Many of us are interested in hackers, even thinking they exude an air of invincibility. Of course, some believe hackers are despicable, having done nothing good. Regardless of whether hacking as a profession is good or bad, understanding hackers helps prevent our own information security from being compromised. Today, we will reveal the commonly used Kali Linux by hackers. (If anyone is interested in learning how to install Kali, feel free to ask me for the installation guide.)
What exactly is Kali Linux?
 >
>
Kali Linux is a Debian-based Linux distribution, which differs from other Linux systems mainly because it comes pre-installed with 14 major categories of software (as shown in the image), over 300 security testing and penetration tools, including the renowned NMap (a port scanner), Wireshark (a packet analyzer), Aircrack-ng (software for penetration testing of wireless LANs), John the Ripper (a password cracker), and so on. The software pre-installed in Kali Linux basically covers all the tools a hacker would use.
What can Kali Linux do, and what is it commonly used for?
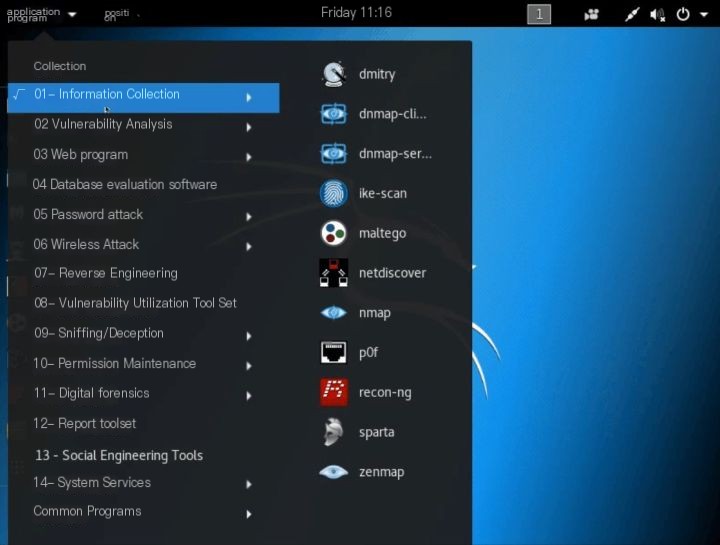 >
>
Don’t be fooled by how extensive the content above is; many of them are not commonly used. The commonly used ones include:
● Forensics (disk recovery, memory analysis, PDF auditing, registry auditing)
● Penetration testing to evaluate network system security (white hat hacker tools); generally, more people study this, with a focus on white-hat hacking nowadays.
● Attacking WPA/WPA2-protected wireless networks (obtaining WiFi passwords, network sniffing)
● Cracking passwords (offline cracking of hashed passwords, online cracking of website login passwords)
● Reverse engineering (decompiling programs written in Android, Java, C++ into code)
● Social engineering (a favorite of black hat hackers)
What drawbacks come with using Kali Linux?
1. Easily vulnerable to hacker attacks
In a regular Linux system, a normal user has an account, and there’s also a separate account for the root user. But that is not the case with Kali Linux. Kali Linux defaults to using the root account, not providing a normal user account. This is because almost all the security tools available in Kali require root privileges, and it’s designed this way to avoid asking you to input the root password every minute.
Because you’re forced to use it as the root user, all software you run on the system also runs with root privileges. If you don’t know what you’re doing, that’s bad, because if there’s a vulnerability in Firefox and you visit an infected site, a hacker could gain full root privileges on your PC and compromise it. If you were using a normal user account, the damage would be limited. Moreover, some tools you install and use might open ports and leak information without you knowing, so if you’re not extremely careful, people might infiltrate you the way you tried to infiltrate them.
2. Potential to spend the rest of your life in prison
Never use the Kali Linux system on any device or network you do not own, and do not have explicit permission to infiltrate. Claiming ignorance will not be accepted as an excuse in court.
There’s a popular saying in the industry: use Kali well, go to jail early, and eat prison food until old age. Of course, if you can control yourself, you can become a penetration engineer. We study to become penetration engineers, not to end up spending our lives in jail…
Well, that’s basically the content for today. Next time, I will introduce the common tools of Kali Linux and their functions.



