Here, we will primarily explain the SNMPv3 message format, along with the authentication and encryption processes based on USM.
1. SNMPv3 Message Format
The following is as shown in Figure 1:
 >
>
Figure 1
In this, the entire SNMPv3 message can use authentication mechanisms and encrypt the EngineID, ContextName, and PDU message body. The SNMPv3 message header is composed of RequestID, MaxSize, Flags, SecurityModel, and SecurityParameters.
The main fields in the message are defined as follows:
RequestID: The sequence number of the request message.
MaxSize: The maximum byte size the sender can accommodate, and indicates the maximum byte size the sender can receive.
Flags: The message identifier, occupying one byte.
SecurityModel: The security model value of the message, ranging from 0 to 3. 0 indicates any model, 1 indicates using SNMPv1 security model, 2 indicates using SNMPv2c security model, and 3 indicates using SNMPv3 security model.
ContextEngineID: Uniquely identifies an SNMP entity. For received messages, this field determines how the message should be processed. For sent messages, this field is provided by the application when sending a message request.
ContextName: Uniquely identifies a particular context within the range of the associated context engine.
The security parameters SecurityParameters include the following main fields:
AuthoritativeEngineID: The authoritative SNMP snmpEngineID in message exchange, used for the identification, authentication, and encryption of SNMP entities. The value is the source’s snmpEngineID in Trap, Response, Report and the destination’s snmpEngineID in Get, GetNext, GetBulk, Set.
AuthoritativeEngineBoots: The authoritative SNMP snmpEngineBoots in message exchange. It represents the number of times the SNMP engine has been initialized or reinitialized since the initial configuration.
AuthoritativeEngineTime: The authoritative SNMP snmpEngineTime in message exchange, used for time window assessment.
UserName: The username, represented by the message it is exchanging. The usernames configured on both the NMS and the Agent must be consistent.
AuthenticationParameters: Authentication parameters, the key required for authentication operations. This is empty if authentication is not used.
PrivacyParameters: Encryption parameters, used in encryption operations, such as the value used to form the initial vector IV in the DES CBC algorithm. This is empty if encryption is not used.
2. Below, we will explain the working process of the SNMPv3 protocol based on actual operations using packet captures with Wireshark:
Note: 192.168.2.110 is the IP address of the NMS, 192.168.2.1 is the IP address of the Agent.
(1) During data interaction with SNMPv3, encryption and authentication are required. Therefore, the NMS must first obtain the AuthoritativeEngineID (which identifies an SNMP entity), AuthoritativeEngineBoots, and AuthoritativeEngineTime from the Agent (to synchronize NMS and Agent time, ensuring timely message reception, and also utilized for data authentication and encryption), as shown in Figure 2:
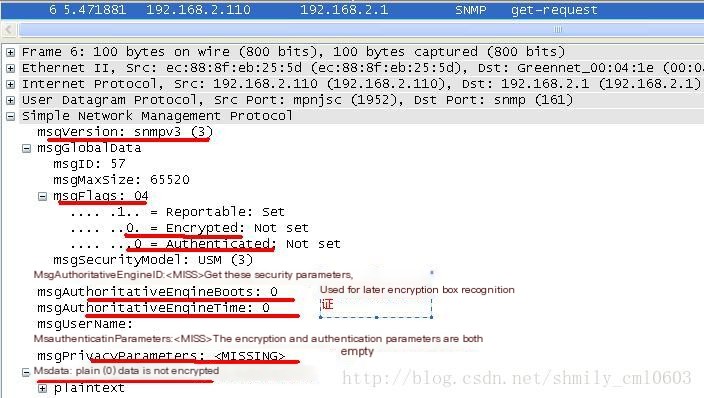 >
>
Figure 2
(2) The Agent replies with the parameters requested by the NMS, with the response message shown in Figure 3:
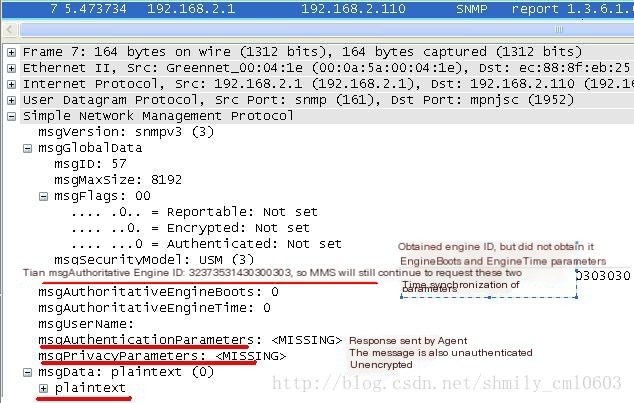
Figure 3
(3) The NMS continues to request the AuthoritativeEngineBoots and AuthoritativeEngineTime parameters from the Agent, as shown in Figure 4:
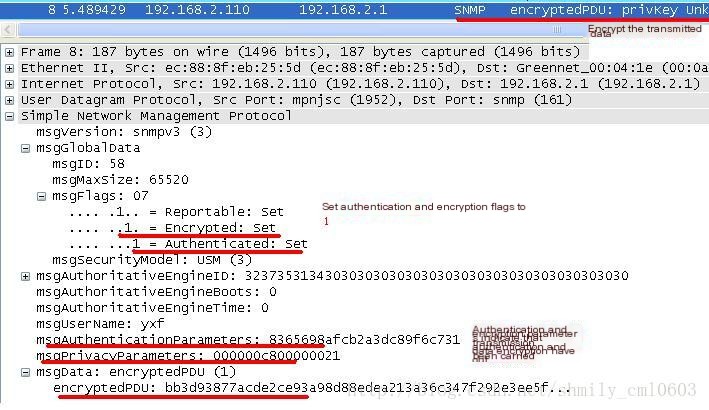
Figure 4
(4) The Agent responds to the NMS’s request, as shown in Figure 5:
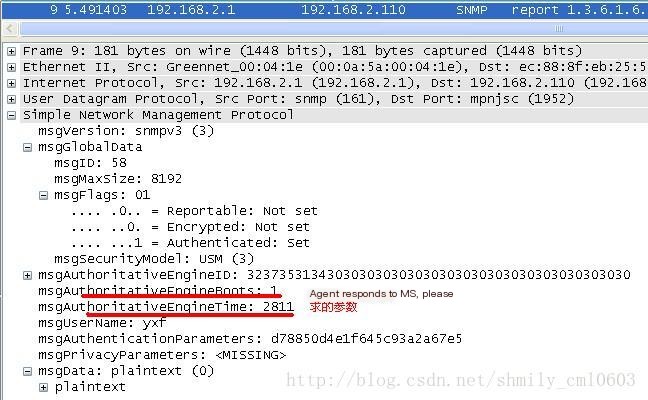
Figure 5
(5) Begin normal data operations below, as shown in Figure 6:
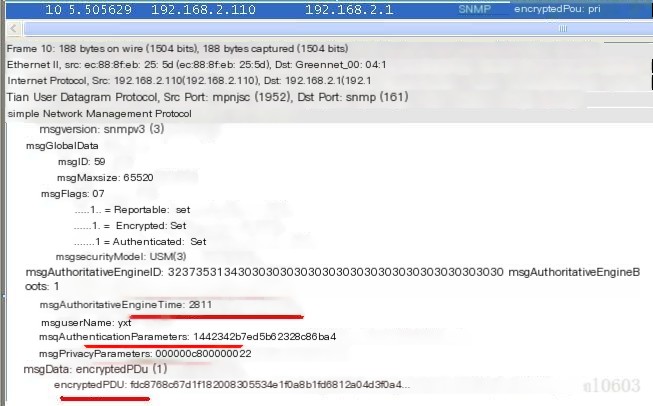
Figure 6
(6) The Agent responds to the NMS data request, as shown in Figure 7, where all transmitted data is encrypted, highlighting the security of SNMPv3:
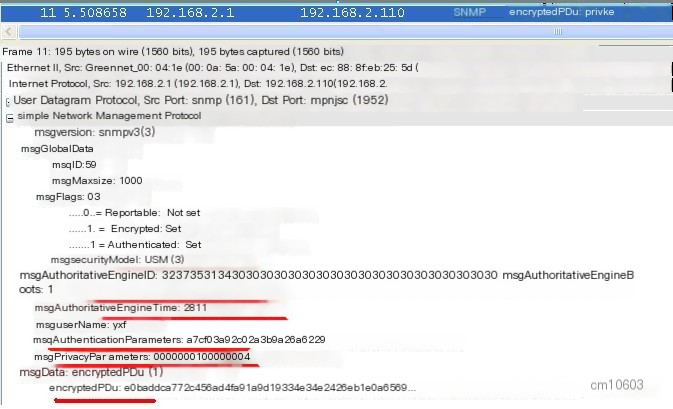
Figure 7



