Background of CVE-2014-0160 Vulnerability
The CVE-2014-0160 vulnerability, commonly known as the OpenSSL vulnerability, refers to a critical security flaw discovered in the OpenSSL cryptographic software library. This vulnerability allowed attackers to read sensitive memory content from the affected systems, compromising private data and security keys. It became widely known as “Heartbleed,” highlighting its severe impact on internet security when it was publicly disclosed in April 2014.
On April 7, 2014, OpenSSL released a security advisory regarding a critical vulnerability (CVE-2014-0160) present in the OpenSSL version 1.0.1. This issue is located in the file ssl/dl_both.c. The Heartbleed module of OpenSSL contains a bug that allows attackers to send specially-crafted packets. If these packets do not have sufficient data, the memcpy function will output subsequent data from the SSLv3 record, enabling attackers to remotely read up to 64KB of memory from a vulnerable OpenSSL server.
Affected and Unaffected Versions of OpenSSL
- OpenSSL 1.0.1f (Affected)
- OpenSSL 1.0.1g (Not affected)
- OpenSSL 1.0.0 branch (Not affected)
- OpenSSL 0.9.8 branch (Not affected)
We recommend the following:
- Upgrade OpenSSL to the latest version 1.0.1g
- Regenerate your private keys
- Request and replace SSL certificates
- Recompile older versions of OpenSSL with the -DOPENSSL_NO_HEARTBEATS flag to disable the Heartbleed module
The latest version can be downloaded from: https://www.openssl.org/source/. (Official OpenSSL site)
Analysis and Verification
Exploitation and verification scripts for this vulnerability are widely available, including the following addresses:
http://fi****o.io/Heartbleed/ (web testing page)
http://s3. ****guin.org/ssltest.py (python script)
http:// **.* u u.com/s/1nt3BnVB (python script)From a security team perspective, it’s not suitable to distribute these addresses in plaintext, but we must inform users that almost all attackers have access to these resources, and in the past 24 hours, this vulnerability has been widely probed and attempted. Many vulnerable sites have likely been attacked multiple times.
Given the severity of this vulnerability and the speed of attack proliferation, we had to break from standard environmental setup and testing management. We immediately chose relatively “lightweight” sites for direct validation to analyze the actual consequences and sensitive information. Using existing network testing methods, we identified several problematic websites for analysis. To avoid inappropriate conduct, we did not select sites related to finance or transactions. Problematic website addresses:
Ap***.*****.gov.cn (testing time: 2014-04-09 01:00)
my-****.in (testing time: 2014-04-09 01:10)
www.shu****.cn (testing time: 2014-04-09 01:15)
git****.com (testing time: 2014-04-09 01:20)
feng*****.com (testing time: 2014-04-09 01:30)Screenshots of returned sensitive information are as follows:

Image 1 Test Website 1
After sending data through the vulnerability exploitation tool, the returned data shows internal IP addresses, paths, and more.
Retrieved sensitive information includes internal IP addresses, paths, and more.
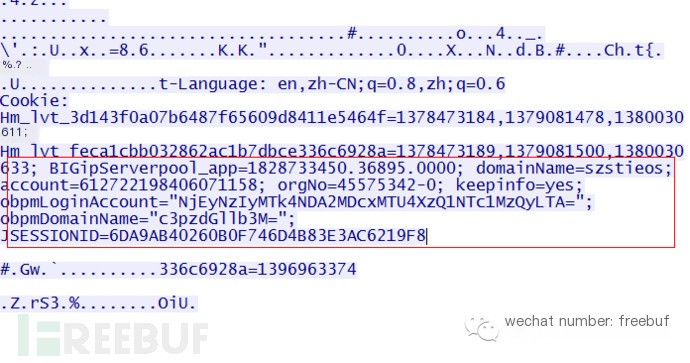
Image 2 Test Website 2
After sending data through the vulnerability exploitation tool, the returned data shows APP information, cookie information, and username details.
Retrieved sensitive information includes APP information, cookie information, username details, and more.
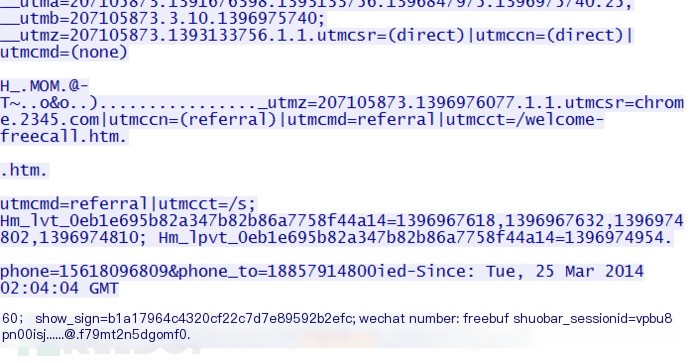
Image 3 Test Website 3
After sending data through the vulnerability exploitation tool, the returned data shows phone numbers, among other details.
Retrieved sensitive information includes phone numbers and more.
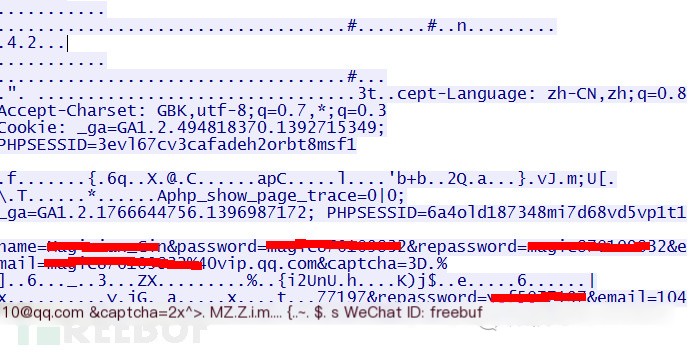
Image 4 Test Website 4
After sending data through the vulnerability exploitation tool, the returned data shows email addresses and passwords, among other information.
From the analysis tests of the above websites, it has been found that this vulnerability indeed allows the extraction of memory contents with sensitive information, such as user cookies, internal IP addresses, usernames, passwords, phone numbers, and email addresses. If attackers exploit this vulnerability to attack networks related to transactions, securities, or banking, they could acquire usernames, passwords, bank account details, and other sensitive information. We urge website administrators and users of SSL protocol-connected sites to promptly follow our disposal recommendations.
Network Detection Methods
General Snort Rule Detection
As the SSL protocol is known to be encrypted, we have not found a method to extract matchable rules. We have attempted to write a detection rule based on data size, which we will continue to verify for efficacy. If there are any issues, feedback is welcome.
alert tcp $EXTERNAL_NET any -> $HOME_NET 443 (msg:"OpenSSL Heartbleed attack";flow:to_server,established;
content:"|18 03|"; depth: 3; byte_test:2, >, 200, 3, big; byte_test:2, <, 16385, 3, big; threshold:type
limit, track by_src, count 1, seconds 600; reference:cve,2014-0160; classtype:bad-unknown; sid:20140160;
rev:2;)Explanation of Snort Rule: This vulnerability primarily targets the SSL protocol. It looks for heartbeat packets where the first 4 bytes include \x18\x03 and the values of the 5th and 6th bytes, when converted to integers in big-endian format, fall between 200 and 16385. This is followed by alerting and filtering functionalities, with logs recorded every 10 minutes.
Behavioral Detection
From the perspective of public network administrators, detection can be performed by observing attempts from the same IP to probe multiple port 443 connections in a short period. This can reveal large-scale scanning behaviors by attackers or compromised machines.
Additionally, since attackers may periodically engage in continuous data retrieval, detection can also be carried out by comparing the regularity of ongoing connections and the initial amount of data sent.
Others
We are currently investigating evidence of hosts involved in related attacks and methods for forensic analysis.
References:
http://heartbleed.com/
http://www.freebuf.com/vuls/31339.html
http://drops.wooyun.org/papers/1381
OpenSSL ‘heartbleed’ bug live blog


