Summary: Intrusion Detection Systems
This article primarily discusses Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS), both of which are critical mechanisms for safeguarding our network security. Over the past few years, the severity of security threats posed by cyberattacks has increased manifold, with several major data breaches occurring almost every month. Network-based IDS/IPS is not a new technology, but considering the latest trends in cyberattack techniques, understanding and considering the implementation of IDS and IPS remains essential for us.
Therefore, in this article, we will discuss from a high-level design perspective how to deploy IDS and IPS more effectively in different IT environments. The topics covered in this article include the following:
1. What are network-based IDS and IPS?2. What are host-based IDS and IPS?3. IDS/IPS design in enterprise environments4. Device-based IDS/IPS5. Router-based IDS/IPS6. Firewall-based IDS/IPS7. Implementing IDS/IPS in cloud environments8. IDS/IPS design for smart IoT devices9. Implementing intrusion detection using machine learning algorithms
What are network-based IDS and IPS?
An Intrusion Detection System (IDS) is software that identifies and detects malicious traffic by monitoring network traffic in real-time. In a network system, the position of the IDS is a very critical design factor. An IDS is usually deployed behind the firewall, but understanding the network data flow and overall network architecture should precede deciding the IDS deployment location. Furthermore, to enhance overall network security, it is also recommended to deploy multiple IDS. Common intrusion detection methods include:
a. Signature-based detection: Vendors can provide over 2000 signatures that an IDS can use for pattern matching against network traffic. When new data packets enter our network, they can be analyzed for similarity to the signature data in the database. If a match is detected, an alert is raised.b. Anomaly detection: Setting a baseline for user operations. For instance, if thirty people simultaneously open a connection (consider connections x5), and an abnormal request establishes 30×5=150 connections simultaneously, an alert is raised.c. Protocol anomaly detection: Detecting anomalies based on protocol information. For example, if the system uses HTTP as the protocol but some requests use other protocols or unknown commands, the system will consider it a violation of the standard protocol and will raise an alert.
When an attack occurs, an IDS can only raise an alert and cannot prevent the attack from occurring. An Intrusion Prevention System (IPS), on the other hand, can effectively prevent attack activities because all network traffic must pass through the IPS before reaching the target server. Without permission, malware cannot reach the server.
IDS design architecture in enterprise environments is shown below:
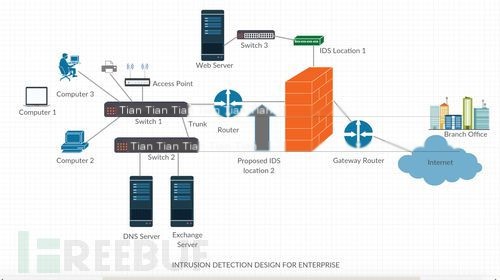 >
>
Design Considerations for Intrusion Detection Systems
a. IDS is generally deployed behind the firewall.b. In the above design diagram, the IDS at Location 1 is used to protect the web server.c. The IDS at Location 2 is used to protect the remaining network components from malware.d. This is a network-based IDS, not a host-based IDS, thus it cannot detect malware generated between two hosts within the network.
IPS design architecture in enterprise environments is shown below:
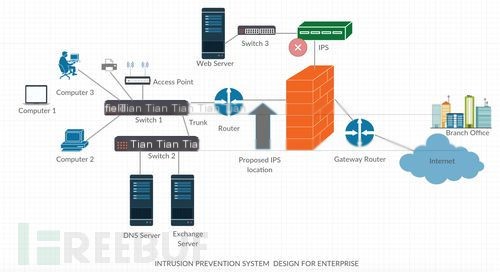 >
>
Host-based Intrusion Detection Systems (IDS/IPS)
A host-based IDS can only monitor a single system as it runs within the host you need to protect. It can read the host’s logs and look for anomalies. However, note that a host-based IDS can only detect anomalies after an attack has occurred. A network-based IPS can detect packets in the segment, and if properly designed, it may replace a host-based IPS. Another downside of a host-based IDS is that you need to deploy a host-based IDS system on every host in the network. Imagine if your environment has 5,000 hosts; your deployment costs would be very high.
Device-based IDS/IPS
You can install an IDS on a physical or virtual server, but you need to enable two interfaces to handle the incoming and outgoing network traffic. Additionally, you can install IDS software like Snort on an Ubuntu server (virtual machine).
Router-based IDS/IPS
In a network, almost all traffic passes through the router. Serving as a gateway for the network system, the router is the bridge for interaction between system internal hosts and external networks. Therefore, in network security design architecture, routers are also a place to consider deploying IDS and IPS systems. There are currently many third-party software solutions that can be integrated into routers to form the first line of defense against external threats.
Firewall-based IDS/IPS
The difference between a firewall and an IDS is that while a firewall seems to prevent external threats from entering our network, it cannot monitor attacks occurring within the network. Many vendors integrate IPS and IDS into a firewall, adding an extra layer of protection.
Implementing IDS/IPS in cloud environments
For users hosting their files and applications in the cloud, whether the cloud service provider has deployed an IDS may become one of the factors customers consider. Moreover, users can deploy Snort IDS (community version) to monitor and detect threats.
The IDS architecture in cloud environments is shown below:
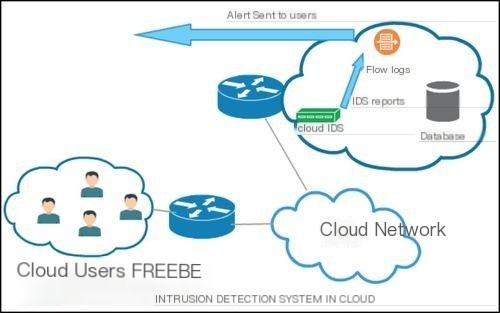
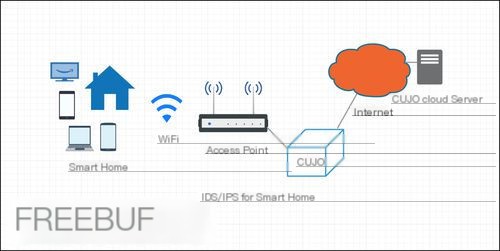
IDS/IPS design for smart IoT devices
With more users starting to use IoT or smart home devices, we also need to consider how to prevent IoT devices from being attacked by external malware. Considering the varying functionalities and sizes of devices, custom designing IDS based on device performance might be required.
The ISD/IPS deployment architecture in smart home environments is shown below:
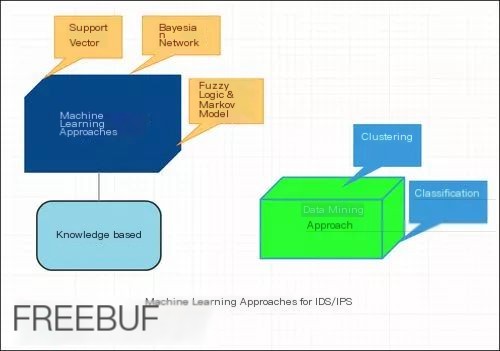
Implementing intrusion detection using machine learning algorithms
Currently, many machine learning algorithms can detect anomalies and generate alerts. Machine learning algorithms can learn the patterns of malicious behavior, and even if malicious behavior changes, they can quickly generate alerts.
Applying Machine Learning methods to IDS/IPS:
Conclusion
In the process of designing network security architecture, a critical factor we need to consider is where to deploy IDS/IPS. Depending on the network and client environment, we have various design options. With the rise of IoT and smart home devices, the importance of the IDS and IPS systems cannot be overstated. It is worth mentioning that most of the network attacks we encounter nowadays success precisely because these systems are not correctly deployed with intrusion detection systems.


