse.html): nmap scripts for PLC scanning
- Wireshark (https://www.wireshark.org/): Network sniffer
- mbtget (https://github.com/sourceperl/mbtget): A Perl script for reading PLCs
- plcinject (https://github.com/SCADACS/PLCinject): A tool for injecting code into PLCs
- Reference Tool List (https://github.com/hslatman/awesome-industrial-control-system-security)



