I. Linux Network Security Model
1. Firewall: Operates at the host or network perimeter, detecting and processing inbound and outbound messages based on a set of predefined rules implemented in hardware or software, or both.
1) Commonly used firewall devices
Hardware Firewall: A dedicated firewall hardware device operating at the entire network entry point.
Software Firewall: Software operating on top of the TCP/IP protocol stack on a host (operating in the kernel).
2) Firewall working positions
Network Layer: Operates at the network layer, similar to routers, primarily dismantling physical layer and link layer protocols, and detects the IP/TCP/UDP/ICMP network layer and transport layer protocol headers to customize rules.
Application Layer: Operates at the application layer, dismantling network and transport layer headers to examine application layer content.
2. IDS (Intrusion-detection system)
HIDS (Host Intrusion Detection System): OSSEC
NISC (Network Intrusion Detection System): Snort (can be used as a network sniffer)
Filesystem: Filesystem-level intrusion detection
3. IPS (Intrusion Prevention System): Integration of IDS and Firewall
4. Honeypot: A deceptive system used to trap hackers and gather evidence.
5. System Security Vulnerability Scanning Tools, conduct system security assessments: Nessus, nmap, etc.
6. Rootkit: Backdoor directly implanted at the system layer cannot be protected against; system reinstallation is the only solution.
II. iptables Working Mechanism
1. iptables/netfilter: A network layer firewall capable of connection tracking (state detection), serving as a rule writing tool. Rules take effect through the netfilter framework in the kernel.
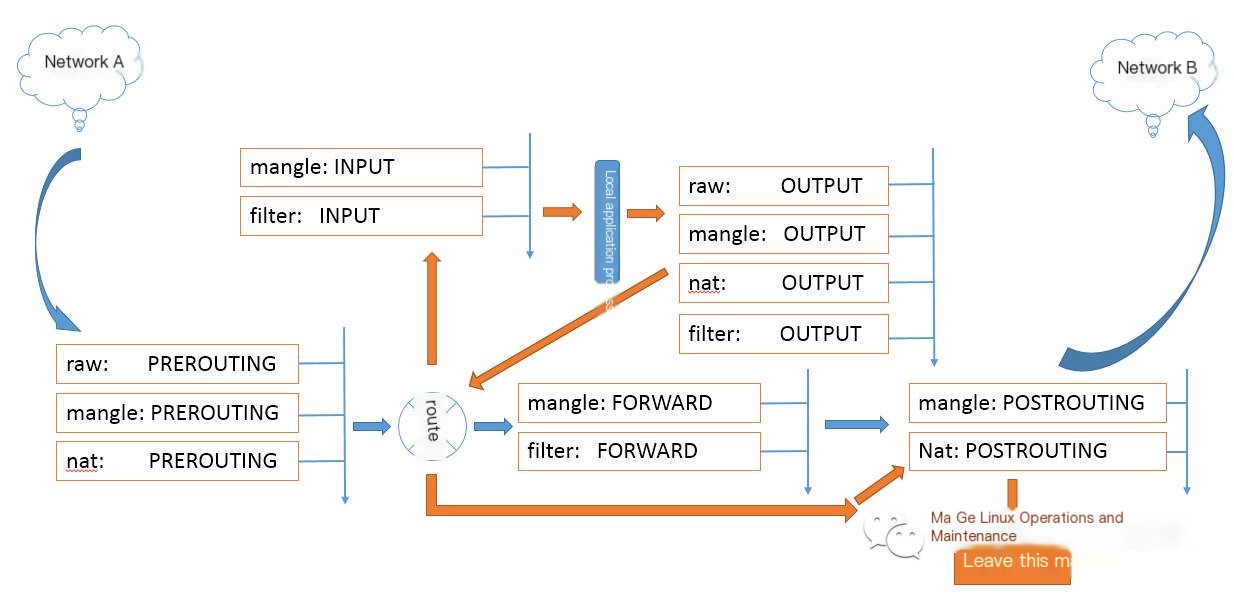
2. Set iptables protection in five positions (hook_function positions) and allow rules (five chains, four tables):
>
1) PREROUTING: Incoming packets from outside the host, allows mangle, nat tables (destination address translation, converting local machine address to actual target machine address, usually referring to response packets)
2) INPUT: Packets entering the local user space, allows filter, mangle tables
3) OUTPUT: Packets leaving the local user space, allows filter, mangle, nat tables
4) FORWARD: Packets routed and detected as not meant for the local machine but not yet knowing which network card to exit from, allows filter, mangle tables
5) POSTROUTING: Packets routed and forwarded out, allows mangle, nat tables (source address translation, converting the original address to the forwarding host’s output network card address)
Four tables: filter, nat, mangle, raw
Five chains: PREROUTING, INPUT, FORWARD, OUTPUT, POSTROUTING
3. Correspondence between tables and chains
1) filter: INPUT, FORWARD, OUTPUT
2) nat: PREROUTING, OUTPUT, POSTROUTING
3) mangle: PREROUTING, INPUT, FORWARD, OUTPUT, POSTROUTING
4) raw:
 >
>
4. Rules: Processing mechanism after matching
1) Allow: Default is to block, only opening for matched rules
2) Block: Default is to allow, only blocking matched rules
5. Network and Transport Layer Protocol Inspection Contents
1) IP:
SIP: Source IP
DIP: Destination IP
2) TCP:
SPORT: Source Port
DPORT: Destination Port
Flags: Flags
3) ICMP: ICMP-TYPE (ping command)
6. TCP Protocol Flags and Finite State Machine illustration
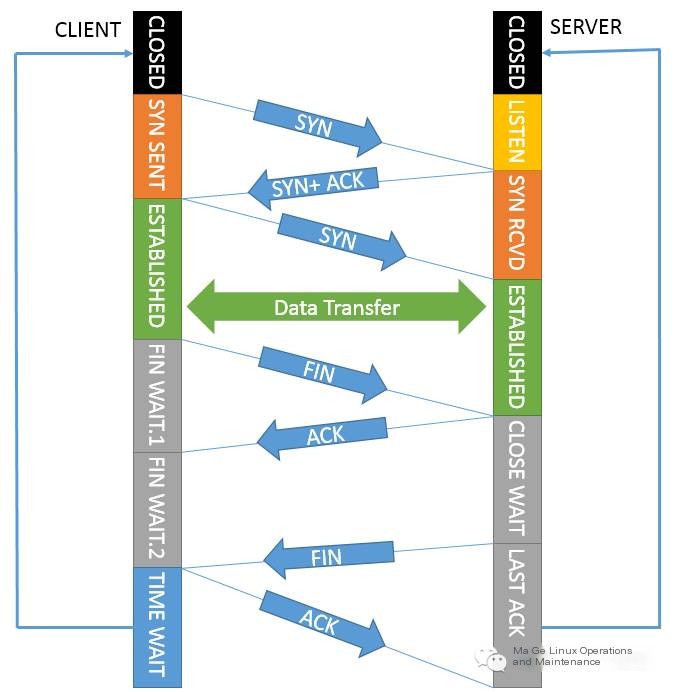
During TCP protocol communication, flags are transmitted and states transition. These flags are subject to rule detection.
7. Extended Detection Mechanisms:
1) time (according to time),
2) application layer protocols (such as QQ)
3) string sensitive characters
4) state (connection-tracking) connection tracking
8. Processing Mechanisms for Matched Packets:
1) DROP: Silently discard
2) REJECT: Reject, not recommended due to potential hostility
3) ACCEPT: Accept
4) SNAT: Source Address Translation
5) DNAT: Destination Address Translation
6) REDIRECT: Port Mapping
7) LOG: Log
8) RETURN: Return
For specific iptables functions and operations, see the next blog post…


