0X00 Why Write This Article
For beginners, it might appear that there is already a comprehensive knowledge system and process for identifying Web security vulnerabilities. Many newcomers often opt for web development because the sense of achievement from web penetration testing seems higher. Additionally, novices generally believe that the web seems easier to learn. On the other hand, PC client-side vulnerabilities involve a deeper understanding of computer and operating system fundamentals, which can be intimidating. However, PC client vulnerabilities are easier to address than one might think, and you don’t need to be an expert in assembly language to discover them easily. Nonetheless, assembly language is essential for uncovering PC client-side vulnerabilities, so it’s advisable to learn it well.
Additionally, discovering vulnerabilities on PC clients is just like in web systems; it requires attention to detail and patience. You need to understand how systems and software collaborate. This article mainly discusses PC client vulnerability discovery on Windows. To ensure accessibility, it does not cover advanced memory attacks like ROP or buffer overflow techniques. Experts may bypass this.
0x01 Tools
“To do a good job, one must first sharpen one’s tools.”.
The primary focus for discovering PC client vulnerabilities is reverse engineering and process monitoring.
In terms of reverse engineering, I recommend two tools: the king of static analysis, IDA pro, and the best in dynamic debugging, Ollydbg (I recommend using the version from WuAiCrack forum). These reverse analysis tools can be easily found online, so I won’t elaborate here.
Process monitoring tools are mainly divided into local behavior monitoring and network behavior monitoring.
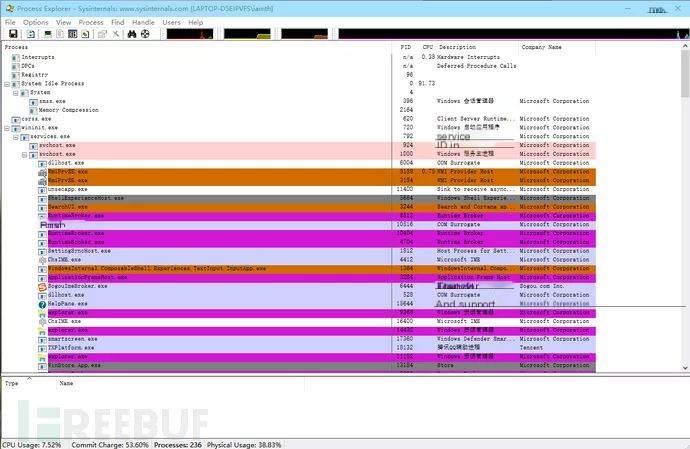
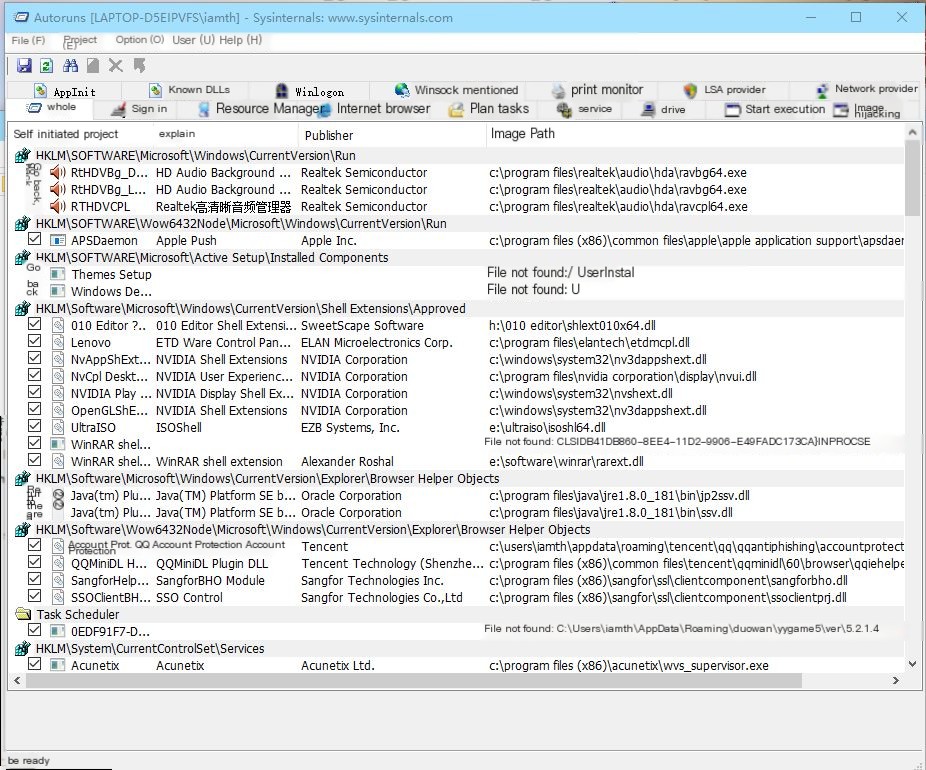
For local behavior monitoring, I recommend: ProcessExplorer and Autoruns for process monitoring. These tools are not widely known but are quite useful.
 >
>
ProcessExplorer Process Monitoring
 >
>
Autoruns Process Monitoring Tool
Among local monitoring tools, there’s also a tool dedicated to monitoring the registry. Here are some recommended ones:
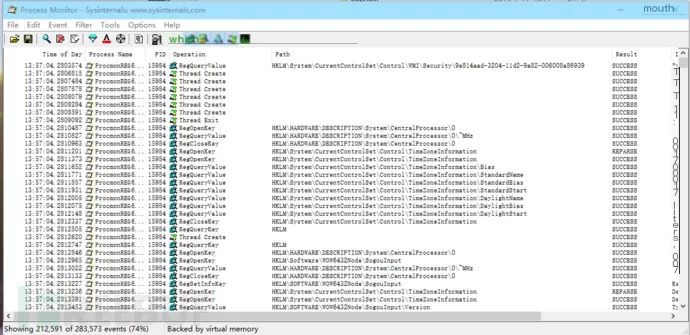
Process Monitor: A powerful registry monitoring tool that can add filter rules for convenience.
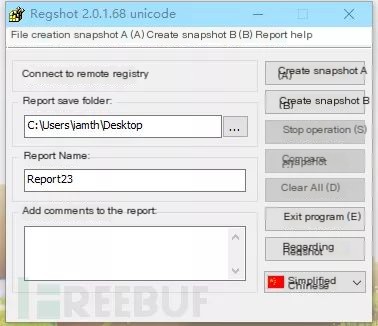
Regshot: A registry backup and comparison tool that can identify registry value changes through snapshots.
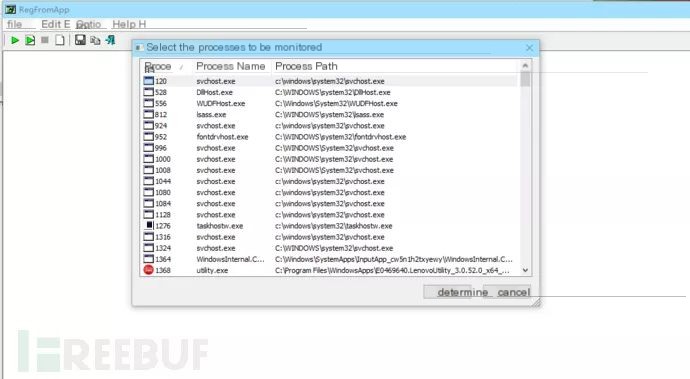
RegfromApp: A process monitoring tool that can track registry modifications by selecting a process.
For network behavior monitoring, the famous Wireshark is the top choice. Additionally, WSExplorer from Suiyue Union, a niche but excellent tool for process packet capture, is recommended.
Wireshark
Suiyue Union’s process packet capture tool WSExplorer is very convenient, with processes on the left and captured packets on the right.
With these tools, we can be well aware of what programs are doing on our computer, understanding is key to victory, enabling us to proceed to the next step of vulnerability discovery.
0x02 Vulnerabilities
For developers, it is impossible to develop a program without any vulnerabilities, especially when the program is large; it is bound to have vulnerabilities. We need to know where vulnerabilities are likely to appear;
Client-side Authorization and Authentication Vulnerabilities:
Genuine client software typically includes an authorization module aimed at ensuring only buyers can use it. Validation usually involves registration codes bound to the personal computer’s machine code or another personal authentication mechanism. Authorization vulnerabilities can lead to software and features being cracked, resulting in the circulation of pirated software — issues stemming from a lack of emphasis on the confidentiality and security of authorization during development.
Client-side Network Service Vulnerabilities:
These vulnerabilities generally occur when strict authentication is not applied during data packet transmission or reception, allowing unconditional calls to high-privilege services.
Client-side Functional Logic Vulnerabilities:
These arise from unreasonable client functionality designs, potentially leading to unauthorized access and other severe consequences.
Client-side Overflow Vulnerabilities:
This type involves higher difficulty in reverse engineering, primarily caused by logical errors in memory management or program execution during development.
This article will only introduce the first three vulnerabilities.
0x03 Practical Application
Client-side Functional Logic Vulnerabilities:
To discover these, primarily examine the logic between client functions, akin to web logic vulnerabilities. However, it differs as functional logic vulnerabilities may include parts after decompilation, generally by modifying the jump logic above critical call functions for discovery. The root cause is overly simplistic client logic, with minimal logical judgments. Such vulnerabilities are uncommon in clients with robust functionality.
Client-side Authorization and Authentication Vulnerabilities:
1. Local Registry-based Crack:
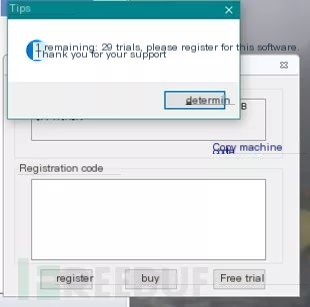
Some software uses the network for authorization validation, but due to registration count verification flaws, it’s possible to modify the registry to achieve unlimited trials, resulting in an “unauthorized use” authorization vulnerability. Take this client program as an example; it prompts 29 trial uses remaining on startup.
Now, open Process Monitor and use filtering to whitelist and show only the related process information.
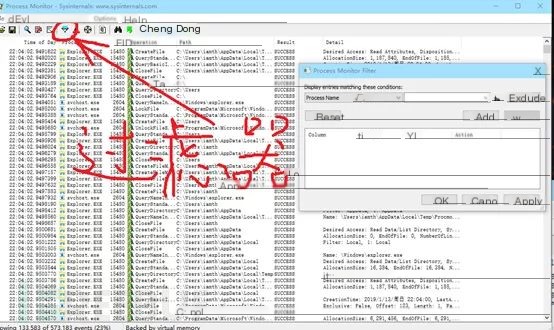
Whitelist filtering to show only the process
Actions were taken at critical points…
After stopping all captures, restart the client and repeat multiple times, observing that upon each launch, it automatically performs a RegsetValue (change registry value), as shown:
Upon testing, it was discovered the remaining trial uses are calculated by subtracting the registry entry value under the key named Nowtimes from 30.
We then write a BAT script to modify the value the client points to, ensuring it runs at startup to lock trial uses at 30 without decrementing.
Reg add HKCU\Software\NameOfClient\SomeLocation /v Nowtimes /t REG_DWORD /d 0 /f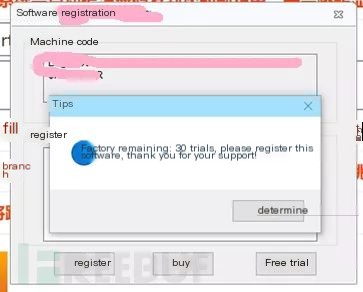
The root cause of this vulnerability is the simplistic method of checking trial uses: no networking, plaintext written to the registry, and the name Nowtimes being easily interpretable. Registry-based vulnerability exploitation and discovery methods are relatively simple, yet such vulnerabilities are quite common, so pay attention to the registry during discovery. If registry monitoring is disabled, use REGshot for snapshot comparison analysis.
2. Network Authorization Verification-based Hosts Spoofing:
This section requires some reverse engineering knowledge. The cracked client this time has no trial mechanism, so the first method didn’t work. We shifted focus to its network verification mode, inspecting how its network authorization worked.
Key code areas processed
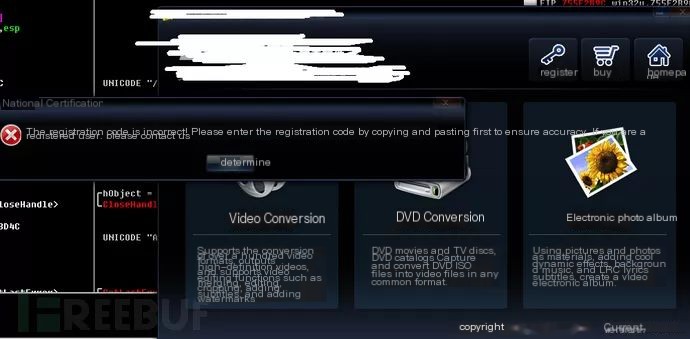
Enter a random registration code
Enter a random registration code, then confirm. Use the resulting error window to locate the client’s registration detection function. Drag into OLLYdbg, search for the string “Registration Code Error,” and trace to the assembly window.
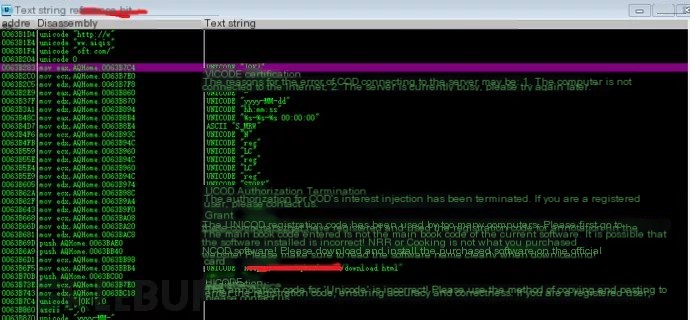
We obtained the server address for registration authorization. To further confirm, use Wireshark to analyze the client’s network requests during registration.
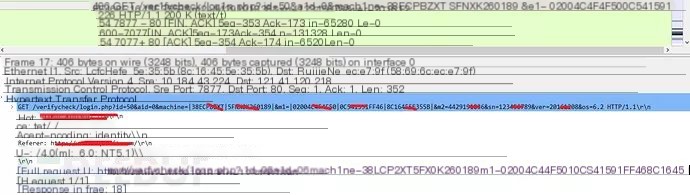
The client requests the server’s /verifycheck/login.php carrying the machine code and other data.
Back to our assembly window, observe several Unicode encodings, possibly server responses, and note them.
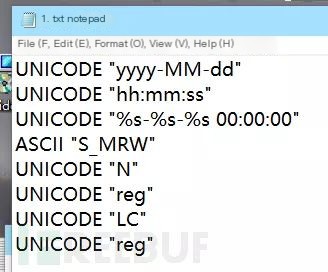
Visiting directly via browser reveals a return value matching one of the assembly window’s records, suggesting the feasability to construct a fake server. Modify the host’s file to redirect requests and return registration success info.
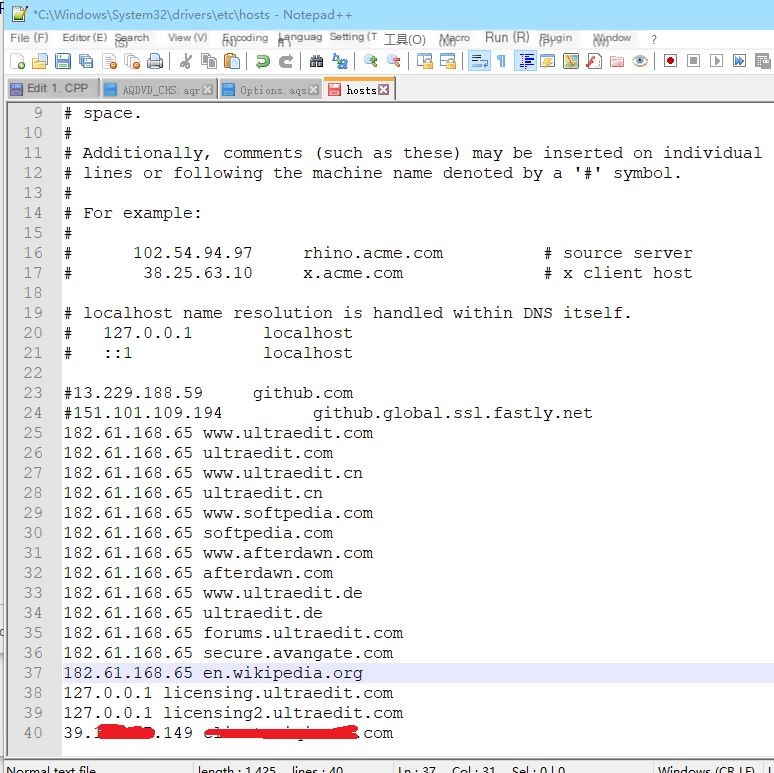
Modify hosts file to map server domain to our fake server’s IP
Construct various payloads on the server to elicit different client responses, indicating partial success.
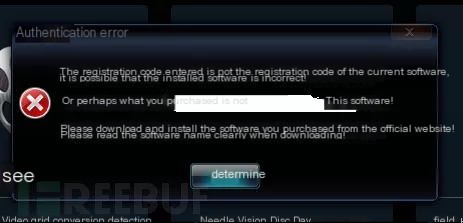
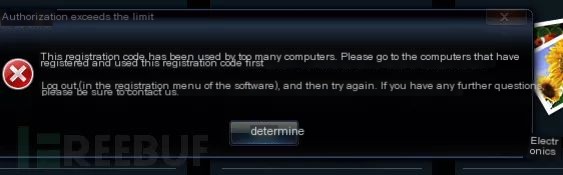
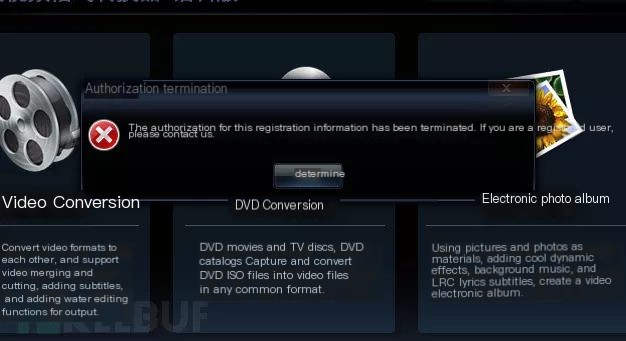
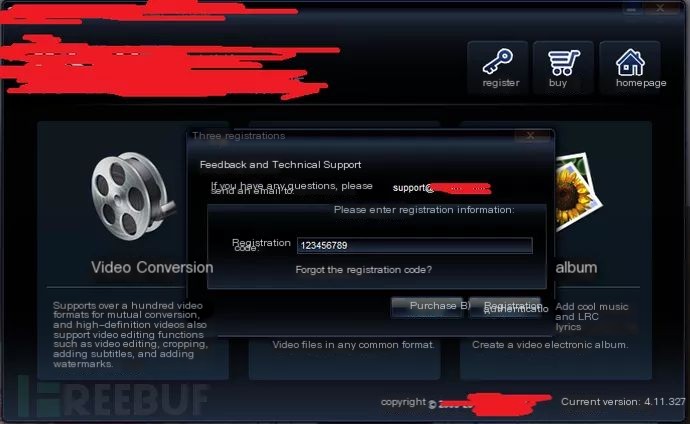
Excluding other payloads, determine a formatted date return value as the success symbol. Construct a formatted time and reopen the client, entering any registration code to see the registration success window.
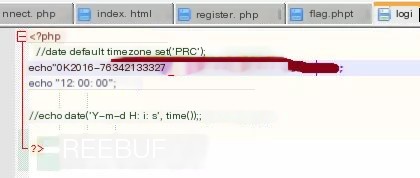
Final payload
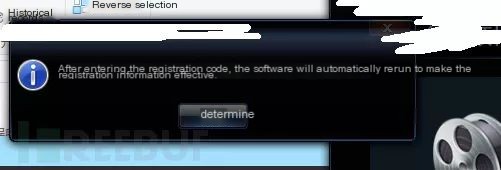
This vulnerability results from overly simplistic handling of registration code return data, affording easy construction of successful registration responses. Additionally, the client’s decompilation is poor, with sensitive info visible post-decompilation. Discovering such vulnerabilities requires basic reverse engineering knowledge and computer networking basics, focusing critically on communication data between the client and the network server, using packet capture tools for vulnerability discovery.
Client-side Network Service Vulnerabilities:
Due to the unpatched vulnerability in the demonstration example, it’s omitted here. Network service vulnerability discovery primarily involves analyzing client network requests, using previously mentioned process packet capture tools and Wireshark. Most network service vulnerabilities arise from unsecured authentication methods in requests, allowing anyone to validly request network services without authorization, thereby exploiting private network service interfaces. Common instances are client-side VIP resource preview services and paid query function interfaces. Unsafe client requests can be intercepted and analyzed, enabling unauthorized access to resources or interfaces. When discovering these vulnerabilities, focus on the client’s network transmission layer, analyzing every network service feature for vulnerability discovery.



