This article is part of the “WitAwards 2016 Annual Security Awards” special report. Unauthorized reproduction is prohibited. The article discusses Next Generation Firewall technology.
As a security product located at the network boundary, a firewall is more like the first gate in enterprise security. Many people may not realize that since the 1980s, when the concept of the first-generation firewall was proposed—up to today, the firewall itself has undergone several generations of changes. This is closely related to today’s stronger demand for security in enterprises.
Modern firewall companies are promoting the “Next Generation Firewall” (NGFW), also known as the next-generation firewall.
The term “next generation” is not just a modifier but exists as a major category of firewalls. Gartner defined “next-generation firewall” as early as 2009, but in recent years, the concept and standards of NGFW have undergone some changes.
Among the new-generation firewall products, the Cisco Firepower series is quite typical. In this article, we will briefly analyze the Cisco Firepower 4100 series next-generation firewall products, including product configuration, features, the market status and development trends of next-generation firewalls, and more.
1. Background on Next Generation Firewall
1.1 The Development Background of “Next Generation Firewalls”
The concept of next-generation firewalls is relative to first- and second-generation firewalls. In the OSI reference model, the latter two only work at the lower four layers or even lower hierarchical levels.
The second-generation firewall began to focus on traffic filtering at the transport layer and maintained the context of active sessions, using “state information” to speed up packet processing—all network connections include source/target IP addresses, UDP/TCP ports, and the current state of the connection (including session initialization, handshake, data transfer, and connection completion), and the firewall compares a packet with the state table.
If it’s in an existing connection, no further processing is needed, allowing the packet to pass; if it’s not an existing connection, more evaluation is needed for the new connection. All second-generation firewalls are also called stateful firewalls, or stateful inspection firewalls.
However, as modern networks and network components continue to develop, the attack surface is also expanding. Driven by profit, attackers are adopting increasingly complex methods to conduct network penetration activities, stealing more and more digital assets. Once attackers infiltrate the network, it’s difficult to detect them.
Network security systems that rely entirely on point-in-time defenses and associated technologies cannot cope with today’s highly sophisticated and evolving multi-vector attack methods. In fact, the “Cisco 2016 Annual Security Report” pointed out that attackers have begun using legitimate online resources to launch attacks, effectively increasing their revenue significantly.
The methods used by attackers include: stealing data and extorting ransom by consuming server capacity and using malicious browser extensions to steal data. Organizations must continue to seek the best possible threat protection solutions.
Meanwhile, organizations must also focus on the time to detection (TTD) because network attackers are launching increasingly undetectable attacks, so detection time is becoming an important metric. The current industry measurement is 100-200 days, far exceeding an acceptable range.
The launch of NGFW is an important step forward in the industry, and generally, NGFW has mainly changed from ordinary firewalls in terms of application access control. Some NGFWs have integrated first-generation intrusion prevention systems and various non-integrated products.
These solutions indeed somewhat improve resistance to security issues, but after the infection occurs, the help these NGFWs provide is still limited; they cannot determine the scope of infection after it occurs, contain malware, and quickly remediate.
More enterprise and organizational users are seeking more effective NGFW solutions. An ideal NGFW solution should meet the following conditions: have various world-class technologies work transparently together and provide multi-layer threat protection and integrated defense; be able to quickly mitigate risks when attacks intrude into the network.
1.2 Background on Cisco Firepower 4100 Series Products
Cisco has also followed this trend, launching NGFW products. The Cisco Firepower 4100 Next Generation Firewall, according to Cisco’s promotion, is “the industry’s first fully integrated, threat-focused next-generation firewall with unified management capabilities.”
It includes Application Visibility and Control (AVC), optional Firepower Next-Generation IPS (AMP), and URL filtering. Cisco’s promotional copy repeatedly emphasizes that before, during, and after attacks, this series of firewall products can provide advanced threat protection.
The NGIPS here—that is, the new-generation IPS—is an essential part of the Cisco Firepower series firewall products—Cisco itself has been promoting standalone NGIPS products. In the Gartner Magic Quadrant, Cisco NGIPS has always been in the leader quadrant.
Its features include establishing a network host and endpoint visibility information database for hosts, operating systems, applications, services, protocols, users, content, network visibility, further utilizing the information database to automatically recommend IPS rules, and automatically analyzing intrusion security events.
Cisco’s Firepower series NGFW inherits its in-house NGIPS functions, enabling “full-stack visibility” and “threat focus”—these are critical features now emphasized in Cisco’s promotions.
Figure 1. Magic Quadrant for Intrusion Prevention Systems
2. Introduction to the Firepower 4100 Series Firewall
2.1 Firepower 4100 Performance and Configuration
The front panel of the Firepower 4100 series NGFW devices includes 2 network module slots and 2 SSD slots, with only 1 SSD slot used by default; at the rear, there are 6 hot-swappable fans and 2 power supplies.
8 x 10 Gb Ethernet enhanced SFP+ network modules; 4 x 40 Gb Ethernet Quad SFP+ network module; up to 24 x 10 Gb Ethernet SPF+ interfaces, up to 8 x 40 Gb Ethernet (QSFP+) interfaces; 1 RJ-45 console port; 1 USB 2.0 interface; 1 Gb Ethernet copper port.
 >
>
The network modules, power supply modules, fan modules, and SSDs here are replaceable (FRU), with power and fan modules supporting hot swapping. The second SSD slot can install MSP (Malware Storage Pack) for storing threat detection results, used for subsequent analysis, and supports advanced malware protection software features.
Thus, the second SSD can both serve as storage and a malware application repository.
Based on different models (4 models currently available, with more potentially released later this year), internal configurations vary, with the top-tier 4150 model using two 22-core Xeon E5-2699v4 processors (44 physical cores, 88 logical cores), a 2.2GHz main frequency (with Turbo Boost to 3.6GHz supported); 256GB DDR4 2400MHz RAM, a single-disk 400GB SSD storage; 2 cryptographic accelerators, Cavium Nitrox V XL NHB PCIe Gen3 x16; 2 Smart NICs.
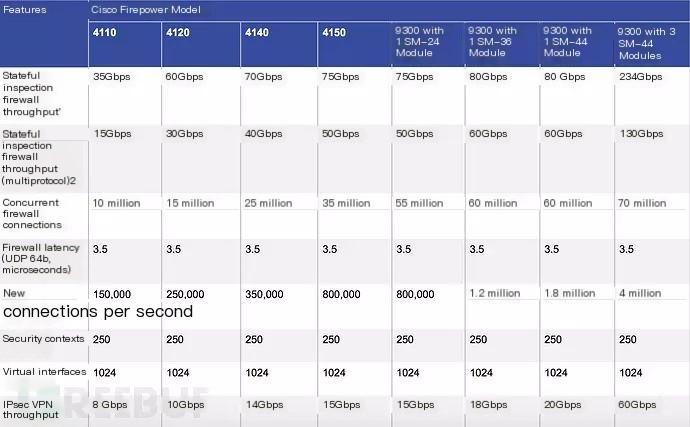
Regarding throughput, the top-tier 4150 model supports a stateful firewall of 75Gbps, a multi-protocol stateful firewall throughput of 50Gbps, and a firewall + Application Visibility and Control throughput of 30Gbps. Such performance is quite outstanding. The general situation of each model is shown below:
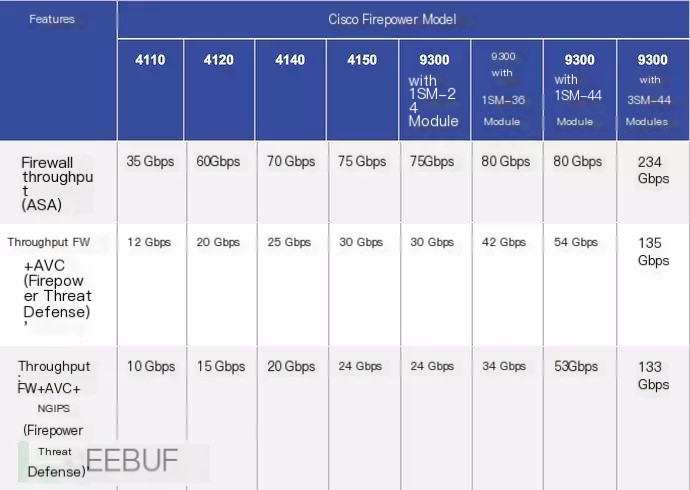 >
>
In addition, Firepower 4100 supports applications including ASA and Firepower Threat Defence. Firepower Threat Defence (FTD) includes Cisco ASA features and FirePOWER services, allowing ASA and FirePOWER functionalities on a single platform and supports functions including:
Stateful firewall functions Static and dynamic routing (supports RIP, OSPF, BGP, static routing) NGIPS URL filtering Application Visibility and Control (AVC) Advanced Malware Protection ISE integration SSL decryption Captive Portal Multi-domain management Site-to-Site VPN (some articles mention VPN is unsupported, but in fact, Cisco’s updated 6.1 version has started to provide support) Multicast routing
2.2 Differentiation Features of Firepower 4100
Nowadays, many manufacturers are making NGFW, and engaging in differentiated competition is key to attracting enterprises to purchase products. This requires Cisco to have its own trump card beyond the concept of next-generation firewalls.
Here, we can first summarize the main features of Firepower 4100, including the basic stateful firewall, VPN, application-based DDoS mitigation, NGIPS, Advanced Malware Protection (AMP), Application Visibility and Control, and URL filtering based on reputation and content classification.
All these functions are provided through a single device and managed through a unified control console—the unified management console is a significant update to the Cisco Firepower series firewall, especially for the integration management of OSI model’s four-layer and seven-layer packet inspection.
Additionally, it’s worth mentioning that Cisco has paid great attention to Chinese localization in recent years, adding a full Chinese management interface and support for numerous Chinese applications.
The aforementioned coverage of the entire attack process “before, during, and after the attack” is a significant feature of the Cisco Firepower 4100. Additionally, this product series can protect Cisco’s evolving SDN (programmable network) and Cisco’s ACI (application-centric) infrastructure architecture.
The Firepower 4100 solution for a programmable open network can combine with the aforementioned solutions to achieve automated security scheduling, which is an embodiment of Firepower 4100’s scalability within the entire Cisco product family.
Unlike traditional NGFW, the Cisco Firepower 4100 Next Generation Firewall still has some highlights worth mentioning:
Redundancy and Performance Optimization Design
Firepower 4100 adheres to the Clustering technology of Cisco firewalls, capable of seamless virtualization of multiple firewalls into one, extending performance on firewall throughput, new sessions, concurrent connections, NAT connections, and other key indicators; providing a higher redundancy mode while offering unified management.
For example, during initial procurement, Cisco can tailor purchases according to the business needs of the enterprise, purchasing two firewalls to form a cluster.
If business growth occurs post-procurement and existing firewall performance becomes insufficient, new firewalls can be dynamically added to the cluster to enhance it, reducing TCO and enhancing ROI.
Clusters can be applied to most firewall deployment scenarios, including the current hot “dual-active data center” security deployments, providing multi-active security protection across multiple data centers through clusters.
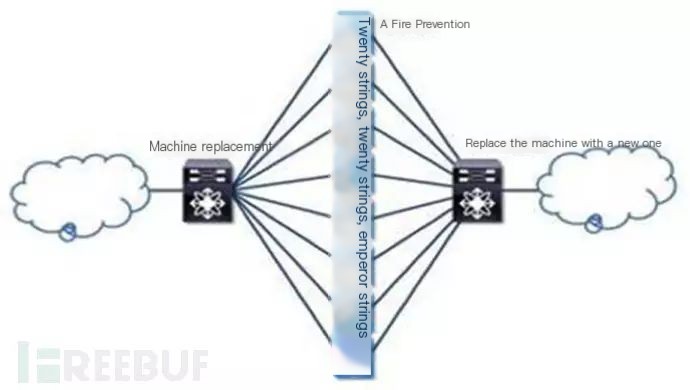
According to Cisco’s promotion, the application offloading function of Firepower 4100, through independent policy definition and hardware optimization, can provide network latency as low as 3 microseconds and extremely high throughput of 40G per stream, meeting the low latency/high throughput requirements of fast trading networks.
Full-Stack Visibility
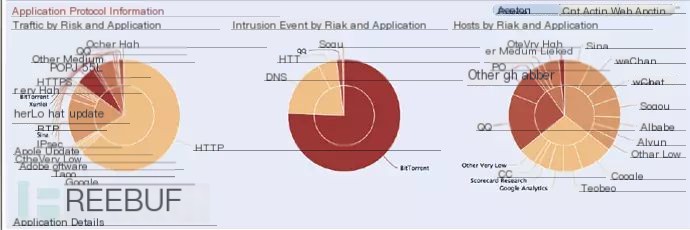
As an extension of application control, Firepower 4100 offers relatively comprehensive network visibility, including all users, mobile endpoints, client applications, operating systems, virtual machine communications, vulnerability information, threat information, and URLs—all displayed graphically.
This has positive significance in defining security policies, only allowing trusted users into the network while controlling malicious, unauthorized users. Notably, Cisco provides over 4,000 application identification features (though only a hundred are for Chinese application characteristics, but the Cisco OpenAPPID community is under development).
Unified Management Platform
Cisco launched the Firepower series next-generation firewalls this year, simultaneously introducing the Cisco Firepower Management Center, also known as the Firepower Management Center.
This is Firepower NGFW’s network hub, serving as a unified management console. It provides shared intelligence, shared contextual awareness, and consistent policy enforcement functionalities for Firepower NGFW, while integrating with other Cisco security and network solutions.
The Cisco Firepower Management Center also integrates some third-party solutions from partners, such as Radware for Distributed Denial of Service (DDoS) attacks. Many NGFW products on the market require users to switch between three or more consoles to get the detailed information they need.
From this perspective, this management center provides unified and relatively rich management functionalities on a single console, truly offering considerable convenience.
As mentioned above, the Cisco Firepower NGFW can integrate with other Cisco security solutions (such as the Cisco Identity Services Engine [ISE] for identifying data and network segmentation) and OpenDNS, offering domain visibility across the internet; it can also share intelligence, context, and policy control with other Cisco security products, meaningfully improving management efficiency and reducing management difficulty and cost; the function of automatic network segmentation also helps quickly contain threats.
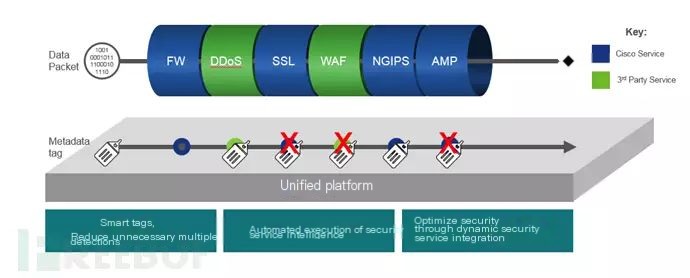
Focused on Threat Defense
In Cisco’s promotional literature, being “threat-centered” is the most emphasized part of Firepower 4100 next-generation firewall, a concept not mentioned by other brands’ next-generation firewalls.
Cisco believes that traditional NGFW products cannot offer contextual information, automation, and prioritization about current threats; companies still need to deploy special threat platforms or integrate NGFW into other systems, but doing so poses budget and deployment complexity pressures.
Specifically, the “focus on threat defense” in the Firepower 4100 series is reflected in supporting the so-called “go back in time” capability, significantly reducing the time required for threat detection involving complex attacks that might have slipped through the net—continuing analysis even post-event.
This process is essentially a desire to cover the entire attack process, especially after the attack happens, conducting intrusion event correlation analysis, abnormal traffic analysis, and malware protection attack tracking tracing, aiming for a quicker response and minimizing damage from malicious attacks.
The entire process essentially integrates the stateful firewall, NGIPS, and malware engine in NGFW, deriving an infection index to help users respond.
Here, Advanced Malware Protection (AMP) is Cisco’s specialty, protecting against malware, APT, and targeted attacks based on cloud security intelligence.
This should indeed be considered a core part of continuous analysis and alert tracing. The “go back in time” capability mentioned above, AMP not only offers single-point detection of advanced malware but also provides continuous analysis to identify, contain, and remediate initially undetected malware. As previously mentioned, this is a result of cross-domain collaboration.
Furthermore, what’s noteworthy about “threat defense” is that the notable Cisco Talos security intelligence team provides global DNS and IP threat intelligence for the Firepower series next-generation firewall.
This team, composed of numerous network security experts, analyzes the latest trends in hacker activities, intrusion attempts, malware, and vulnerabilities. This team is supported by resources from the Snort, ClamAV, Senderbase.org, and Spamcop.net communities and is considered the largest security research team in the network security industry.
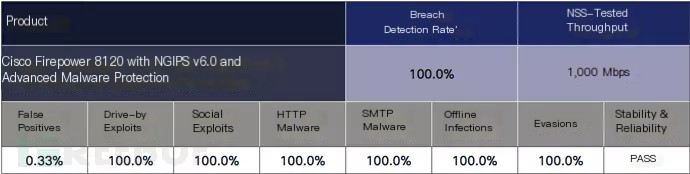
The “Breach Detection Report” issued by NSS Labs this August rated Cisco’s solution highly in the threat focus segment:
“Cisco FirePOWER 8120 with NGIPS and AMP services achieved a threat detection rate of 100.0%. FirePOWER 8120 displayed effectiveness across all evaluated technology tests. The solution also passed all stability and reliability tests.”
While this report is not directly targeted at the Firepower series next-generation firewall, AMP and NGIPS, the technologies included, are the same, making it relevant. The evaluation criteria for this report are described as such:
“The ability of the product to successfully and timely detect and report infections is crucial for maintaining the security and functionality of the monitored network. Against malware infections and spread, rapid and accurate reporting should be made, allowing administrators to control infections and minimize their impact. To control damage caused by malware, response time is critical, hence the tested system needs to detect known samples or analyze unknown samples and report them within 24 hours from initial infection and C&C callbacks.”
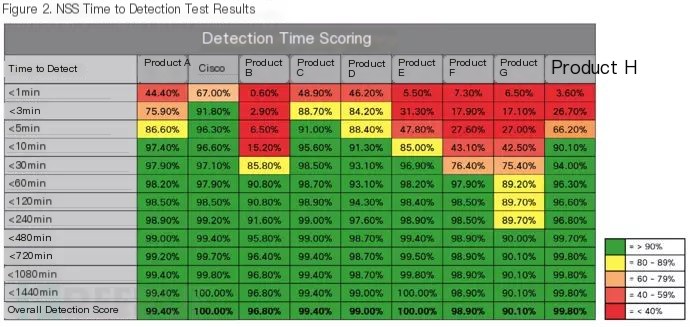
That is, Cisco’s products can detect 100% of the NSS Labs test threats within 24 hours. However, according to Cisco, the 24-hour standard is still not stringent enough. The Chief Engineer of Cisco’s Security Business Department, Jason Brvenik, proposed a concept called “Reducing Operational Space,” which essentially reduces the playing field for attackers or threats after an attack’s occurrence.
Hence, “time” becomes a better standard for detecting intrusion threats, i.e., Time to Detection (TTD). Imagine two security products that both achieve 100% threat detection, one in 5 minutes and the other in 24 hours; there is a qualitative difference between these two results.
Hence, even though the NSS Labs tests show a 100% Breach Detection rate, differences exist between products. Faster detection times are Cisco Security’s goal, and in the latest Cisco mid-year cybersecurity report, Cisco claims to have reduced the Threat Detection Time (TTD) to 8.64 hours, compared to the industry average of 100-200 days.
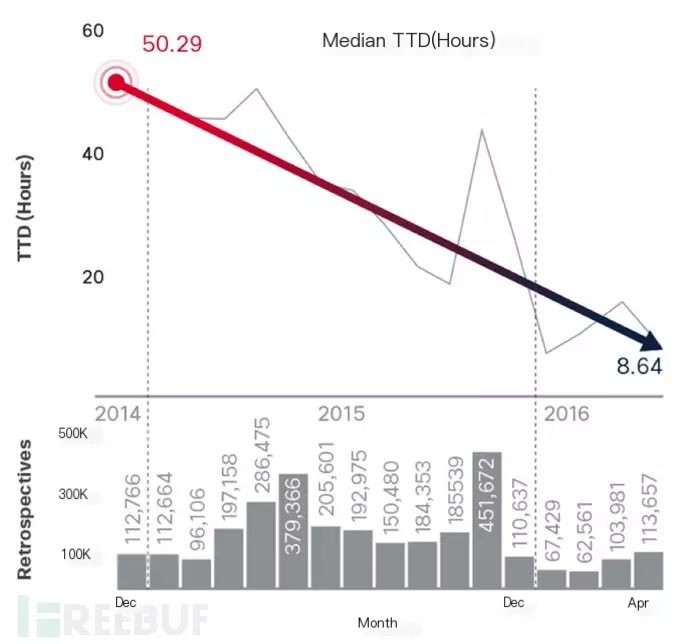
Thus, in the “focus on threat defense” section, Cisco still pursues its goals. This set of solutions is also applied to the Firepower 4100 series firewalls, becoming the core of the Firepower 4100 series firewalls.


