Tcpreplay is a tool for replaying pcap packets. It allows for the editing, modification, and replay of network traffic packets captured by tools like tcpdump and Ethereal/Wireshark. It rewrites data packets on Layers 2, 3, and 4, and re-sends the traffic to the target network, thereby reproducing issue scenarios to pinpoint bugs.
Tcpreplay itself includes several auxiliary tools (tcpprep, tcprewrite, tcpreplay, and tcpbridge, etc.)
» tcpreplay: Replays pcap files onto the network at varying speeds
» tcprewrite: Edits pcap files and creates a new pcap file
» tcpreplay-edit: Edits pcap files and replays them to the network
» tcpprep: Creates client/server definition cache files used by tcpreplay/tcprewrite
» tcpbridge: Bridges two network segments using tcprewrite’s functionality
» tcpliveplay: Replays TCP pcap files in a manner recognizable by the server
» tcpcapinfo: Raw pcap file decoder and debugger
Below is a simple introduction to using tcpreplay to replay syslog UDP packets
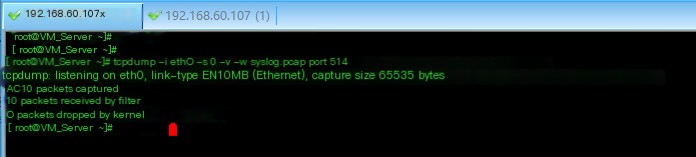
1. First, use tcpdump to capture a segment of syslog packets
tcpdump -i eth0 -s 0 -v -w syslog.pcap port 514
 >
>
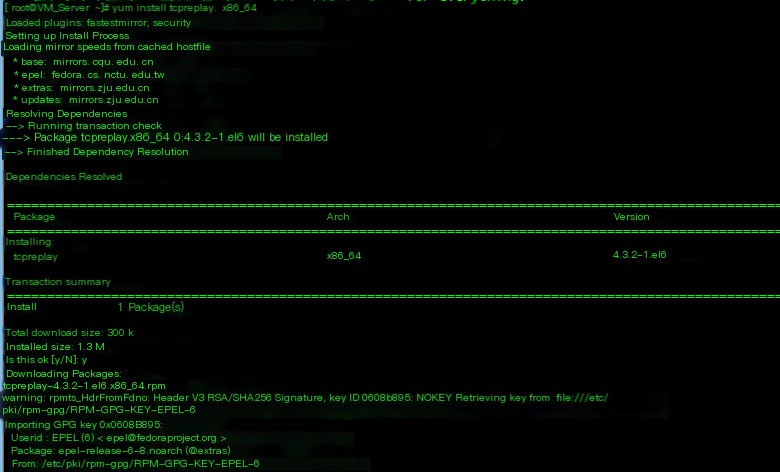
2. yum install tcpreplay to install, you need to use the EPEL source
 >
>
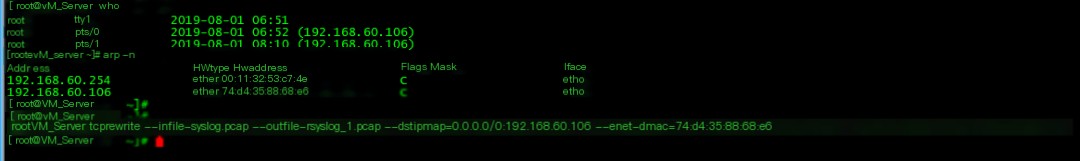
3. Use the who and arp commands to view the IP address of this machine as 192.168.60.106, and the MAC address as 74:d4:35:88:68:e6. Then use tcprewrite to rewrite the target IP address and MAC address
tcprewrite –infile=syslog.pcap –outfile=rsyslog_1.pcap –dstipmap=0.0.0.0/0:192.168.60.106 –enet-dmac=74:d4:35:88:68:e6
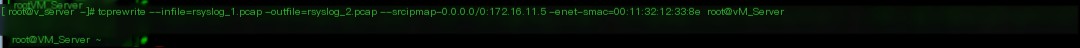
4. Of course, you can also rewrite the source IP address and source MAC address
tcprewrite –infile=rsyslog_1.pcap –outfile=rsyslog_2.pcap –srcipmap=0.0.0.0/0:172.16.11.5 –enet-smac=00:11:32:12:33:8e
5. Update the checksum of the packets
tcprewrite –infile=rsyslog_2.pcap –outfile=rsyslogfinal.pcap –fixcsum
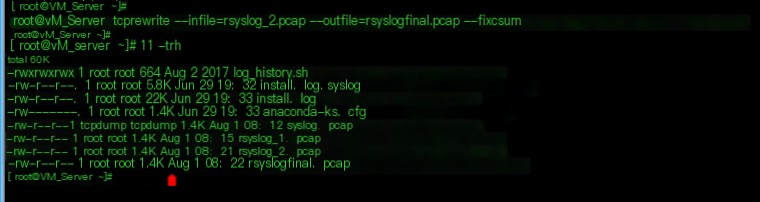
6. After completing the packet rewrite, replay the final packet
tcpreplay -v -i eth0 -M 1000 rsyslogfinal.pcap
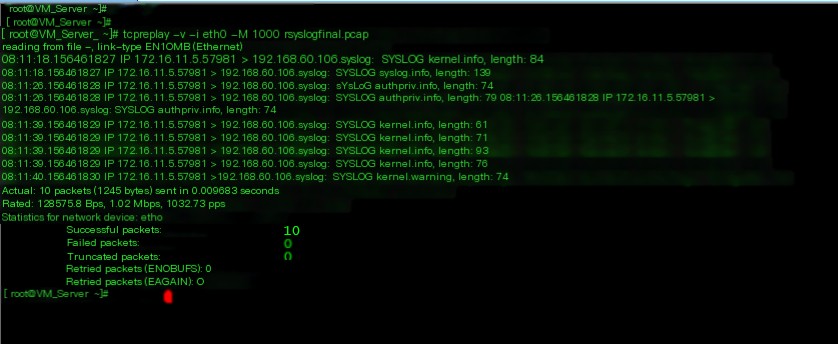
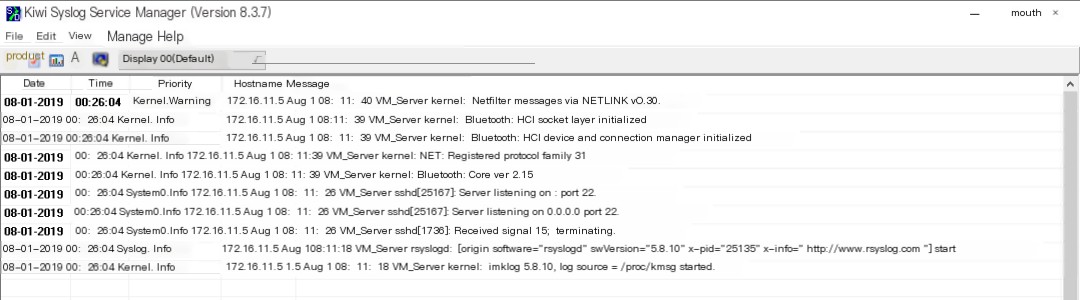
The figure above shows that you can see the syslog packets replayed to this machine 192.168.60.106 on the Kiwi Syslog Server, indicating successful replay.



