NFCGate
NFCGate is an NFC security tool for Android applications, designed to aid researchers in capturing, analyzing, and modifying NFC traffic on Android platforms. It serves as a security research tool that can assist with reverse engineering protocol analysis or conducting security assessments and audits of protocols.
It is important to note that the development of this tool is intended solely for security research purposes and should not be used for malicious intent.
Function Introduction
On-device Capture: Capture NFC traffic sent and received by other applications running on the device.Relay: Use a server to relay NFC communication between two devices. One device operates in “Reader Mode” to read NFC tags, while the other uses Host Card Emulation (HCE) to simulate NFC tags.Replay: Replay previously captured NFC traffic in “Reader” or “Tag” mode.Clone: Clone initial tag information, such as ID.pcapng Export of captured NFC traffic, readable by Wireshark.
Specific Module Dependencies
NFC Support;Android 4.4+ (API Level 19+);EdXposed or Xposed for on-device capture, relay tag mode, replay tag mode, and clone mode;ARMv8-A and ARMv7: relay tag mode, replay tag mode, and clone mode;HCE: relay tag mode, replay tag mode, and clone mode;
Tool Download
Researchers can clone the project source code locally using the following command:
Code language: javascriptCopy
git clone https://github.com/nfcgate/nfcgate.gitTool Usage
Code Building
Initialize submodules:
Code language: javascriptCopy
git submodule update --initNext, build the code using Android Studio or Gradle.
Operating Modes
For each operating mode, detailed operating instructions are provided in the doc/mode/ directory within the project:
On-device CaptureRelayReplayClone
On-device Capture Mode
Switch to “Capture Mode” in the navigation bar;Press the “Begin Capture” button to start capturing and recording NFC traffic;Switch to the target third-party application;Use the NFC functionality of the third-party application;Switch back to NFCGate;Press the “Stop Capture” button to stop capturing NFC traffic;
Captured NFC traffic can be viewed in Logging, where it can be exported as a pcapng file format.
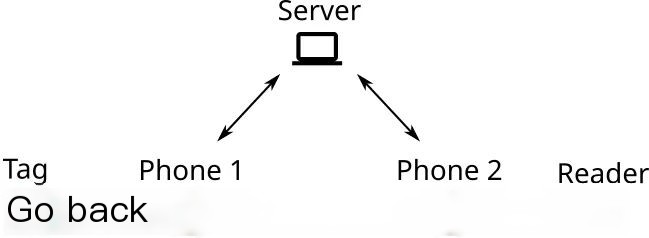
Relay Mode
Enter the “Settings” interface in the navigation bar;Specify hostname, port, and session;Ensure the server application is running and is accessible over the network;Switch to “Relay Mode” in the navigation bar;Click “Reader” or “Tag”, with one device in “Reader Mode” and the other in “Tag Mode”;Once the connection is successful, the application will display a green status indicator;
The recorded NFC traffic can be viewed in Logging and used for subsequent analysis.
Replay Mode
Switch to “Replay Mode” in the navigation bar;Select the session you want to replay;Click “Reader” or “Tag” to replay the corresponding session traffic;
New NFC traffic can be viewed in Logging and used for subsequent analysis.
Clone Mode
Switch to “Clone Mode” in the navigation bar;Scan a tag;The phone will clone the tag information;When read by another Reader, the phone will respond with the cloned tag information;
Tag information can also be saved and used for subsequent analysis.
Pcapng Export
Captured traffic can be exported in the pcapng file format or imported from it, allowing further analysis of NFC traffic captured using Wireshark. 【Reference Document】
Libraries Used
xHookXposed BridgeLibNFC-NCIProtobufAndroid About Page·Android Device NamesAndroid Support library – preference v7 bugfixAndroid RoomAndroid Lifecycle
Project Address
NFCGate: 【GitHub】



