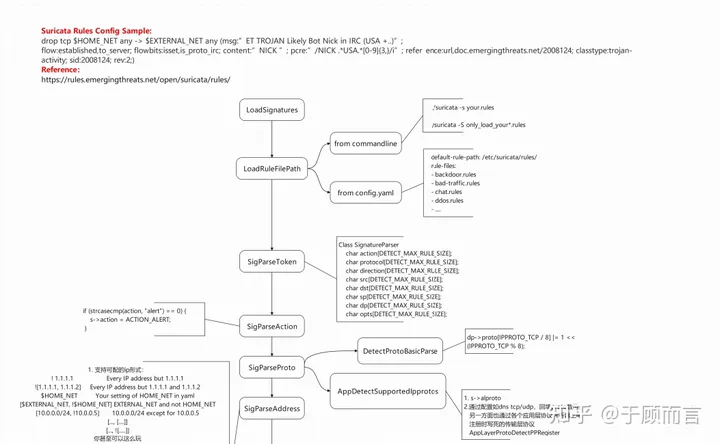
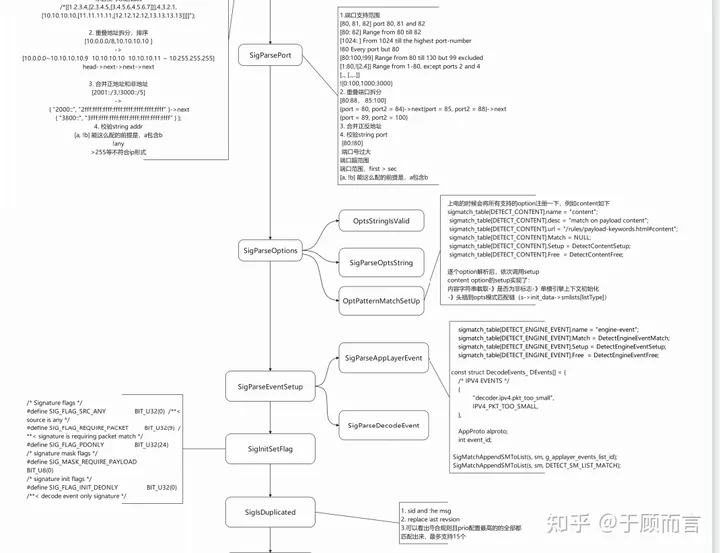
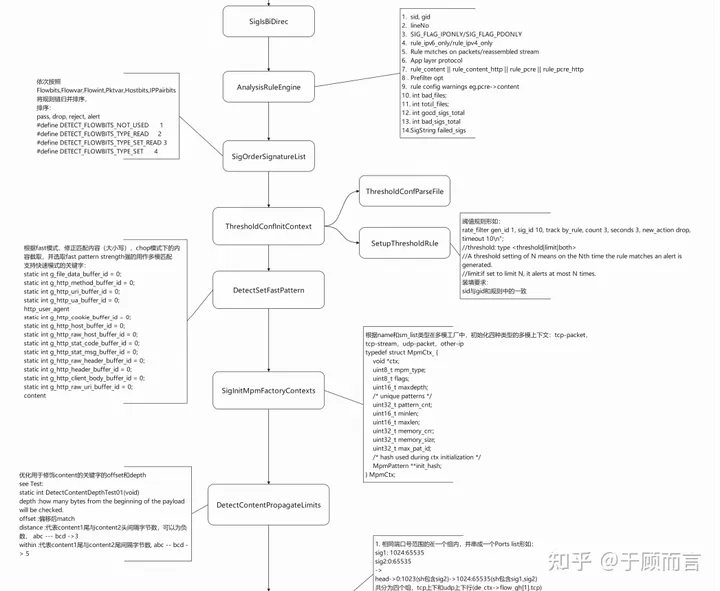
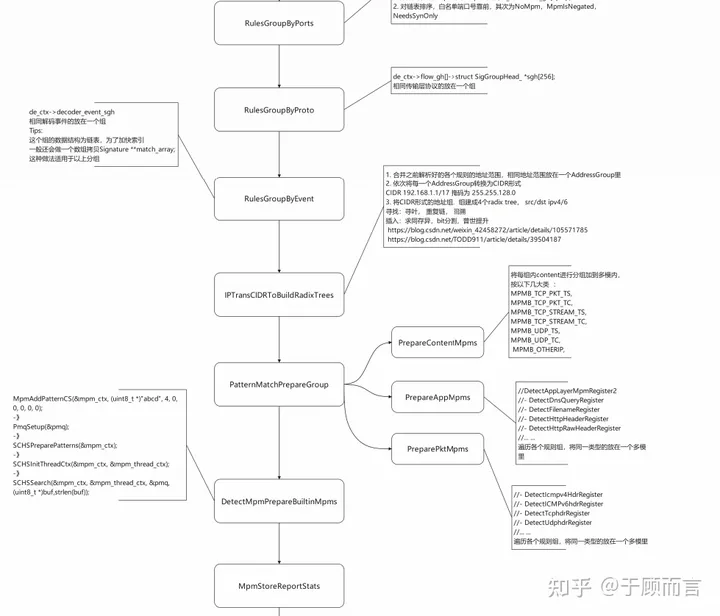
IP Rule Parsing Flowchart for Loading Suricata Rules
IP Rule Parsing:
1. Configurable IP Formats Supported:
! 1.1.1.1 Every IP address but 1.1.1.1
![1.1.1.1, 1.1.1.2] Every IP address but 1.1.1.1 and 1.1.1.2
$HOME_NET Your setting of HOME_NET in yaml
[$EXTERNAL_NET, !$HOME_NET] EXTERNAL_NET and not HOME_NET
[10.0.0.0/24, !10.0.0.5] 10.0.0.0/24 except for 10.0.0.5
[…, [….]]
[…, ![…..]]
You can even do it like this
/*[[1.2.3.4,[2.3.4.5,[3.4.5.6,4.5.6.7]]],4.3.2.1,
[10.10.10.10,[11.11.11.11,[12.12.12.12,13.13.13.13]]]]”);
2. Splitting and Sorting of Overlapping Addresses
[10.0.0.0/8,10.10.10.10 ]
->
[10.0.0.0~10.10.10.10.9 10.10.10.10 10.10.10.11 ~ 10.255.255.255]
head->next->next->next
3. Merge Positive and Negative Addresses
[2001::/3,!3000::/5]
->
{ “2000::”, “2fff:ffff:ffff:ffff:ffff:ffff:ffff:ffff” }->next
{ “3800::”, “3fff:ffff:ffff:ffff:ffff:ffff:ffff:ffff” } };
4. Validate String Address
[a, !b] The prerequisite for this configuration is that a contains b
!any
>255 does not conform to IP format
Port Parsing:
1. Port Range Support
[80, 81, 82] port 80, 81 and 82
[80: 82] Range from 80 till 82
[1024: ] From 1024 till the highest port-number
!80 Every port but 80
[80:100,!99] Range from 80 till 100 but 99 excluded
[1:80,![2,4]] Range from 1-80, except ports 2 and 4
[.., [..,..]]
![0:100,1000:3000]
2. Splitting of Overlapping Ports
[80:88, 85:100]
{port = 80, port2 = 84)->next{port = 85, port2 = 88}->next
{port = 89, port2 = 100}
3. Merge Positive and Negative Addresses
4. Validate String Port
[80:!80]
Port number too large
Port out of range
Port range, first > sec
[a, !b] The prerequisite for this configuration is that a contains b