With the advancement of technology, industrial control systems are increasingly connecting to the Internet. However, the current Internet environment is rife with attacks that directly threaten the security of industrial control systems. The security landscape for these systems is becoming increasingly severe. Notable incidents such as the Stuxnet attack in Iran in 2010, the Duqu Trojan in 2011, Havex in 2014, and the Ukraine power grid attack in 2015 highlight the critical challenges in Industrial Control Systems Security.
To enhance industrial control network security, many researchers have adopted honeypot technology to protect systems. Honeypots, as an active defense technology, can attract attacks, analyze them, speculate on their intent, and incorporate the results into threat blocking technologies such as firewalls, IDS, and IPS.
Introduction to Honeypot Technology in Industrial Control Systems Security
The development of honeypots can be divided into three stages:
1. Initial stage: The honeypot concept was first proposed, marking the formation phase of honeypots;2. Middle stage: Large-scale development of honeypot tools, such as the introduction of tools like DTK, honeyd, honeybrid;3. Later stage: Using a network system constructed through comprehensive means such as virtual simulation, real devices, real systems, IDS, data parsing tools, and data analysis technology to lure in intrusions.
In recent years, as the security situation of industrial control has intensified, honeypot technology has increasingly been applied to the industrial control sector, starting from the simulation of protocols to the emulation of industrial control environments. Interaction capabilities are improving, and the structure is becoming more complex. In open-source industrial honeypots, there is a focus on simulating industrial control protocols like modbus, s7, IEC-104, and DNP3. Among them, conpot and snap7 are relatively mature representatives of honeypots. Conpot implements the simulation of protocols such as s7comm, modbus, bacnet, HTTP, and belongs to low-interaction honeypots. Conpot is easy to deploy, allows for easy expansion of protocol content, and device information is configured in XML format, which is convenient for modification and maintenance. Snap7 is a honeypot specifically targeting Siemens PLCs and has essentially implemented the s7comm protocol stack. It can simulate the information and status of actual devices and achieve interaction with common PLC operations. However, these mainstream virtual honeypots can only simulate a single industrial control protocol and can only capture attack data for a single industrial control protocol.
New Honeypot Technology (Introduction to Hybrid Honeypots)
To improve honeypot deployment capability and reduce honeypot deployment costs, researchers have proposed an architecture of mixing low-interaction and high-interaction honeypots, using appropriate honeypots when suitable, academically referred to as hybrid honeypots. Below are some examples:
Snort+honeybrid Solution
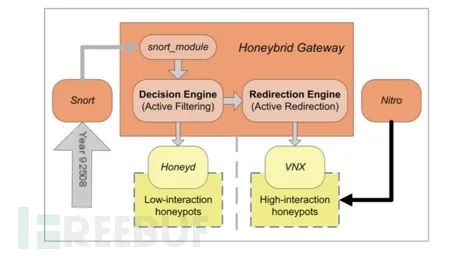
In this scheme, Snort primarily identifies low-high interaction traffic and informs the Honeybrid gateway, facilitating subsequent steps. The Honeybrid gateway includes a decision engine and a redirection engine, responsible for coordinating filtering and redirection between the front and back ends. The decision engine is used to select interesting traffic, while the redirection engine is used to transparently redirect traffic.
 >
>
Honeybrid is a typical hybrid honeypot framework, consisting primarily of the following four components, as shown in the diagram below:
Decision Engine: Decides which honeypot should handle specific businesses;Redirection Engine: Decides if certain businesses need redirection for more detailed analysis;Control Engine: Restricts outbound network traffic sent by potentially compromised honeypots;Logging Engine: Continues processing data streams for detailed records.
 >
>
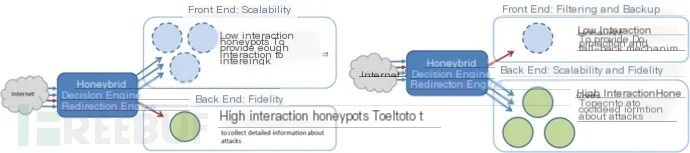
These four components are centered around the target concept, which includes norms for honeypot-based experiments. Therefore, whenever we want to run new honeypot-based experiments, we must consider the type of traffic we want to collect and how we intend to collect it, i.e., with how much granularity and control. The target consists of four declarations: a filter rule, using tcpdump syntax to define the exact type of traffic this target should handle,
a frontend rule, defining which honeypot should first interact with the incoming attack traffic and the criteria for accepting this incoming traffic;an optional backend rule, used to define which honeypot to redirect traffic to for more detailed analysis and the criteria for traffic redirection;an optional control rule, defining how to restrict outbound traffic initiated by honeypots.
Snort+SDN Solution
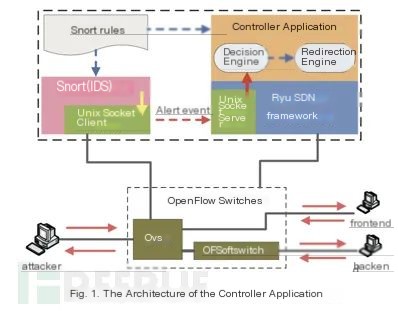
SDN is software-defined networking, which controls traffic by issuing flowtables. The right diagram shows a hybrid honeypot architecture proposed by the authors. It is mainly managed by an OpenFlow-based switch handling the control plane and responsible for redirecting connections between the attacker and different honeypots. In the control plane, the open-source IDS Snort analyzes traffic to generate alerts and sends alert messages to the controller application via UNIX sockets. Based on the alert messages, the Decision Engine (DE) will decide whether to forward or redirect the connection and signal the Redirection Engine (RE) to perform the corresponding actions.
In the above schemes, the Snort tool is used, which is an intrusion detection tool that can parse packets individually. Upon detecting a packet, it first parses the incoming data packet, then extracts features, matches the rules, and triggers alert information, as shown in the diagram below:
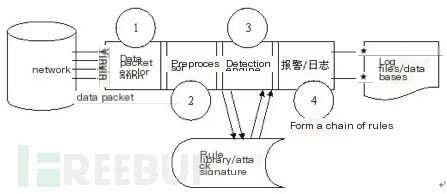
In the honeypot framework, it utilizes its data parsing and alert functionalities. Upon matching the corresponding information, it can send signals so that the subsequent processing program can proceed.
Conclusion
This article mainly introduces honeypot technology, from the origin to development of honeypots, and the emergence and development of industrial control honeypots. It describes typical honeypot architectures, which, through these architectures, can deploy honeypots more efficiently and provide a general understanding of honeypot technology. The current capability of honeypots always looks at the interactivity indicator. To enhance honeypot interactivity, researchers have adopted various methods, and this article primarily introduces ways of selecting reasonable deployment methods to improve the overall interactivity of honeypots.
However, most current honeypot frameworks are elaborated only from a technical standpoint without outlining an impeccable theoretical basis. There are still many issues that need addressing, such as rational scheduling criteria. The lack of these criteria is due to our limited understanding of attacks and the inability to obtain precise and universally applicable attack analysis methods.


