Introduction to Suricata
For many years, Snort has been the de facto standard for open-source Intrusion Detection/Prevention Systems (IDS/IPS), but as more and more server network card bandwidth increases, it’s becoming increasingly difficult for Snort to perform the computationally intensive task of intrusion detection on packets in the line. In this case, you might consider deploying an open-source IDS tool: Suricata.
Suricata
Overview
Suricata is developed by the Open Information Security Foundation (OISF). It is also signature-based but integrates innovative technologies. The engine embeds an HTTP normalizer and analyzer (HTP library) to provide very advanced HTTP flow processing, which allows for parsing traffic at the seventh layer (application layer) of the OSI model.
Suricata is a multi-threaded intrusion detection system that supports IDS and IPS. Compared to traditional Snort, Suricata’s multi-threaded and modular design allows it to surpass original Snort in efficiency and performance. It assigns CPU-intensive deep packet inspection tasks parallelly to multiple concurrent tasks. This parallel detection can fully utilize the advantages of multi-core hardware to improve the throughput of the intrusion detection system, with superior effects on deep packet inspection. Simultaneously, Suricata is compatible with existing Snort rule signatures and adds support for IPv6, gradually becoming a replacement for traditional Snort intrusion detection systems.
Architecture
Suricata has three operating modes: single, workers, and autofp. The best performance recommended by officials is the workers mode.
- Single mode: Only one packet processing thread, generally used in development mode.
- Workers mode: Multiple packet processing threads, each containing complete processing logic.
- Autofp mode: Multiple packet capture threads and multiple packet processing threads. Generally suitable for nfqueue scenarios to process traffic from multiple queues.
A packet detection system typically includes four parts: packet acquisition, packet decoding, packet detection, and log recording; Suricata’s different functionalities are divided into modules, where the output of one module is the input to another module.
Setup
The setup process for Suricata is very simple; if installed from a software source, you only need to add the corresponding repository source.
Language: txt
sudo add-apt-repository ppa:oisf/suricata-stablesudo apt updatesudo apt install suricata jqTesting Usage
Language: txt
suricata-update # Update rules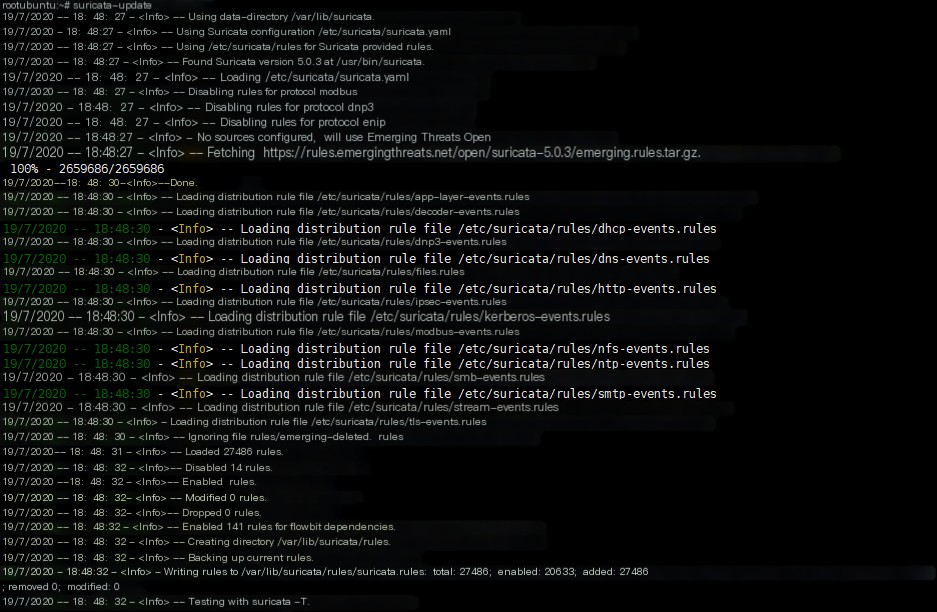 >
>Language: txt
suricata -T # Test run >
>Language: txt
suricata -i ens33 -c /etc/suricata/suricata.yaml # Start runTo maximize Suricata’s power, you can also configure it with luajit, PF_RING.
LuaJIT
LuaJIT is an interpreter for Lua code written in C. LuaJIT attempts to retain the essence of Lua: lightweight, efficient, and extensible.
Language: txt
wget https://luajit.org/download/LuaJIT-2.0.5.tar.gztar -zxf LuaJIT-2.0.5.tar.gzcd LuaJIT-2.0.5/sudo make && make installConfiguration Files
Under the /etc/suricata/ directory, there are 4 configuration files and one folder, each serving a different purpose:
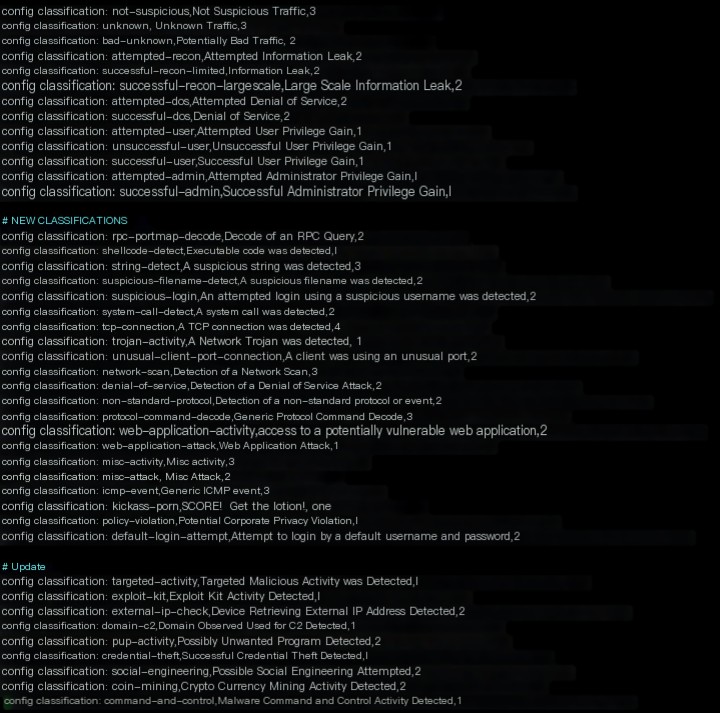
- classification.config: Defines various traffic attack types and priorities, such as denial of service attacks and web application attacks.
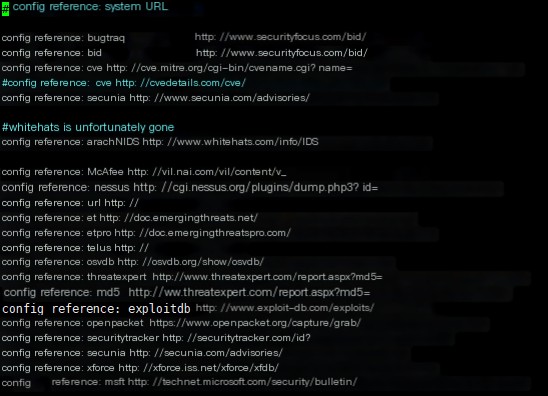
- reference.config: Records URLs of security websites and vulnerability platforms or user-defined URLs. It is used to liaise with external malicious attack detection websites about similar attacks.
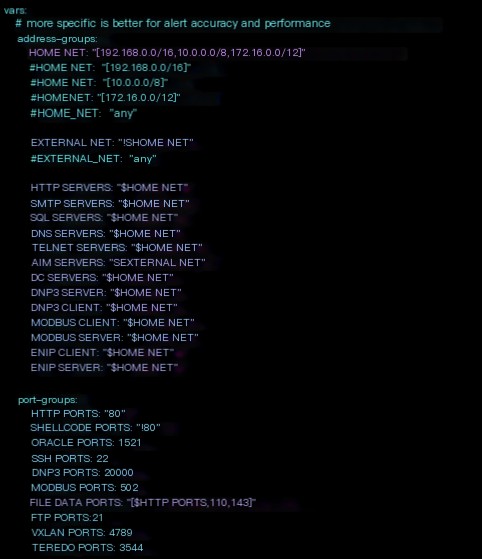
- suricata.yaml: Suricata’s default configuration file, written in the source code as hardcoded, defining almost all Suricata’s operations, including running modes, packet capture numbers and sizes, signatures and rules attributes, and log alert outputs.
- First set
HOME_NETandEXTERNAL_NET; it’s recommended thatHOME_NETcontains the internal network segment, whileEXTERNAL_NETis set toany. - If
HOME_NETis set toany, andEXTERNAL_NETis set to!$HOME_NET, it will cause an error. IfHOME_NETcontains internal addresses, andEXTERNAL_NETis set to!$HOME_NET, some internal alerts might not be matched.
- First set
- threshold.config: The threshold keyword can be used to control the rule’s alert frequency, setting a minimum threshold before alert generation.
- rules: The rules directory stores different types of rules used to determine traffic attack types and define attack and alert types. These can contain either built-in rules or user-defined rules based on the rule syntax.
Rules Explanation
Suricata is fully compatible with Snort rules.
Language: txt
alert modbus any any -> any any (msg:"SURICATA Modbus Request flood detected"; flow:to_server;app-layer-event:modbus.flooded; classtype:protocol-command-decode; sid:2250009; rev:2;)- alert: Default order is: pass, drop, reject, alert, covering four types of actions: skip, discard, reject, alert
- Modbus: Specify the protocol type, such as UDP/ICMP, etc.
- Any: Source address/destination address (IP)
- Any: Source port/destination port
- ->: Direction, unidirectional flow; <> bidirectional flow
- Any: Source address/destination address (IP)
- Any: Source port/destination port
- msg: “SURICATA Modbus Request flood detected”: The keyword msg provides relevant signature/rule-related text prompt information for alarm triggering.
- flow:to_server: Client to server
- app-layer-event:modbus.flooded: Specific attack content
- classtype:protocol-command-decode: Provides information about the rule and alert classification, defined by the classification.config file.
- sid:2250009: Used for unique rule identification, sid cannot be duplicated.
- rev:2: Rule version number, rev increments by 1 each time the rule is modified.
Complete Rule
Language: txt
alert tcp $EXTERNAL_NET $FILE_DATA_PORTS -> $HOME_NET any (msg:"INDICATOR-SHELLCODE heapspray characters detected - ASCII"; flow:to_client,established; file_data; content:"0d0d0d0d"; fast_pattern:only; metadata:service ftp-data, service http,service imap, service pop3; reference:url,sf-freedom.blogspot.com/2006/07/heap-spraying-internet-exploiter.html; classtype:attempted-user; sid:33339; rev:1;)alert tcp $EXTERNAL_NET $FILE_DATA_PORTS -> $HOME_NET anyRule action protocol source IP source port flow direction destination IP destination port Red indicates rule header- Rule action, prioritized:
passIf matched, Suricata stops scanning the packet and skips to the end of all rulesdropUsed in IPS mode, blocks the packet immediately without sending any message if matchedrejectActively rejects the packet, both sender and receiver receive a rejection packetalertRecords all matched rules and related data packets
- Protocol: Specifies the protocols to match, Suricata supports more protocols than Snort
- TCP, UDP, ICMP, IP (for both TCP and UDP), http, ftp, smb, dns
- Source IP, Destination IP:
- Supports single IP, CIDR, IP group, 96.30.87.36, 96.32.45.57, all hosts any, and IP variables configured in the rule file
$HOME_NET(protected IP range) and$EXTERNAL_NET(all other IPs):
- Supports single IP, CIDR, IP group, 96.30.87.36, 96.32.45.57, all hosts any, and IP variables configured in the rule file
- Source port/Destination port:
- Can set single port 80, port group 80,8080, port range 1024:65535, and any arbitrary port. You can add port groups in the configuration file and use
!for exclusion
- Can set single port 80, port group 80,8080, port range 1024:65535, and any arbitrary port. You can add port groups in the configuration file and use
- Flow direction:
- -> Unidirectional flow, from source IP to destination IP
- <> Bidirectional flow, flow between the two IPs
- Rule action, prioritized:
- Rule body:
(msg:"INDICATOR-SHELLCODE heapspray characters detected - ASCII"; flow:to_client,established; file_data; content:"0d0d0d0d"; fast_pattern:only; metadata:service ftp-data, service http,service imap, service pop3; reference:url,sf-freedom.blogspot.com/2006/07/heap-spraying-internet-exploiter.html; classtype:attempted-user; sid:33339; rev:1;)- MSG: Rule name, the first field in the rule
- Information displayed on the IDS alert, INDICATOR-SHELLCODE heapspray characters detected – ASCII
- Source IP, Destination IP Detection:
- sameip displays traffic with identical source and destination IP
alert ip any any -> any any (msg:"GPL SCAN same SRC/DST"; sameip; reference:bugtraq,2666; reference:cve,1999-0016; reference:url,www.cert.org/advisories/CA-1997-28.html; classtype:bad-unknown; sid:2100527; rev:9; metadata:created_at 2010_09_23, updated_at 2010_09_23;)
- sameip displays traffic with identical source and destination IP
- Flow Match:
- flow is data packets with the same data (5-tuple information) within a specific time frame belonging to one stream, saved in memory by Suricata.
- flowbits set, name Set condition
- flowbits isset, name Select condition
- If flowbits is set and the first rule is not hit, the second rule will not display even if hit, for example, certain attack response information, condition set in request and selected in response
- to_client/from_server Server to client
- to_server/from_client Client to server
- established Matches an established connection (tcp is after 3-way handshake, udp is bidirectional)
- no_established Matches connections not established
- only_stream Matches reassembled data packets by stream engine
- no_stream Does not match reassembled data packets by stream engine
- Threshold Value:
- threshold:
type <threshold|limit|both>, track <by_src|by_dst>, count , seconds - Minimum threshold, i.e., alerts only after matching at least a certain number of times.
- limit restricts alert frequency, for instance, alerting at least once every 5 minutes.
- Control threshold via 2 methods: use threshold keyword in the rule or control through /etc/suricata/threshold.config file, recommended this method as rules will be replaced upon each update.
event_filter gen_id 1 (group id), sig_id 1101111 (rule id), type limit, track by_src, count 1, seconds 60- suppress excludes alerts by specific IP
- threshold:
- Content Match: Checks for existence of content in packet, e.g., checking if traffic contains 0d0d0d0d
- Multiple matches can be written as
content:"evilliveshere"; content:"here";However, IDS won’t match in sequential order unless using content modifiers, they need to be modified to match in sequence with distance 0 to match second content after first match. - Negate matches with exclamation
!:content:!"evilliveshere"; - Encase hexadecimal string with pipe (|): content:”|FF D8|”; Mix strings and hex: content:”FF |SMB|25 05 00 00 80″;
- Case-sensitive match, escape or encode reserved characters (;) “\” “|”)
- Content modifiers, ensuring precise matches
- Case-insensitive nocase:
- content:”root”;nocase; # Modifier added directly after semicolon
- Offset Position offset:
- content:”xss”;offset 100; # Start match 100 bytes from packet’s beginning
- End Position depth:
- content:”xss”;offset 100;depth 200; # Matches until packet end unless given offset, calculates from offset, thus 100 to 200 bytes.
- Out of Range distance:
- This match must be outside the range of previous match’s endpoint, e.g., content:”msg1″;content:”msg2″;distance 25; If msg1 ends on line 100, then it looks for msg2 starting beyond 100+25
- Within Range within:
- This match must occur before previous match’s endpoint within the set range, If 100 bytes end position, within 15 meant match starts by 100-115, both distance and within indicated content:”evilliveshere”; content:”here”; distance:1;within:7; means matching here within 1-7 range after evilliveshere ends.
- Payload Size dsize:
- dsize: >64 used to detect abnormal packet size
- PCRE Regex pcre:
- content:”xss”; pcre:”xss\w” Matches pcre regex after content, minimizing system overhead
- HTTP Modifiers:
- For more details see: http://suricata.readthedocs.io/en/suricata-4.0.4/rules/http-keywords.html
alert tcp any any -> any 80(msg:"Evil Doamin www.appliednsm.com"; "content:"GET";httpmethod; content:"www.appliednsm.com";http_uri; sid:5445555; rev:1;)- http_client_body HTTP client request’s body content
- http_cookie HTTP header field “Cookie” content
- http_header Any content of HTTP requests or responses header
- http_method HTTP methods used by client (GET, POST, etc.)
- http_uri Contents of HTTP client’s URI content
- http_stat_code Contents of HTTP status field in server response
- http_stat_message Server response’s HTTP status message content
- http_encode Encoding type used during HTTP transmission
- url_len URL length
- Fast Match Mode:
- fast_pattern; If multiple matching items in Suricata rules, priority setting for matching item, set fast match mode to skip rule if not activated.
- Multiple matches can be written as
- Metadata Metadata:
- Suricata ignores statements behind metadata, used to add comments
- Group gid:
- 1:2000000 Alarm prefixed with 1 indicates group ID
- Priority priority:
- Manually set rule priority levels from 1-255, with 1 being the highest, 1-4 common, higher priority rules checked first by Suricata
- Reference reference:
- Links to external information sources for description, e.g., reference:url,sf-freedom.blogspot.com/2006/07/heap-spraying-internet-exploiter.html
- Classification classtype:
- Categorizes rules according to detected activities, classtype:attempted-user
- Signature Identifier sid:
- Used for unique rule identification, sid must be unique, 0-10000000 VRT reserved, 20000000-29999999 Emerging reserved, 30000000+: public
- Revision rev:
- Rule version number, with rev incrementing by 1 upon each rule modification
Rule Modification
Language: txtsuricata-update list-sources # List current rule sourcessuricata-update # Update rulesFor example, to disable a specific rule, simply create a
/etc/suricata/disable.conffile and enter the SID; each update will automatically disable the specified rule.After rules update, all rules will be saved in
/var/lib/suricata/rules/suricata.rulesfile, necessitating modification in Suricata configuration file’s default-rule-path and rule-files to point rule files to this rule.Suricata mainly uses et/open rules, which are built-in system rules, currently open-source and free rules are et/open, pt rules, sslbl rules, all others require an authorization code to update.
Conclusion
This article introduces the installation and configuration of Suricata under Linux, as well as the configuration files and corresponding configuration rules. Both Suricata and Snort are excellent NIDS tools, and Suricata offers better support for scenarios with high concurrency. Integrating it with distributed ELK further enhances security capabilities.
- MSG: Rule name, the first field in the rule


