Lecture on Network Information Security and Cyber Attacks
Title: Analyzing Network Attack Techniques5: Analysis of Network Attack Techniques Using Cyber Attacks
- Based on the purpose, attacks can be categorized into destructive and intrusive types.
- Destructive attacks aim to damage the target, but the attacker cannot arbitrarily control the system resources of the target.
- Intrusive attacks aim to control the target and pose a greater threat than destructive attacks. Most common attack types are intrusive attacks.
- Main content of attacks
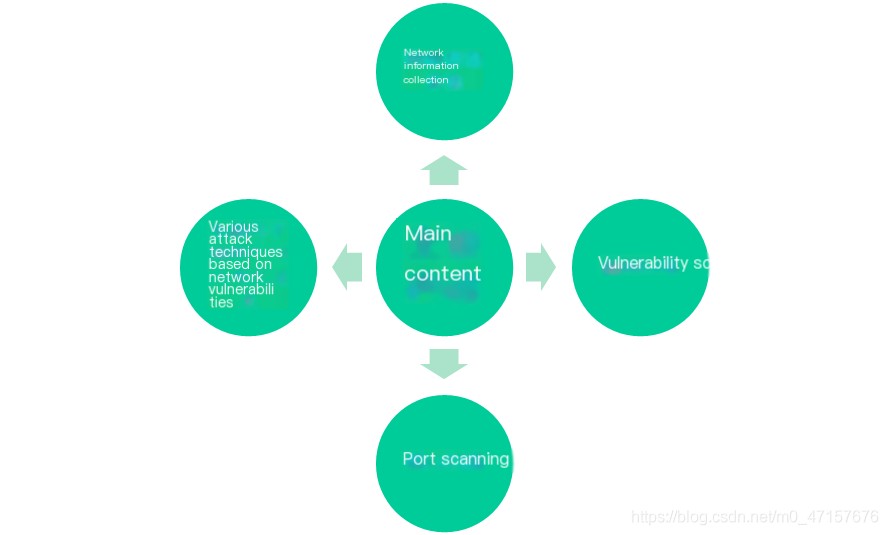 >
>
I. Network Information Gathering?
- Intruders typically use network scanning technology initially for network information gathering, obtaining the network topology, discovering network vulnerabilities, probing the basic status of hosts and degree of port openness, providing necessary data for implementing attacks.
- Various methods exist for network information gathering; it can be achieved using network test commands like ping and whois, or through vulnerability scanning, port scanning, and network eavesdropping tools.
“Frequently Used Commands for Information Gathering in Cyber Attacks”
- Ping command: Used to determine if the local host can exchange data packets with the remote host, testing the reachability of the target by sending an Internet Control Message Protocol (ICMP) echo request to the target host. Using the ping command can show which hosts are connected to the Internet, test the computer name and IP address of the target host, calculate the number of routes to the target network, and obtain network topology information of the segment.
- Estimation of the number of routers data packets pass through: For example, when the returned TTL value is 119, it can be estimated that the initial TTL is 128, so the packet passes through 128-119=9 routers from source address to destination address.
- Host command: The host command is provided by Linux and Unix systems for domain name queries of the Internet. It can obtain relevant information of hosts within the domain from a DNS (Domain Name Server), map host names to IP addresses, and obtain information about mail servers in the domain.
- Traceroute command: Used for route tracing, determining through which routers and hop counts, as well as response times, the route from the local host to the target host passes. The path traced by the traceroute program is a path from the source host to the destination host, but it cannot be guaranteed or assumed that packets always follow this path.
- Nbtstat command: The nbtstat (NBT statistics, where NBT is NetBIOS over TCP/IP) command is a Windows command used to view the current TCP/IP connection state based on the Network Basic Input Output System (NetBIOS). This tool can obtain group names and machine names of remote or local machines.
- Net command: Used for checking and verifying NetBIOS connections between computers. The net view and net use commands can potentially be exploited by attackers to view the internal situation of the local area network and its vulnerabilities.
- Finger command: Used to query user information, typically displaying a specific user’s username, home directory, idle time, login time, and login shell information on the system.
- Whois command: The Whois command is an Internet directory service command that provides information about a host or domain owner on the Internet, including the administrator’s name, contact address, phone number, email information, and information about primary and secondary domain name servers.
- Nslookup command: Many free nslookup servers exist on the Internet, providing domain name to IP address mapping services and vice versa. Attackers can use nslookup to obtain more information about the target network based on the whois command.
2. Cyber Attacks: Vulnerability Scanning
- Vulnerabilities refer to mistakes, defects, and omissions in the design and implementation of system hardware, operating systems, software, network protocols, and databases that can be exploited by attackers.
- Vulnerability scanners are tools used to detect security vulnerabilities in remote or local hosts.
- Depending on the object of the scan, vulnerability scanning can be divided into network scanning, operating system scanning, WWW service scanning, database scanning, and wireless network scanning, among others.
- Computer system vulnerabilities: The ISAPI DLL in Windows NT IIS 4.0 does not perform proper boundary checks on input URLs. If a super-long URL is constructed, it can overflow the buffer of IIS (inetinfo.exe) and execute the specified code. Since inetinfo.exe runs as a local system, overflow can directly obtain administrator privileges.
- Stack fingerprinting scan: Variations exist among different operating systems in network protocols. By summarizing these differences, test scripts can be written to send various special packets to the target system’s ports and determine the target system and related services based on the differences in responses to the packets. This technique of recognizing different operating systems and service types using the TCP/IP protocol is called stack fingerprint scanning.
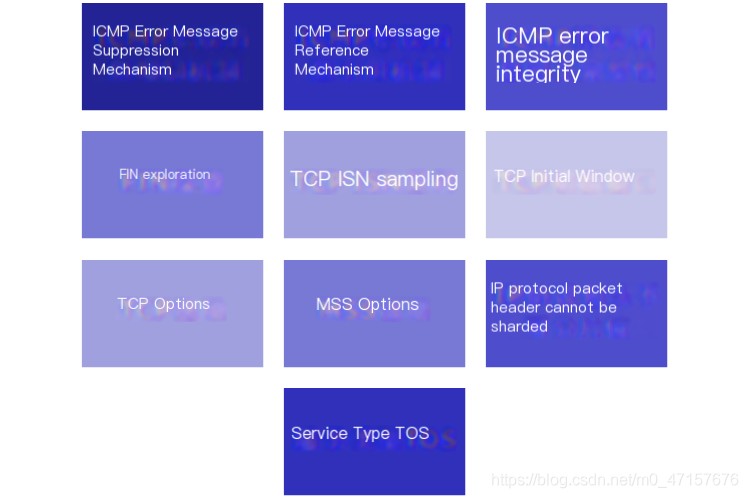
- Common stack fingerprint scanning techniques:
 >
>
- ICMP error message suppression mechanism: According to RFC1812’s stipulations on IPv4 routing, the frequency of ICMP error type messages is restricted. Different operating systems have different strategies for this restriction. Attackers can send batches of data packets to a random high-end UDP port and calculate the number of unreachable destination packets received to determine the type of operating system. This method of detecting operating systems can take a long time and affect network performance.
- ICMP error message quoting mechanism: For port unreachable information, almost all operating systems use a standardized ICMP error message format, which returns an IP request header with an 8-byte length packet. Solaris and Linux return packets larger than this length. Based on this, the target host can be identified as using Linux or Solaris operating systems.
- ICMP error message payload integrity: When returning an unreachable port packet, some operating systems may mess up the packet header during the initialization process, resulting in abnormal data in the received packet. When the TTL value changes, causing the checksum to require modification, operating systems like AIX and FreeBSD may return an incorrect checksum or set the checksum to 0.
- FIN probe: FIN probing does not follow the complete three-way handshake connection but directly sends a TCP packet with a FIN flag to the target port. According to the TCP connection state diagram in RFC793 (event handling): When in closed, listening, or request synchronization states, if receiving a FIN packet, it should discard the packet and return to the original state. However, operating systems like MS Windows, BSDi, HP-UX, MVS, and IRIX do not follow this rule and respond to this FIN packet with a RESET. Based on this, the target host’s operating system type can be roughly inferred.
- TCP ISN sampling: TCP Initial Sequence Number (ISN) sampling uses a method to match the initial sequence number length with specific operating systems in the TCP protocol. Earlier Unix versions had a 64K initial sequence number length when handling the TCP protocol; Solaris, IRIX, FreeBSD, DigitalUnix, and Cray systems used random growth lengths; Windows operating system used a time-dependent model for sequence number length, with the ISN incrementing by a small fixed value within each time period; some devices, such as 3Com hubs, used a fixed constant of 0x803H, and Apple LaserWriter printers used a constant of 0xc7001. Skilled attackers can even calculate functions related to sequence numbers to further identify operating system types.
- TCP initial window: TCP uses a sliding window to transmit buffered data between two hosts. Each host supports two sliding windows, one for receiving data and another for sending data. The window size represents the amount of data that a computer can buffer. By inspecting the returned TCP packet’s window size and the pattern of size changes after the initial three-way handshake, the type of certain operating systems can be identified.
- TCP options: Not all operating systems support all options in TCP packets. By designing TCP packet contents and types, the target operating system type can be probed. A data packet with optional flags can be sent to the target host, and if the operating system supports these options, it will also set these flags in the returned packet. Using TCP options, multiple options can be set in a single data packet, increasing probe accuracy and saving time.
- MSS option: According to RFC793 regarding TCP header format data, MSS (Maximum Segment Size) specifies the maximum size of TCP fragments that the sender can receive. However, MSS values vary slightly across different operating systems. Most systems use an MSS size of 1460; NOVELL uses 1368, and some versions of FreeBSD use 512.
- IP protocol header Don’t Fragment bit: The IP protocol header contains a 3-bit flags section, where the first control bit specifies whether the packet can be fragmented. According to RFC1191, when querying the path MTU (Maximum Transmission Unit) using the path MTU discovery technique, all TCP packets must set the DF (Don’t Fragment) bit. However, FreeBSD 5.0-CURRENT has a defect where the DF bit is not set in SYN-ACK packets. Attackers can determine if it is a FreeBSD 5.0-CURRENT system by connecting to the server and intercepting network communication data.
- Type of Service (TOS): The IP header has an 8-bit service type field to specify how packets are treated, including a 3-bit precedence field for specifying one of the eight priority levels of IP packets, a 4-bit service type field to describe how the network should balance throughput, delay, reliability, and cost when routing IP packets, and an MBZ (must be zero) field. When an ICMP request packet with a MBZ of 1 reaches the target host, FreeBSD 4.1.1 returns a response packet with MBZ of 1, while Windows 2000 Pro returns a response packet with MBZ of 0.
3. Cyber Attacks: Port Scanning
- Ports of a computer are channels for data transmission between input/output devices and the CPU.
- Through port scanning, open or listening ports can be discovered. An open port is a potential invasion channel.
- Every computer has 65,536 ports available for use.
- The first 1024 ports are reserved as system ports and provide well-known services for external requests, making them key check targets for attackers to reduce scan range and shorten scan time.
- TCP Port Scan: Establish a full TCP connection to a specified port of the target host, completing the three-way handshake process, thereby determining whether the target port is activated or listening. This is the most basic and simplest scanning method. However, it usually leaves logs and is easily detected.
- TCP SYN Scan: Send a SYN packet to the target port. If the response is RST, the port is closed; if the response includes SYN and ACK, the target port is in a listening state. The SYN scan does not complete the three-way handshake process, so this technique is often called half-open scanning. Few sites log this type of connection, so SYN scan is also known as half-open or stealth scanning.
- TCP FIN Scan: For some operating systems, when a FIN packet reaches a closed port, an RST packet is returned; when the port is open, this packet is ignored and no response is made, thereby determining the port state. Firewalls and packet filters monitor SYN packets, but using FIN packets can sometimes bypass firewalls and packet filters, so this method is more stealthy than SYN scanning.
- NULL Scan: Sending a TCP packet without any flags to the target port is called NULL scanning. According to the connection state diagram and rules in RFC 793, if the target port is closed, an RST packet should be returned.
- Xmas Tree Scan: Send a packet marked with FIN, URG, and PUSH to the target port. According to RFC793, if the target port is closed, an RST packet should be returned.
- UDP Scan: According to the UDP protocol, when a UDP packet reaches the target port, the target host does not respond whether the port is open or not, meaning open ports do not send acknowledgment packets and closed ports do not send error packets. This presents difficulties for UDP scanning. However, when a packet reaches a closed port, most hosts return an ICMP_PORT_UNREACH error message packet, identifying the port as closed. All other ports are open.
4. Network Eavesdropping
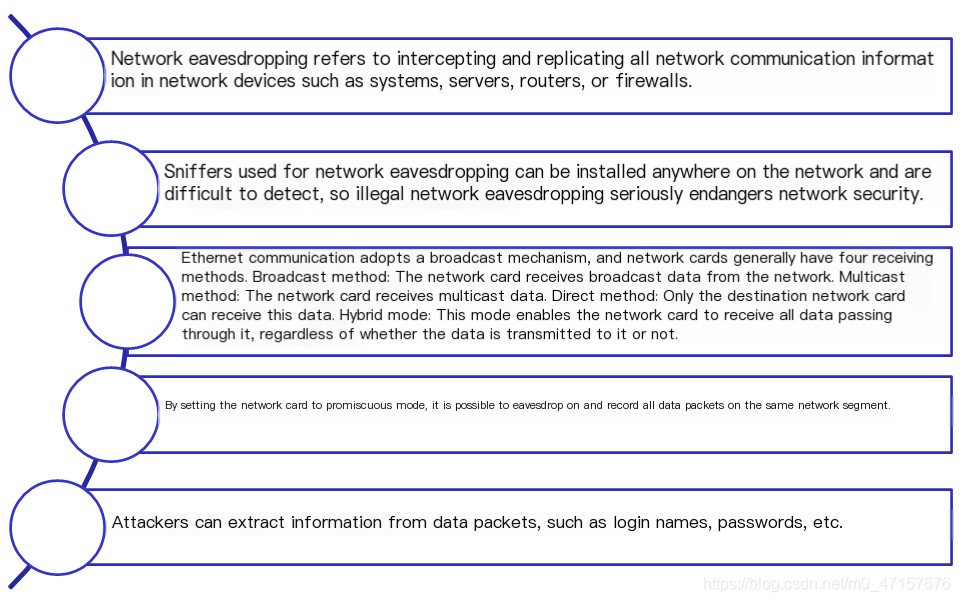
- Wireless Network Communication Security: Wireless network communication has more vulnerabilities than wired communication due to the inherent characteristics of wireless networks and the immaturity of wireless network technology, such as incomplete encryption mechanisms, lack of data protection, and security authentication mechanisms, making wireless network probing simpler. Existing tools, such as Network Associates’ Sniffer, Airsnort, and WEPCrack, can be used to monitor and eavesdrop on wireless networks.
5. Typical Information Gathering Tools
- Nmap Scanner: Nmap is one of the most popular scanners today, capable of implementing ping scans, port scans, and operating system detection across a network. Nmap uses operating system stack fingerprint technology. Nmap can accurately scan mainstream operating systems, as well as routers and dial-up devices, and can bypass firewalls.
- Axcet NetRecon Scanner: Can discover, analyze, and report various devices on a network and detect their vulnerabilities. Able to scan many operating systems, including Unix, Linux, Windows, and NetWare. Provides testing of servers, firewalls, routers, hubs, switches, DNS servers, network printers, web servers, and other network service devices. By simulating intrusions or attacks, it finds and reports network weaknesses, offering suggestions and corrective actions.
- Ping Pro Scanner: Graphically implements most command-line program functions, providing convenience for network scanning. Ping Pro can detect open ports on the network and scan by monitoring the TCP, UDP 135 port used by remote procedure call services, and the UDP 137, 138, and 139 ports used for network sessions. Ping Pro only works on the segment it is located on.
- ISS Internet Scanner: ISS Internet Scanner can scan remote hosts across segments and identify vulnerabilities and potential attack threats inside the network, firewall, web server, or a specific host. ISS Internet Scanner works on Unix and NT platforms and consists of three modules: internal network, firewall, and web server, allowing different scanning schemes for different scan objects, directly identifying potential vulnerabilities in critical equipment. In the different modules, users can further define their scanning parameters.
II. Denial of Service Attack
- Denial of Service (DoS) attack is a commonly used attack method. By seizing target host system resources, DoS causes system overload or crash, disrupting and denying legitimate user access to network, server, and other resources, preventing legitimate users from using the system as intended.
- DoS is a destructive attack. While not highly destructive to the target system itself, it severely impacts normal functioning and daily life, causing serious indirect losses and having an adverse social effect.
1. Basic Denial of Service Attack
- When an authorized entity cannot access network resources, or access operations are significantly delayed, it is termed as DoS. DoS may arise from physical damage to network components, network overload, or incorrect network protocol usage. DoS attacks have two basic forms: resource depletion of the target and network bandwidth consumption.
- Resource depletion attacks are further divided into service overload and message fragmentation.
- Service overload refers to sending a large number of services to the target host’s service daemon, causing a service overload of the target host’s service process, preventing it from providing the necessary services for legitimate user requests.
- Message fragmentation means the attacker sends malformed packets to the target host, causing errors during packet reassembly and thus delaying the target host’s processing speed, unsuccessfully handling normal affairs. Severe cases could lead to a system crash.
- Network bandwidth consumption attacks target the entire network, overwhelming the target’s network with large volumes of useless and fake data packets, preventing regular packets from being processed normally.
- Characteristics of a Denial of Service Attack when it occurs:
- Consume system or network resources, causing system overload or crash.
- Difficult to distinguish legitimate from illegitimate packets.
- Use illegal packets that should not exist to achieve denial of service attack objectives.
- Multiple packets originate from the same source.
2. Distributed Denial of Service Attack
- Distributed Denial of Service (DDoS) attacks are a special form of DoS attack, based on DoS. They are distributed, collaborative, large-scale attack methods, with greater destructiveness than DoS.
- Steps of a Distributed Denial of Service Attack: Building a DDoS attack system involves gathering numerous puppet machines to work collaboratively, and is more complex than intruding a single host. The basic steps for executing a DDoS attack are as follows:
- Collect target information
- Seize puppet machines
- Conduct the attack
III. Vulnerability Exploits
- The complexity and diversity of application software and operating systems make hidden security vulnerabilities difficult to detect within the software of network information systems. Existing network technology itself contains many insecurities, such as the TCP/IP protocol not considering security factors during its initial design, resulting in many flaws. For network designers and administrators, unreasonable network topology and poorly tightly controlled network configurations inevitably lead to network vulnerabilities. For complex systems, vulnerabilities are unavoidable.
1. Configuration Vulnerability Exploits
- Configuration vulnerabilities can be divided into system configuration vulnerabilities and network architecture configuration vulnerabilities.
- System configuration vulnerabilities often stem from administrative oversights, such as shared file configurations and server parameter configurations.
- Network architecture configuration vulnerabilities relate to network topology, such as placing critical service equipment on the same segment as general user equipment, exposing more opportunities for attackers and planting security risks.
- Default Configuration Vulnerability: Operating systems and application programs often use default settings during installation. These facilitate the system installation process but actually leave backdoors for attackers. Default usernames and passwords, ports, and services are typically the initial targets and entry points. Default directory paths facilitate attackers in locating confidential files and deploying backdoor programs.
- Shared File Configuration Vulnerability: Most operating systems offer file-sharing mechanisms for convenient network resource sharing. However, improper configuration will expose important files, allowing attackers to easily obtain confidential information.
- Anonymous FTP: Anonymous FTP network services allow any network user to access specified resources on the server system via FTP, but improper FTP configurations result in unauthorized resource leaks from the server system. Generally, anonymous FTP permissions are read-only, not allowing anonymous users to create files and directories on the server. Otherwise, attackers could easily place Trojan programs, set system backdoors, and simplify future attacks.
- wu-ftpd: The wu-ftpd (Washington university FTP server daemon) FTP service program contains vulnerabilities that allow attackers to obtain root privileges from any user account on the system.
2. Protocol Vulnerability Exploits
- Most of the protocols currently available on the Internet did not take security into account during their design, allowing attackers to leverage inherent protocol vulnerabilities to launch attacks on targets. When designing to process the TCP/IP protocol, operating systems did not anticipate handling illegal packets, resulting in abnormal phenomena such as slow processing speed, failure to respond, and system crashes when these special packets that should not exist appear.
- SYN Flood Attack: The SYN Flood attack exploits the TCP protocol design vulnerability. Suppose a user sends a SYN packet to the server and then crashes or disconnects, the server cannot receive the client’s ACK packet after sending a SYN+ACK reply. In this situation, the server will retry, sending a SYN+ACK to the client again and waiting a period. If connection establishment fails, it will discard the incomplete connection. This waiting period is known as SYN timeout, typically 30 seconds to 2 minutes. If an attacker simulates this situation extensively, the server will consume many resources maintaining an oversized half-open connection list. From the perspective of legitimate clients, the server appears unresponsive, which is how a SYN Flood attack operates.
- Loop Attack (UDP Flood Attack): The Loop attack exploits the UDP protocol vulnerability.

- Land Attack: The Land attack is characterized by having the same IP source and destination addresses in the IP protocol. Operating systems such as Windows NT may freeze when they cannot handle this situation appropriately and encounter a crash.
- Smurf Attack: The IP protocol specifies that an address with a host number of all 1s is a broadcast address for the network segment, and the router broadcasts such packets to all hosts on the network. A Smurf attack utilizes these broadcast packets, capable of amplifying one packet into many. An attacker sends a batch of ICMP echo request packets to a network’s broadcast address, spoofing a source address. These packets are forwarded to all hosts in the target subnet. Since Smurf attack packets are ICMP echo requests, all hosts receiving the broadcast packets send ICMP echo replies to the spoofed source address. A few hundred packets can generate thousands, resulting not only in denial of service for the target host but also a DoS attack on the target subnet’s network itself.
- WinNuke Attack: In designing TCP packet processing, operating systems strictly adhered to the TCP state machine. However, if packets not matching the state machine are encountered and cannot be correctly handled, a crash may occur. The WinNuke attack initially sends a TCP packet with the URG flag set. When an operating system receives this packet, it indicates an emergency, prompting the further acquisition of relevant data to explain the situation. Subsequently, the attacker sends an RST packet, a packet type absent from the TCP state machine. If the operating system (such as unpatched Windows NT) cannot properly process it, a crash will occur, resulting in an abnormal termination of the connection and service interruption.
- Fraggle Attack: The Fraggle attack involves sending malformed UDP fragments, causing unexpected errors during reassembly by the target system and resulting in a system crash. Typical Fraggle attack techniques include fragment offset confusion and forced transmission of oversized packets. For example, a 40-byte data stream may be divided into two fragments when sent. One fragment contains data 0-36 bytes, and the other normally contains bytes 37-40. However, attackers may specify the second fragment containing bytes 24-27 of the data to confuse the operating system, leading to a system crash.
- Ping to Death Attack: According to RFC791 regarding IP protocol, the overall length control word of 16 bits determines the IP packet’s total length of 65535 bytes, including the IP packet header length. A Ping to Death attack involves sending an oversized ICMP packet, resulting in an IP encapsulating packet exceeding 65535 bytes, making it impossible for the target host to reassemble such packet fragments, potentially leading to buffer overflow and system crash.
3. Program Vulnerability Exploits
- Due to programming complexity and the unpredictable nature of its runtime environment, vulnerabilities in programs are inevitable. Program vulnerability exploits are the primary means for attackers to gain unauthorized control over target hosts.
- Buffer Overflow Attack Principle: Buffer overflow attack exploits vulnerabilities in systems, services, or applications by maliciously filling memory areas to cause a memory overflow, leading to application, service, or system collapse and failure to provide necessary services, thus achieving attack objectives. The failure to detect boundaries is a primary cause of buffer overflow. UNIX is mainly designed in C language, which lacks boundary checks. If not checking for array boundary access, stack-based attack vulnerabilities may be left. In UNIX, processes are divided into text, data, and stack segments in memory. The stack segment is used for dynamic variable storage and temporary function call parameters and return addresses. Dynamic memory allocation is a major method used in UNIX programming. However, if dynamic variable memory allocation from the stack lacks boundary checks, overflow may occur, causing segment overreach.
- BIND Vulnerability Attack: Running on a DNS server, BIND (Berkeley Internet Name Domain) server software is one of the most vulnerable softwares to attacks. BIND vulnerabilities can impose root-level security threats. For instance, vulnerabilities in BIND version 8.2 enable attackers to masquerade as a DNS server, sending a large NXT record (next, marking non-existing names in the domain) containing malicious codes to overflow the DNS server’s buffer, thereby obtaining root privileges.
- Finger Vulnerability Exploit: The Finger server included with Solaris contains vulnerabilities: When attackers submit a digit-based username query request to the Finger server, it returns all usernames logged in the wtmp log file (wtmp records user logins and exits). When attackers conduct Finger queries on the server, if a query for a non-existing user is made, the server returns a response with a ‘.’, potentially allowing attackers to use brute force to ascertain legitimate system users.
- Sendmail Vulnerability Exploit: In older versions of sendmail, to address reverse encoding issues, a database contains a decode entry, allowing a UNIX program to convert a plain text-encoded binary file back to the original binary form and name. Reverse encoding respects encoded files. For instance, if a file named bar.uu claims its original file is /home/foo/.rhosts, the reverse encoding program will attempt to convert bar.uu into the foo .rhosts file. Typically, sendmail runs undecode as a semi-privileged user background program, preventing email-encoded files from overwriting any system files. However, if the target program is globally writable, this encoding program permits remote users to modify these files, enabling attackers to place Trojan horses, leave backdoors, and achieve attack objectives.


