A developer proposed a business requirement that requires enabling server access to a specific database, specifically access to port 1521. A network work order was submitted, and after the network implementation, testing was conducted,
> telnet x.x.x.x 1521 Attempting connection to 10.6.1.1…
It couldn’t connect? Consulting the network confirmed that access had been granted. What could be the issue?
You might have guessed it already; it’s possibly the firewall blocking access to port 1521. How can this be verified? Since this is a test environment, the simplest method is to disable the firewall,
> service iptables stop
Then, upon testing, the connection was successful,
> telnet x.x.x.x 1521 Trying x.x.x.x… Connected to x.x.x.x (x.x.x.x). Escape character is ‘^]’.
This indicates the network is open, but the database server’s firewall is not allowing port 1521, which causes the telnet error. The solution should not involve simply turning off the firewall, but rather adding an access policy for port 1521.
Solution:
1. As root, edit the /etc/sysconfig/iptables file to include the portions highlighted in red,
> vi /etc/sysconfig/iptables # Firewall configuration written by system-config-firewall # Manual customization of this file is not recommended. *filter :INPUT ACCEPT [0:0] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [0:0] -A INPUT -m state –state ESTABLISHED,RELATED -j ACCEPT -A INPUT -p icmp -j ACCEPT -A INPUT -i lo -j ACCEPT -A INPUT -m state –state NEW -m tcp -p tcp –dport 22 -j ACCEPT -A INPUT -m state –state NEW -m tcp -p tcp –dport 1521 -j ACCEPT -A INPUT -j REJECT –reject-with icmp-host-prohibited -A FORWARD -j REJECT –reject-with icmp-host-prohibited COMMIT
2. Restart the iptables service
service iptables restart iptables: Applying firewall rules: [ OK ]
Now, port 1521 can be accessed normally.
For using iptables, the above process is generally sufficient, but delving deeper into iptables reveals its vastness. The more you look into it, the more unfamiliar it becomes, highlighting the difference between knowing how to use it and mastering it.
Regarding the command,
-A INPUT -m state –state NEW -m tcp -p tcp –dport 1521 -j ACCEPT
The meaning is to allow access to port 1521, with some parameters explained as follows:
-A: Add an entry to the rule chain;
-p: Specify the protocol type of the packet to be matched;
-j : Specify the target to jump to;
ACCEPT: Indicate accepting the packet;
Order of iptables command options (referenced from: http://man.linuxde.net/iptables):
iptables -t table_name <-A/I/D/R> chain_name [rule_number] <-i/o interface_name> -p protocol_name <-s source_IP/source_subnet> –sport source_port <-d destination_IP/destination_subnet> –dport destination_port -j action
An online article explains the basic concepts in an easy-to-understand manner. For more details, refer to http://www.zsythink.net/archives/1199,
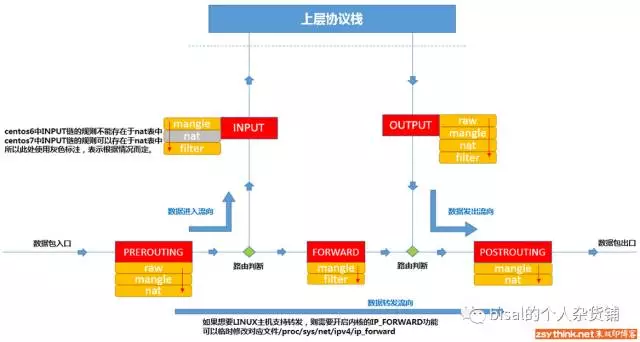
From a logical perspective, firewalls can be broadly divided into host firewalls and network firewalls. Host Firewall: Provides protection for individual hosts. Network Firewall: Typically located at the network’s entrance or edge, providing protection for the network entrance, serving the local area network behind the firewall. Host and network firewalls are not in conflict; think of network firewalls as external (collective), and host firewalls as internal (personal). Physically, firewalls can be categorized into hardware firewalls and software firewalls. Hardware Firewall: Implements part of the firewall functionality at the hardware level, with other functions based on software implementation, with high performance and cost. Software Firewall: A firewall where the application logic runs on a general hardware platform, with lower performance and cost. iptables is not really a firewall; it can be understood as a client proxy. Users use this proxy, iptables, to execute their security settings on the corresponding “security framework,” which is the actual firewall, and this framework is named netfilter. netfilter is the actual security framework (framework) for the firewall, residing in the kernel space. While iptables is a command-line tool located in the user space, it is used to operate the actual framework. Netfilter/iptables (hereinafter referred to as iptables) forms the packet filtering firewall on the Linux platform. Like most Linux software, this packet filtering firewall is free and can replace expensive commercial firewall solutions to perform packet filtering, packet redirection, and network address translation (NAT) functions. Netfilter is a data packet processing module inside the core layer of the Linux operating system, offering the following functions: Network Address Translation (NAT) Packet content modification And packet filtering firewall capability Hence, although we employ ‘service iptables start’ to initiate the iptables “service,” accurate understanding reveals that iptables does not have a daemon process, so it isn’t a genuine service but should be considered a function provided by the kernel.
In conclusion, in a Linux system, the firewall (Firewall), URL translation (NAT), packet (package) recording, and traffic statistics are functions provided by the Netfilter subsystem, and iptables is a tool to control Netfilter. iptables organizes complex rules in a manageable way, enabling administrators to perform group testing or switch groups of rules on and off. iptables reads only the packet header, doesn’t increase the data stream burden, and requires no verification. (quoted from: https://www.centos.bz/2017/11/linux-iptables防火墙原理与常用配置/)
This graphic is a flowchart of data packets passing through a firewall (quoted from: http://www.zsythink.net/archives/1199)
iptables involves knowledge of Linux configuration, networking, among other areas. A simple command is quite extensive; if you wish to enable database and port access strategies, knowing the above command is sufficient. If you find this intriguing, deeper exploration can lead to acquiring some very pure knowledge.


