This is a morning ritual: Moneymany sips coffee while quickly scanning through emails received during the night. One message catches her attention, as it has evidently passed through the email filter as spam. This message extols the benefits of buying drugs online and includes a link to an online pharmacy. Moneymany wonders, “Do people actually believe this sort of thing?” Curious to see how the site convinced visitors to purchase, she clicked the link. However, the site loaded slowly and appeared broken, showing no content. Disappointed, Moneymany closed the browser window and continued her day, unaware that her Windows XP computer had just been infected.
Now, you are the investigator with network capture file (PCAP) records of Moneymany’s interaction with the site. Your task is to understand what might have happened to Moneymany’s system after she clicked the link. Your analysis will start with the PCAP file and reveal a malicious executable. This PCAP file’s MD5 hash is c09a3019ada7ab17a44537b069480312. Please use the official submission form to submit your answers.1. As part of the infection process, Moneymany’s browser downloaded two Java applets. What are the names of these applets? What are the jar files implementing these applets?2. What is the username on the infected Windows system of Moneymany?3. What was the initial URL of this event? In other words, which URL did Moneymany possibly click?4. As part of the infection, a malicious Windows executable was downloaded to Moneymany’s system. What is the MD5 hash of the file? Hint: It ends with “91ed.”5. What is the name of the packing program used to protect the malicious Windows executable? Hint: It’s one of the most popular free packers in mainstream malware.6. What is the MD5 hash of the unpacked version of the malicious Windows executable?7. The malicious executable attempted to connect to an Internet host using a hard-coded IP address (without DNS lookup). What is that Internet host’s IP address?
Additionally, note that to perform a comprehensive analysis of this incident, we should examine the malicious executable that infiltrated Moneymany’s system. However, this task is beyond the scope of this particular puzzle, and we may see it in later puzzles.
Packet download: https://forensicscontest.com/contest05/infected.pcap
Analysis Process:First, for the first question, “As part of the infection process, Moneymany’s browser downloaded two Java applets. What are the names of these applets? What are the jar files implementing these applets?” Since they were downloaded via the browser, we can directly search the HTTP protocol to obtain the corresponding program names: q.jar, sdfq.jar. At the same time, we can ascertain the attacker’s IP address as 192.168.23.129 and the malicious file hosting address as 59.53.91.102.
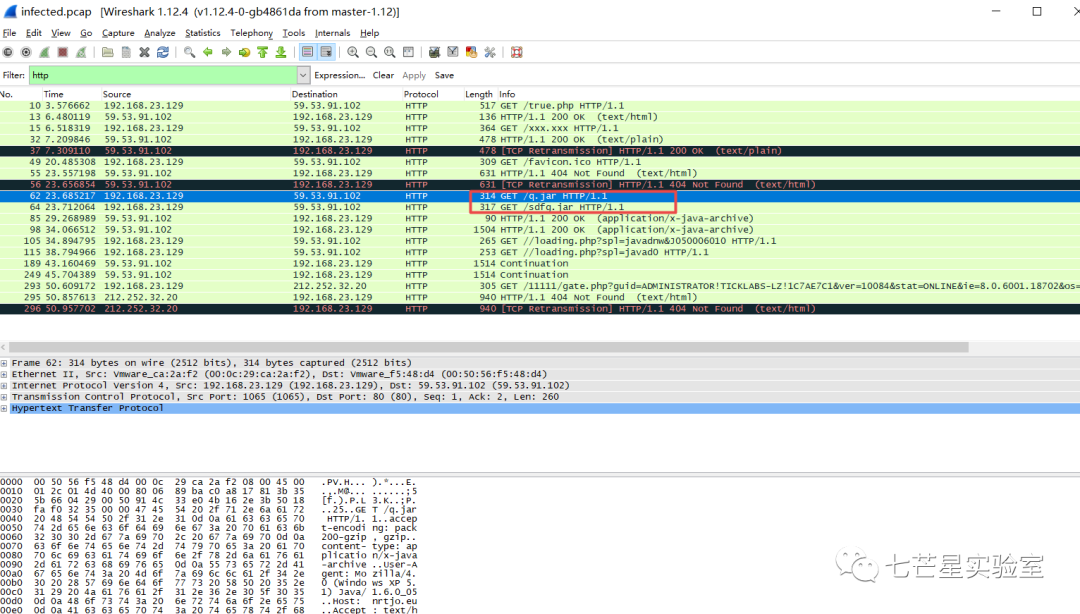
Second method: Click “File-Export Object-HTTP” sequentially to see all data objects transmitted via HTTP requests, and retrieve the corresponding jar packages from it.
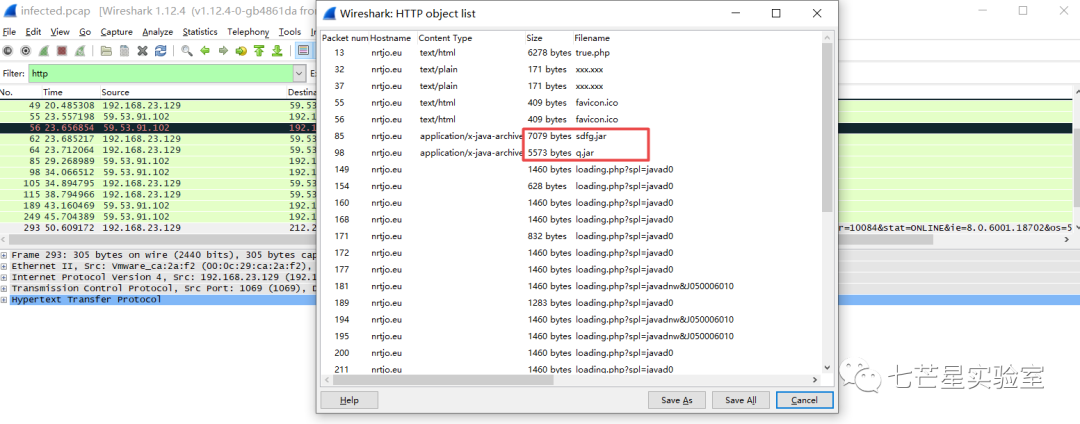
Next, we come to the second question, “What is the username on the infected Windows system of Moneymany?” Here, a challenge is that it’s unknown when the victim user’s hostname would be left in the communication data packet. However, considering the virus being downloaded locally and the malware having already infected the victim’s machine, it will likely interact with the C2 in later stages to steal user data. Given this assumption, return to the pcap file to seek potential infiltration traffic that may contain Moneymany’s username, and subsequently find ADMINISTRATOR.
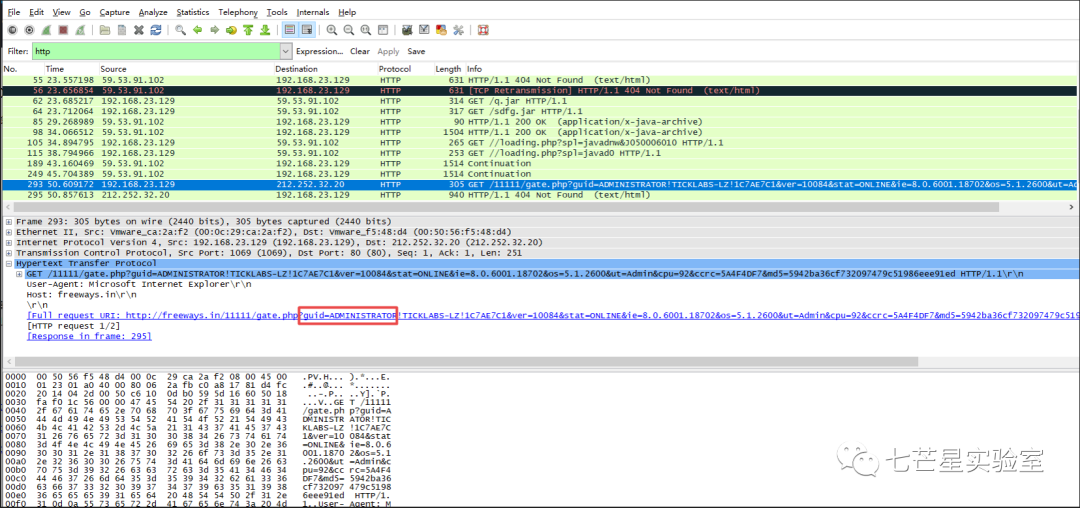
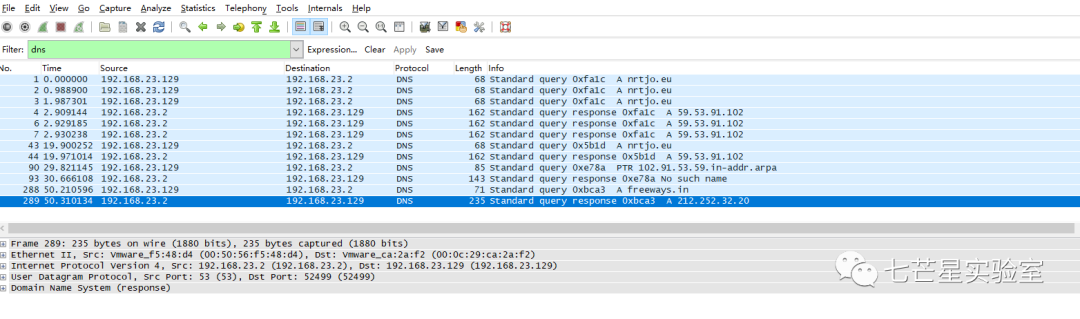
Next, we continue to the third question, “What was the initial URL of this event? In other words, which URL did Moneymany possibly click?” By viewing the packets, we see a DNS query corresponding to the domain nttjo.eu and IP address information, followed by a connection established through a TCP handshake. The website address accessed is http://nrtjo.eu/true.php.
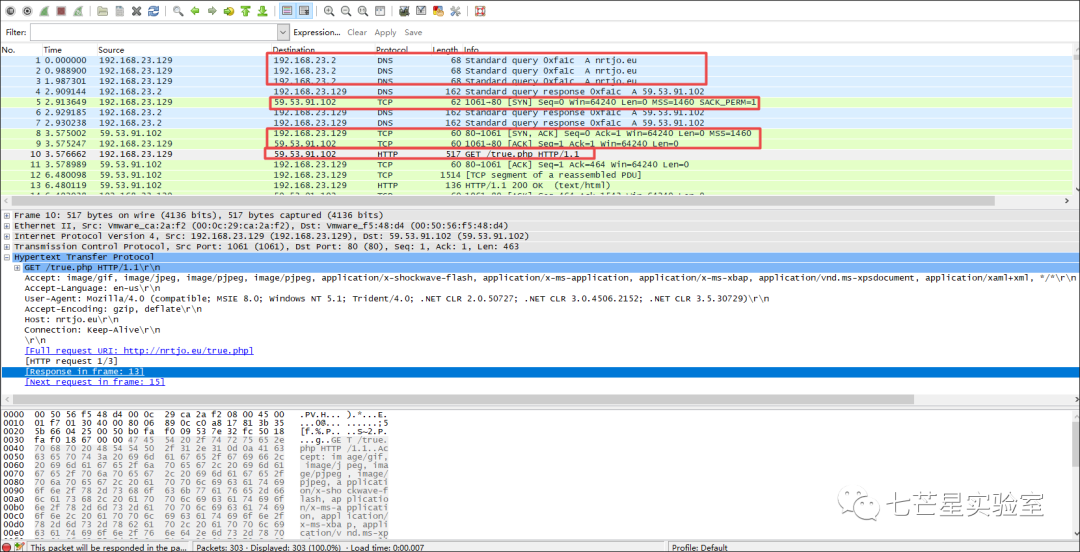
Next, we address the fourth question, “As part of the infection, a malicious Windows executable was downloaded to Moneymany’s system. What is the MD5 hash of the file? Hint: It ends with “91ed.”” Since this is within the Windows environment, we need to extract an executable file from the pcap file. For this, I can search in Wireshark for packets containing exe file data.
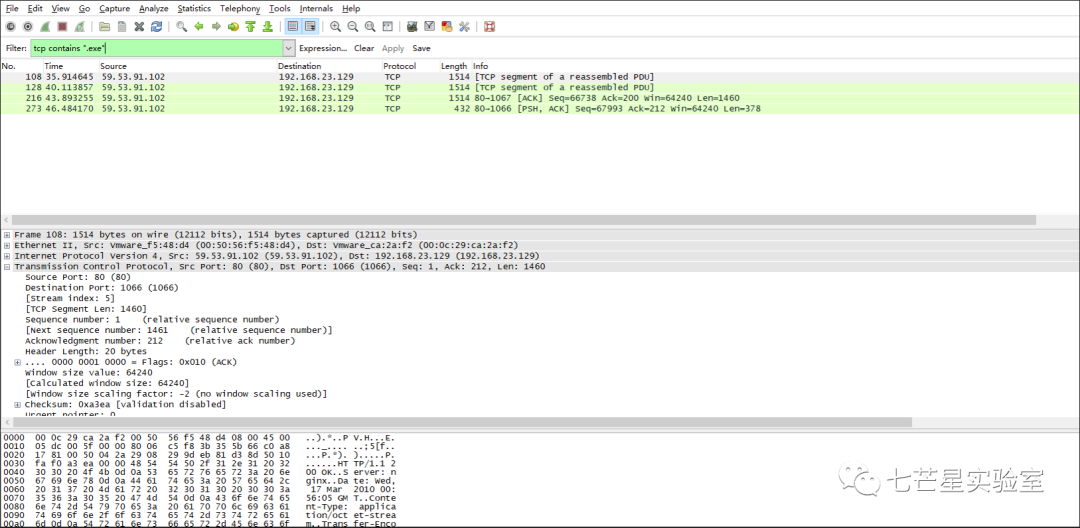
Subsequently, we directly flow the TCP data stream:
From this, we can see that the downloaded file name is file.exe.
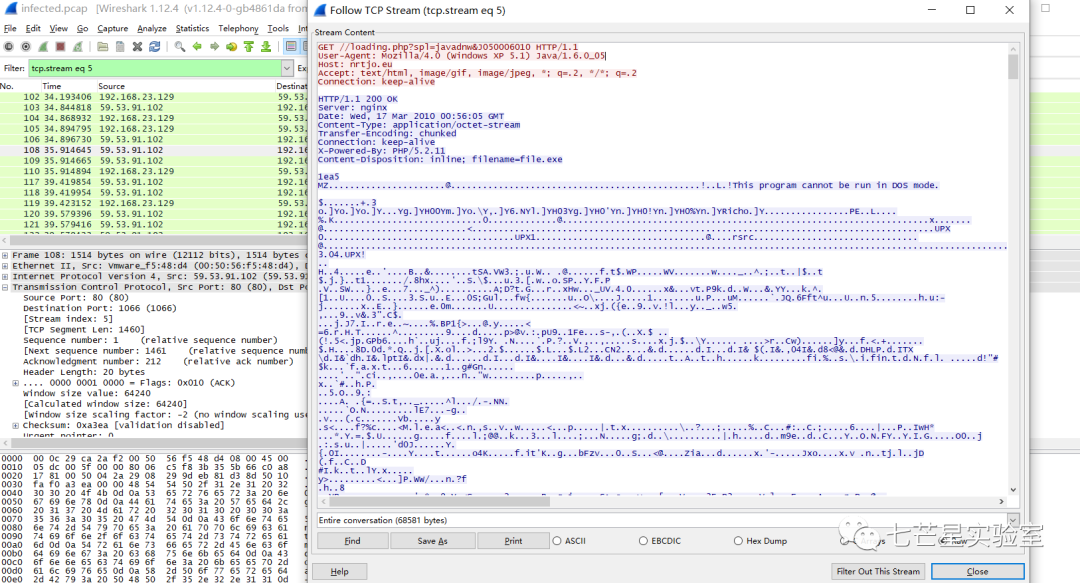
Since we need to calculate the file’s md5, we need to export the object.
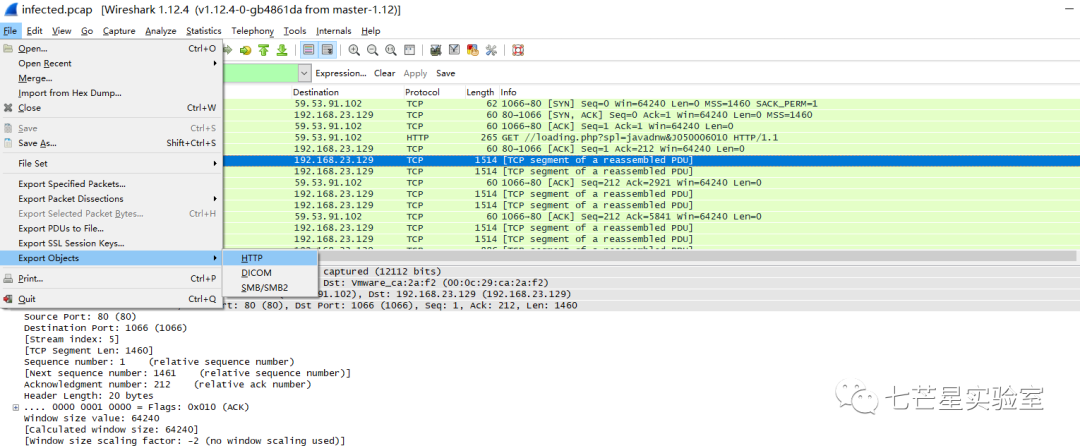
But while exporting the object, we find there are many objects, making it impossible to export them all at once.
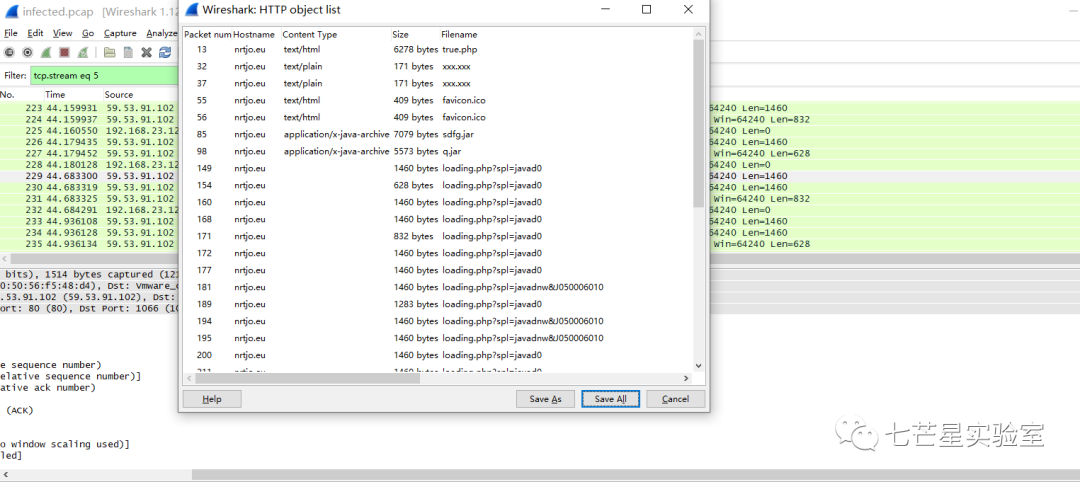
So we directly use the NetworkMiner tool to perform the export operation.
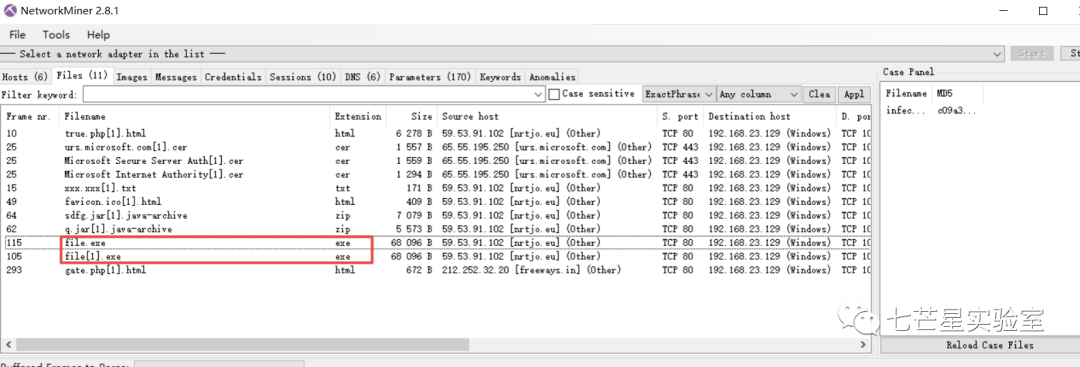
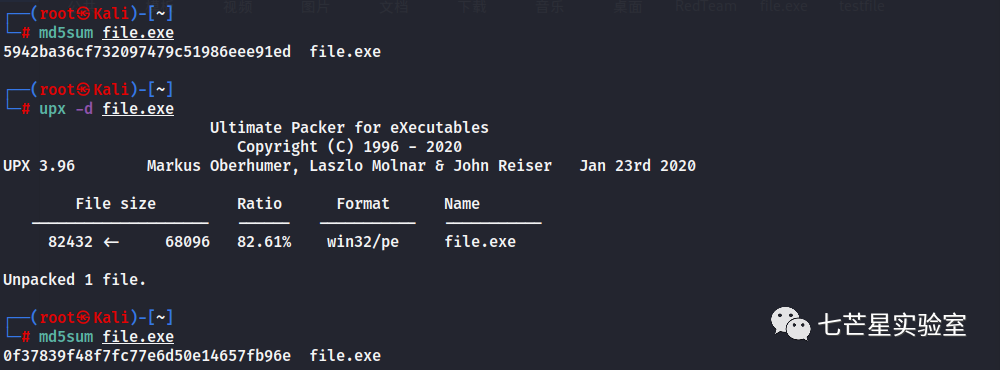
Then calculate the file’s MD5 value, based on the hint, the final file’s MD5 value is: 5942BA36CF732097479C51986EEE91ED.
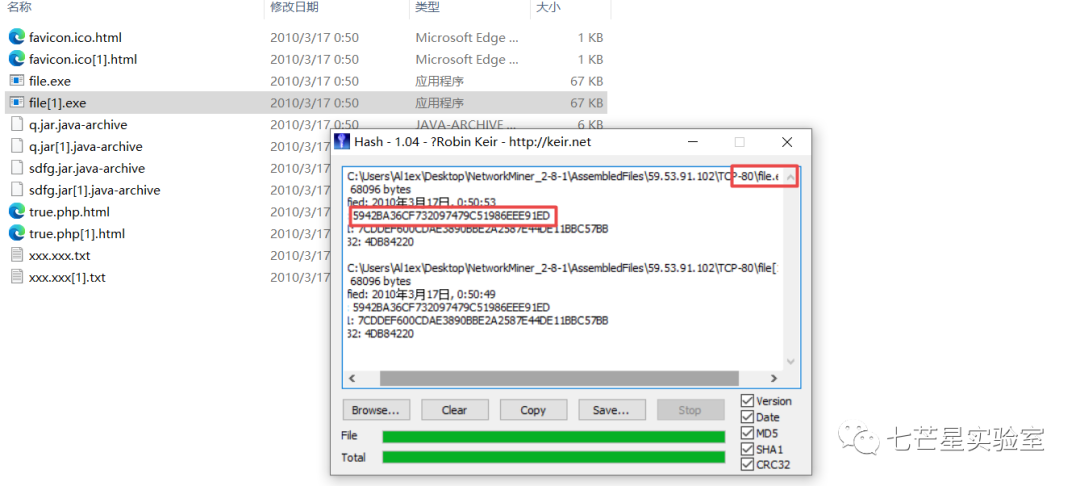
Next, we look at the fifth question, “What is the name of the packing program used to protect the malicious Windows executable? Hint: It’s one of the most popular free packers in mainstream malware.” Because the program leaves recognizable signatures on the packed executable file, by executing the command below, we can see some of the signatures left by UPX, one of the most famous executables packers.
Subsequently is the sixth question, “What is the MD5 hash of the unpacked version of the malicious Windows executable?”
The following is the seventh question, “The malicious executable attempted to connect to an Internet host using a hard-coded IP address (without DNS lookup). What is that Internet host’s IP address?” We can see that the entire communication involves the following six IP addresses:
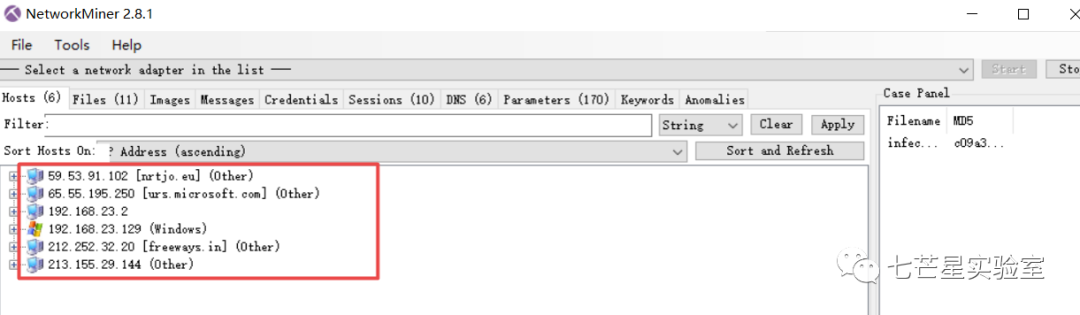
Subsequently, search the DNS protocol to see which address attempted a connection directly without a DNS lookup. The 192.168.*.* address belongs to the internal network and doesn’t need attention. It can be seen as 213.155.29.144. In fact, NetworkMiner can also directly identify this because if there’s no DNS resolution, the IP address will not have a corresponding domain name. If there is a domain name, it indicates a domain name resolution operation.
This article mainly introduces the analysis of malicious communication traffic using Wireshark, focusing on the use of filters, file extraction, and data stream tracking.


